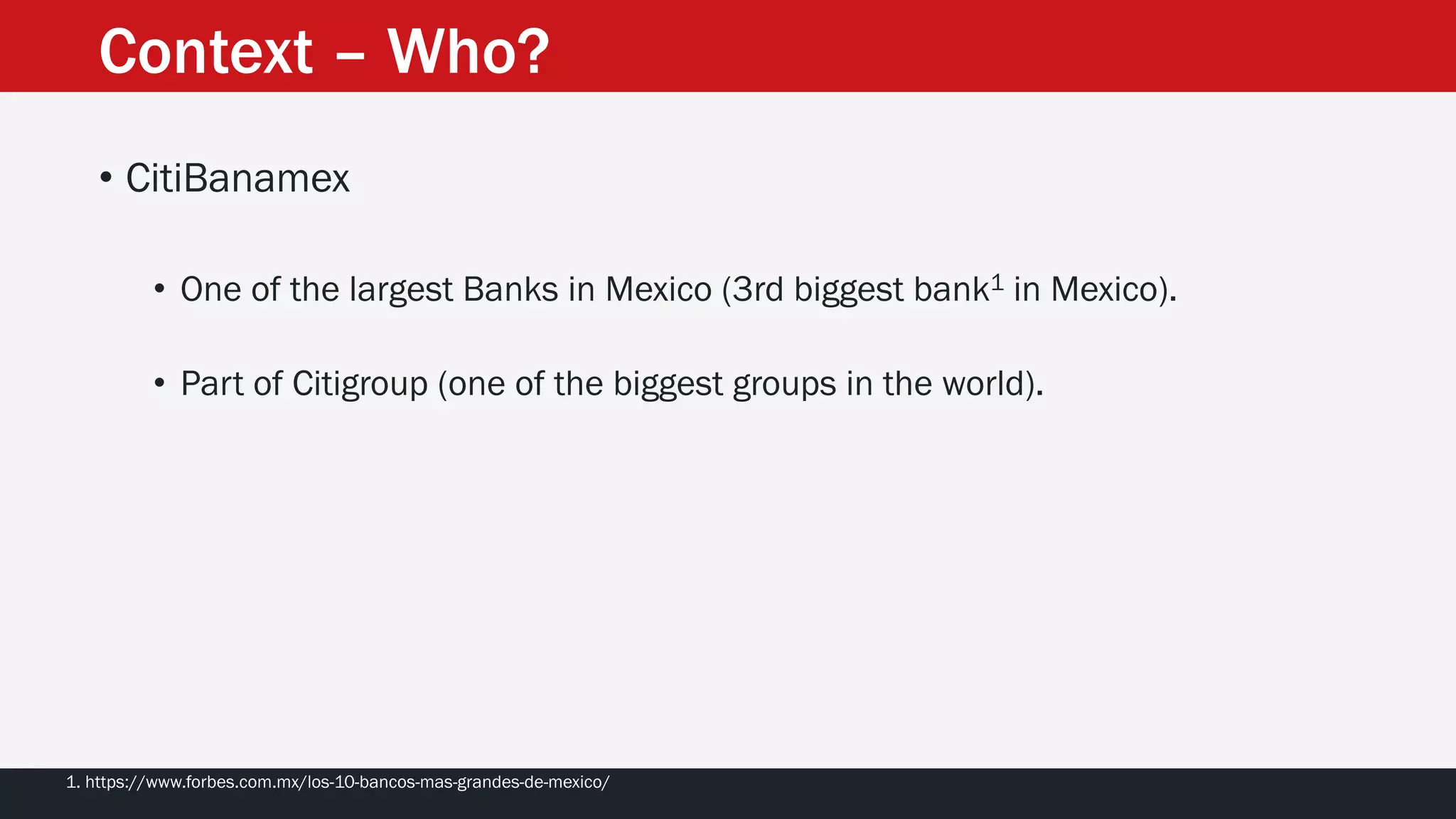
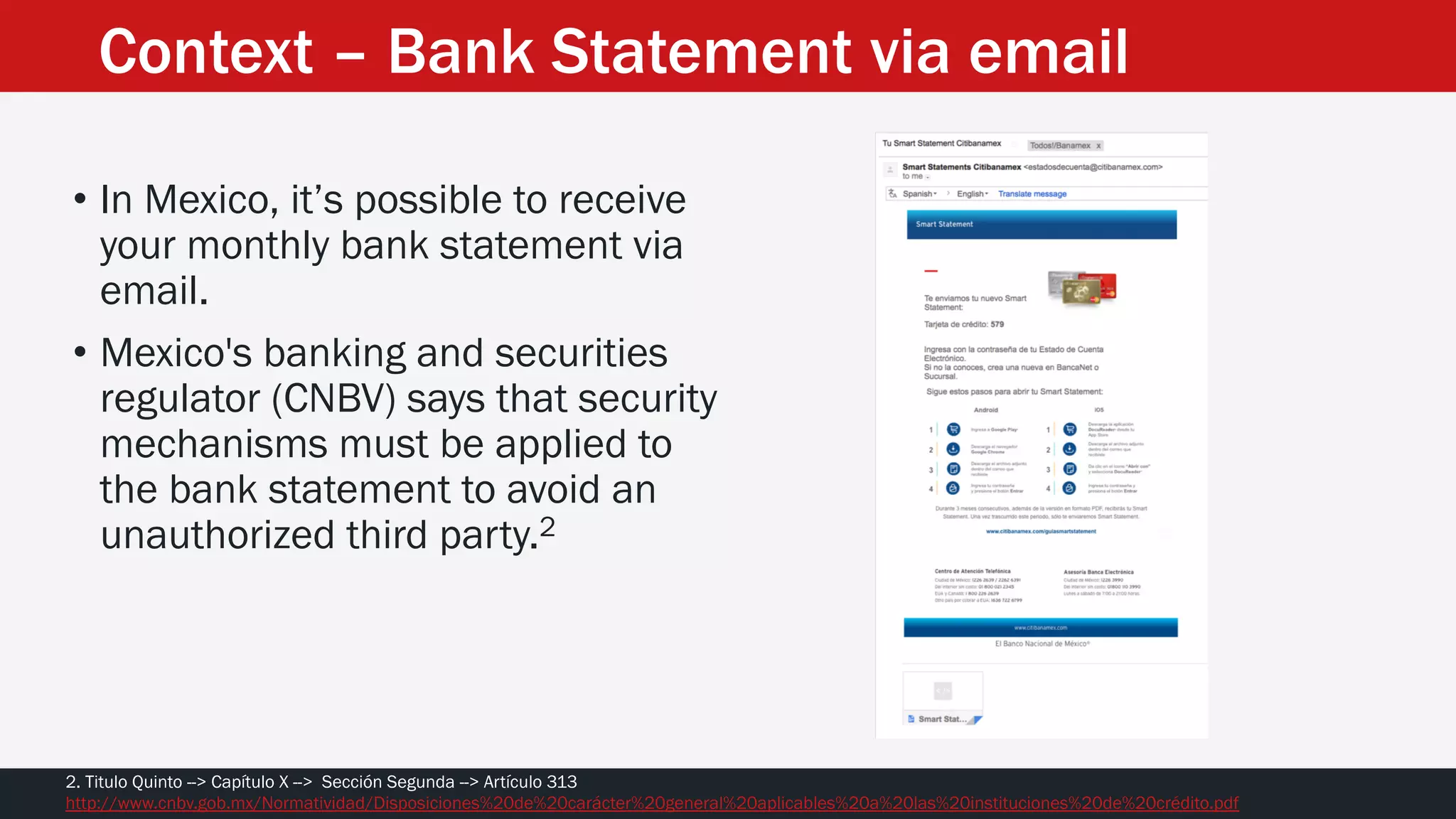
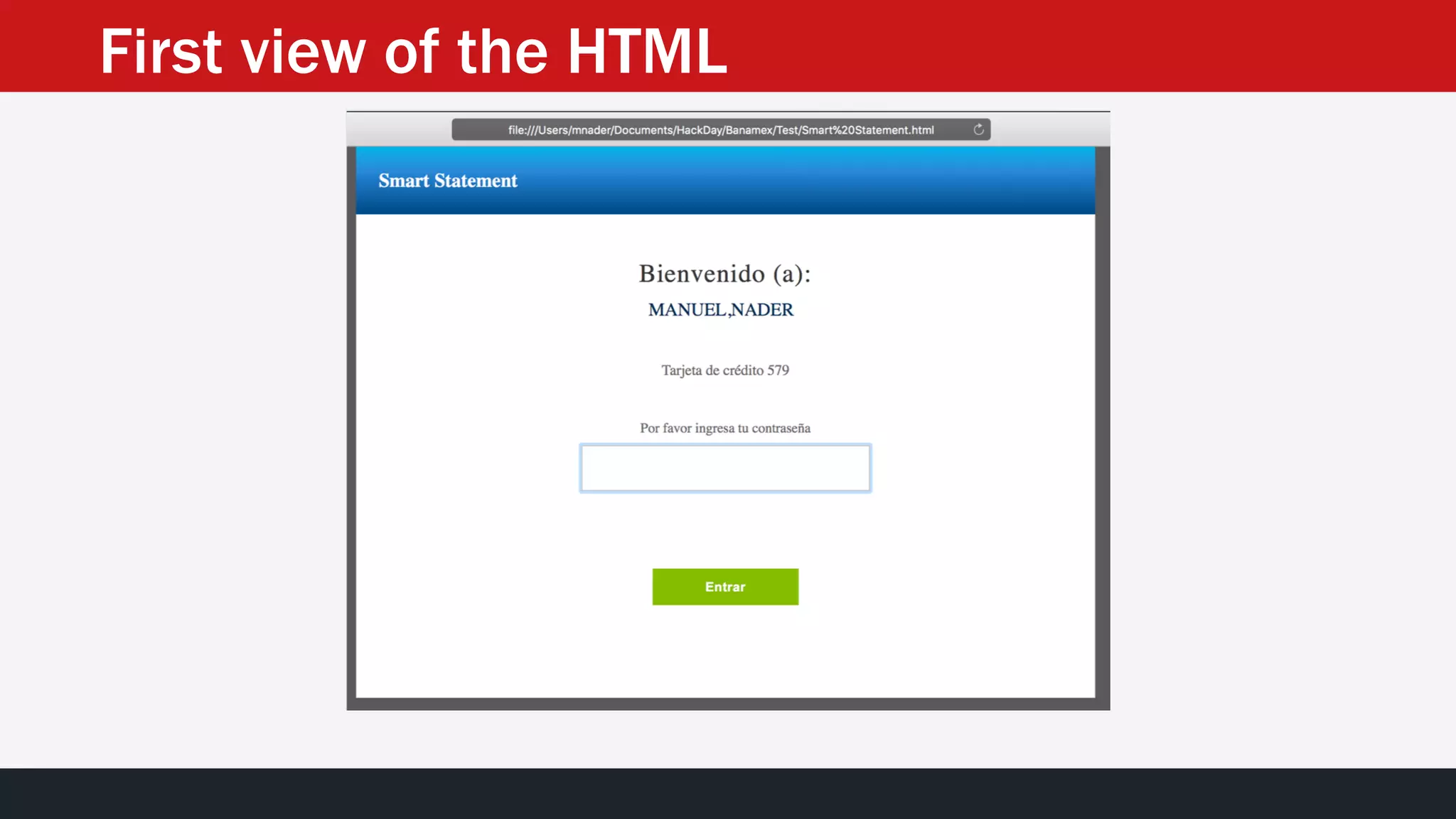
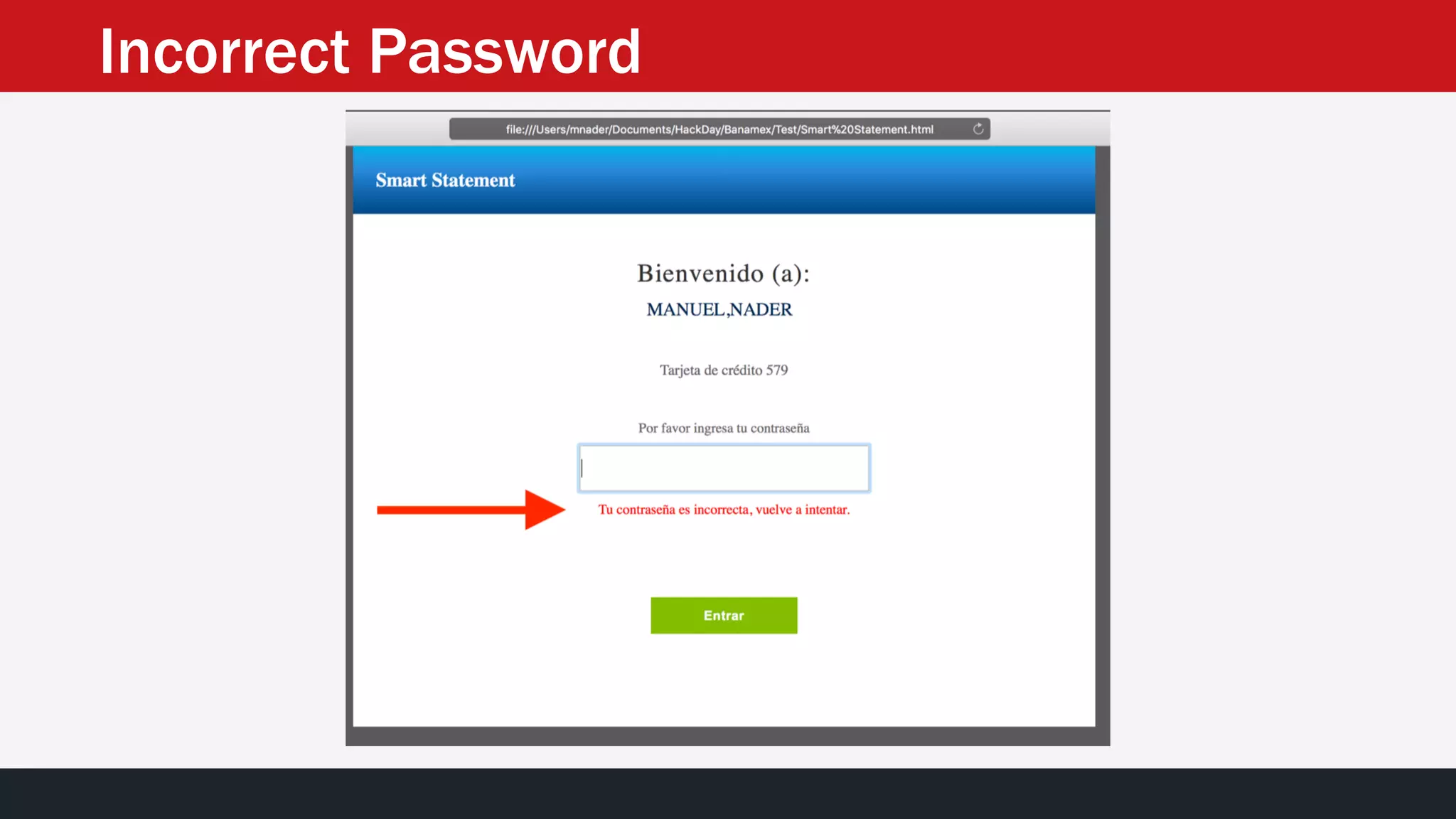
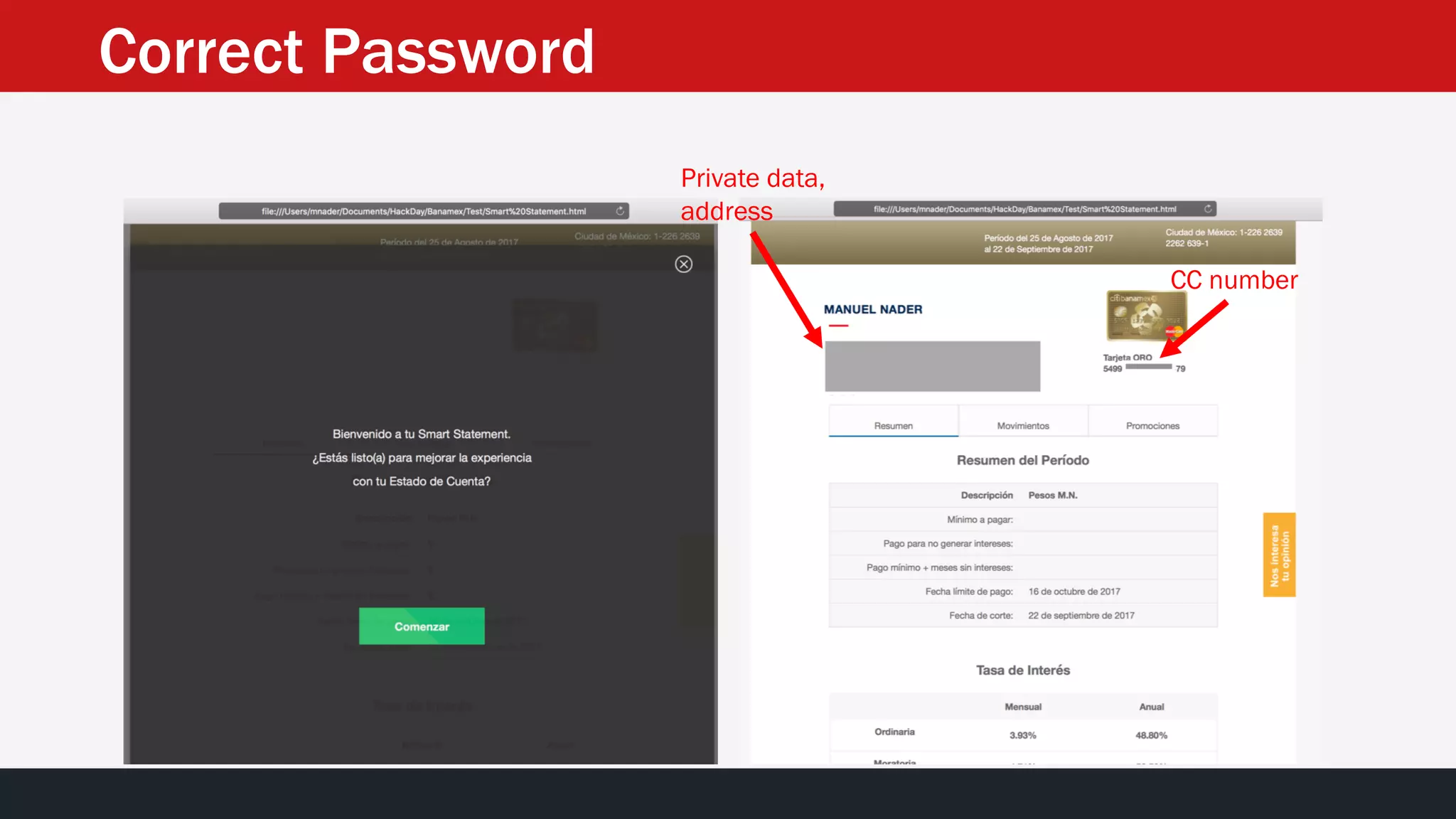
