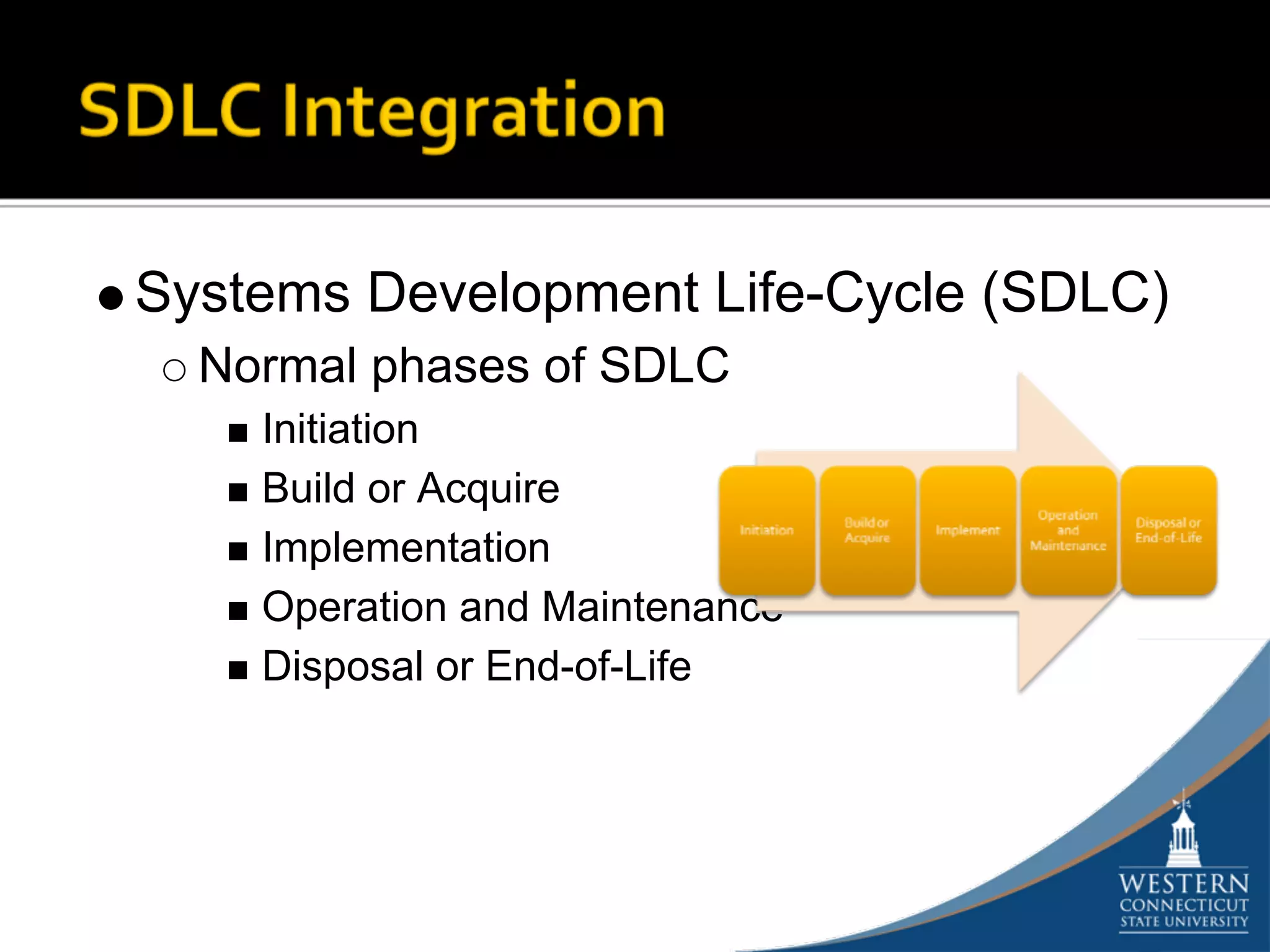
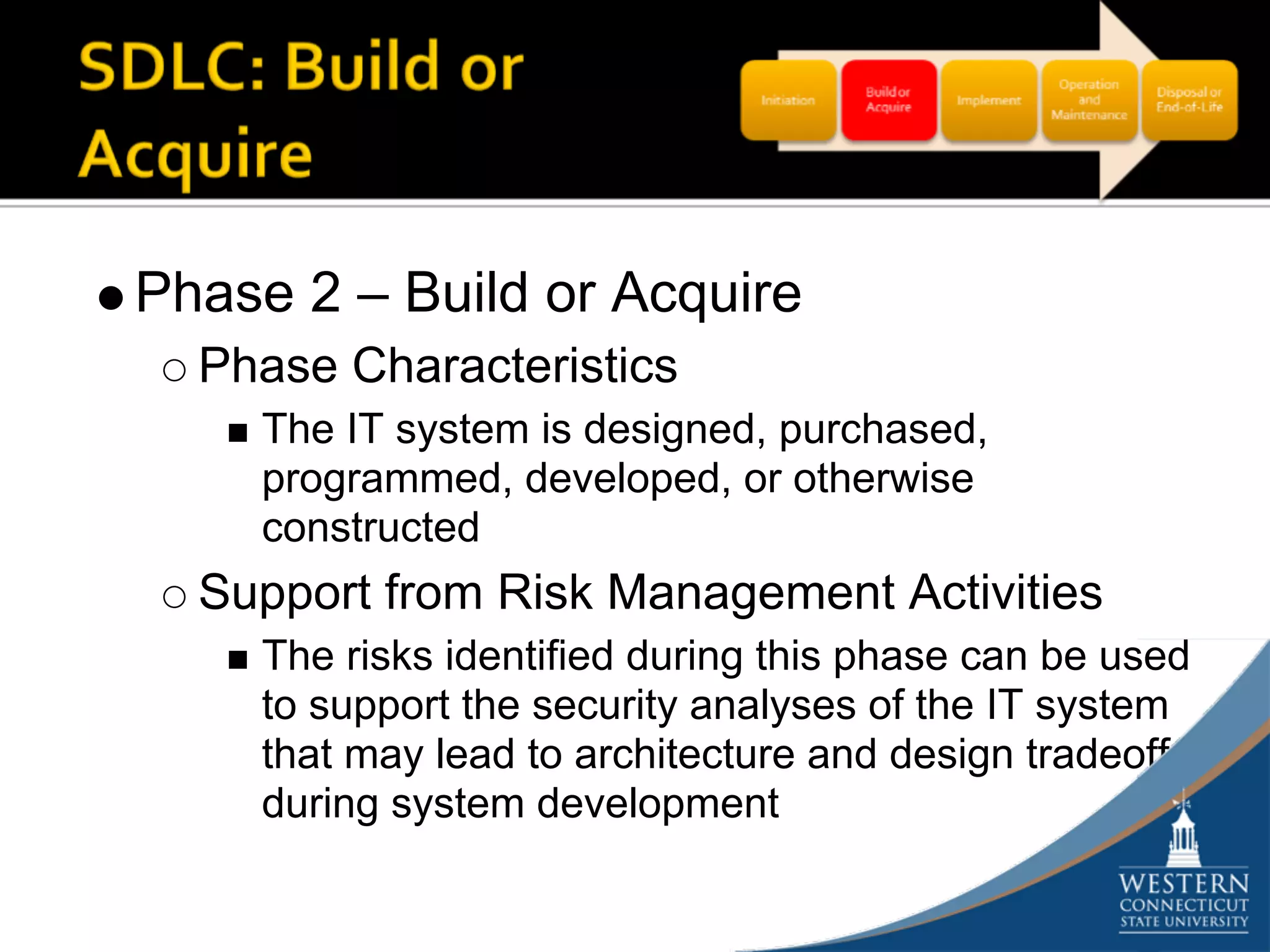
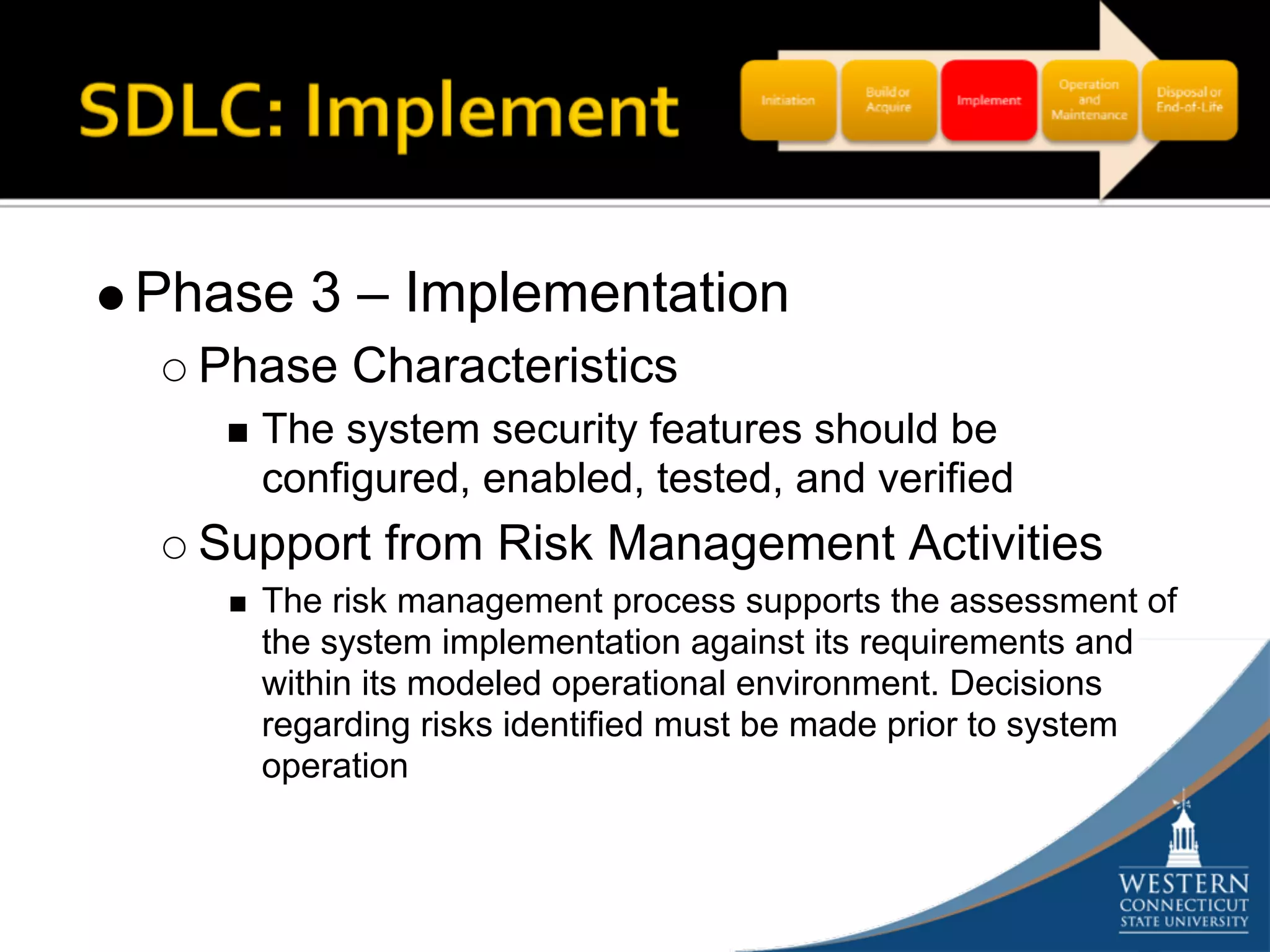
