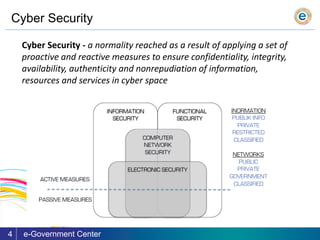
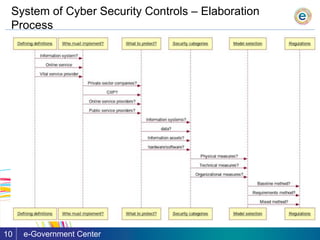
The document outlines the challenges and trends regarding cyber security in Moldova, emphasizing the lack of a unified approach and qualified personnel. It discusses the importance of establishing a comprehensive system of security controls that complies with international standards and promotes quick, actionable steps to improve cyber security. The ultimate goal is to enhance awareness and create a baseline for protecting information and resources in a rapidly evolving digital landscape.