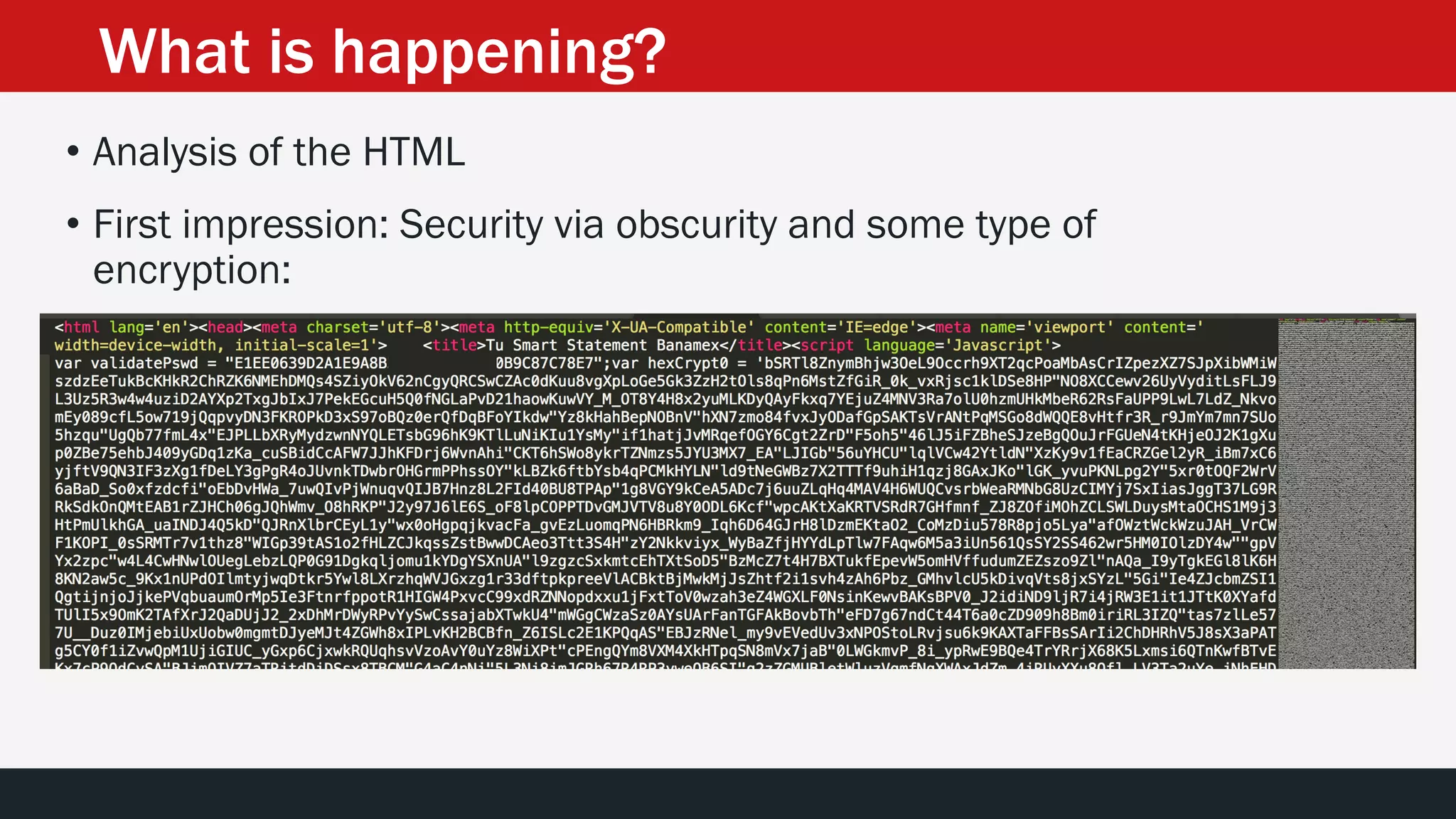
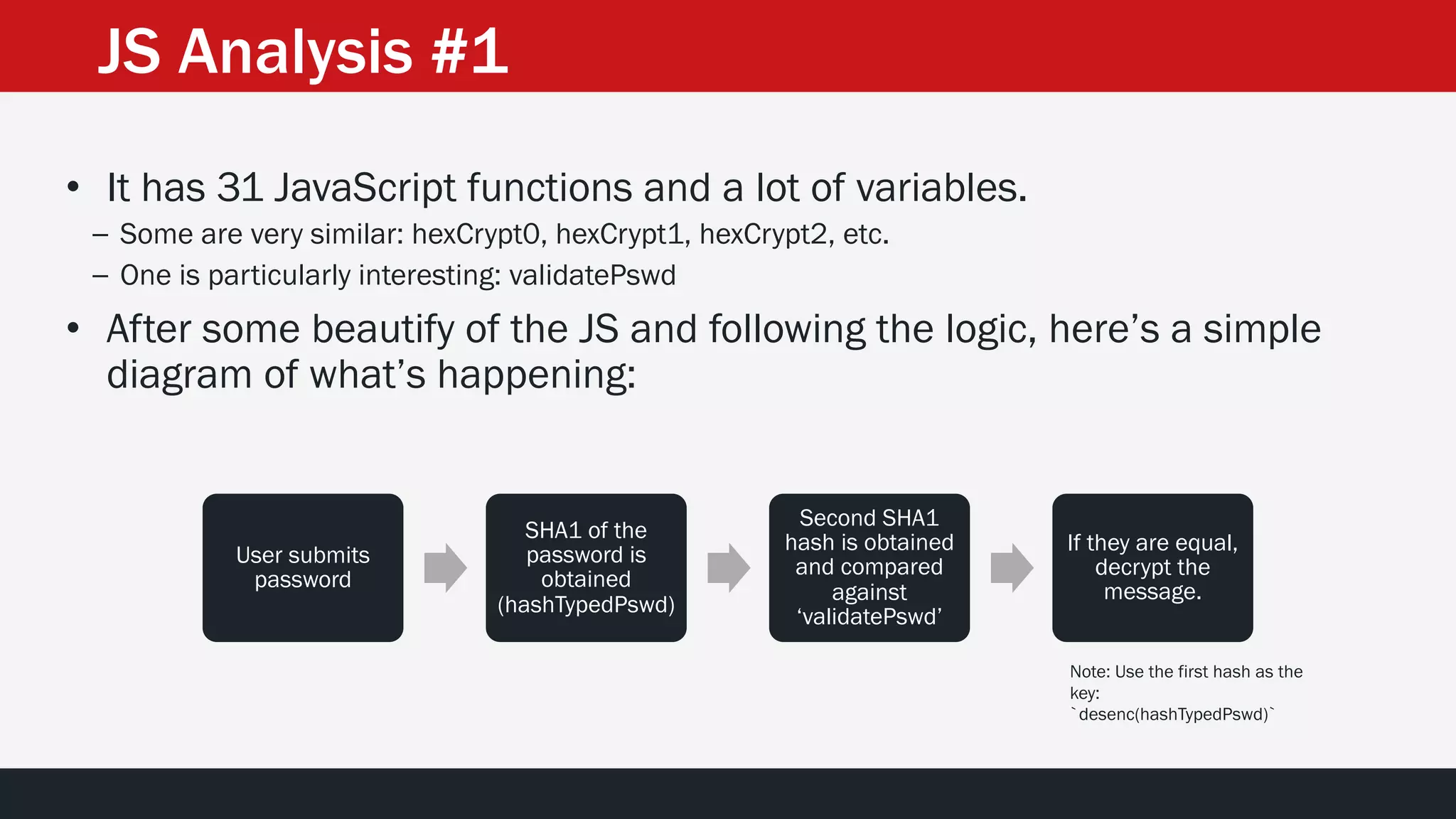
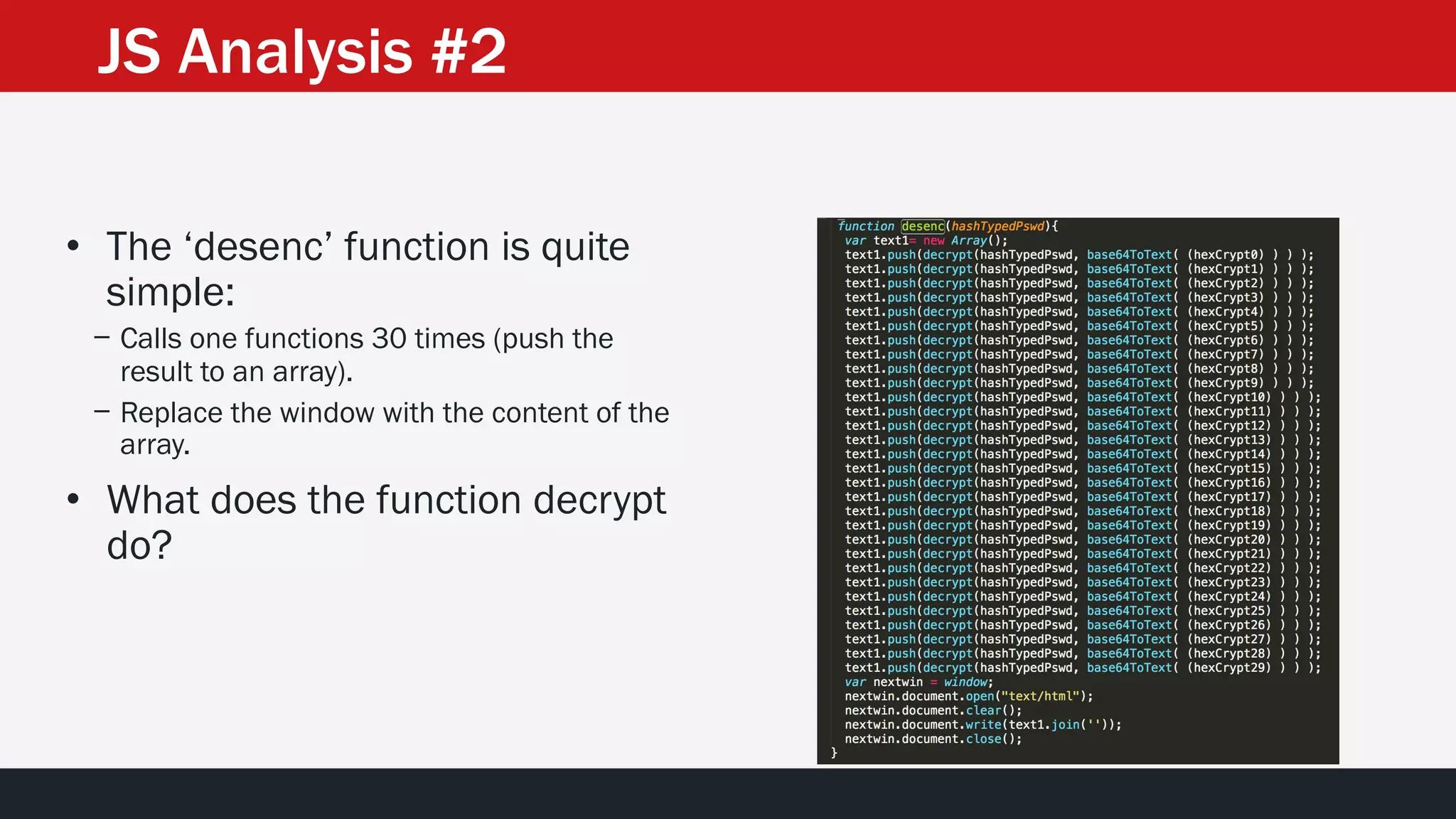
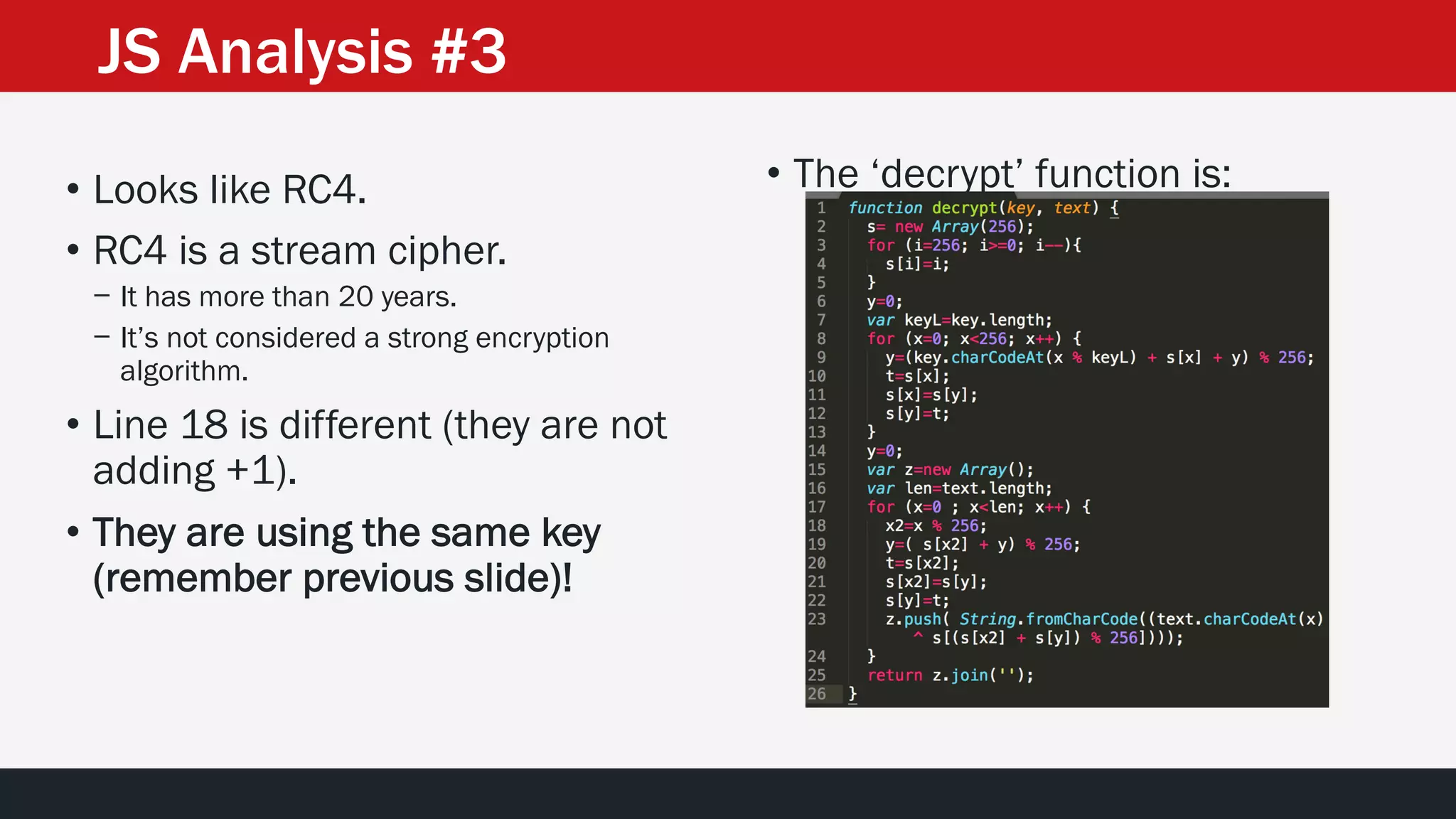
