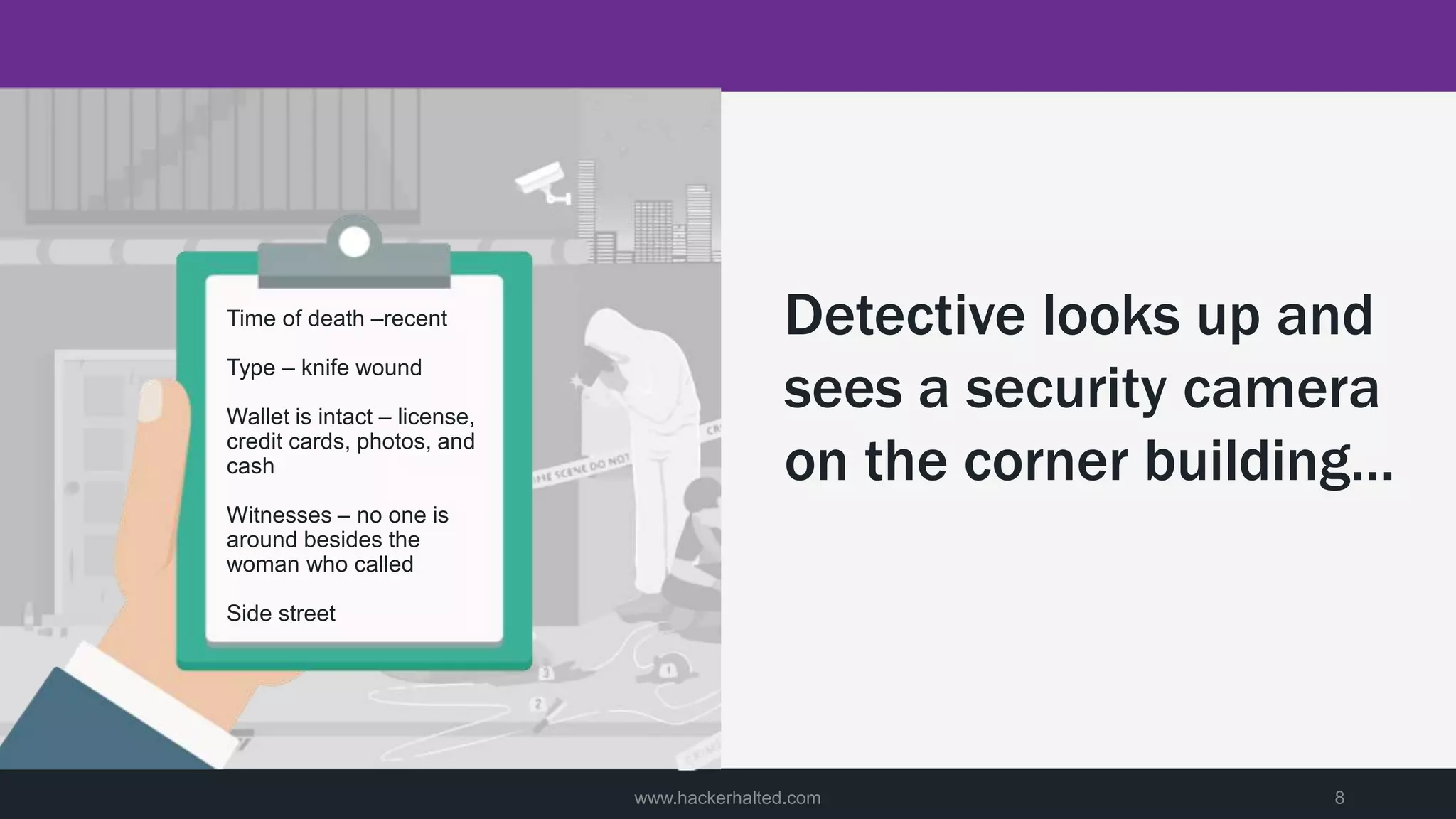
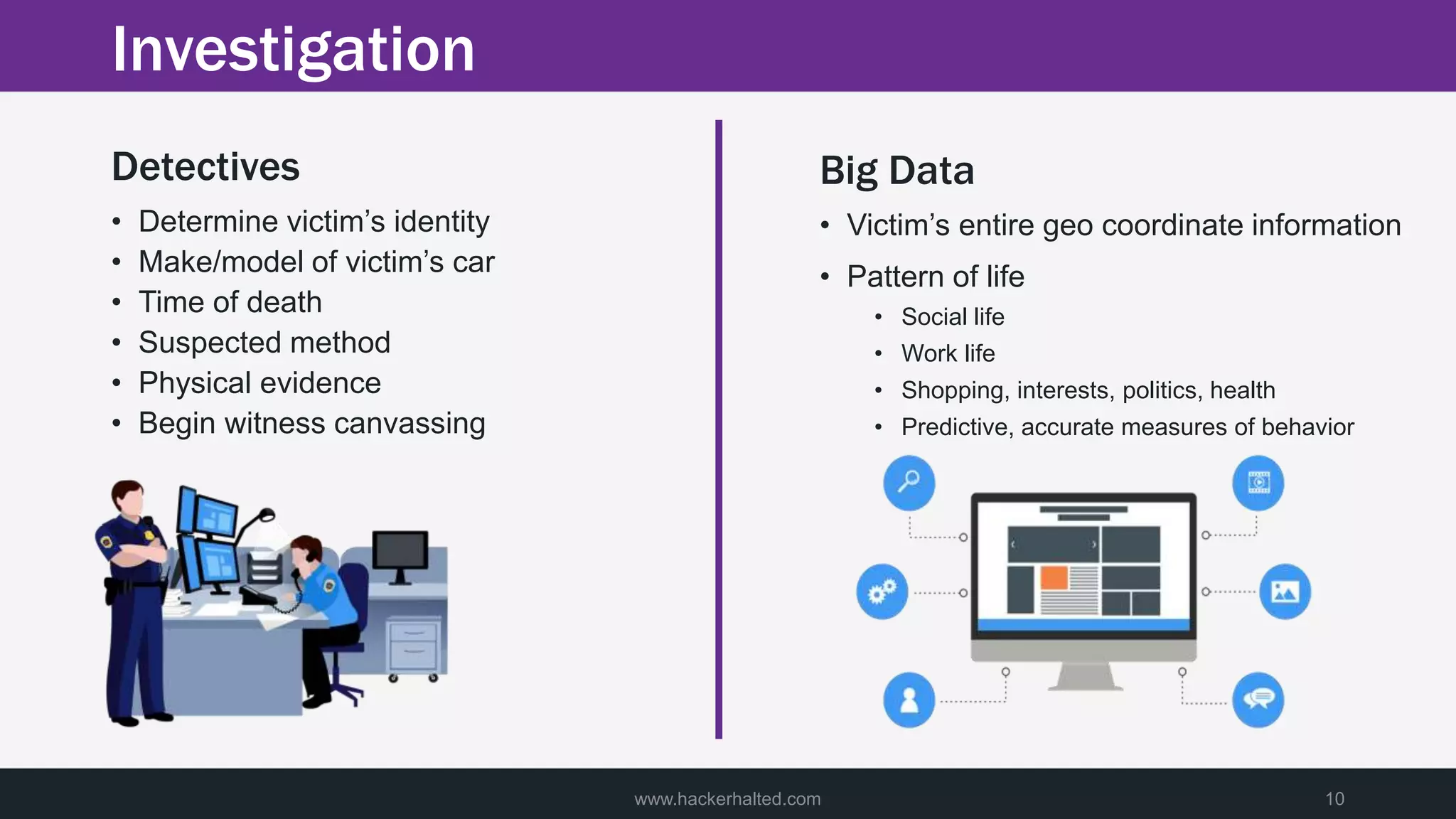
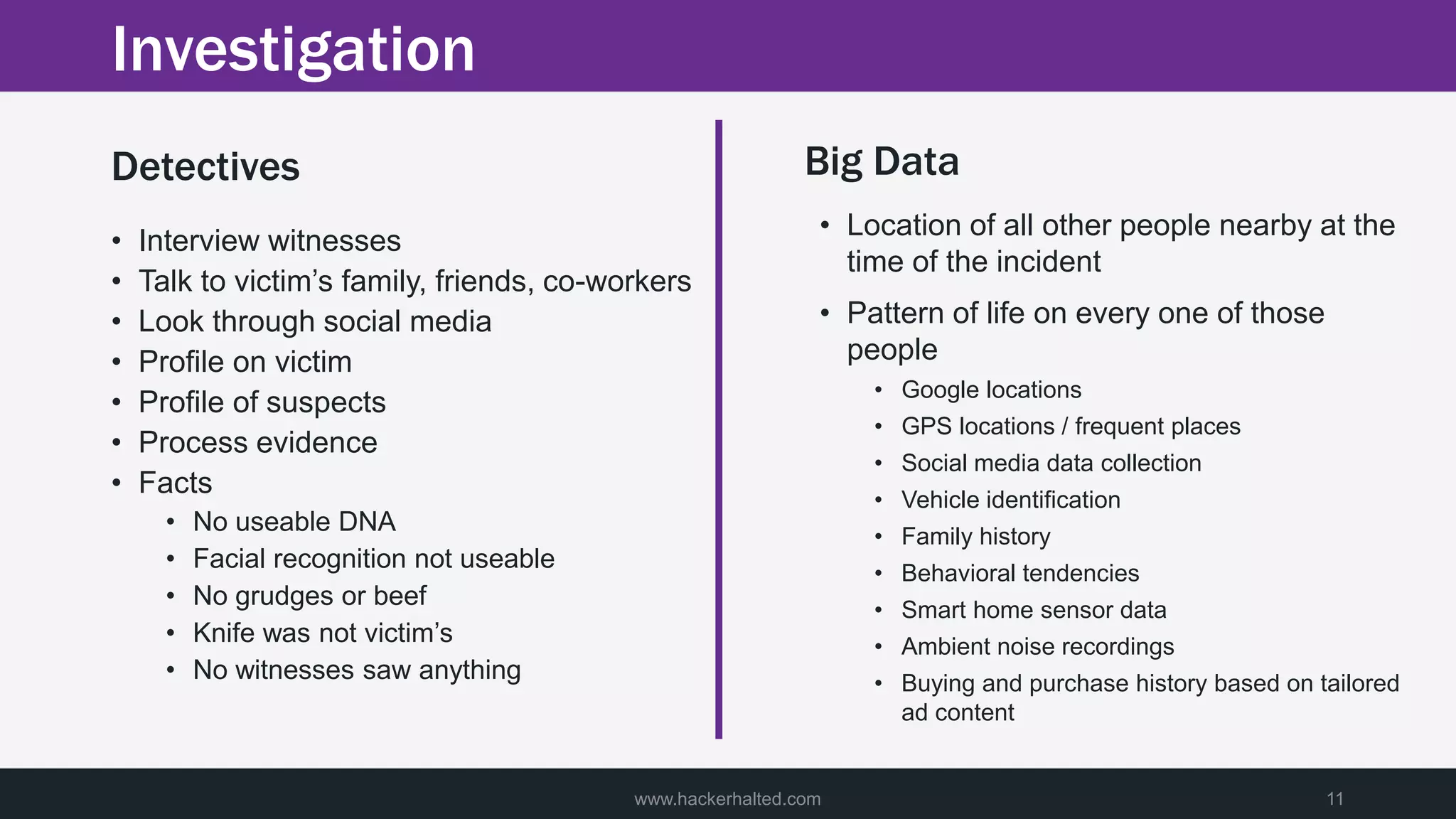
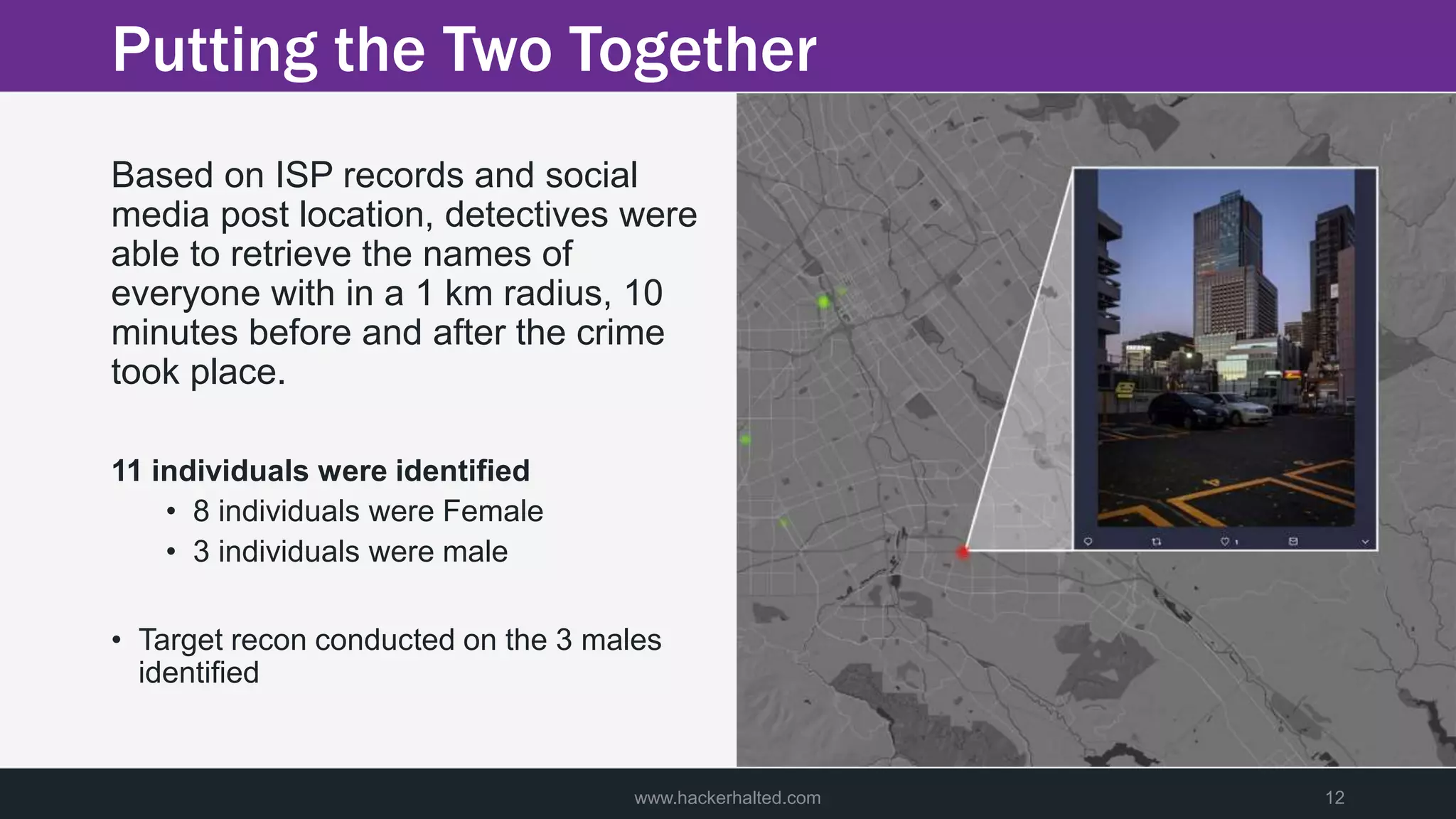
A man was discovered murdered on a street late at night. Police were called to the scene and began their investigation. They found limited clues but saw footage of a potential suspect. Detectives then used big data analytics to identify individuals near the crime scene around the time of the murder. This led them to three male suspects. Further investigation of these suspects focused on building profiles of their patterns of life in hopes of identifying the killer.