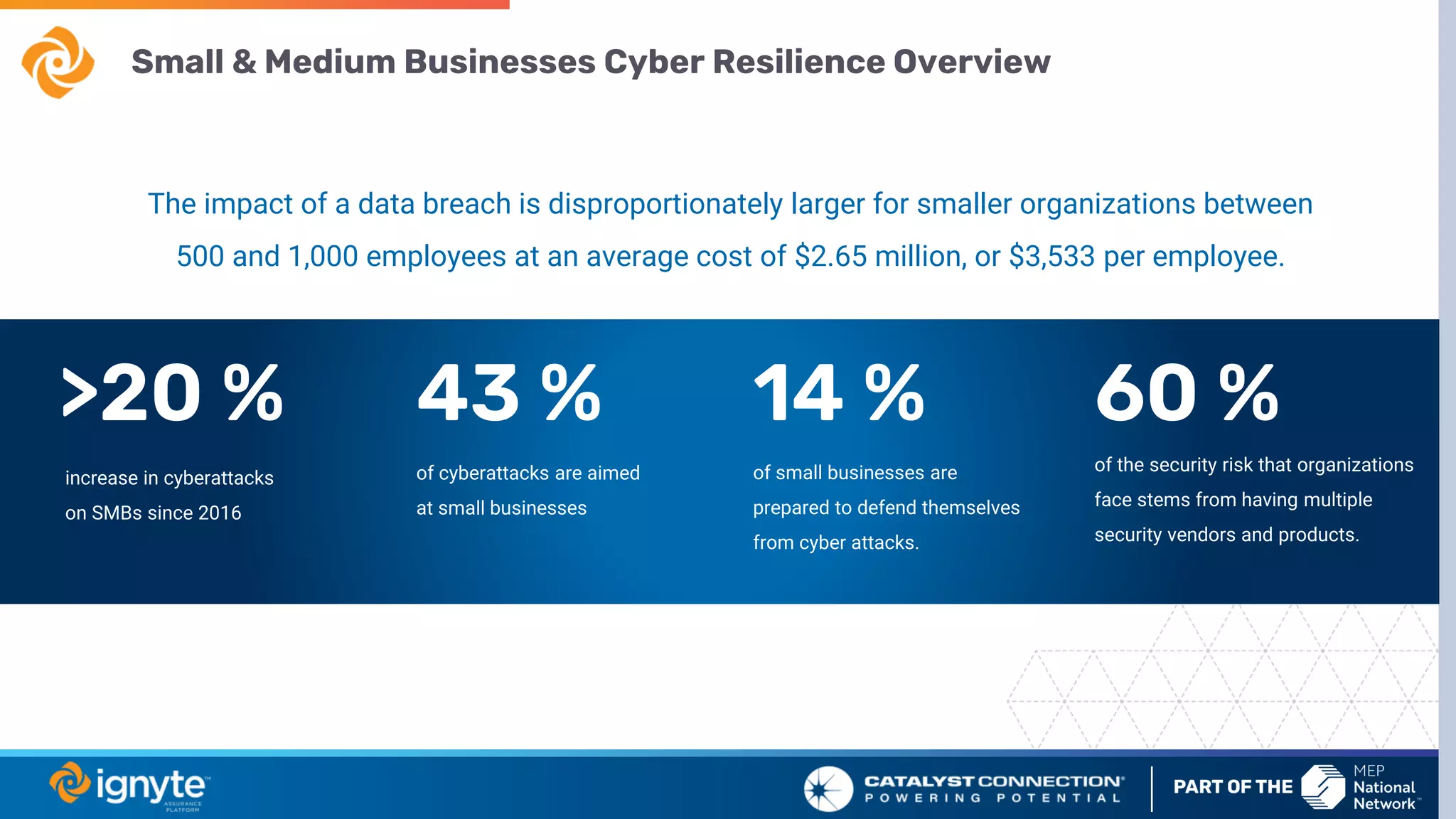
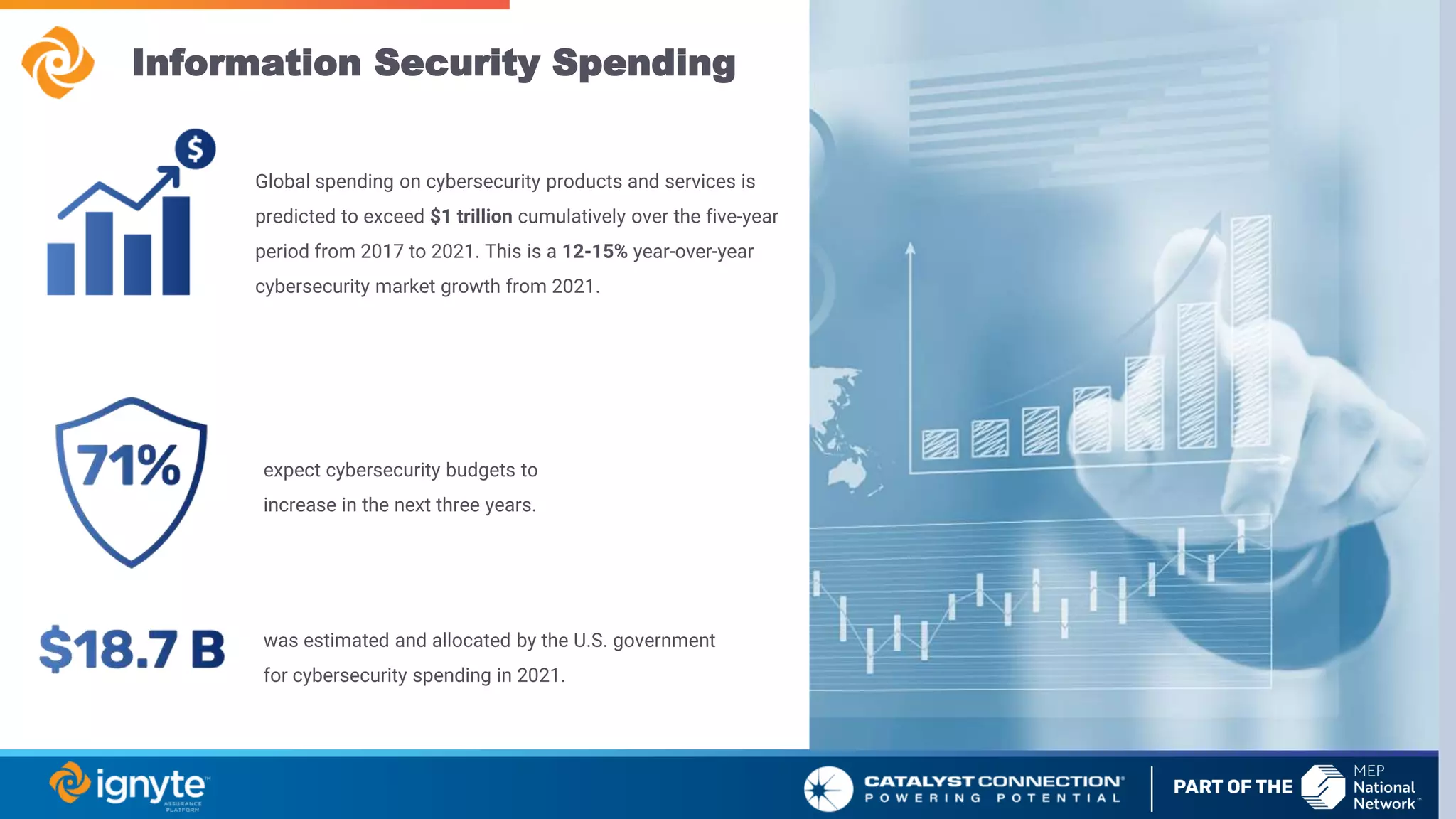
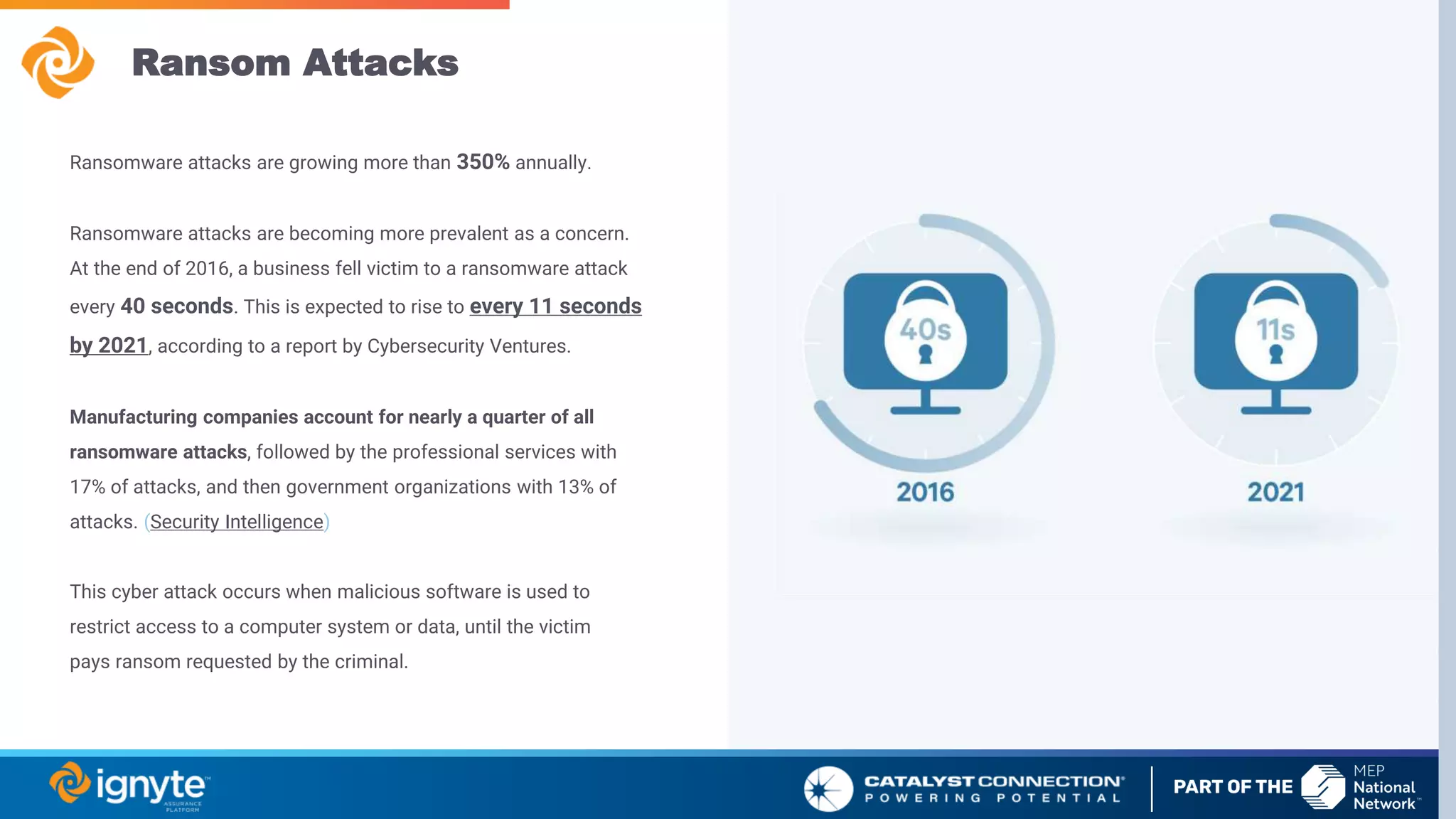
