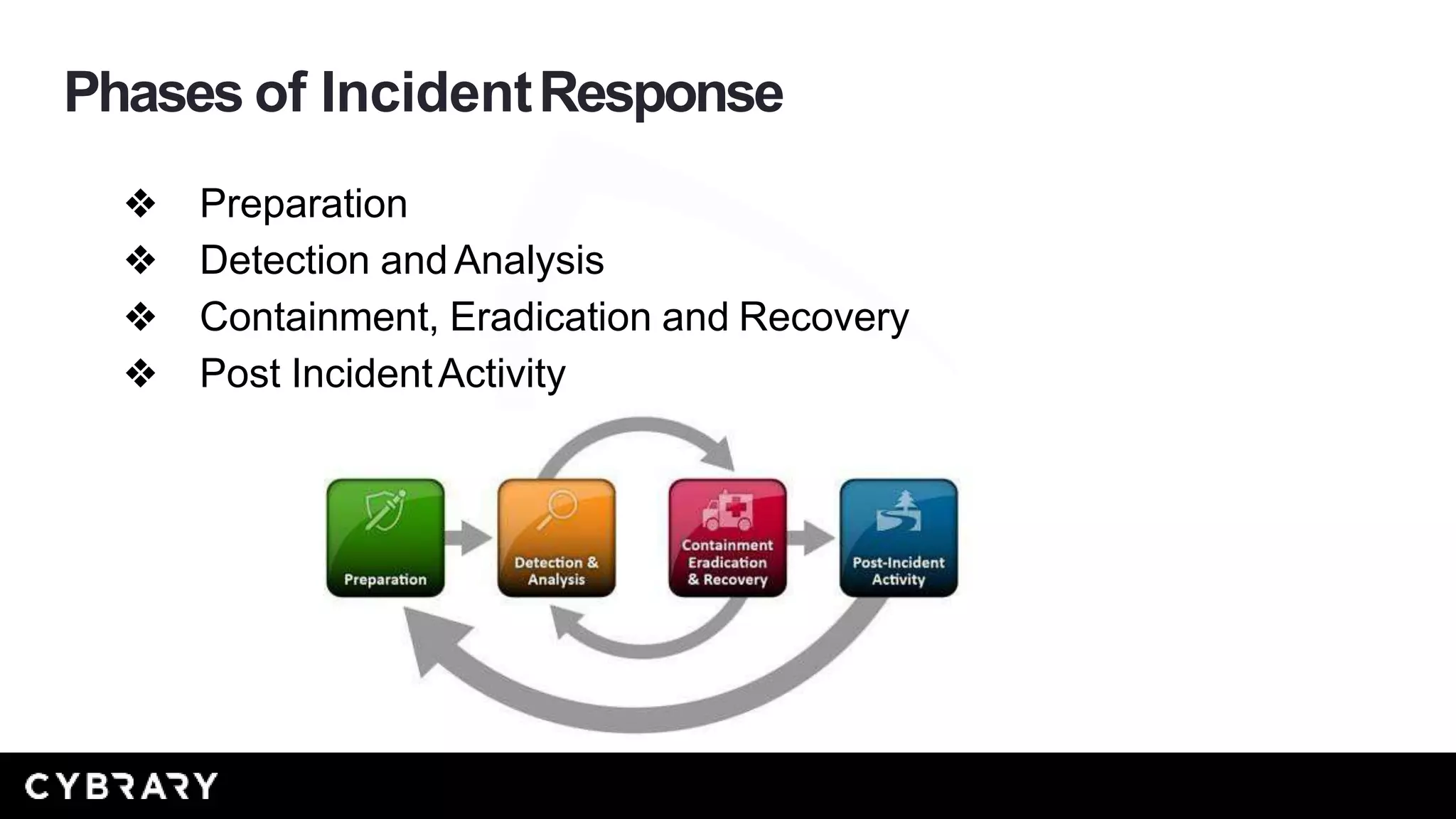
This document outlines a class on incident response in information security, detailing learning objectives such as identifying phases of incident response and creating incident response plans. Key phases of incident response discussed include preparation, detection and analysis, containment, eradication and recovery, and post-incident activity. The instructor, Zachery S. Mitcham, has extensive experience in the field and aims to guide participants towards effective strategies for handling security incidents.