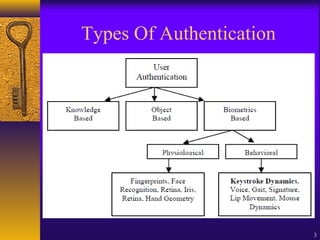
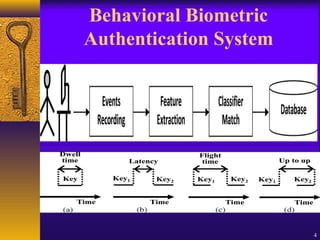
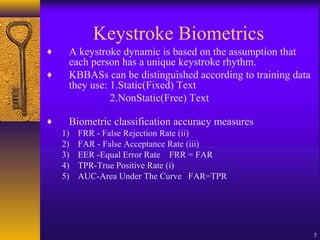
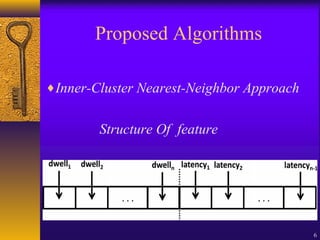
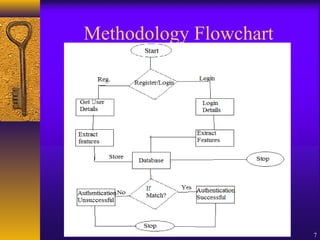
The document discusses user authentication through behavioral biometric systems, particularly focusing on keystroke dynamics, which relies on the uniqueness of individual typing rhythms. It outlines various types of authentication, proposed algorithms, advantages and challenges of keystroke dynamics, and suggests future research directions to enhance accuracy and error rates. Overall, while promising, the method requires further development for effective user identification.