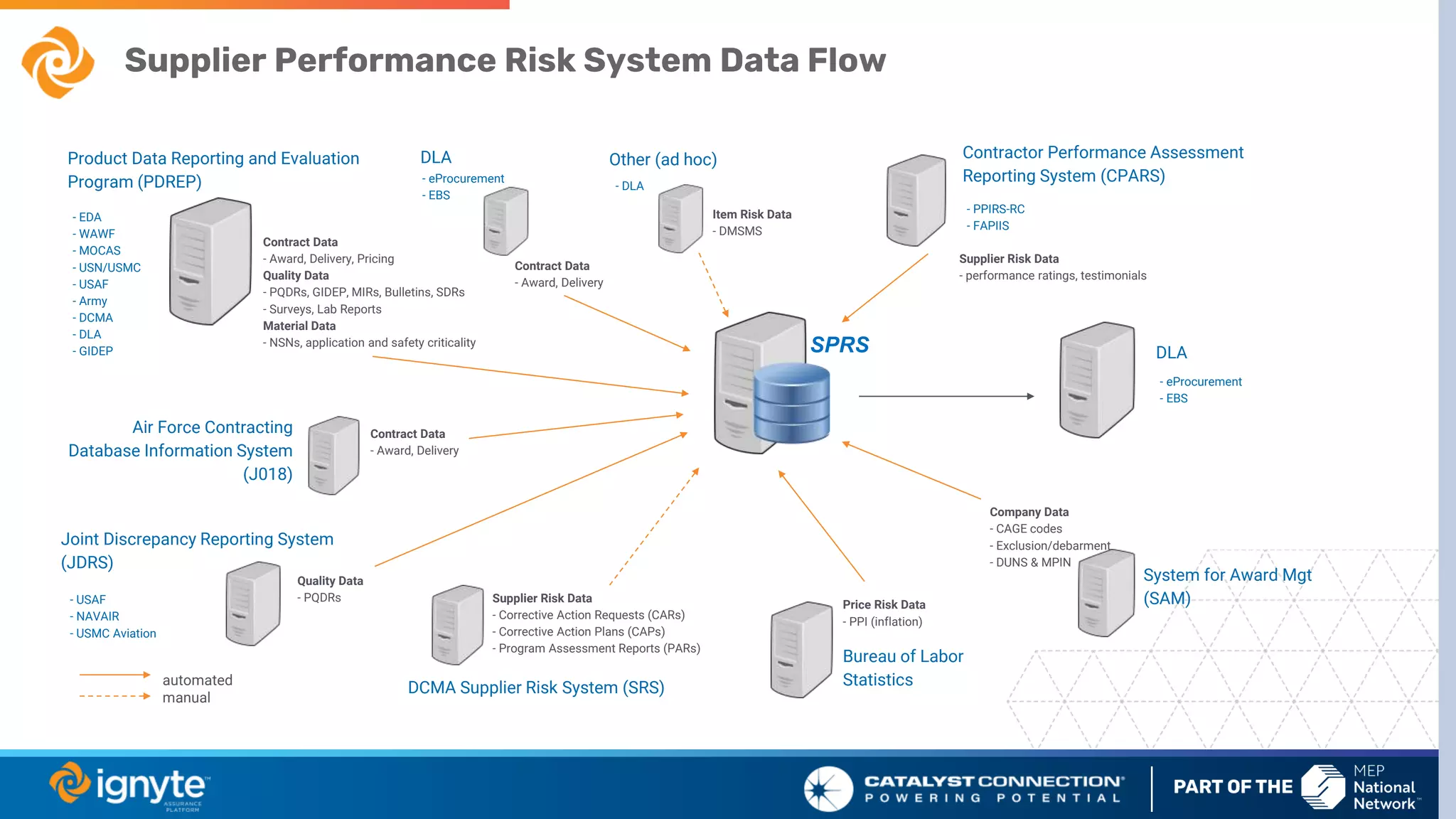
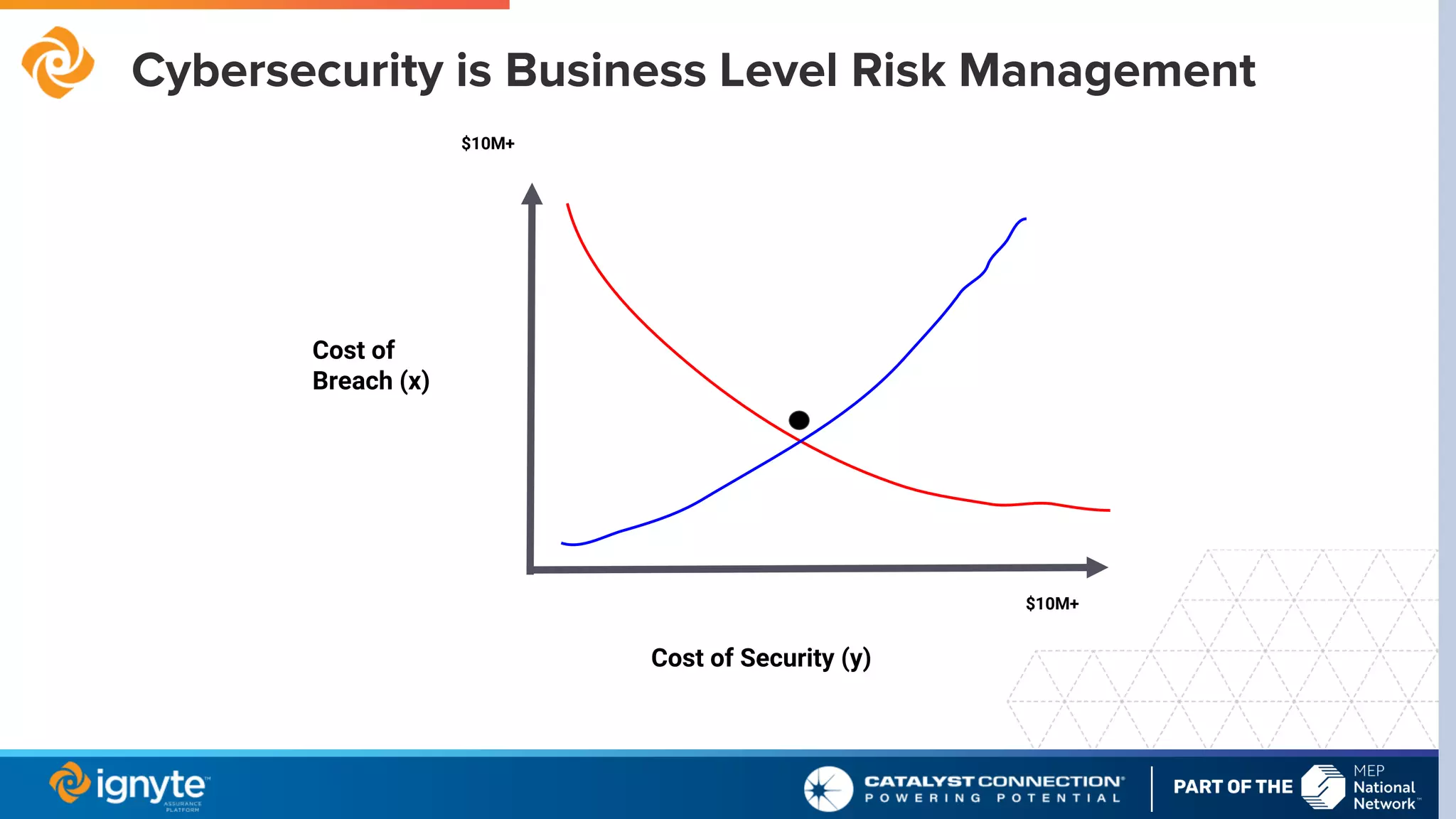
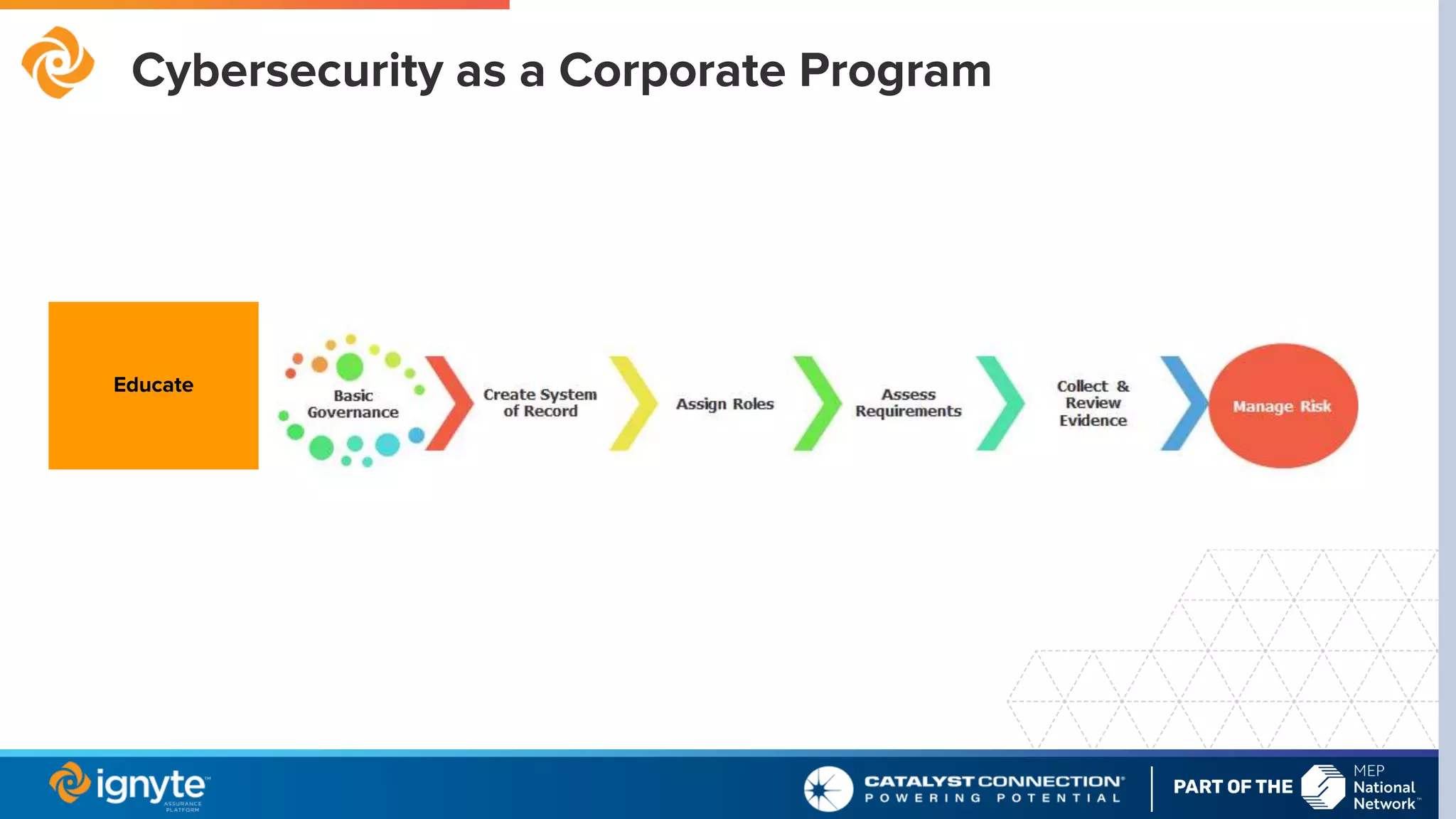