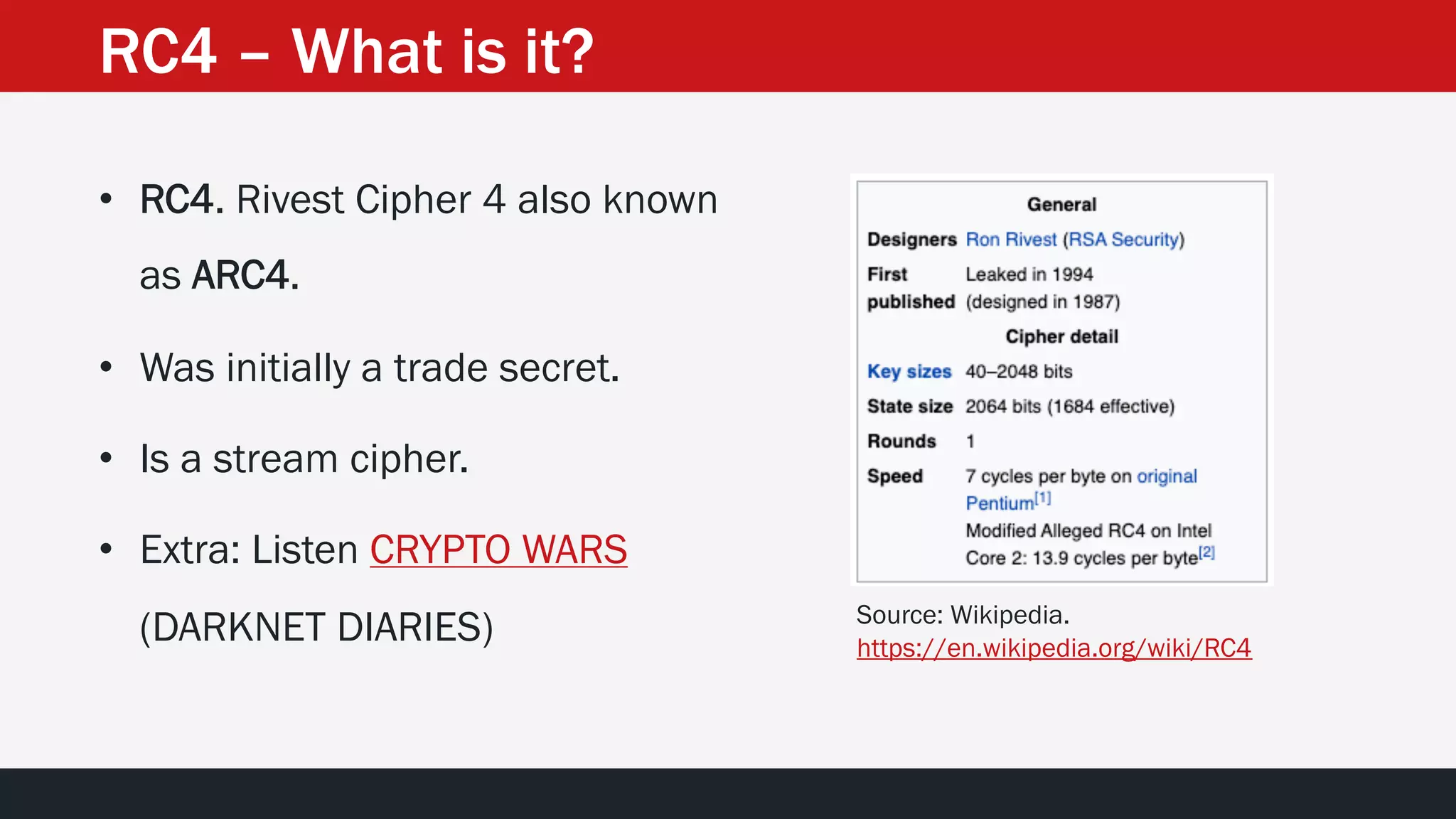
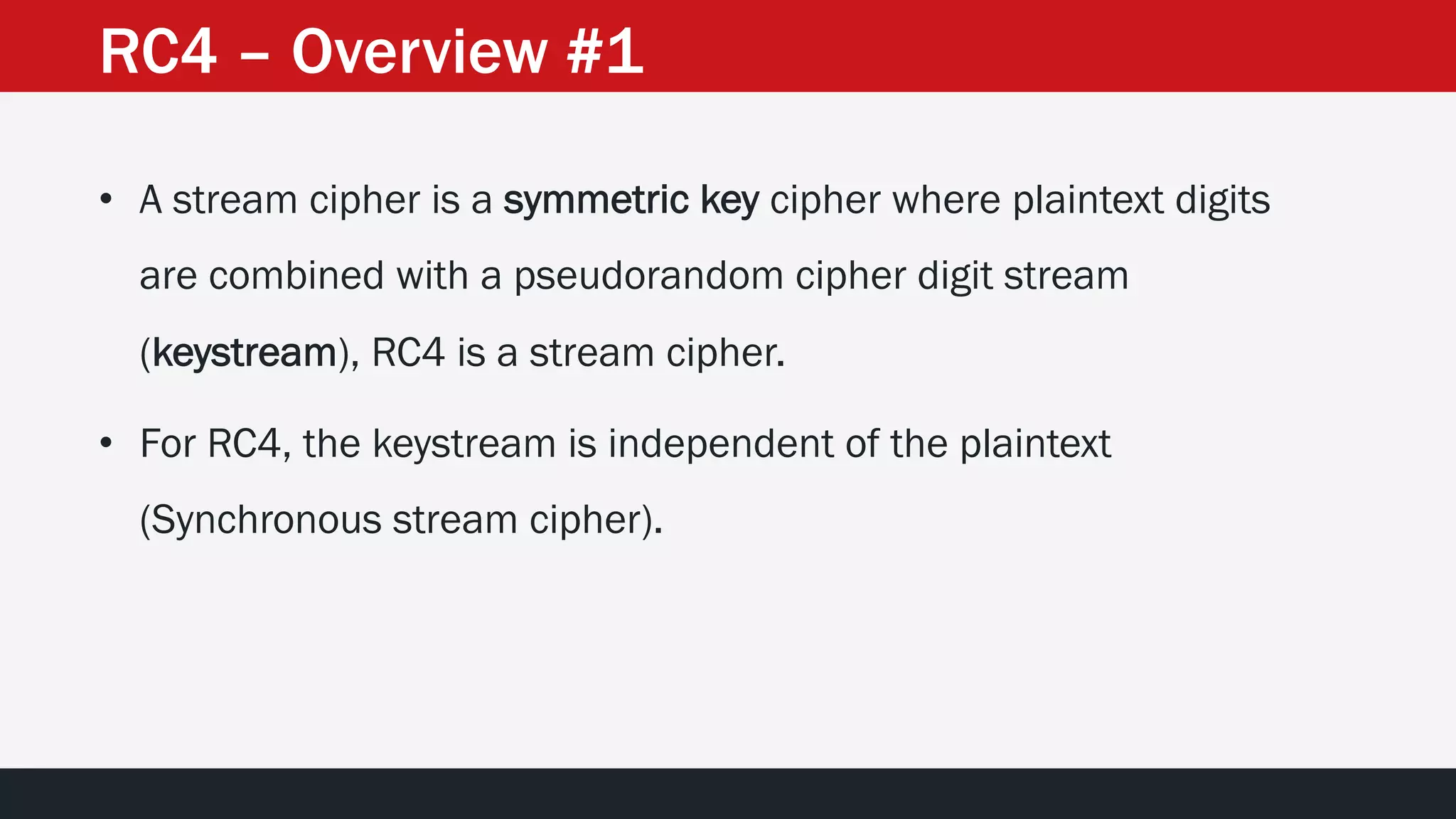
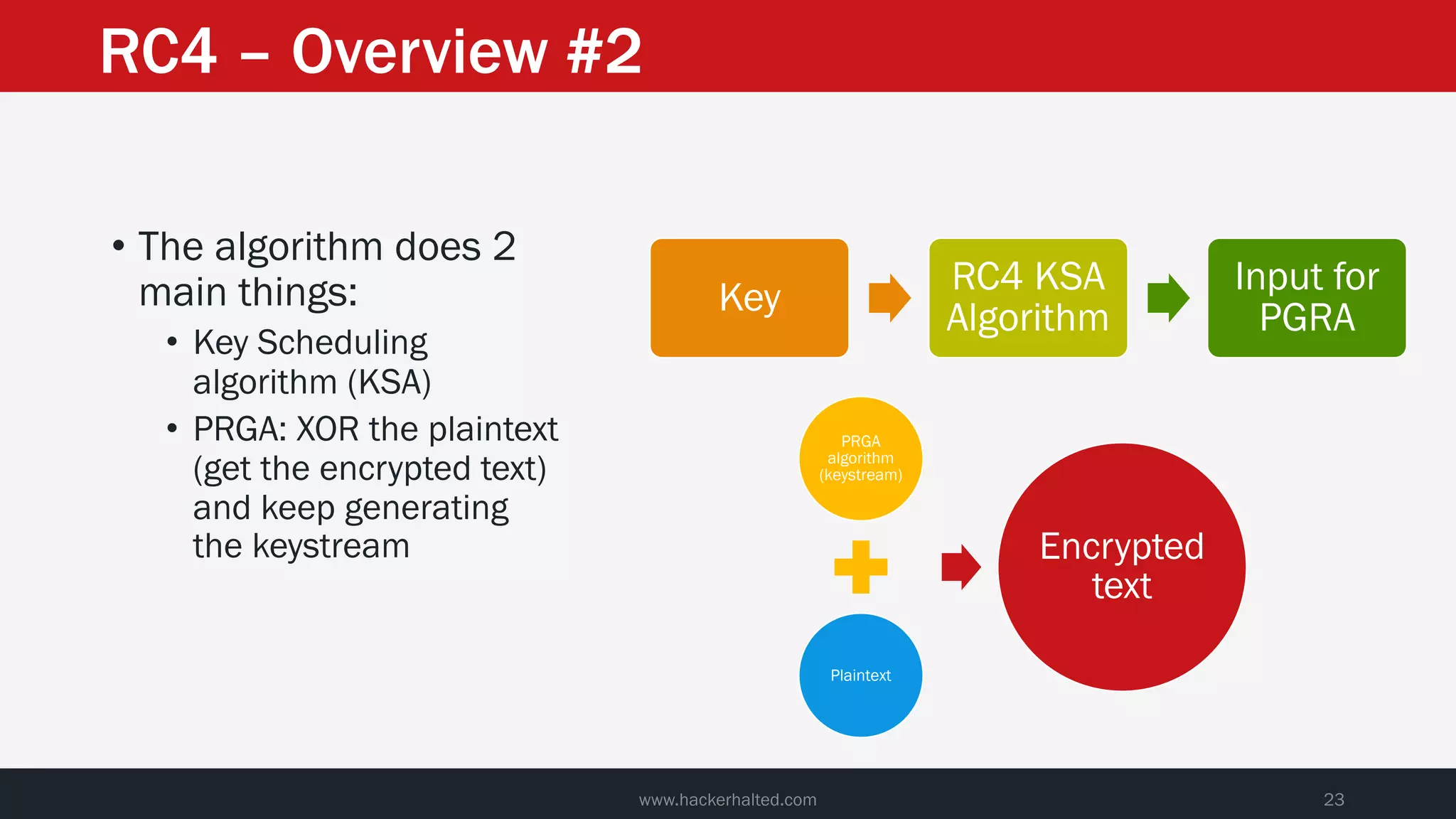
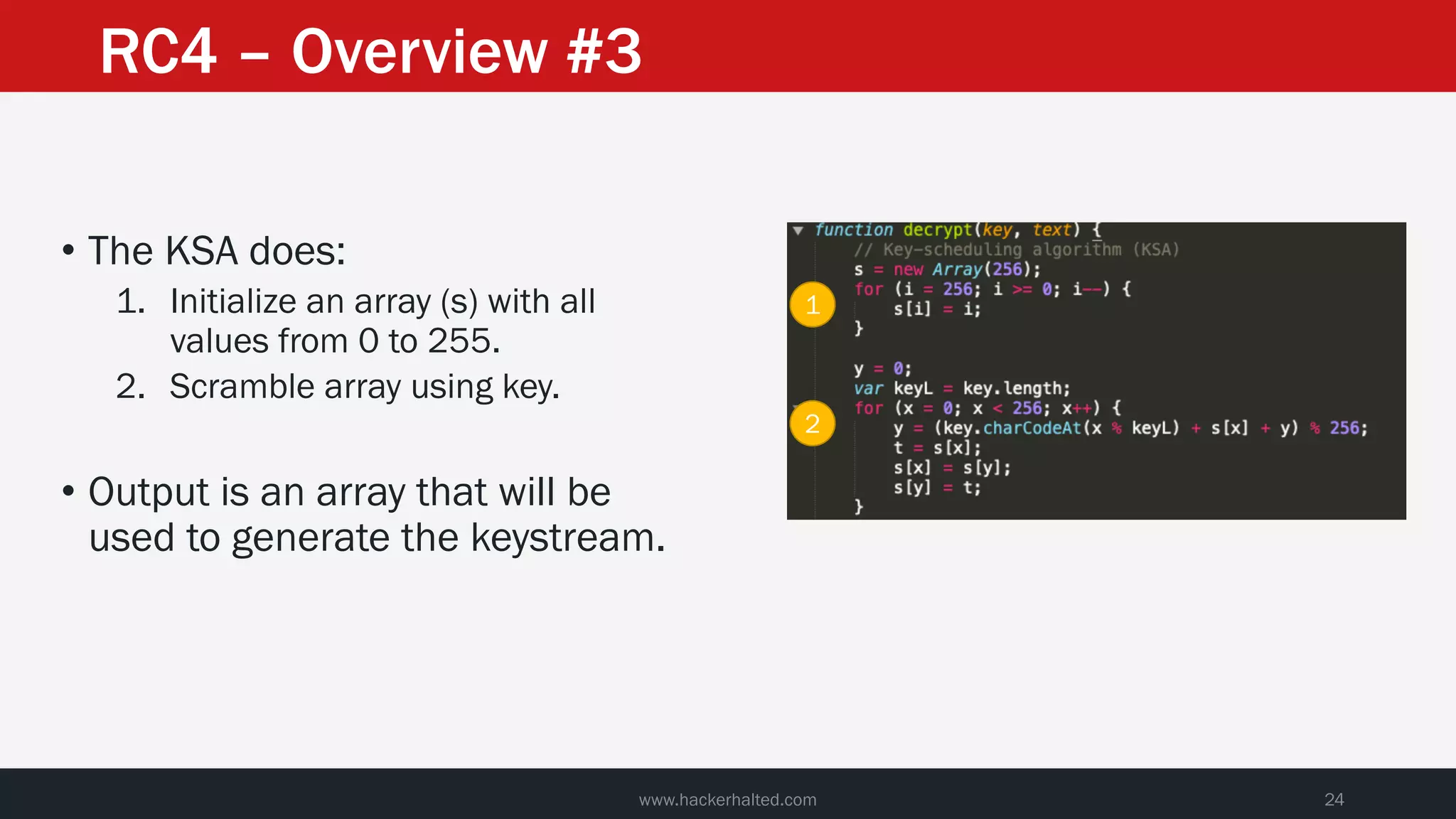
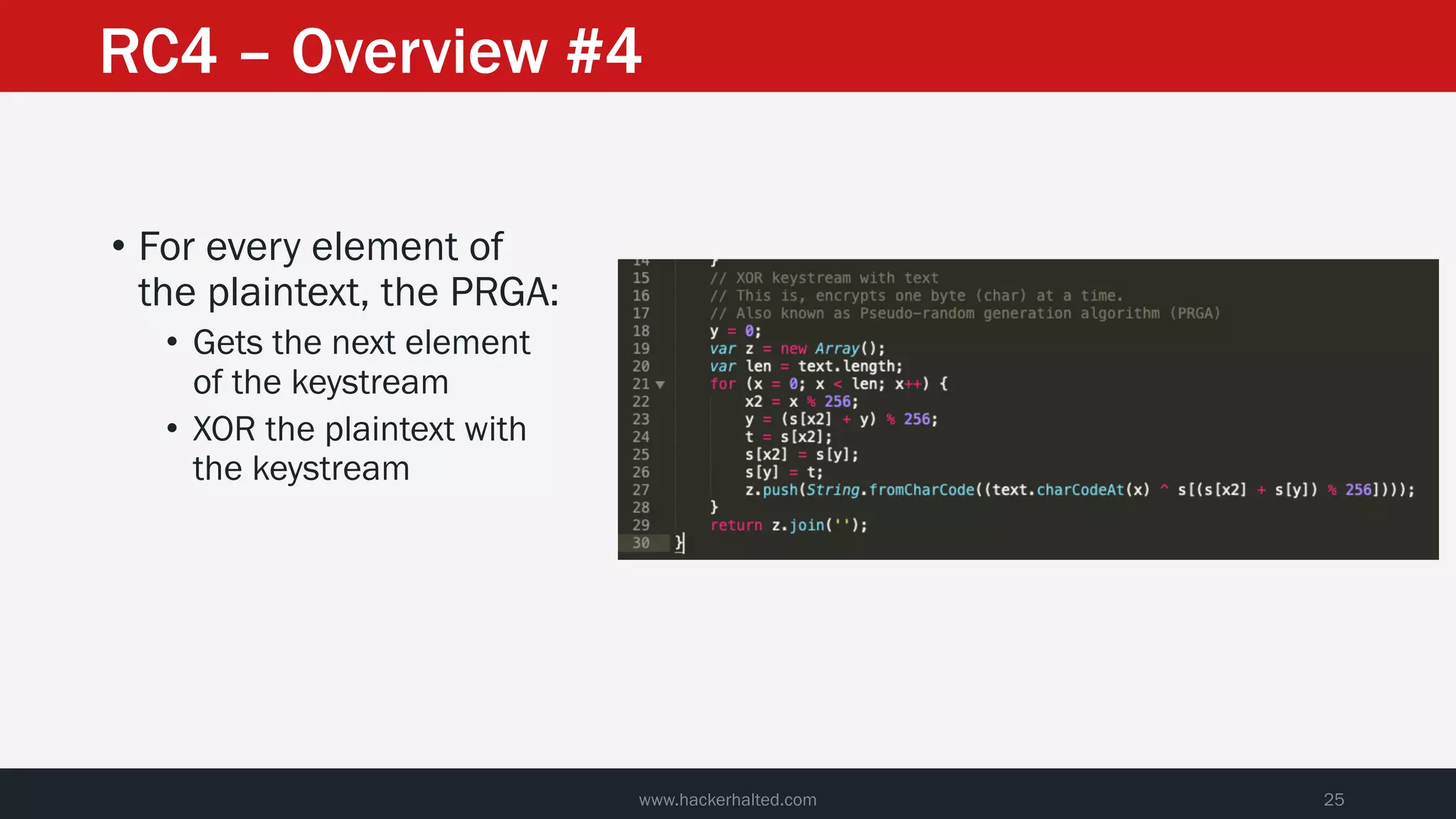
