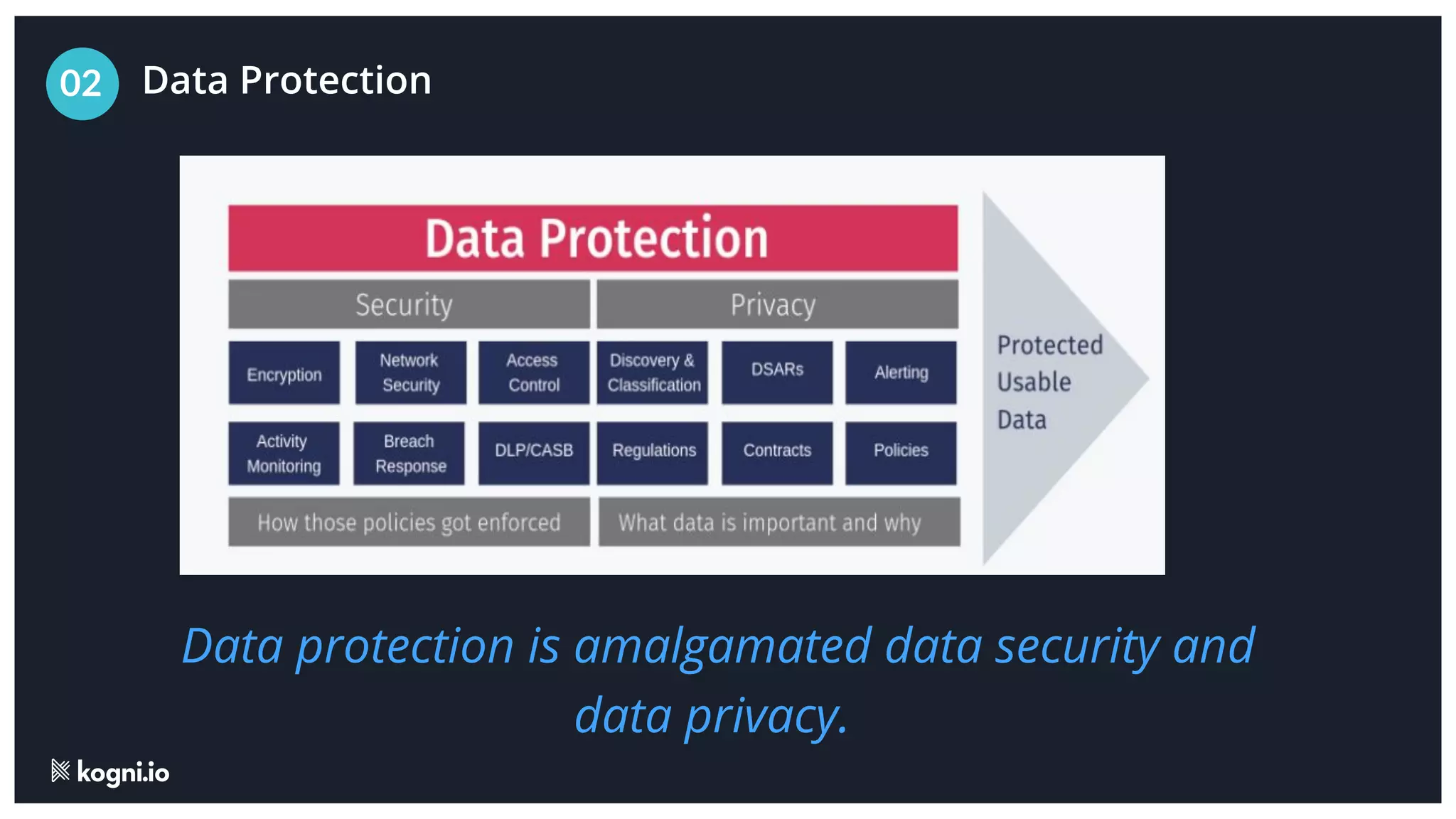
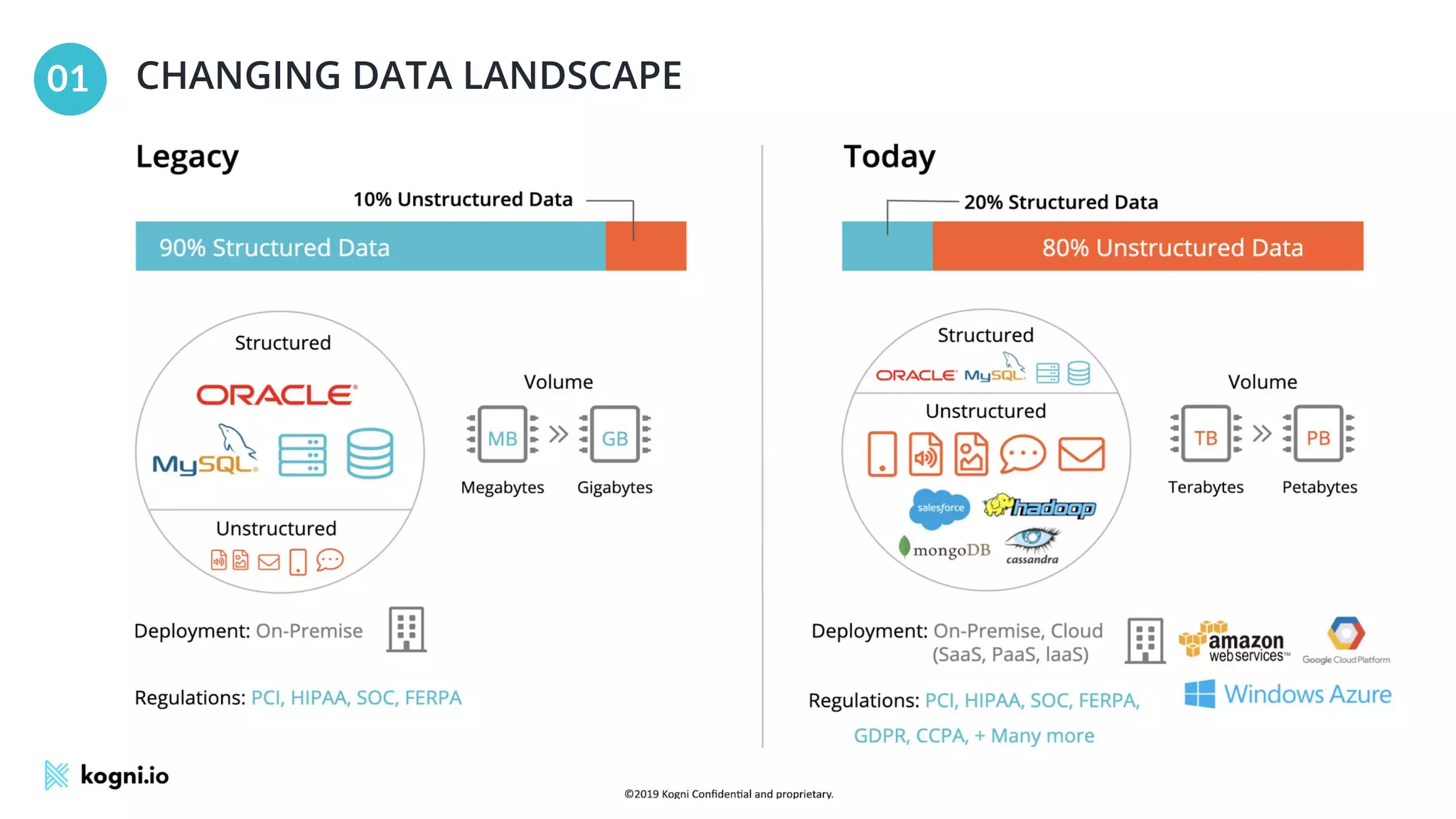
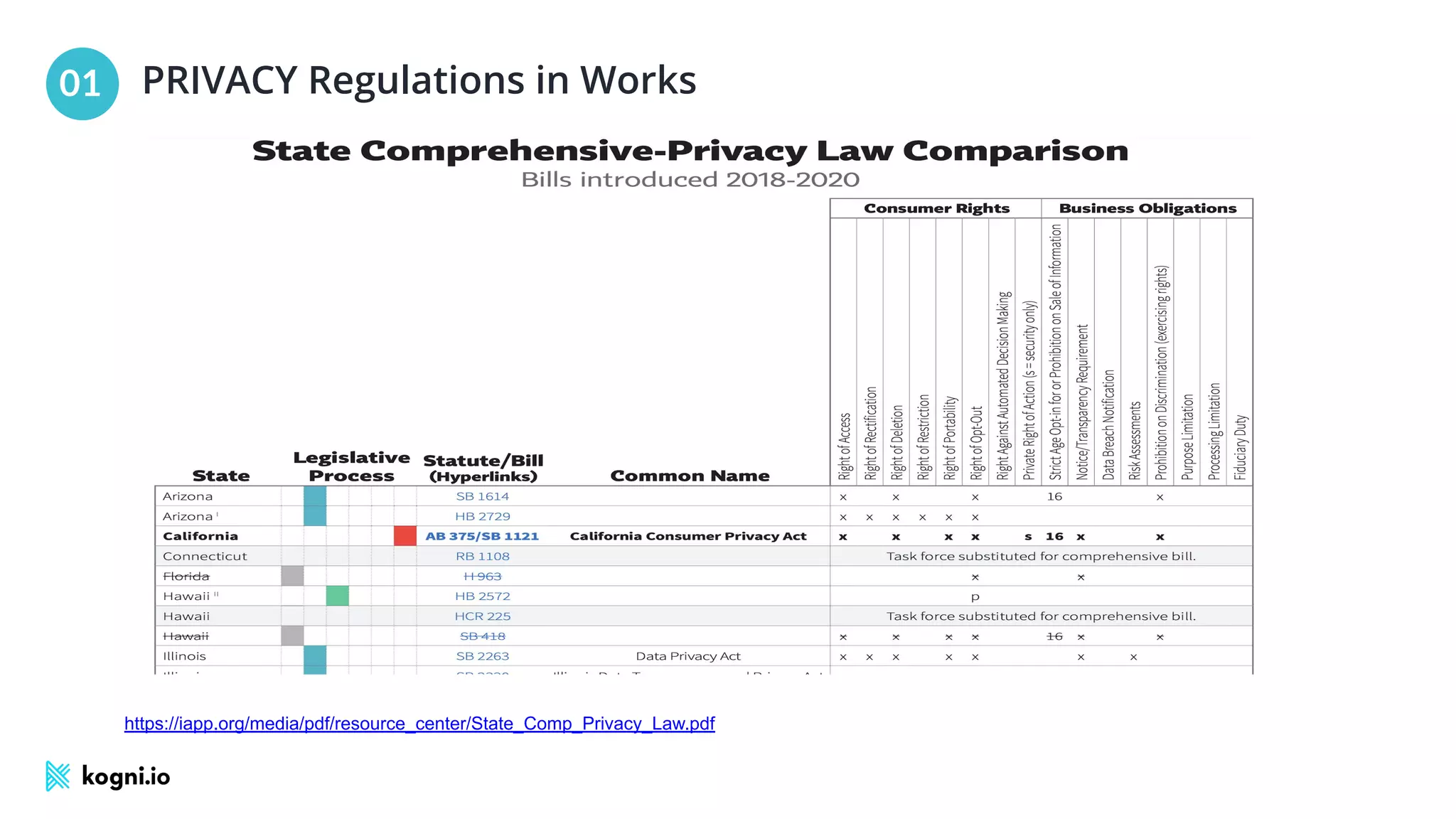
