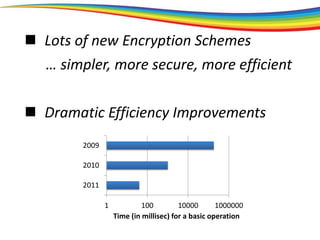
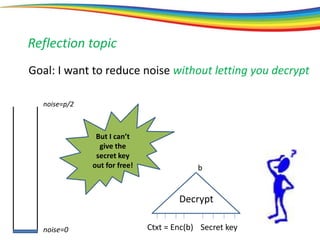
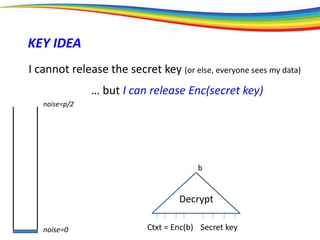
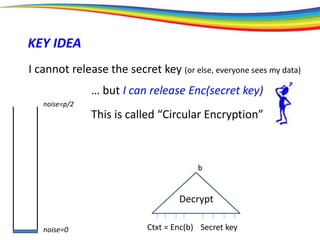
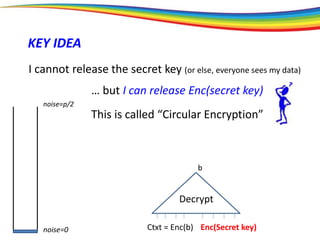
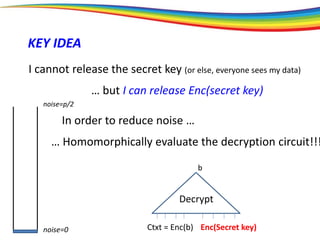
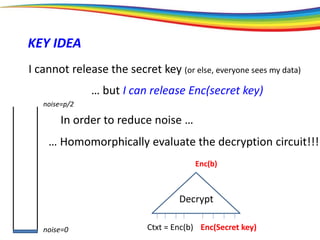
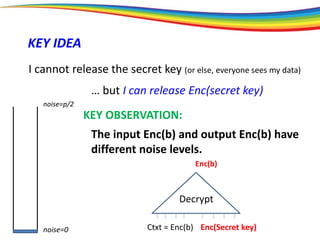
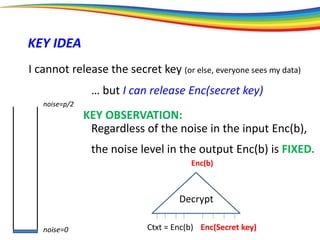
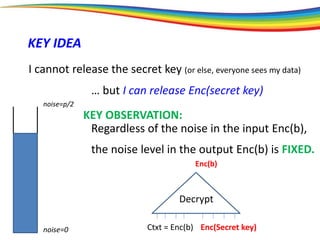
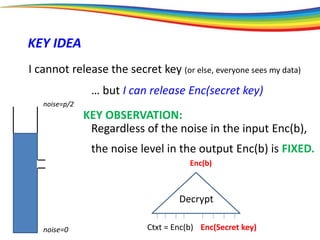
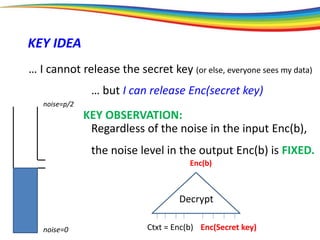
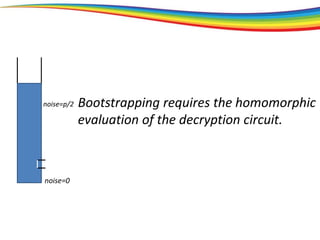
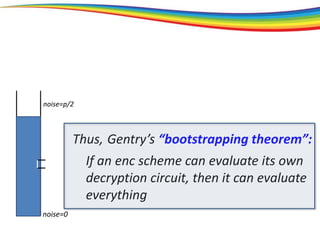
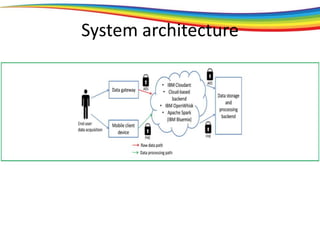
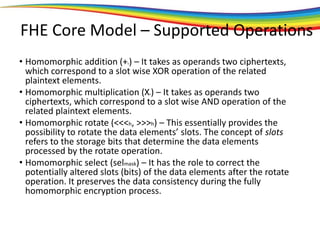
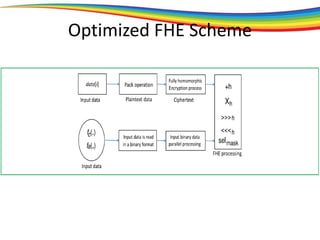
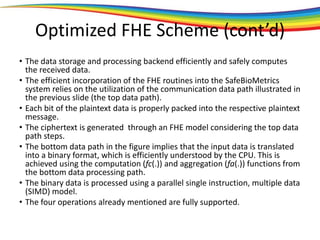
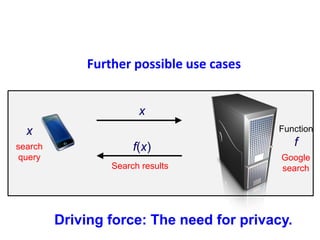
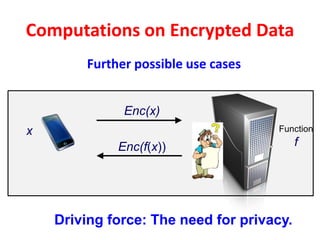
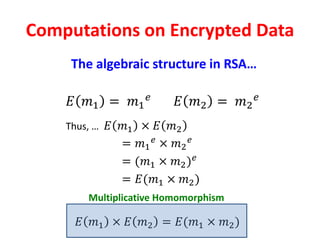