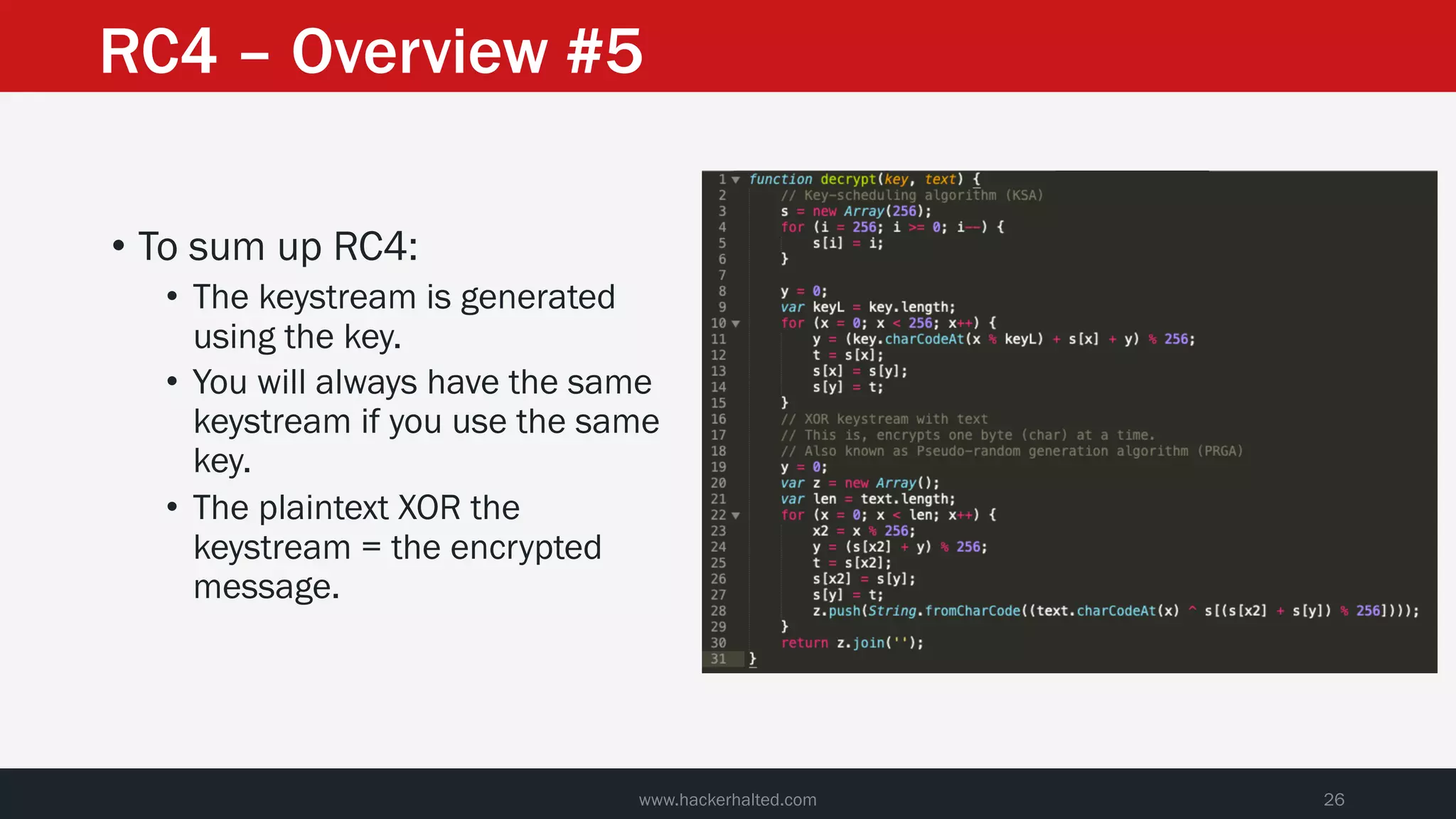
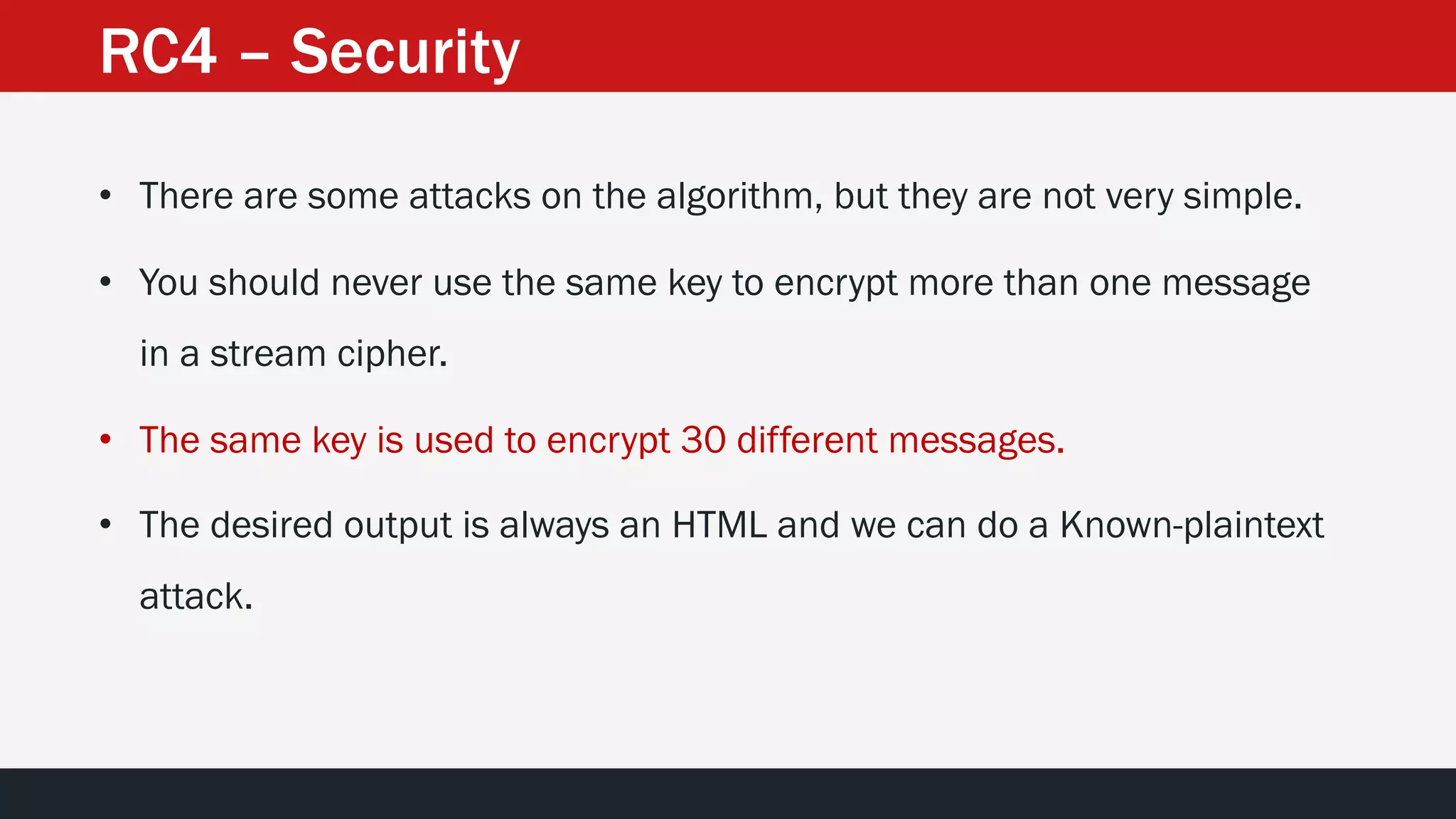
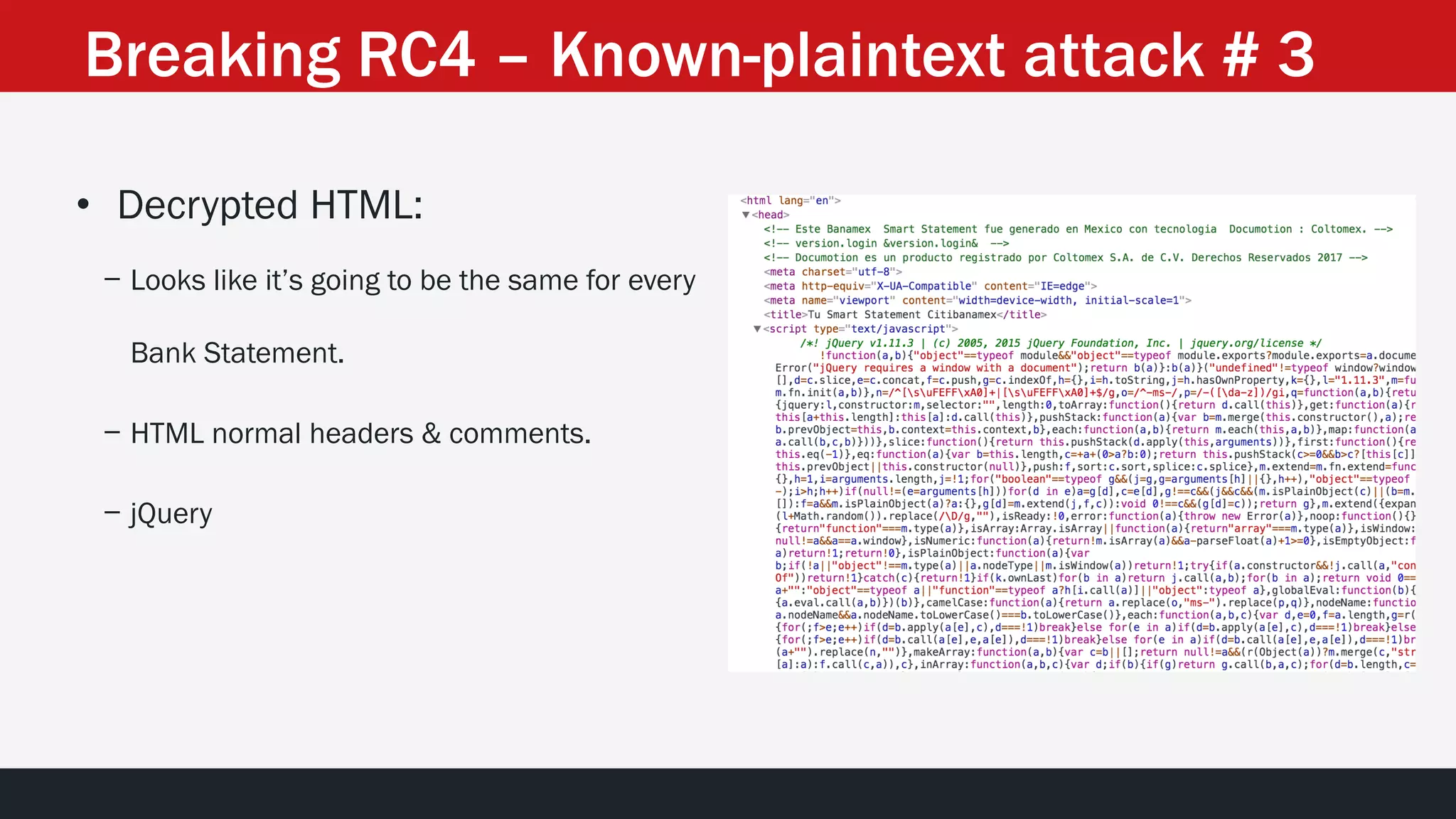
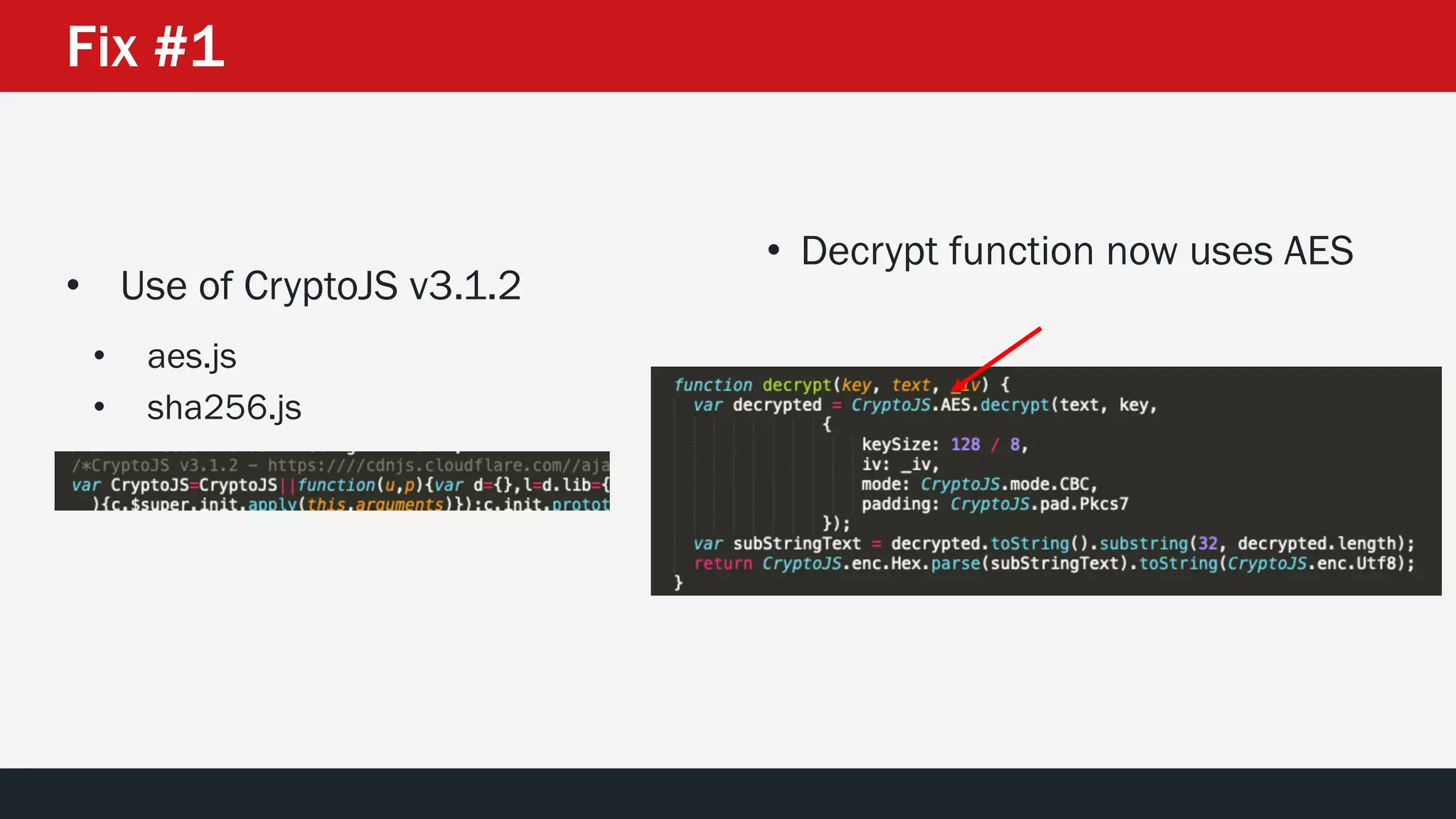
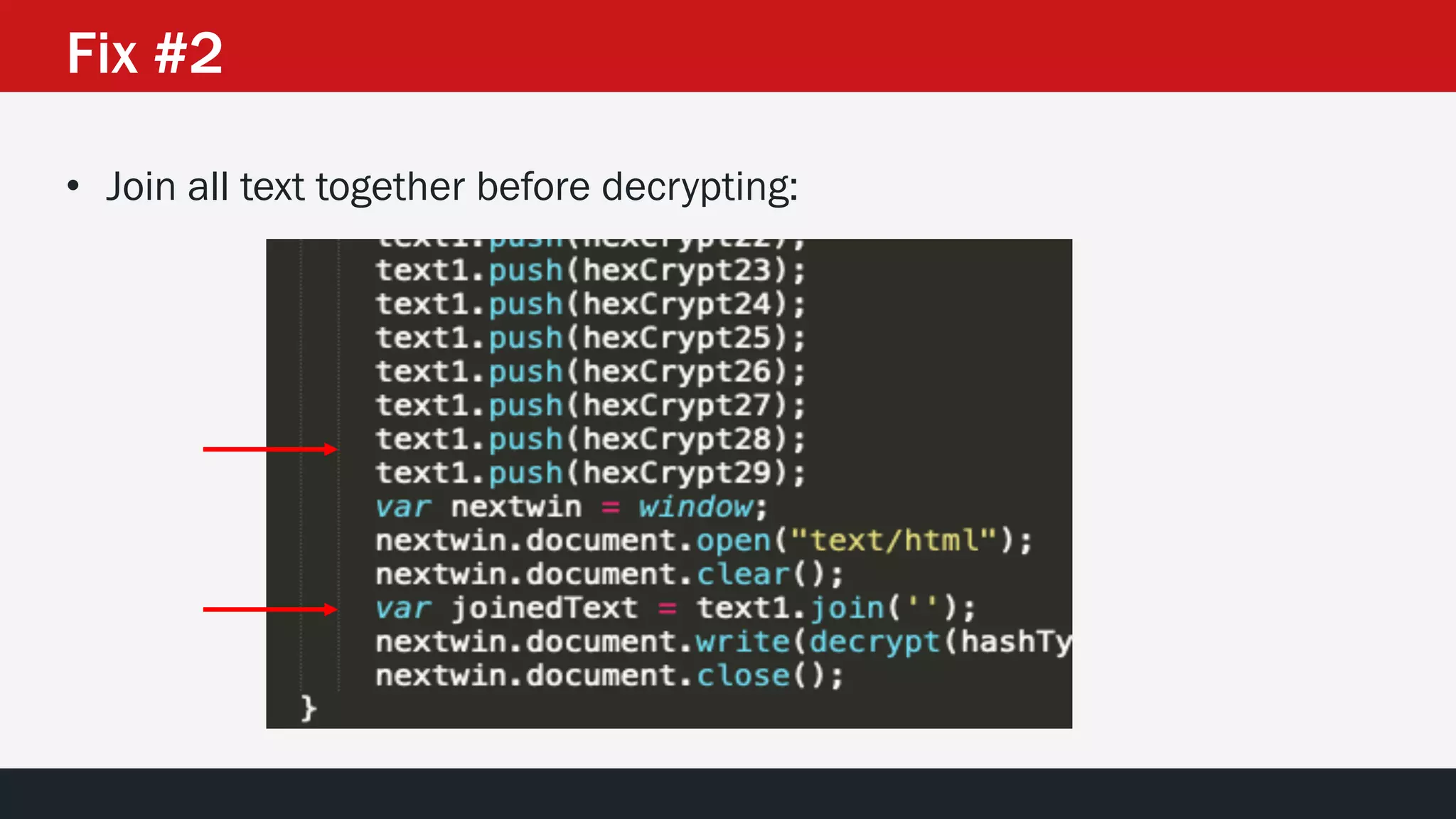