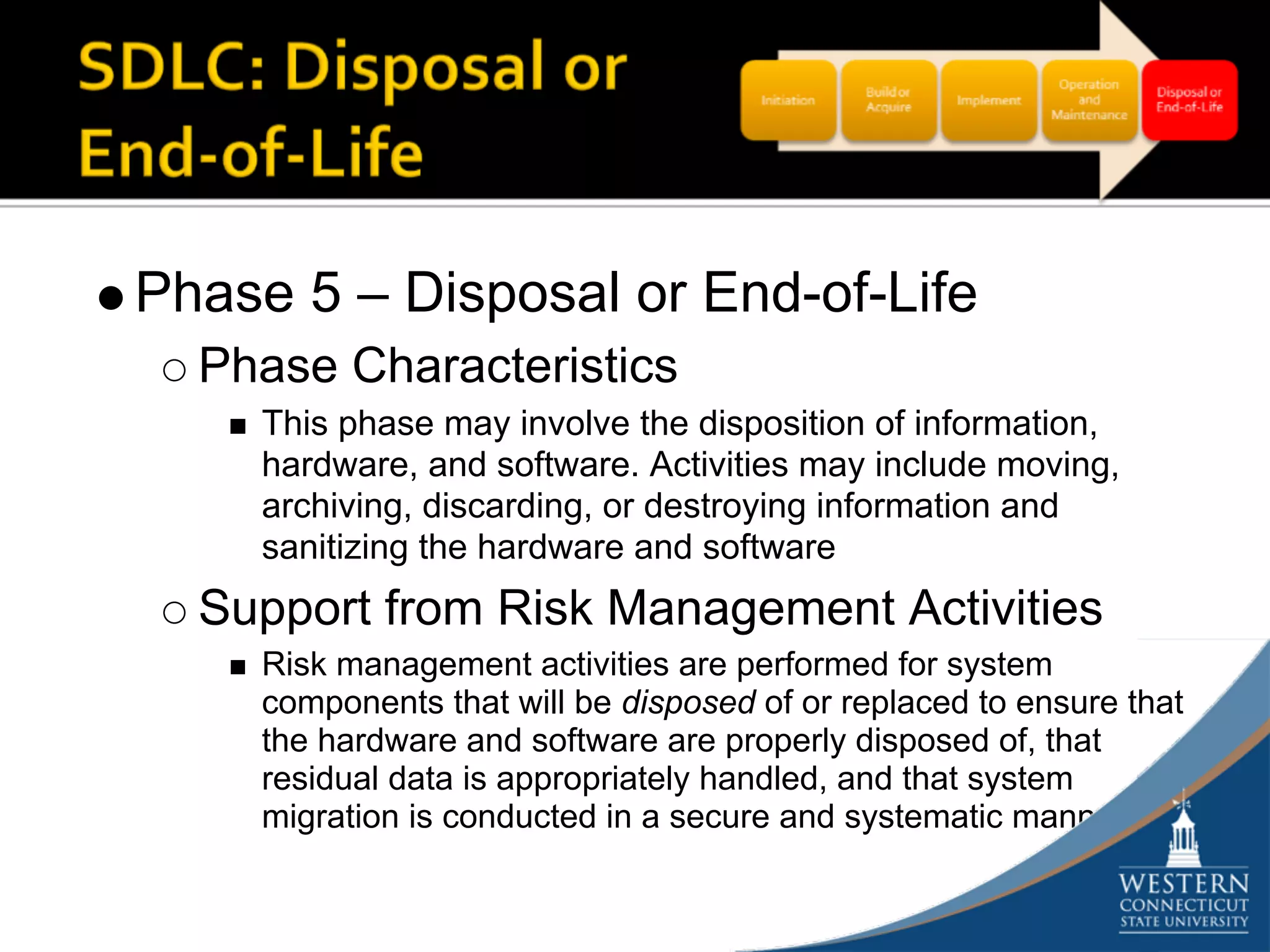
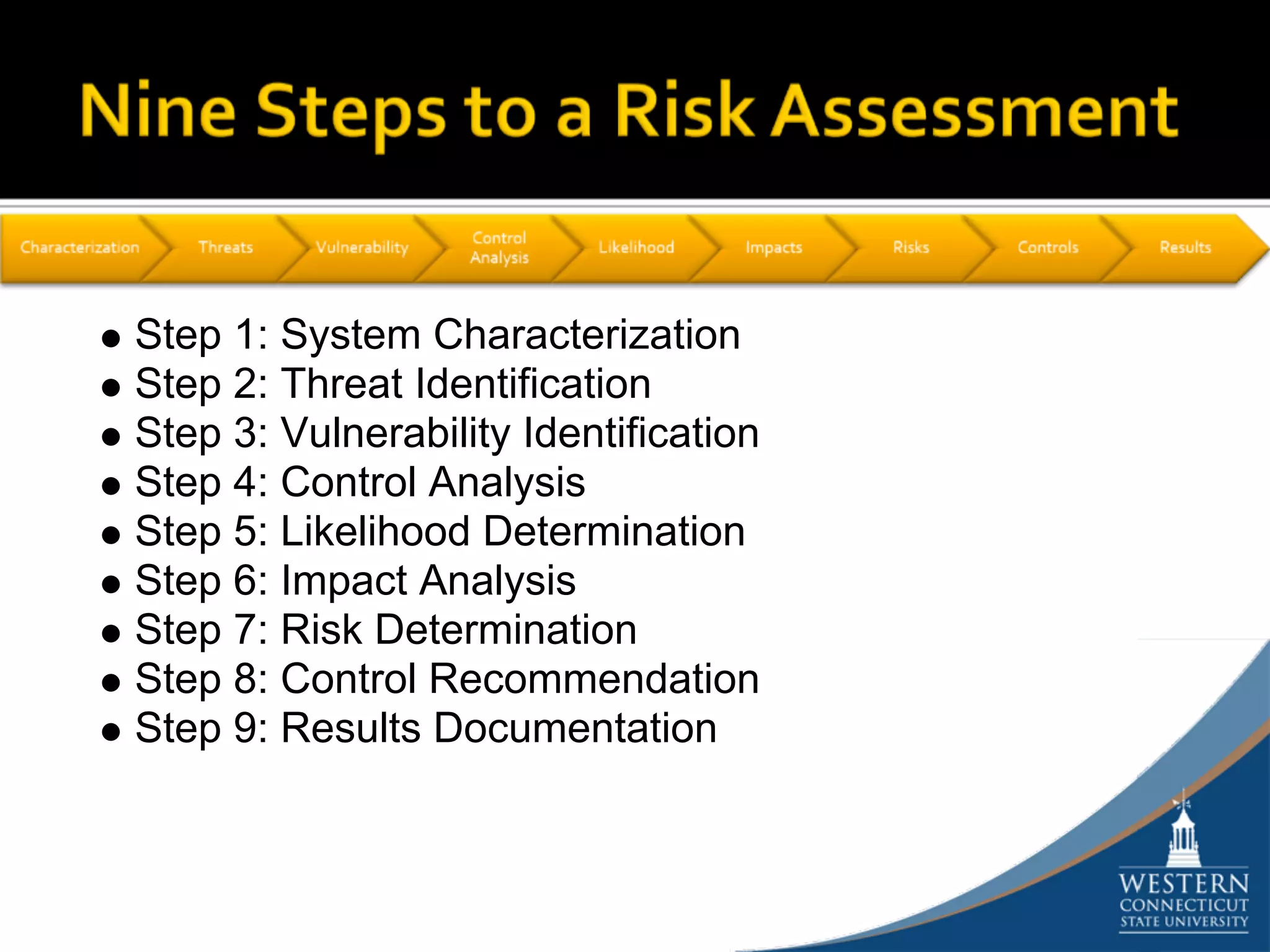
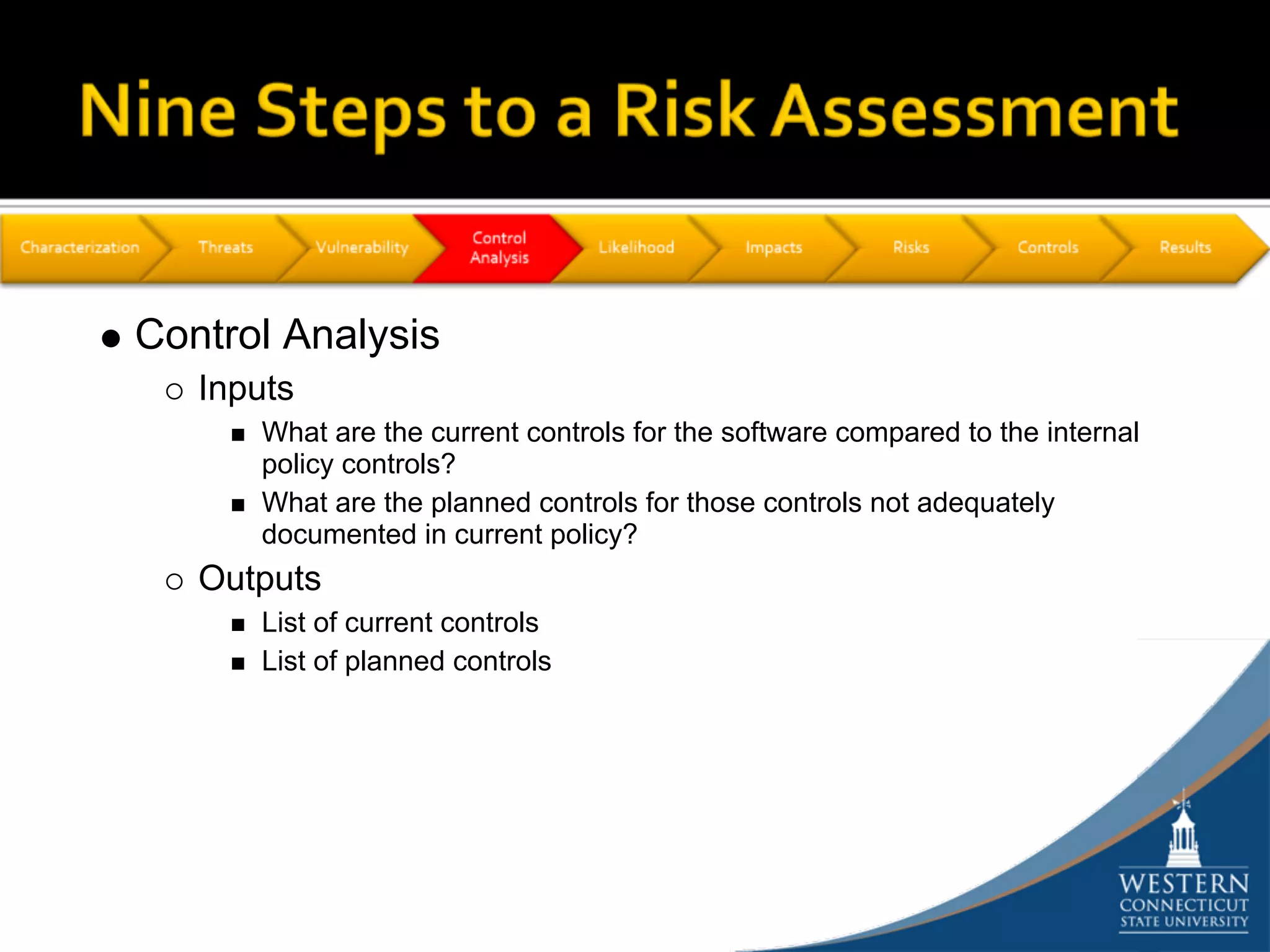
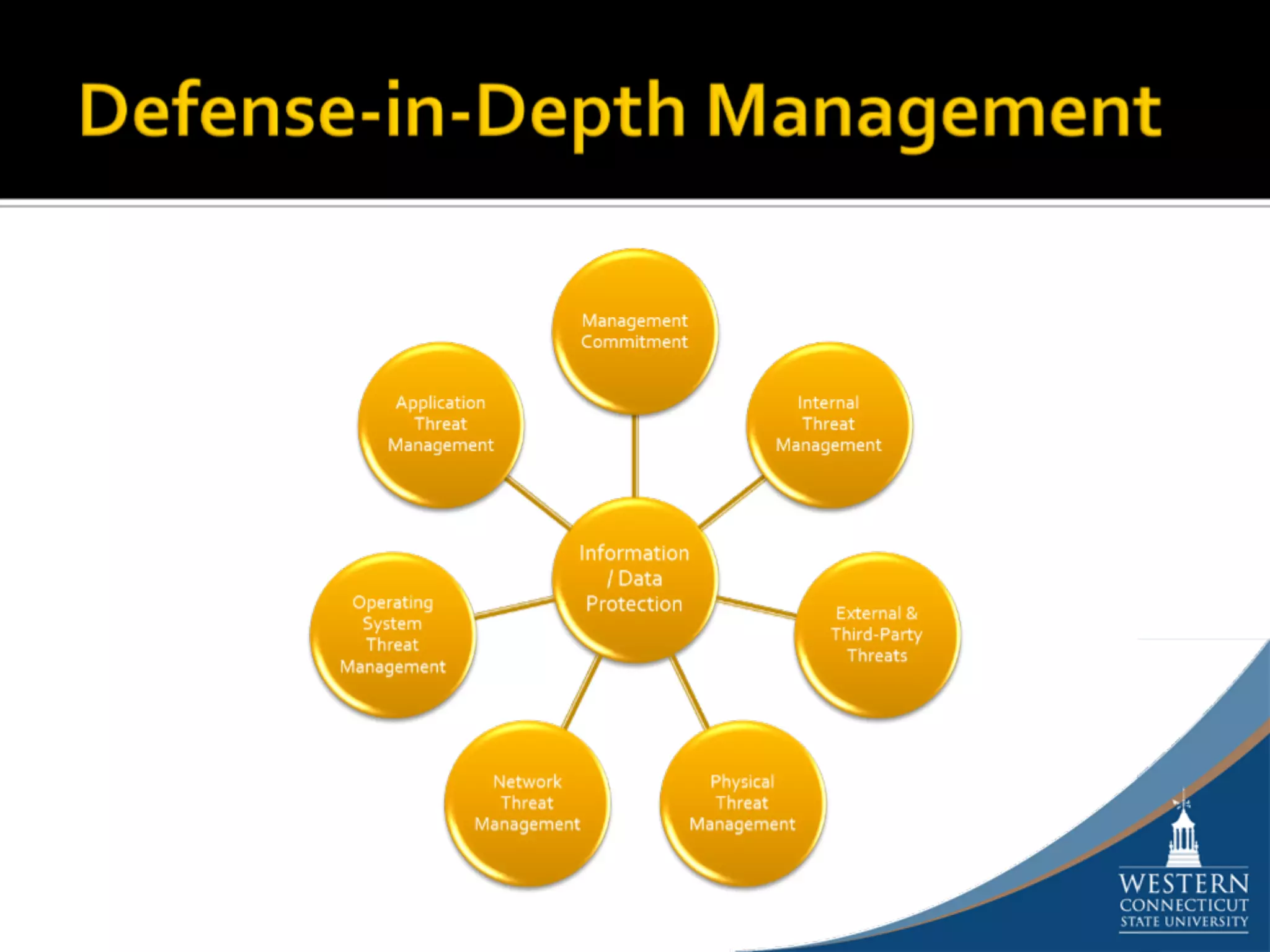
