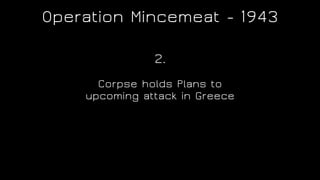
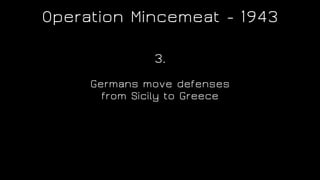
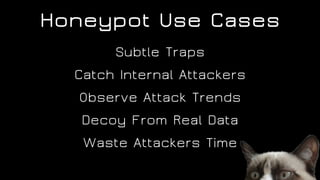
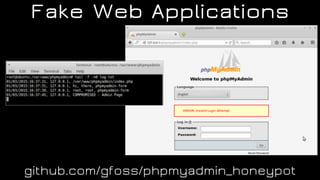
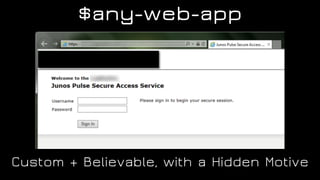
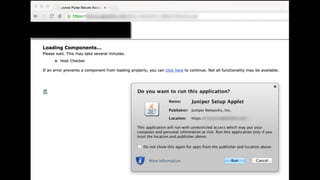
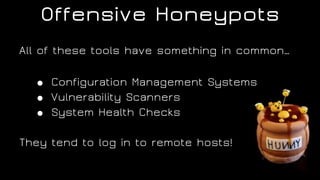
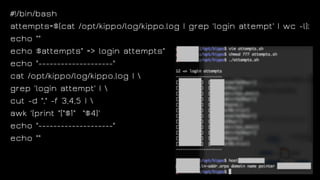
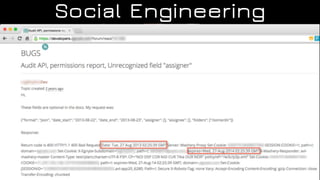
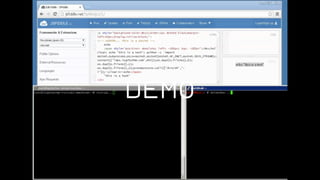
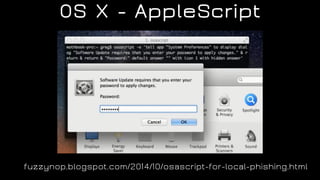
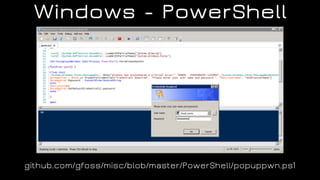
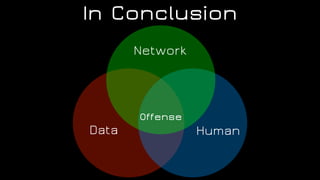
The document discusses the application of diversion and deception strategies in cybersecurity, aligning historical warfare tactics with modern information security practices. It emphasizes the importance of using honeypots, social engineering, and red teaming to distract and mislead potential attackers. Key insights include the necessity for adequate secrecy and control over information channels, as well as implementing real-world awareness training for personnel.