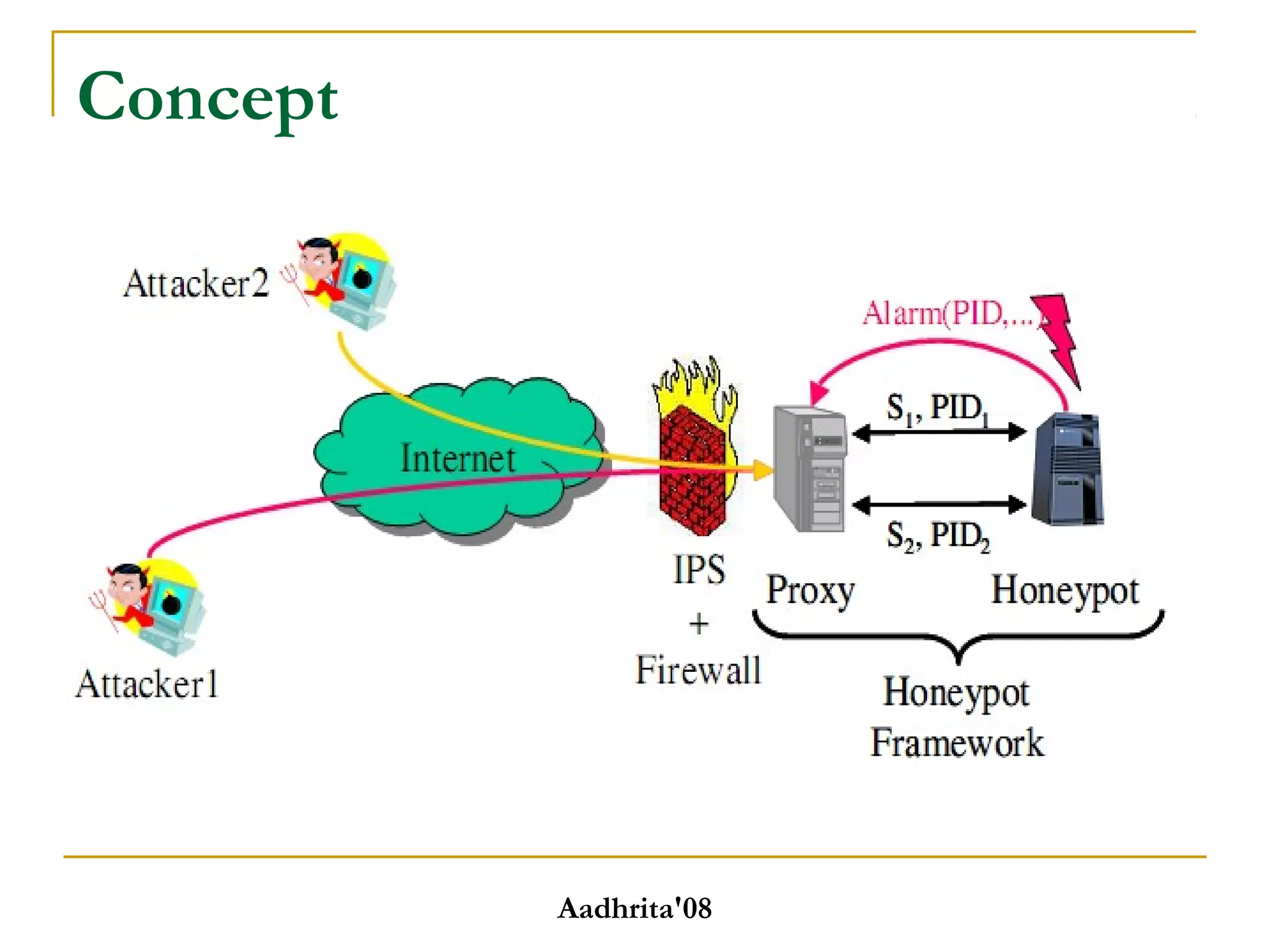
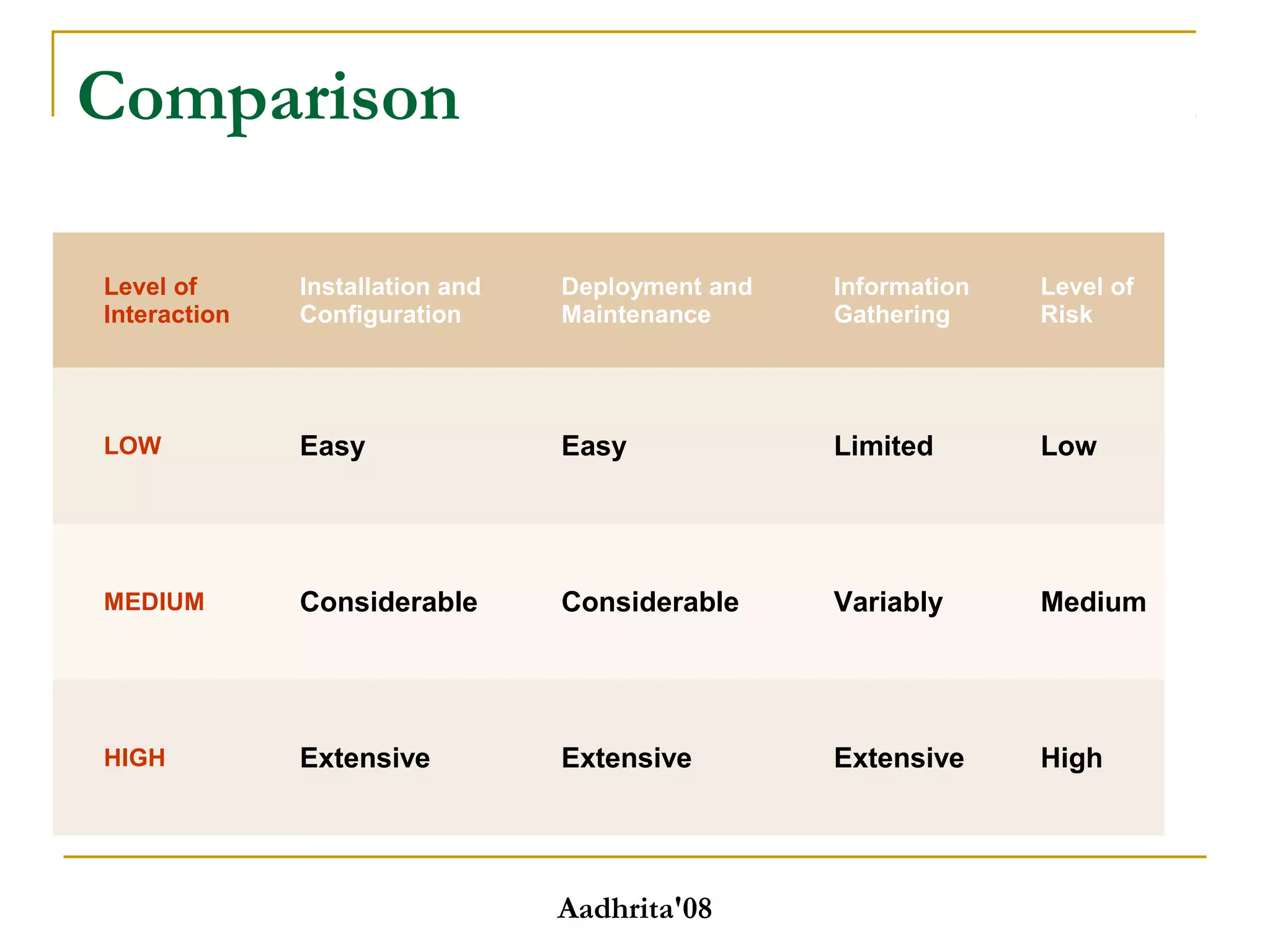
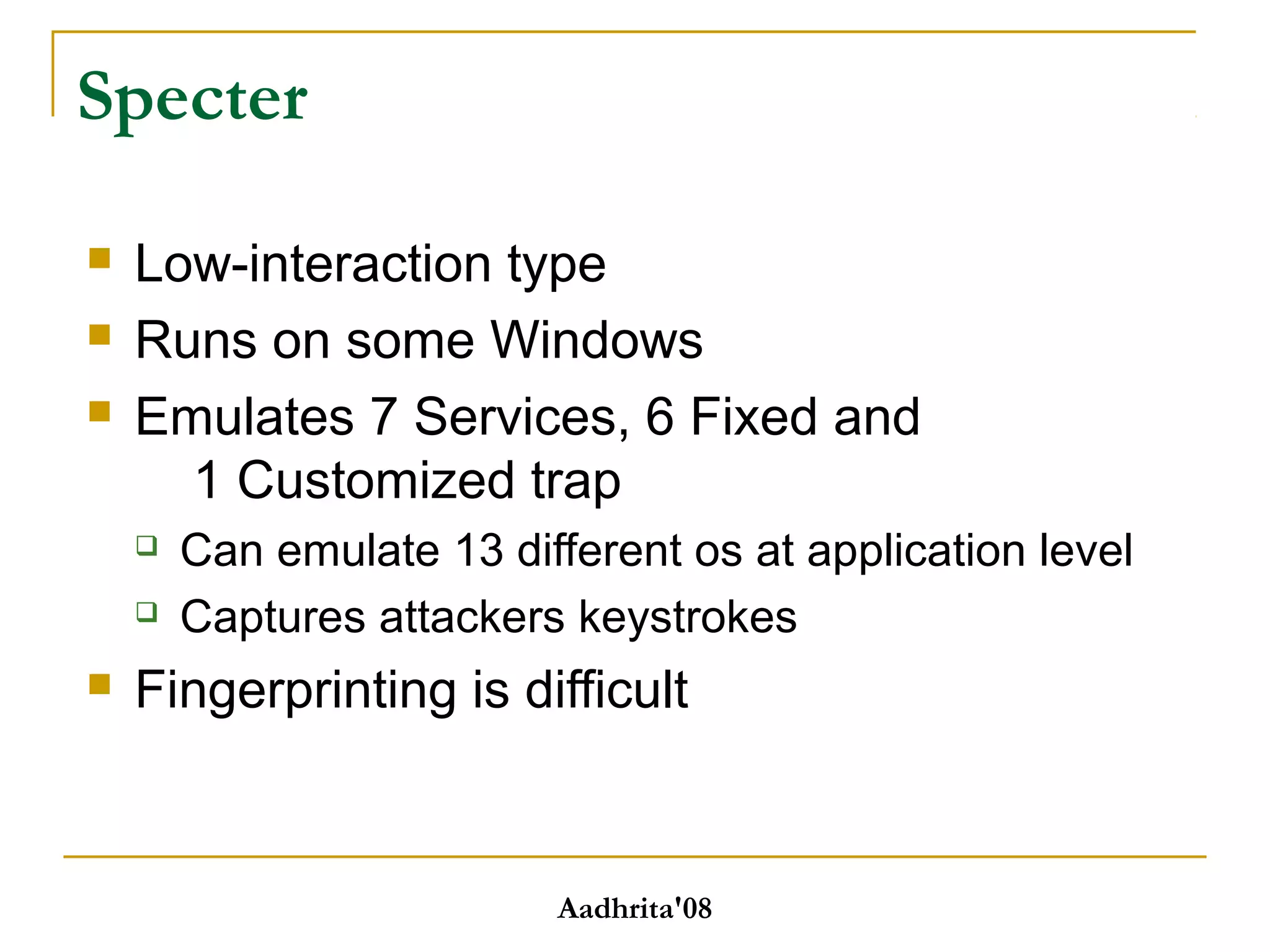
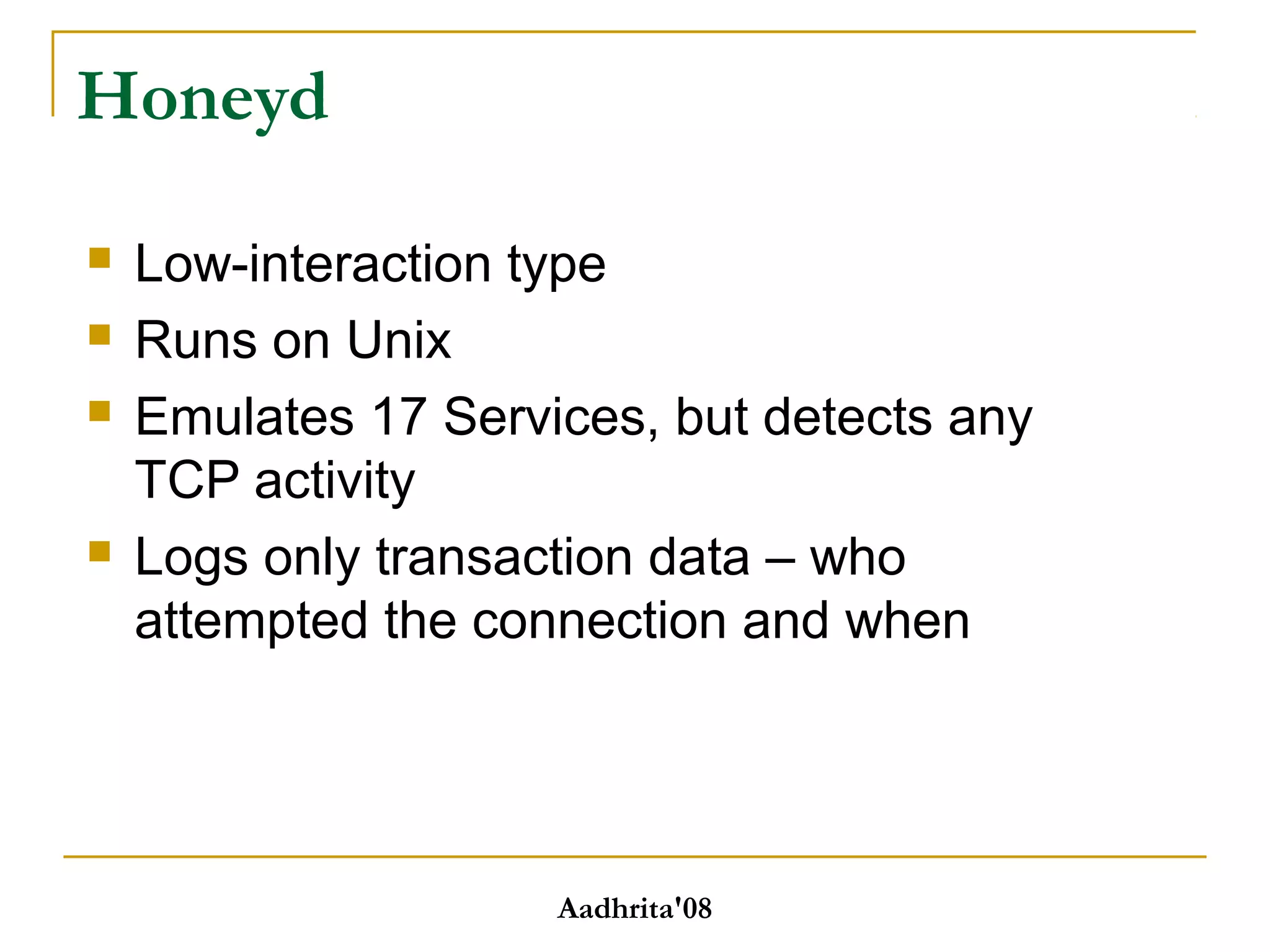