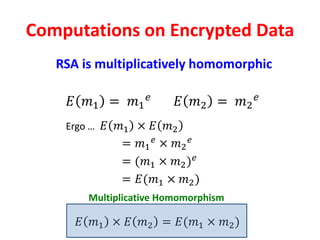
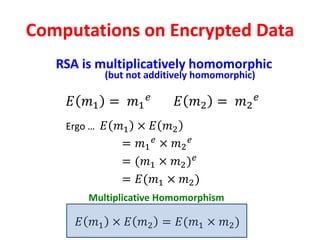
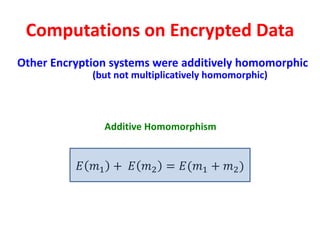
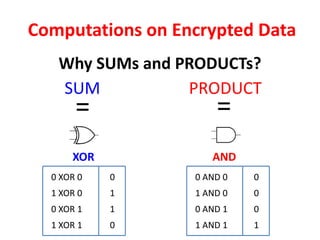
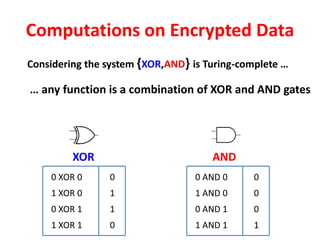
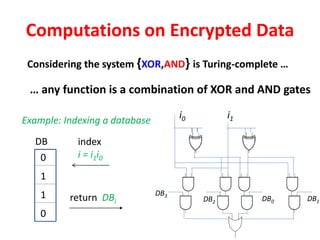
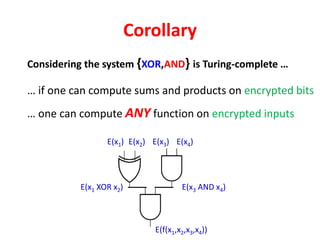
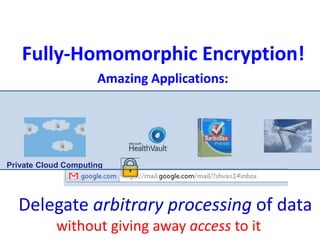
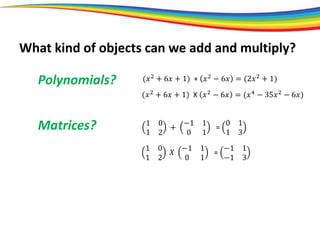
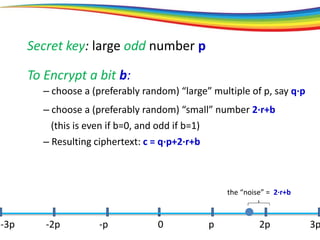
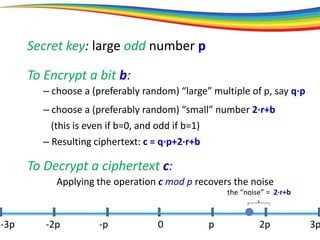
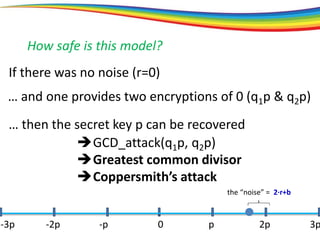
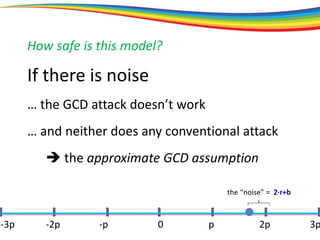
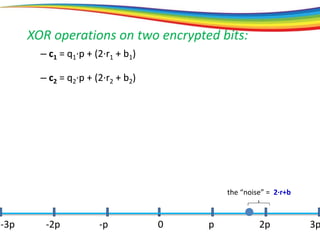
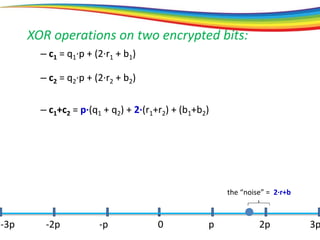
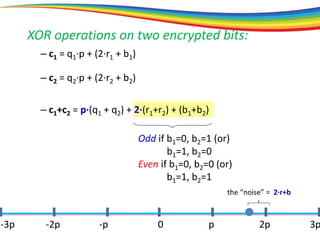
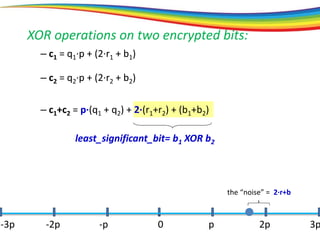
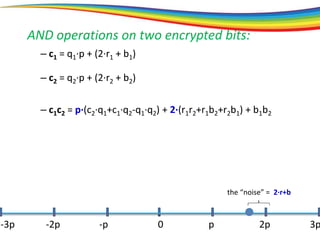
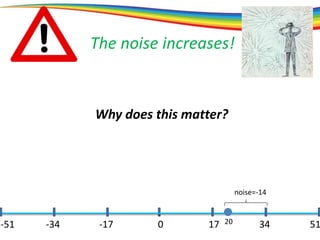
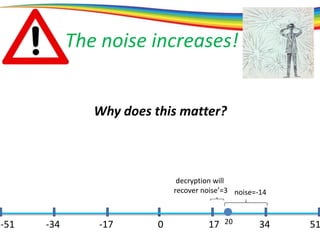
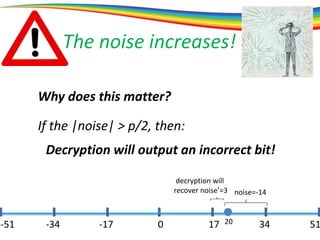
