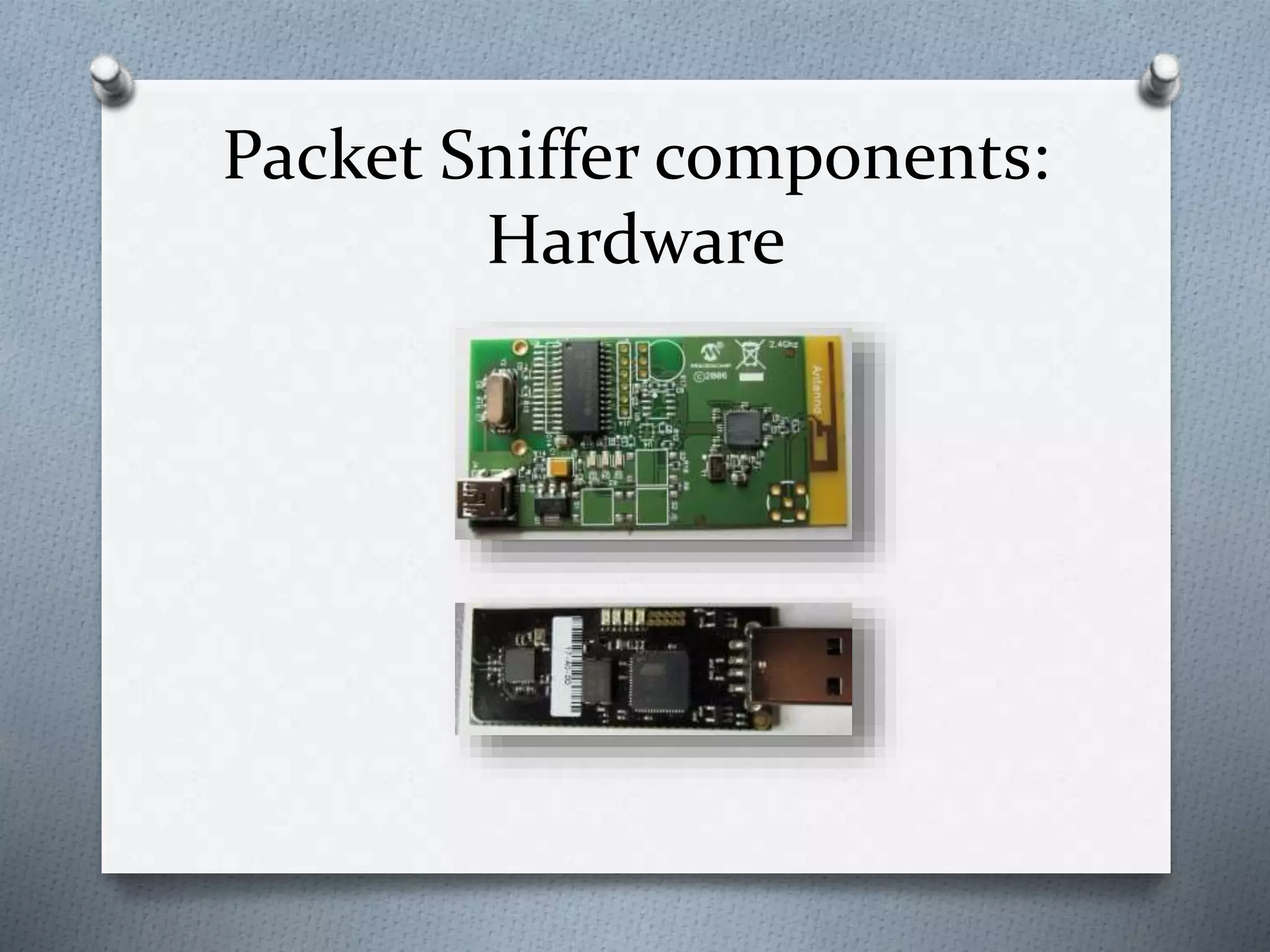
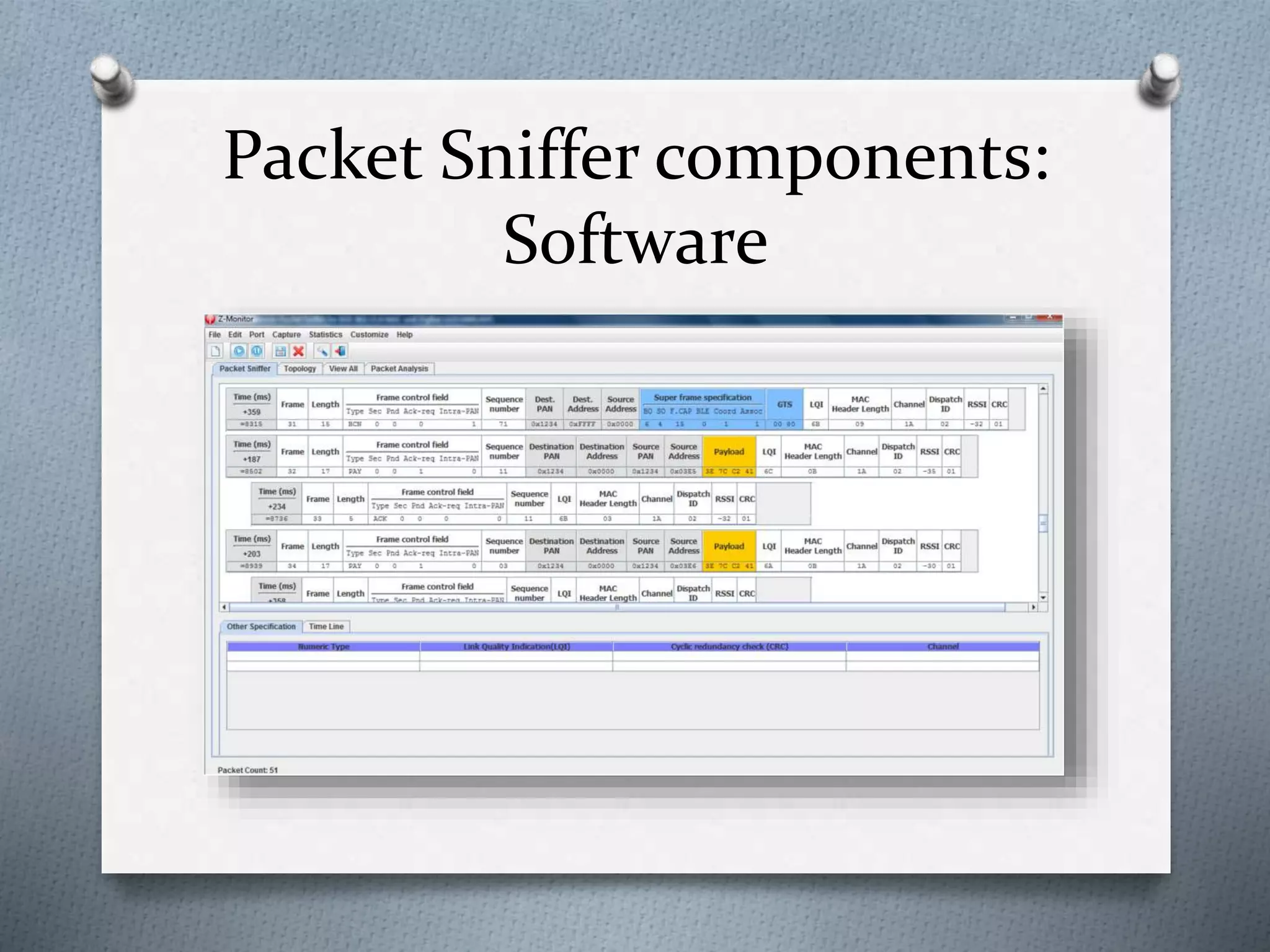
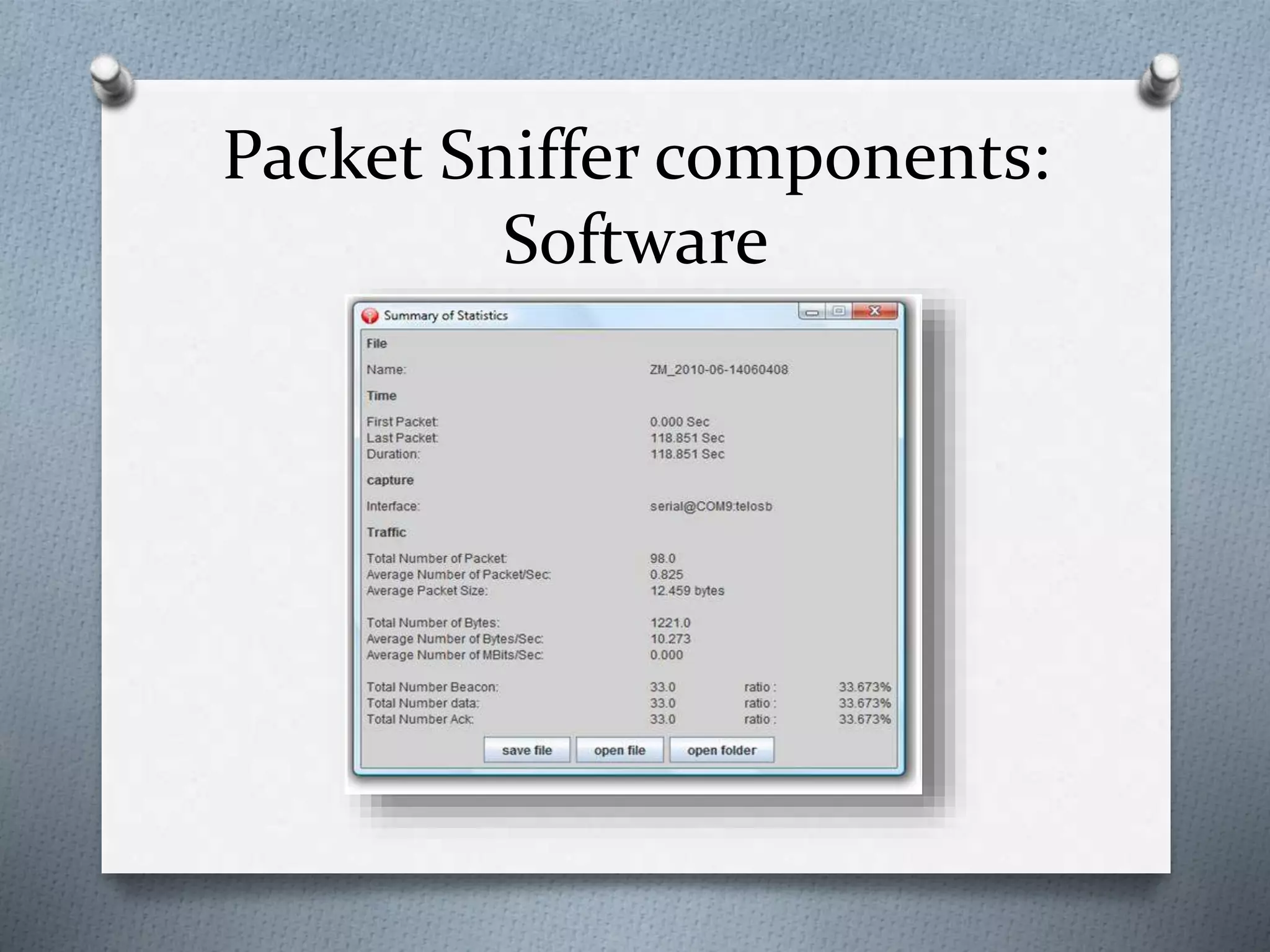