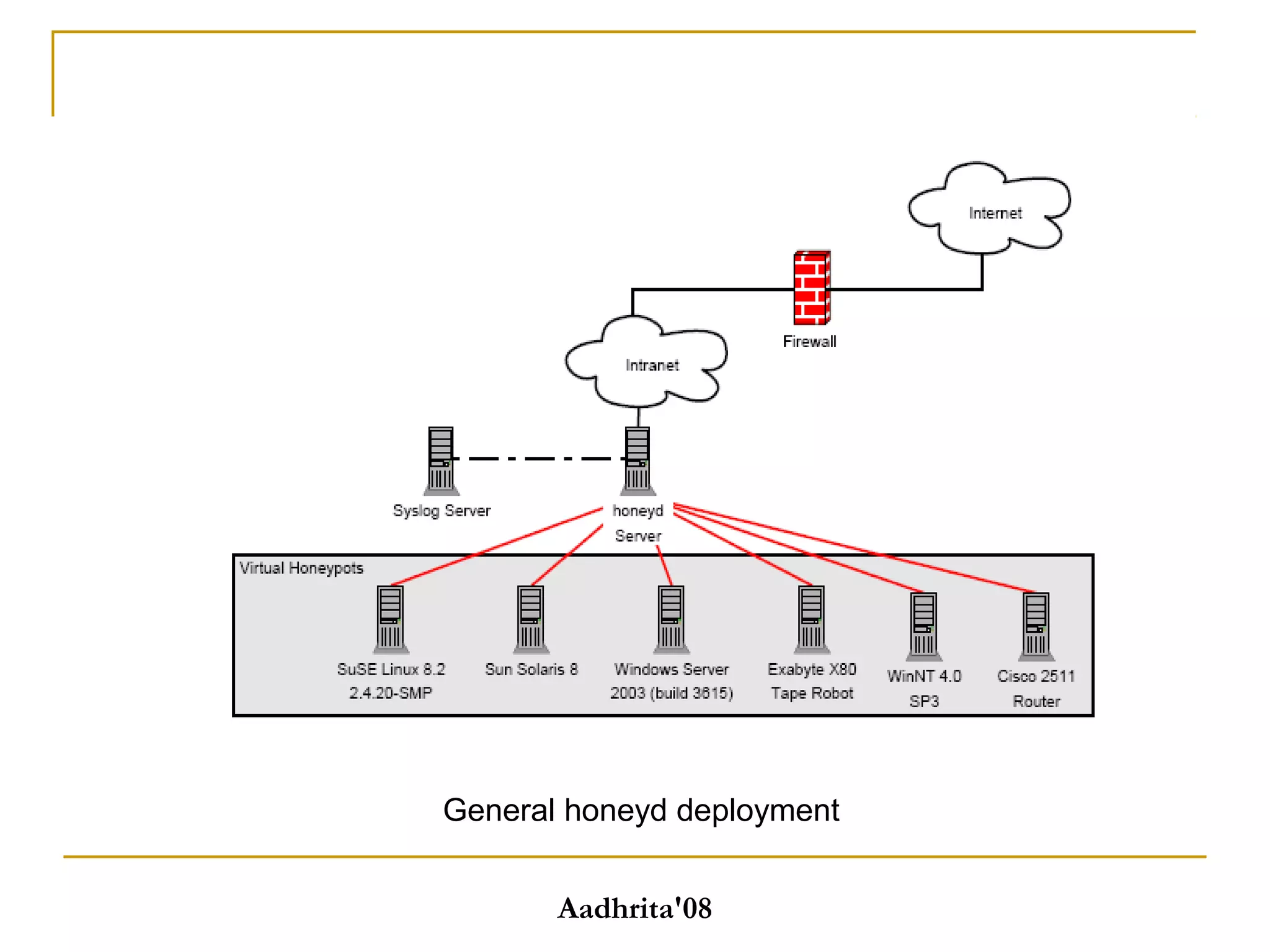
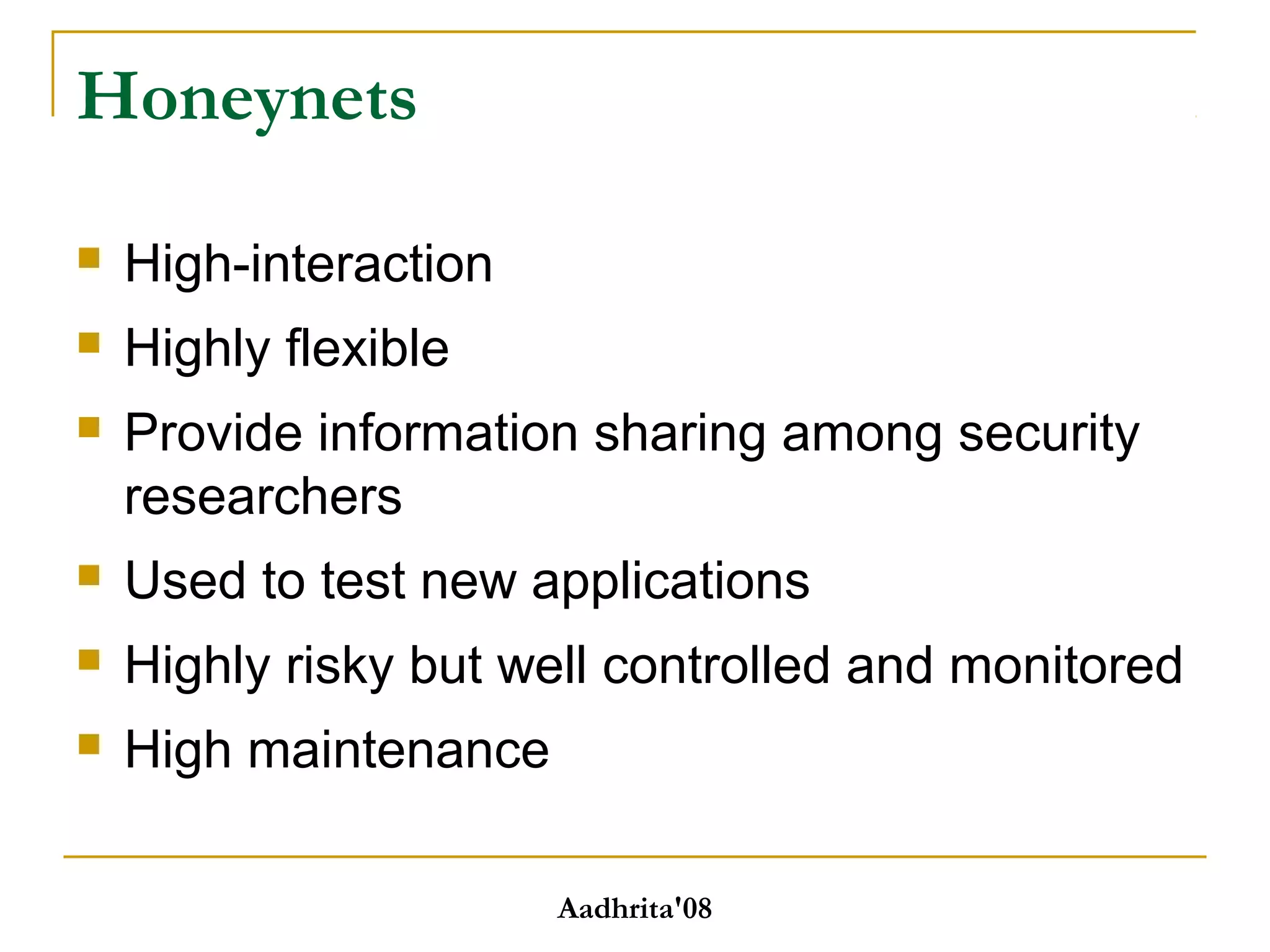
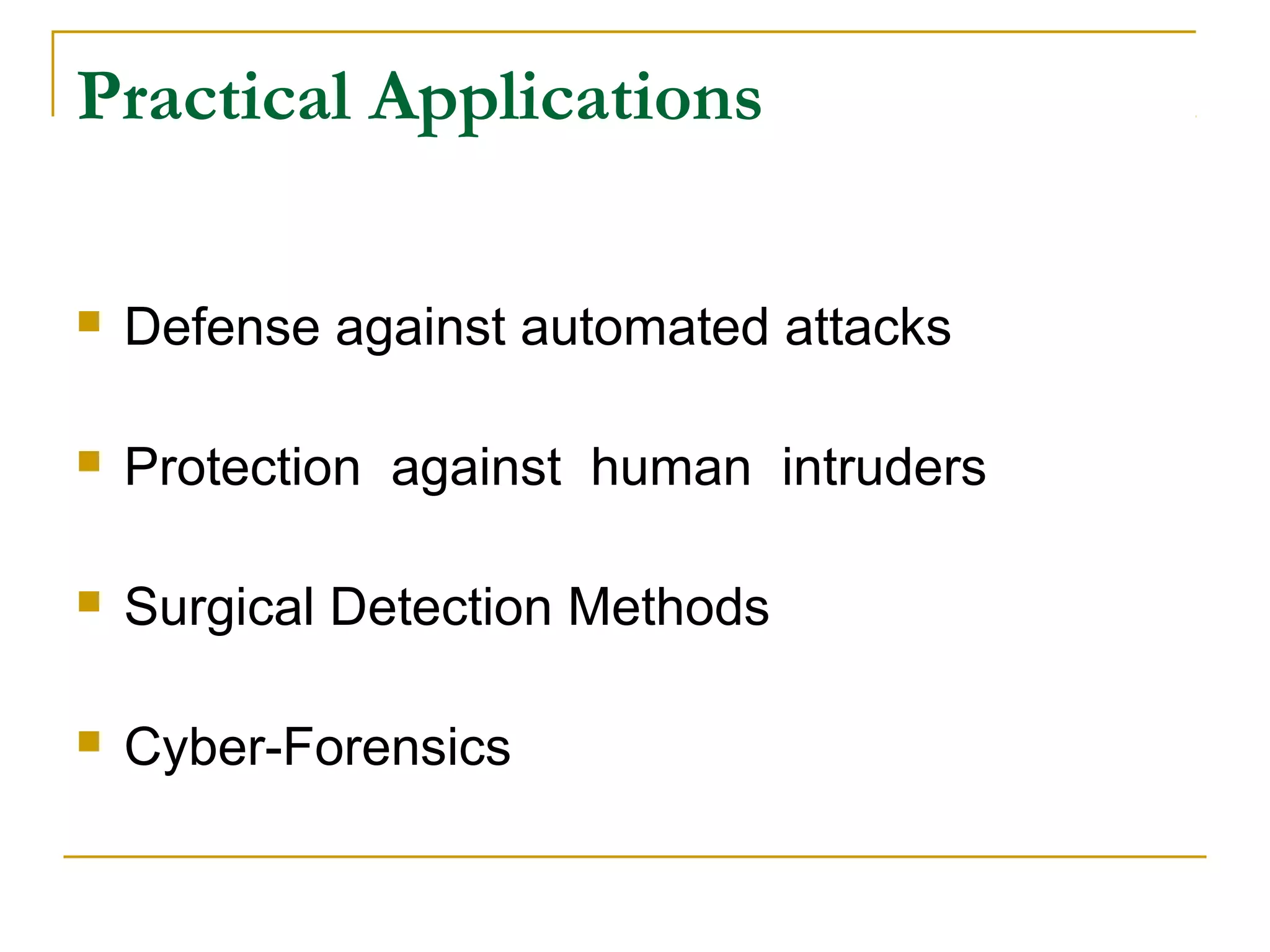
Honeypots are security tools that allow systems to be monitored, analyzed and defended. They work by emulating vulnerabilities to attract hackers and observe their behavior without exposing real systems to harm. There are different types of honeypots based on level of interaction, from low to high. Low interaction honeypots like Honeyd emulate services with limited functionality while high interaction ones like Honeynets create fully functional virtual systems. Honeypots provide benefits like reduced false alarms, new threat intelligence and forensic data but also have drawbacks like single data points and fingerprinting risks. They are useful for research, detection and prevention when used carefully alongside other security practices.