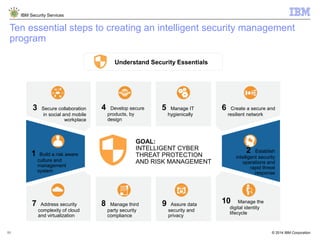
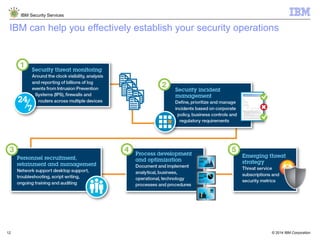
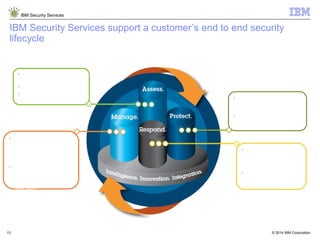
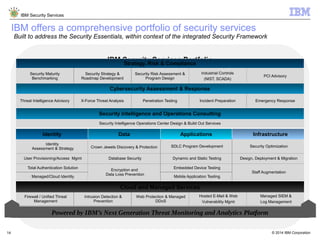
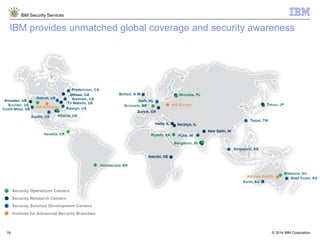
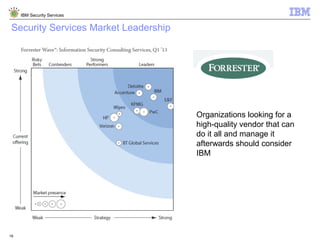
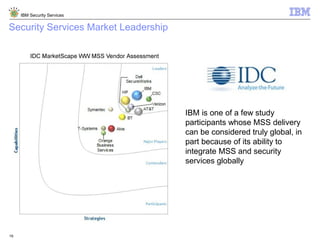
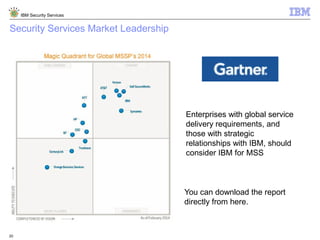
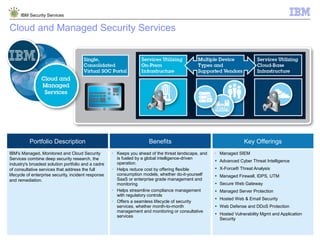
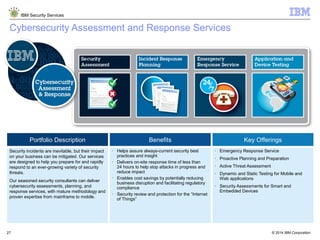
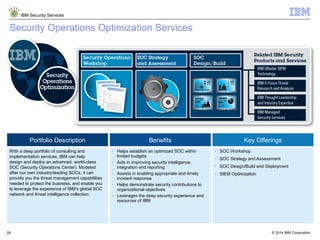
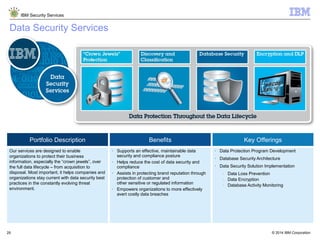
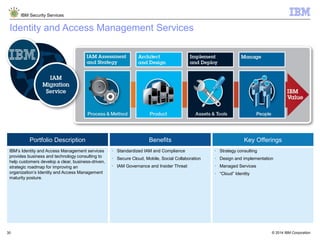
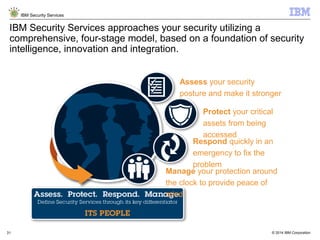
The document is a presentation from IBM about IBM Security Services. It discusses the evolving threat landscape facing organizations, the need for a new intelligent approach to security management, and IBM's security solutions and services. IBM provides services across security strategy, risk and compliance, cybersecurity assessment and response, security operations optimization, and data security. The presentation emphasizes IBM's global scale, security expertise, and ability to help organizations address all aspects of the security lifecycle.