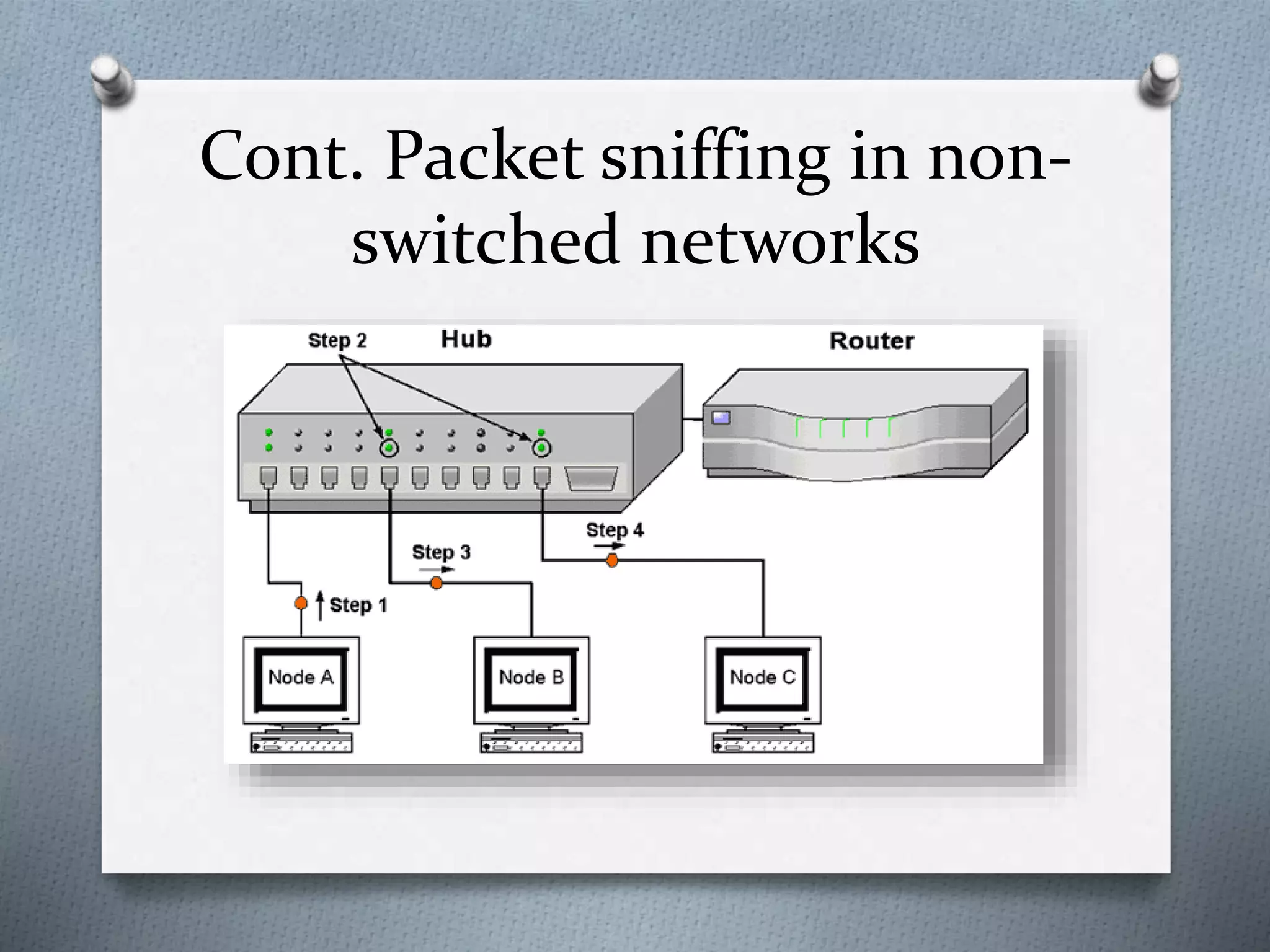
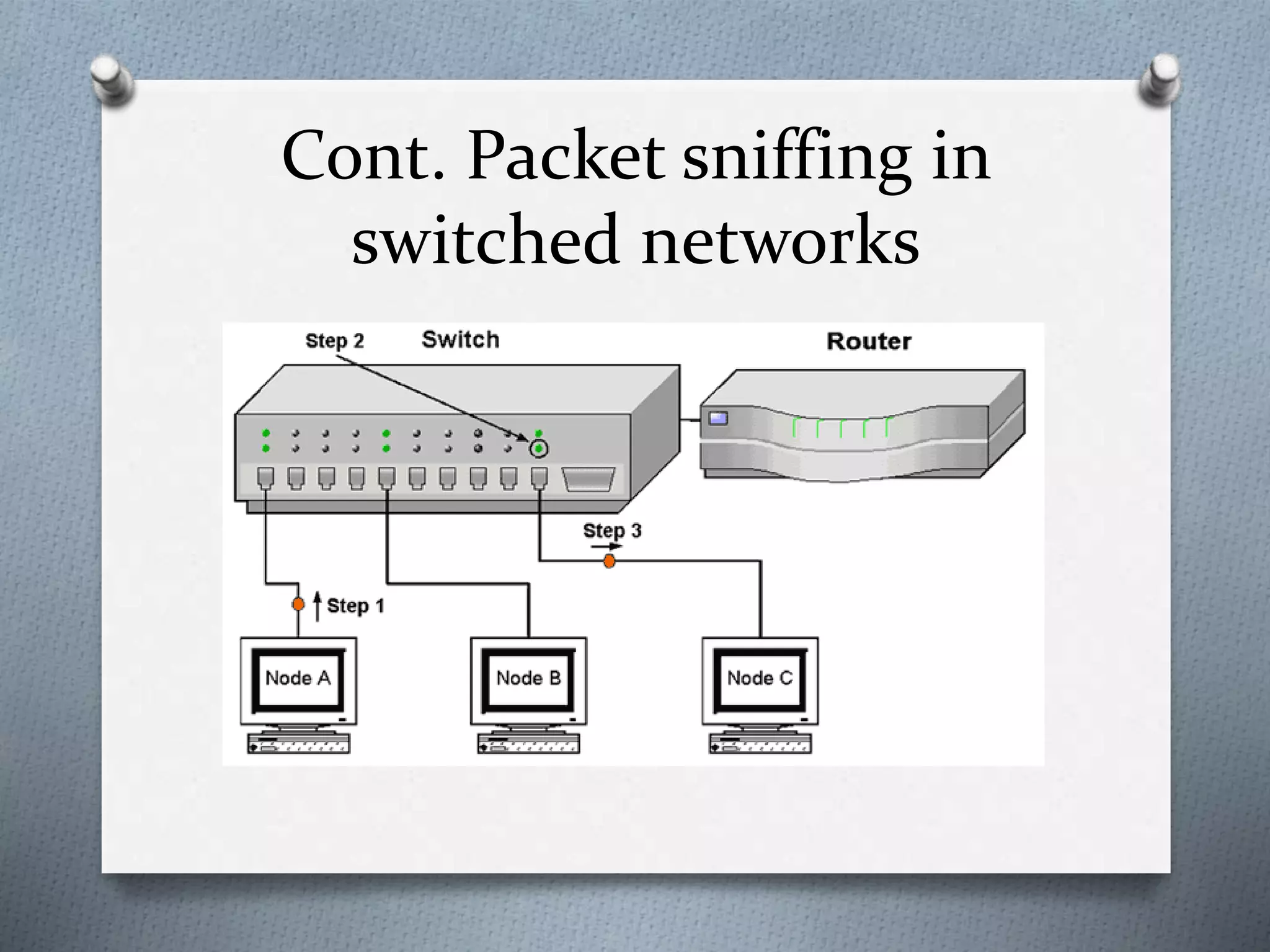
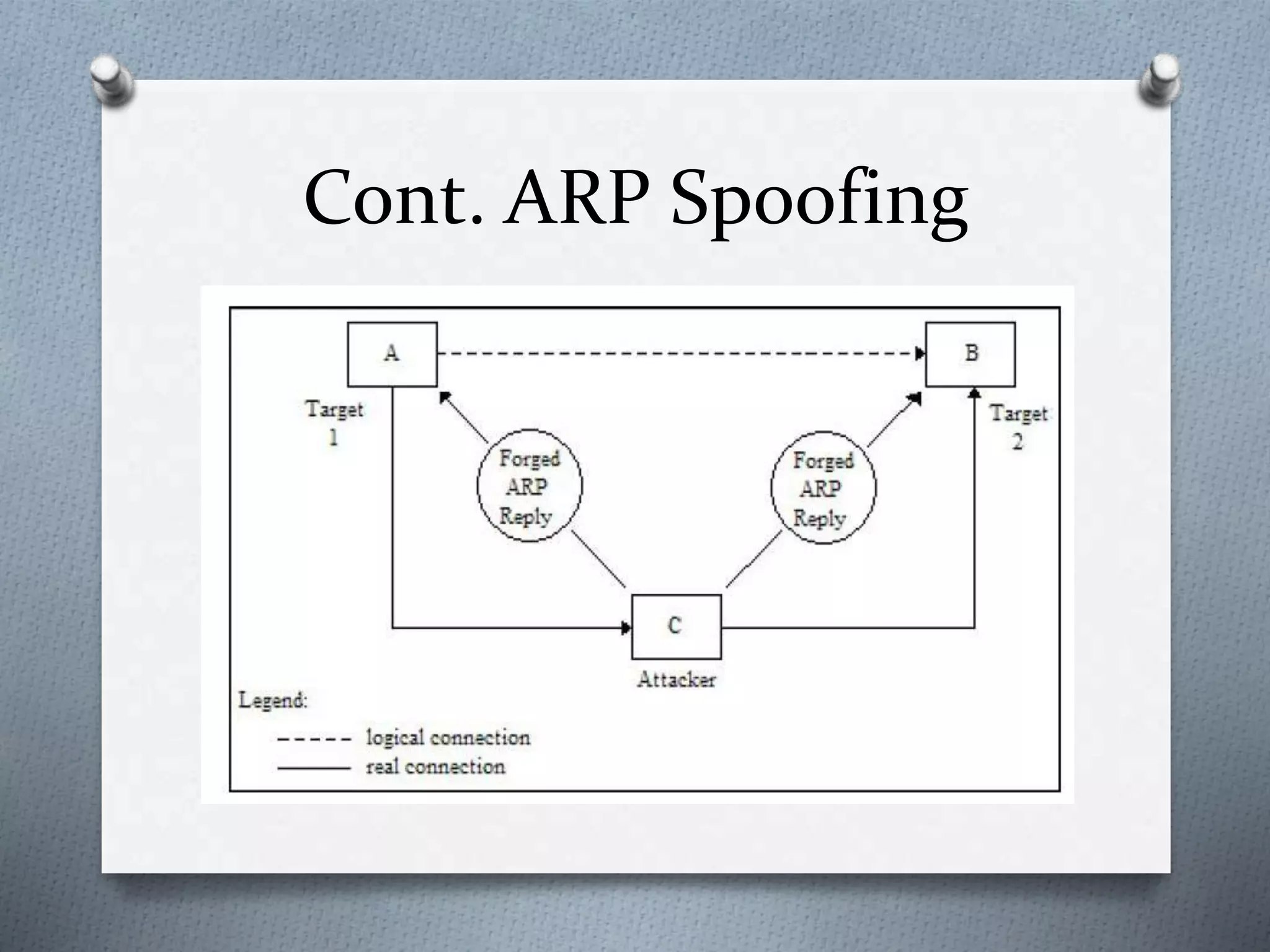