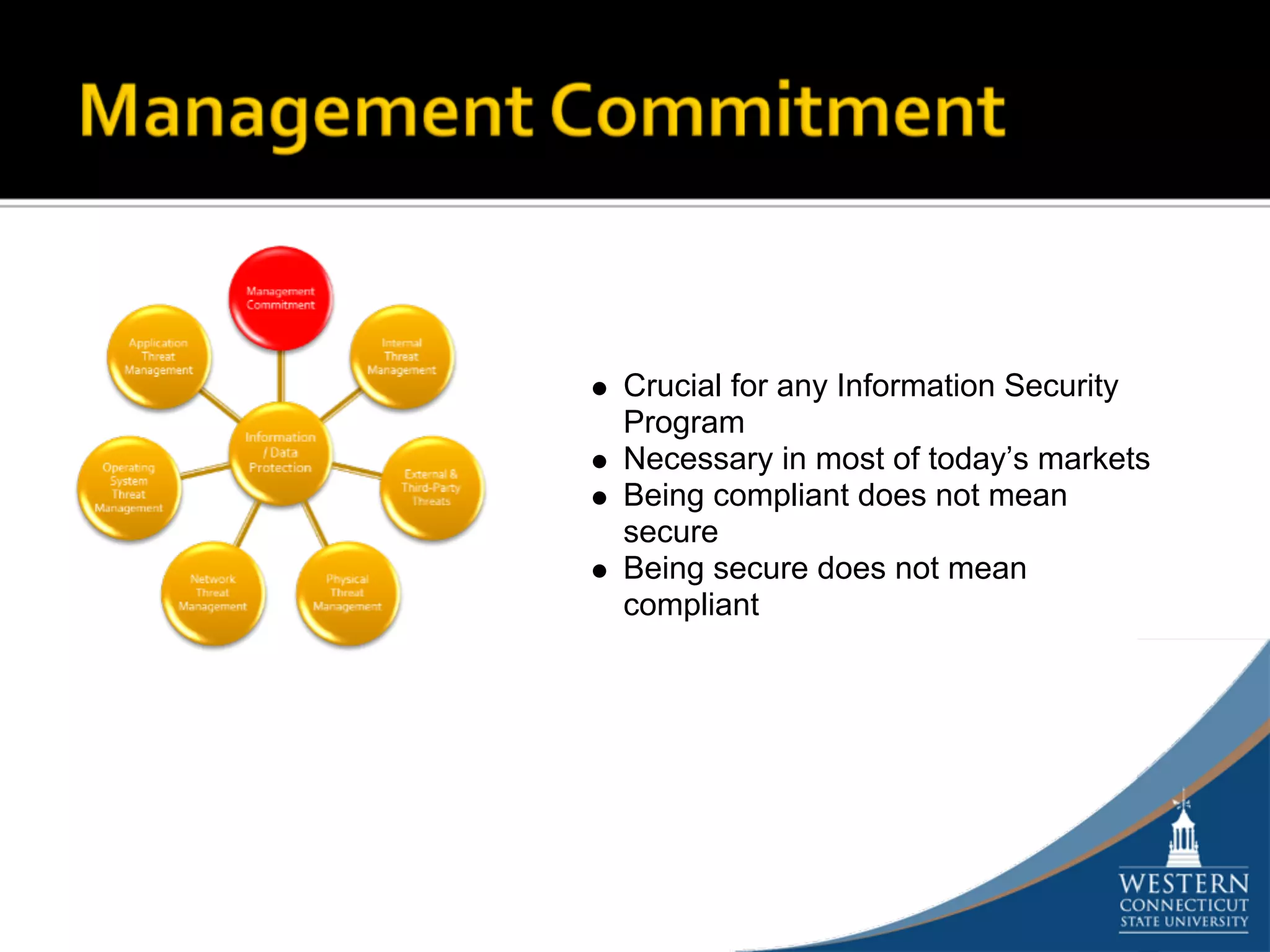
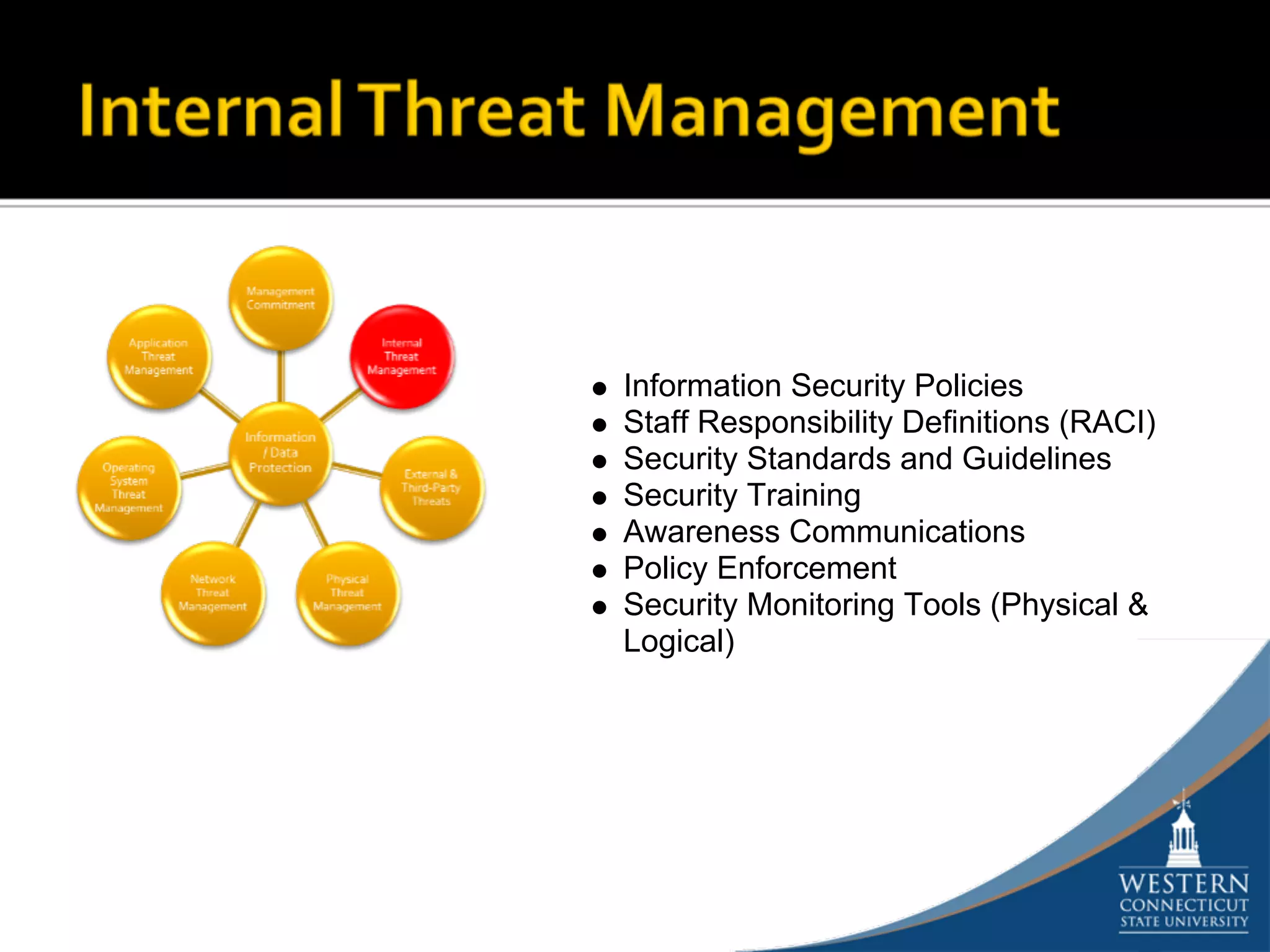
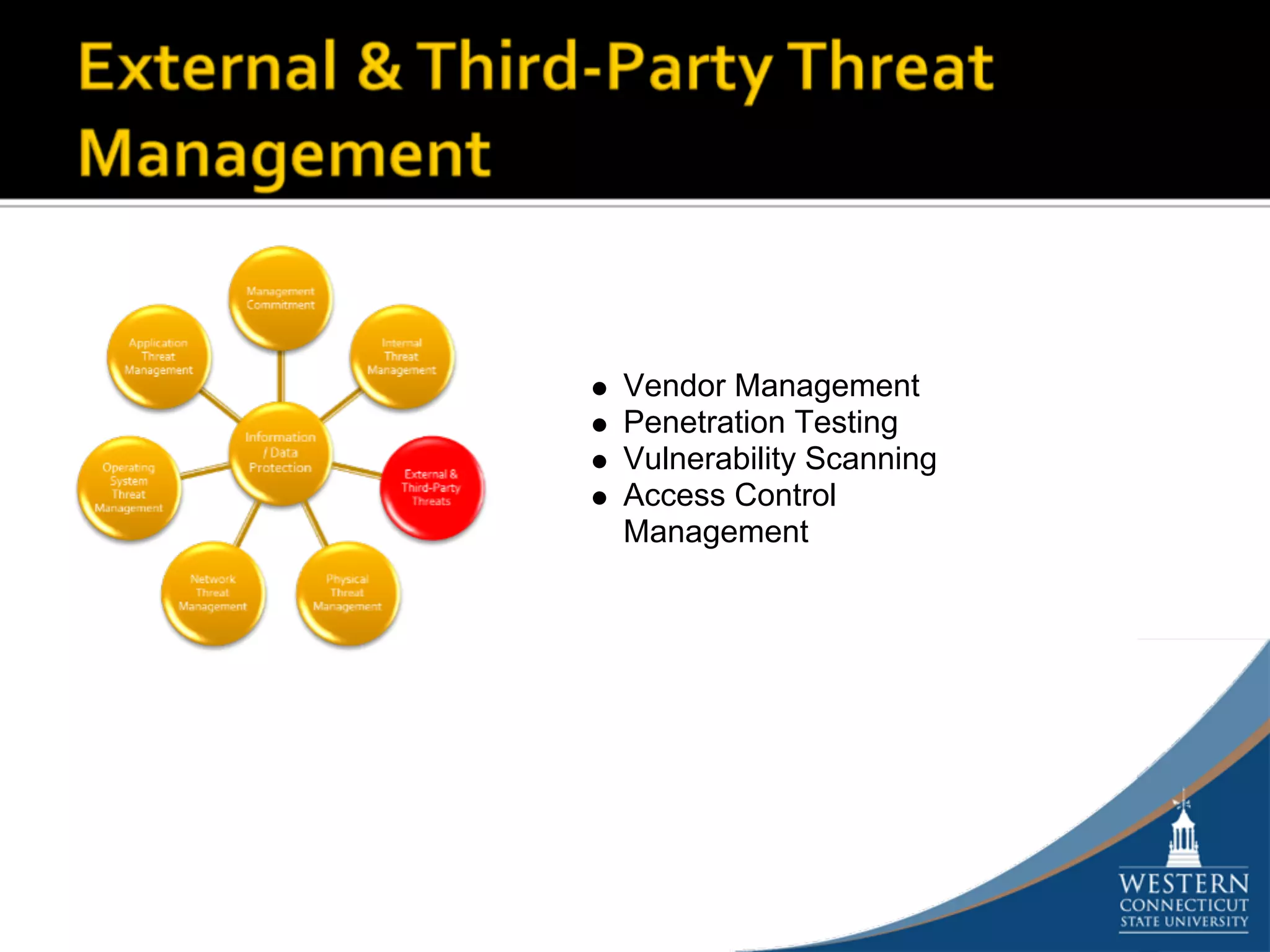