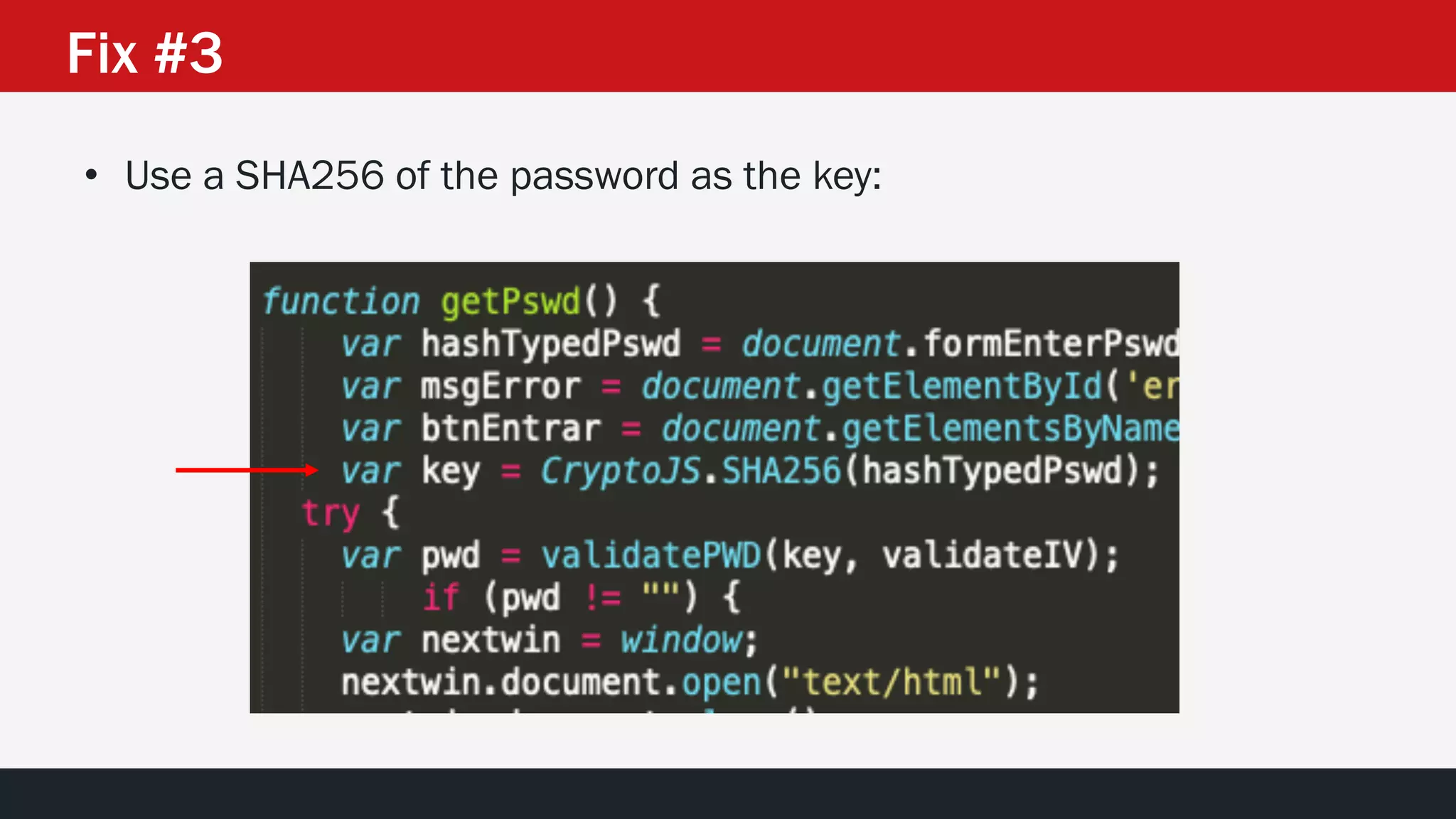
The document discusses the vulnerabilities in the smart bank statements provided by Citibanamex, focusing on how the encryption utilized (RC4) can be compromised through known-plaintext attacks. It details the process of analyzing the bank statement's HTML and JavaScript, revealing weak security practices such as the reuse of keys. The document concludes by recommending best practices for security, including the adoption of stronger encryption methods and ensuring no single key is reused across multiple messages.