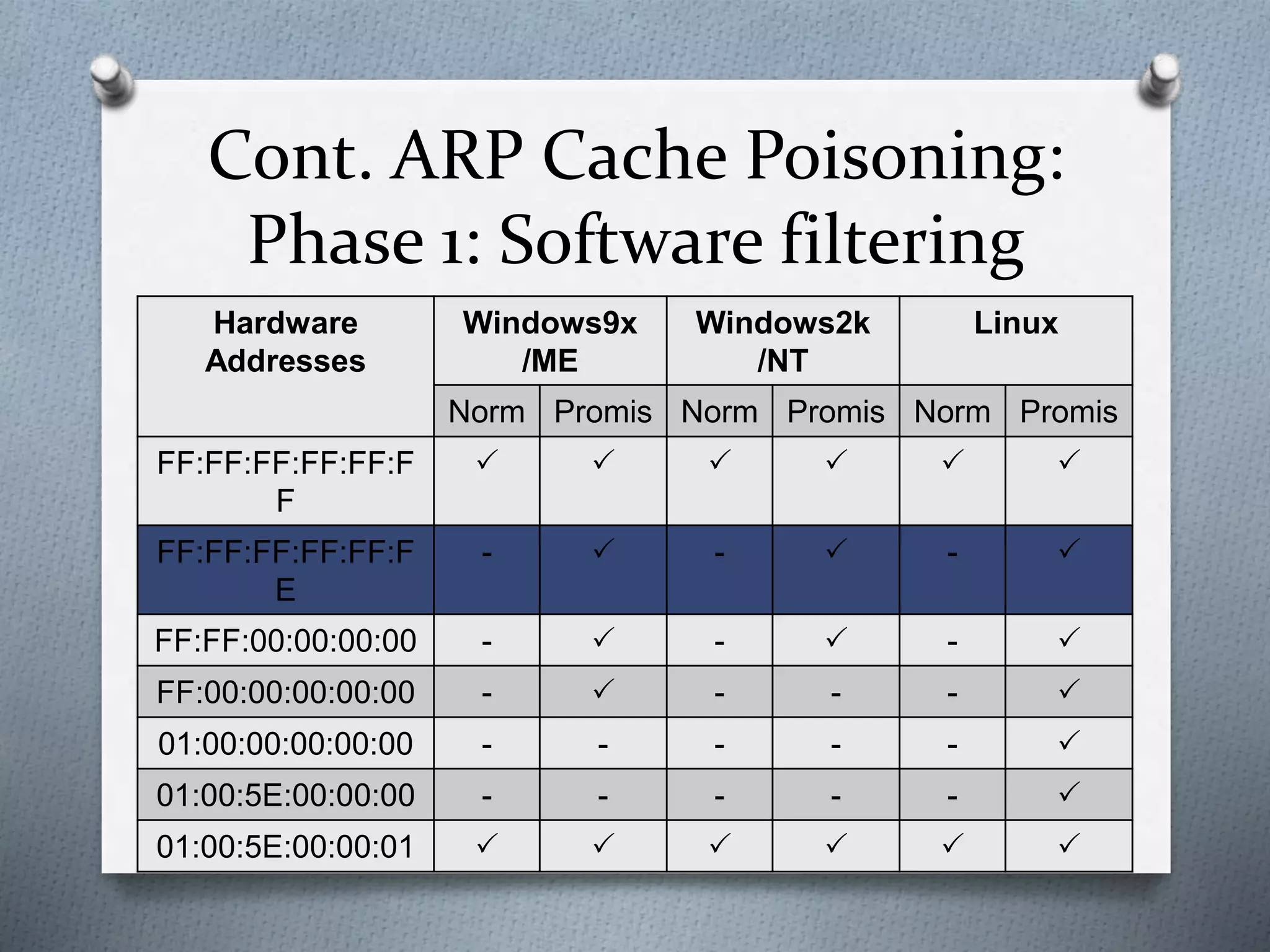
This document discusses packet sniffing in switched local area networks. It begins by defining packet sniffing and describing the differences between switched and hubbed networks. It then outlines several packet sniffing attacks like ARP spoofing and switch port stealing. The document also proposes methods for detecting packet sniffing like ARP cache poisoning and preventing it through techniques such as port security, authentication, encryption and secured protocols. It concludes by emphasizing that switched networks are still vulnerable to sniffing and that while no solution is perfect, networks can be protected.