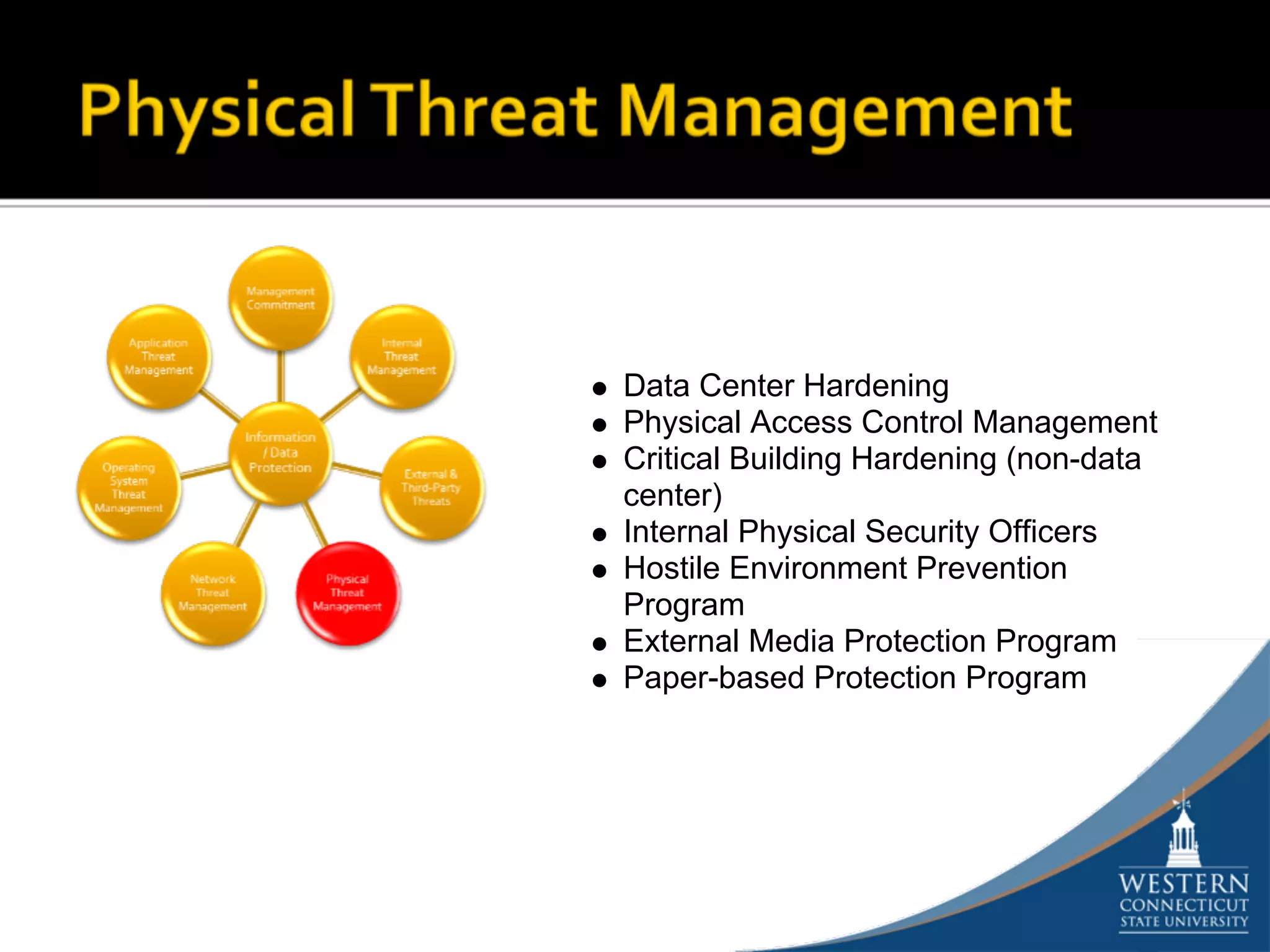
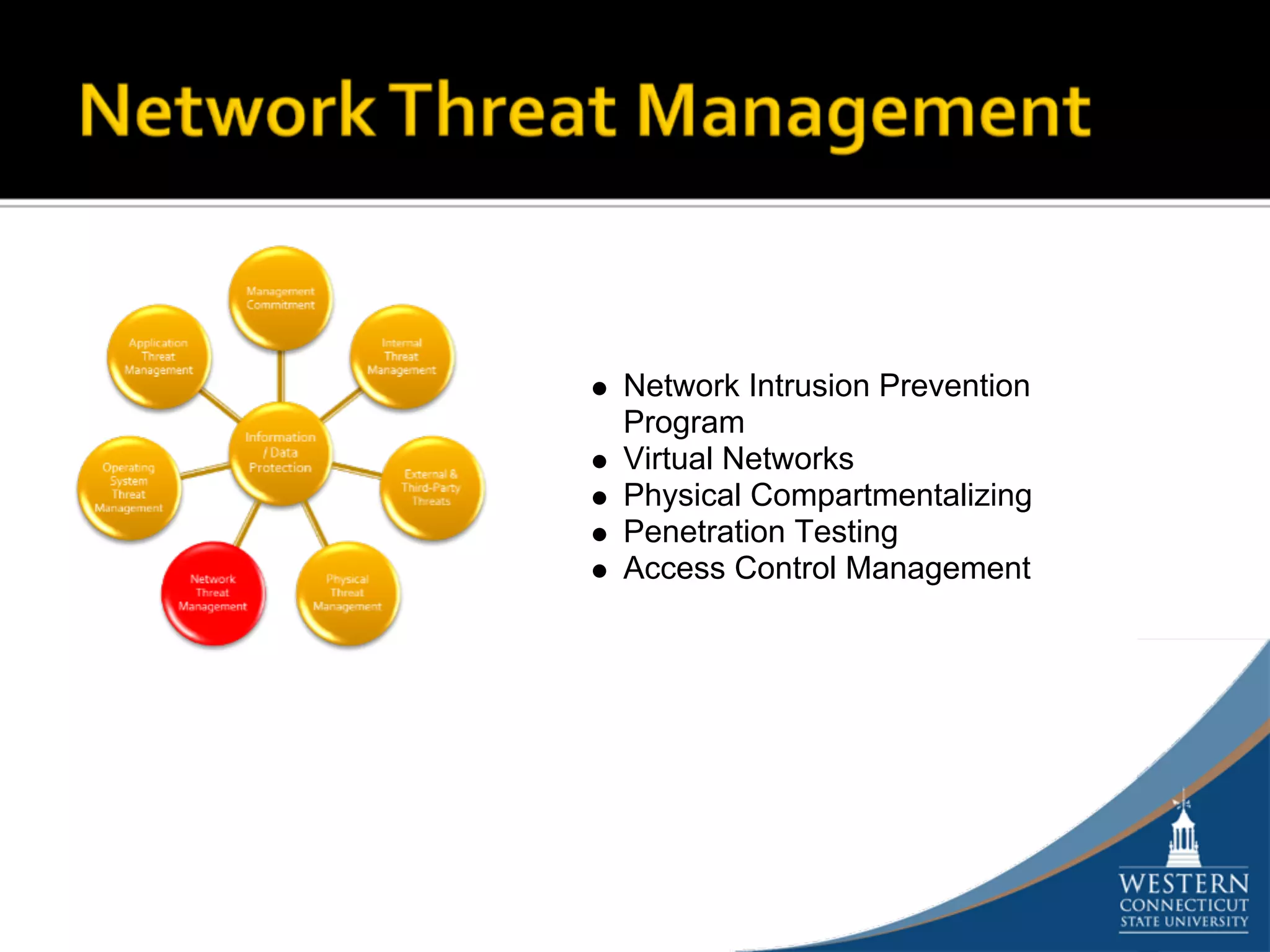
The document outlines a comprehensive strategy for risk management and defense in depth within information security, detailing the phases of the systems development life-cycle (SDLC) and the importance of identifying and mitigating risks throughout. It emphasizes the need for systematic risk assessments, control analyses, and the implementation of security measures to protect IT systems against vulnerabilities. Ultimately, the document argues that while complete security is unattainable, a structured approach can significantly reduce risks when supported by organizational commitment.