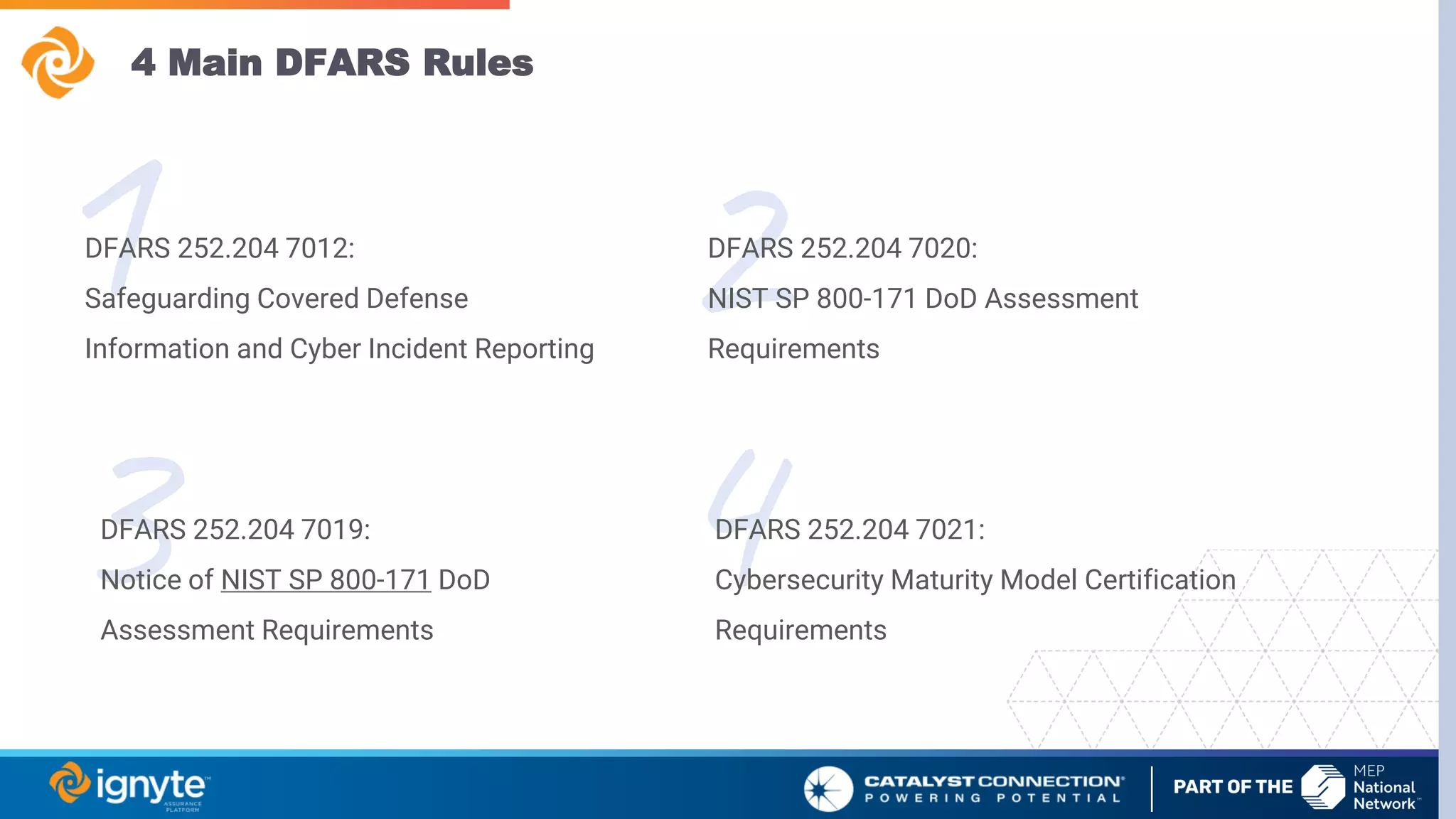
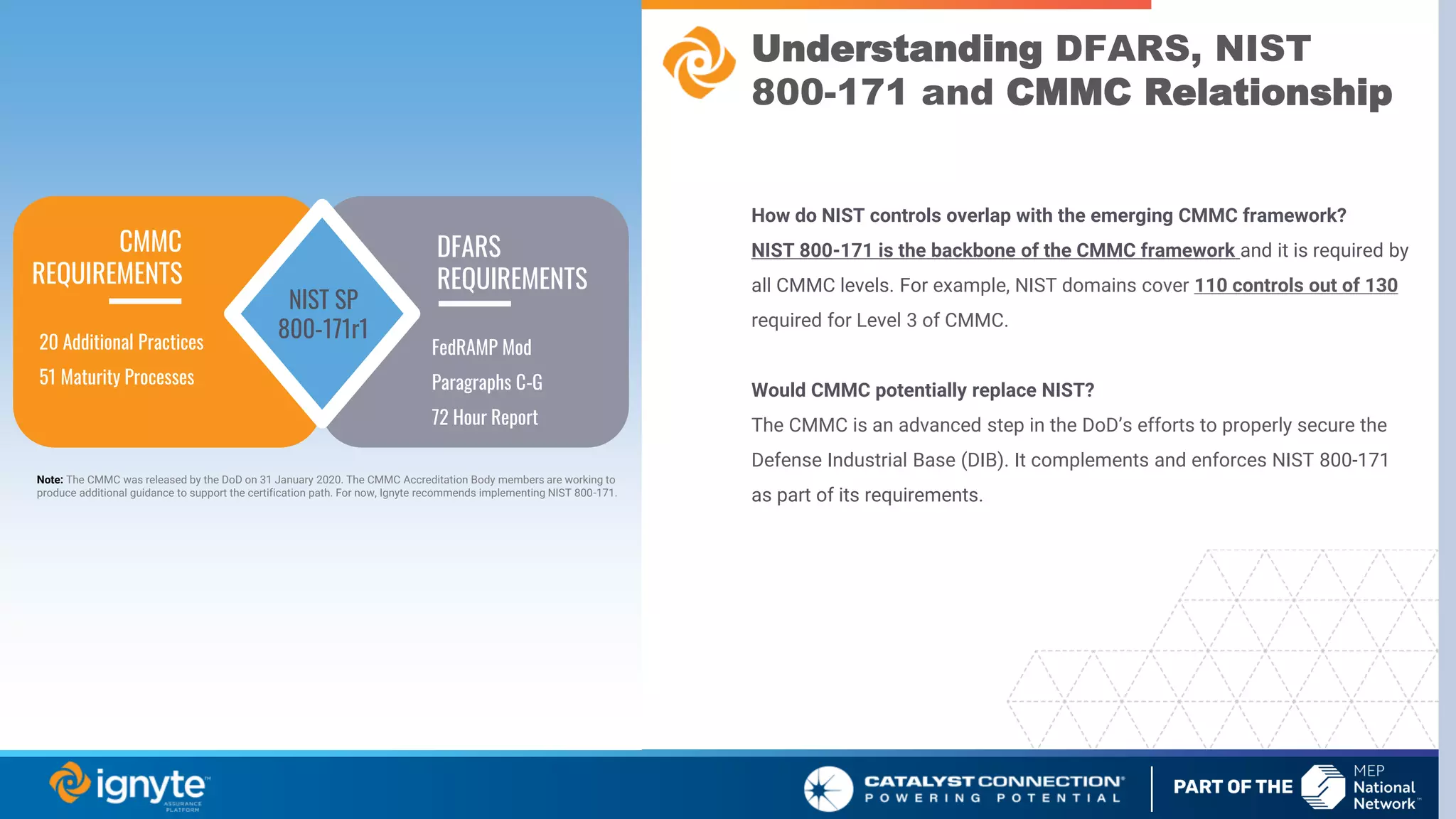
The document outlines a webinar series focused on the necessity of cybersecurity in U.S. manufacturing, led by experts Max Aulakh and Connie Palucka. It highlights the rising threat of cyberattacks on small and medium-sized businesses, emphasizing the growing costs and impacts of data breaches, particularly in the context of compliance with Defense Federal Acquisition Regulation Supplement (DFARS) and Cybersecurity Maturity Model Certification (CMMC) requirements. The series will cover various topics including DFARS compliance, cybersecurity strategies, and risk management practices for defense contractors.