This document provides an overview of digital fingerprinting technology. It explains that digital fingerprinting can automatically identify phrases from confidential documents that appear in analyzed texts. The technology works by analyzing media like songs or videos to identify unique portions that can be matched to a database. Major companies like YouTube and Audible Magic use digital fingerprinting to identify copyrighted content and prevent unauthorized sharing. The document also discusses watermarking and how fingerprinting offers a more effective way to restrict copyrighted material than visible watermarks.



















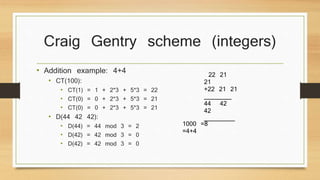
![CRAIG GENTRY
scheme(integers)
• KEY: odd integers p>2N
• ENCRYPTION ALGORITHM: given a bit b-> E(b)=c=
b+2x+kp, where x is in [-n/2,n/2] and k is an integer
chosen from some range
• DECRYPTION ALGORITHM: b=(c mod p) mod 2, where
(c mod p) is the noise and belongs to [-n,n]
• Decryption works if b+2x ∈ [-N,N] ⊂[-p/2,p/2]](https://image.slidesharecdn.com/dfp-141127044439-conversion-gate02/85/Digital-Fingerprinting-21-320.jpg)
![CRAIG GENTRY
scheme(integers)
• Graig Gentry scheme’s homomorphic assumptions
• Addiction: c1 + c2 = b1+ b2 + 2(x1+x2) + (k1+k2)p = b1 xor b2 +
2x + kp
• Decryption works if (b1+2x1) + (b2+2x2) is in
[-N,N]
• Multiplication: c1*c2 = b1*b2 + 2(b1x2 + b2x1 + 2x1x2) + kp =
b1*b2 + 2x + kp
• Decryption works if (b1+2x1) * (b2+2x2) is in
[-N,N]](https://image.slidesharecdn.com/dfp-141127044439-conversion-gate02/85/Digital-Fingerprinting-22-320.jpg)