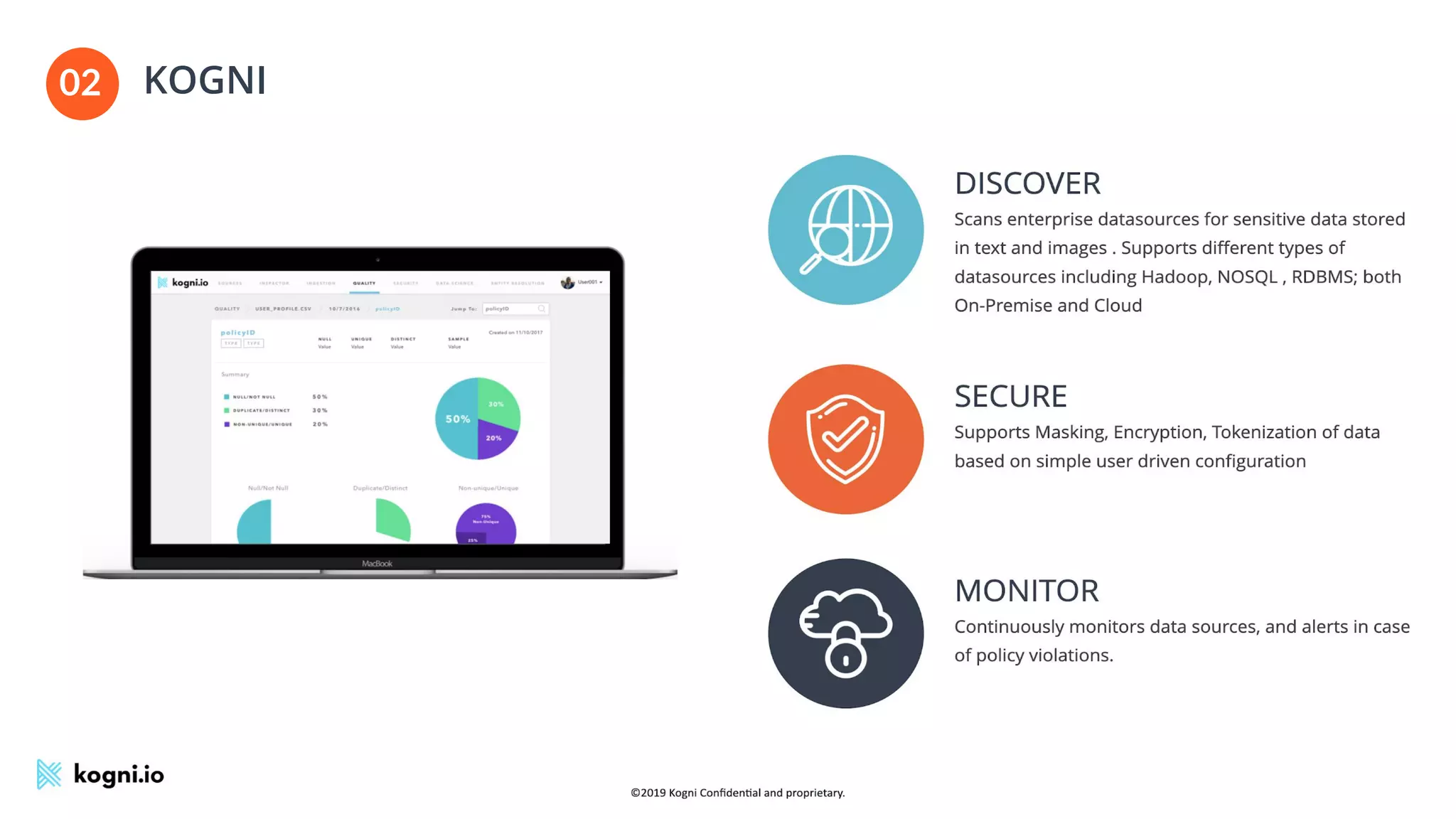
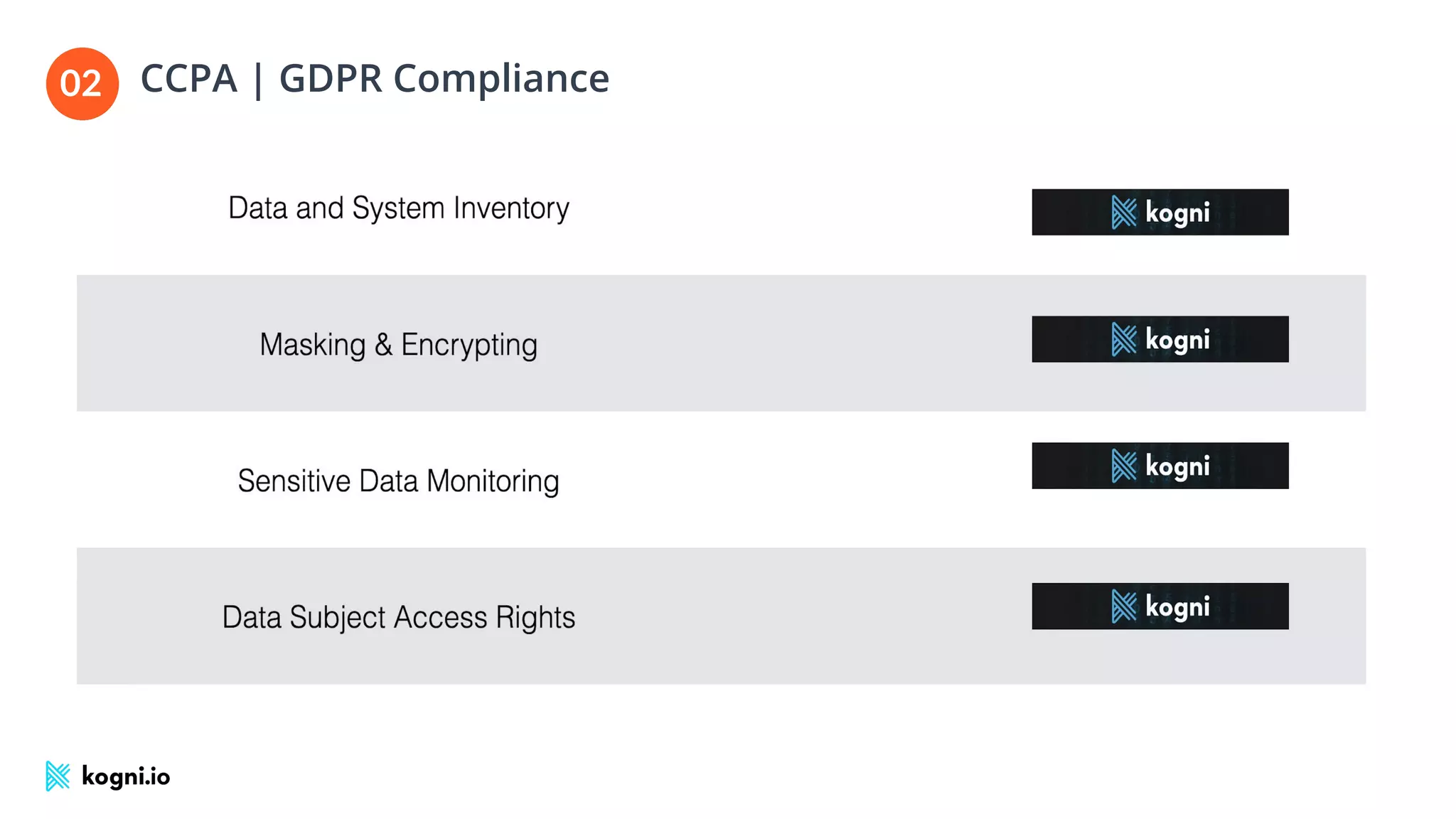
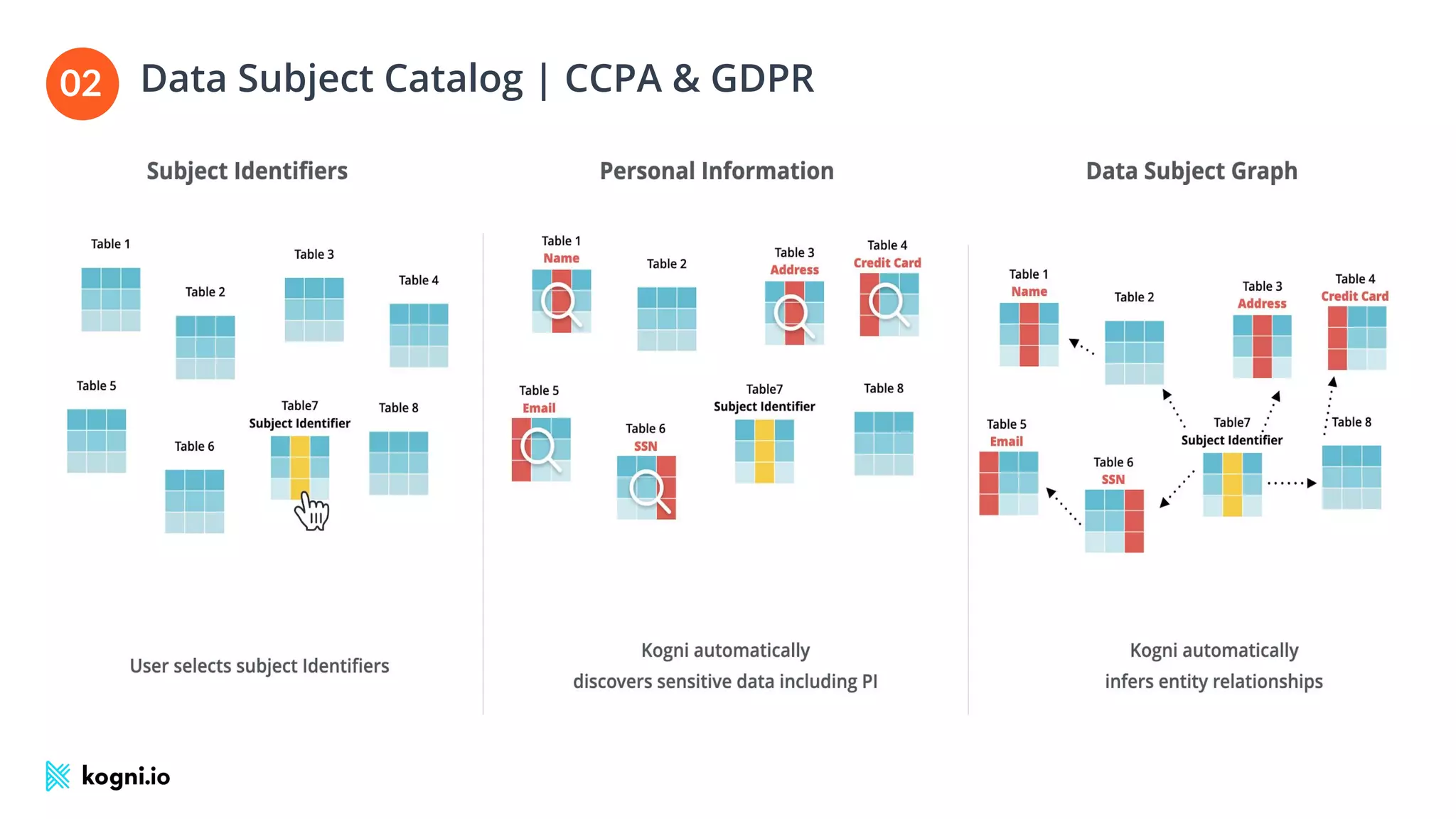
The document discusses the essential elements of data security and privacy, emphasizing the need for automated privacy programs that effectively address modern challenges. It outlines the distinctions between data security, data privacy, and data protection, while identifying obstacles to building effective privacy programs. Key steps for establishing such programs include understanding regulatory obligations, identifying data assets, and gaining executive support.