![Breaking Smart [Bank] Statements
How to read a Bank Statement without a password](https://image.slidesharecdn.com/bankstatementhackerhalted2019-191031170529/75/Breaking-Smart-Bank-Statements-Hacker-Halted-2019-Manuel-Nader-1-2048.jpg)




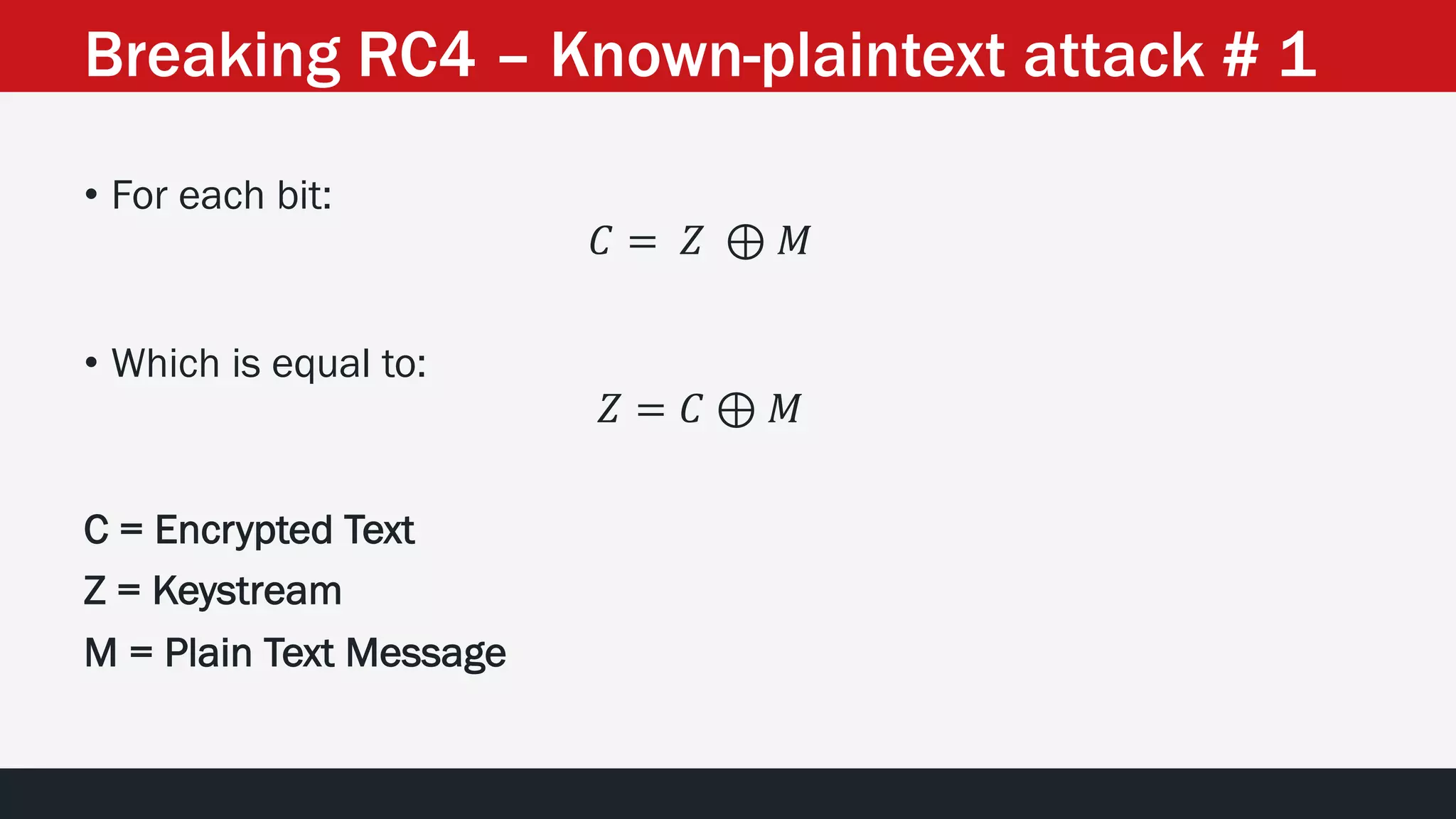
![• We have the Encrypted Message and it is split in ~30 variables [for
our convenience].
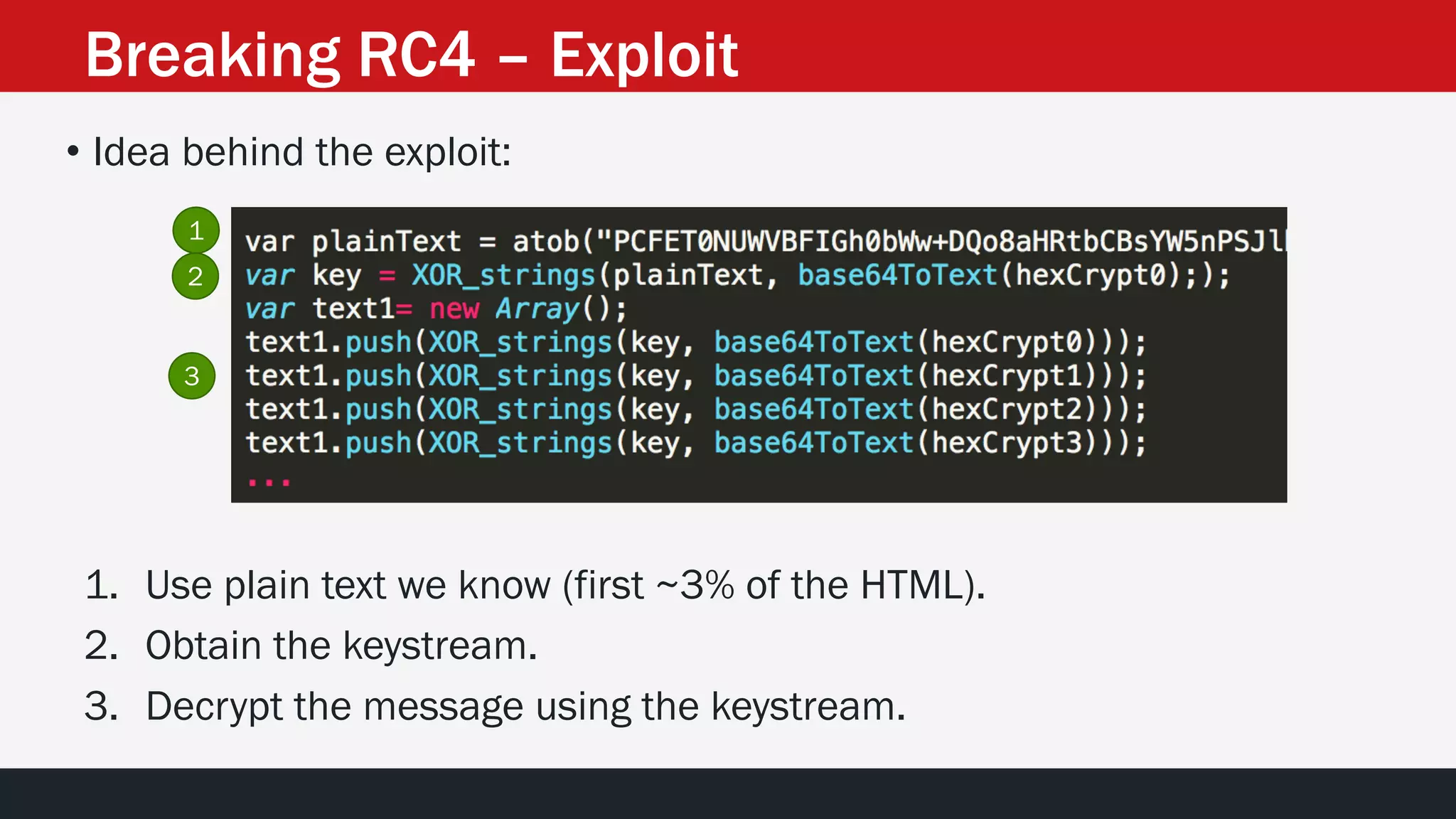
• Could we obtain the Keystream?
• Could we obtain the complete plain text?
Breaking RC4 – Known-plaintext attack # 2](https://image.slidesharecdn.com/bankstatementhackerhalted2019-191031170529/75/Breaking-Smart-Bank-Statements-Hacker-Halted-2019-Manuel-Nader-29-2048.jpg)




![Breaking Smart [Bank] Statements – Hacker Halted 2019 – Manuel Nader](https://image.slidesharecdn.com/bankstatementhackerhalted2019-191031170529/75/Breaking-Smart-Bank-Statements-Hacker-Halted-2019-Manuel-Nader-43-2048.jpg)