The document discusses the evolution and significance of homomorphic encryption, starting from symmetric and asymmetric encryption to the development of fully-homomorphic encryption by Craig Gentry in 2008. It explains the mathematical principles behind homomorphic encryption that allow computations on encrypted data, emphasizing the importance of adding and multiplying data without compromising privacy. The document concludes by highlighting advancements in encryption schemes that enhance efficiency and security while addressing noise-related challenges.





















![Fully homomorphic
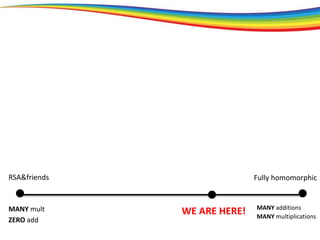
MANY add
MANY mult
WE ARE HERE!
[bootstrapping]
How is this possible?
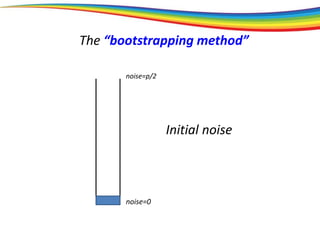
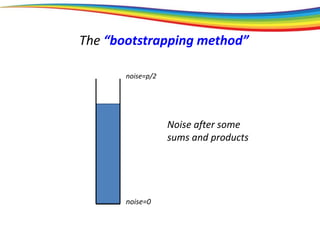
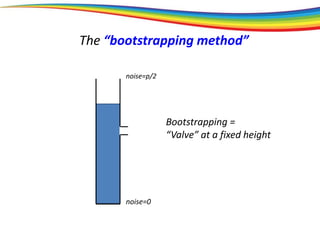
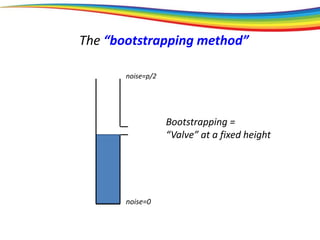
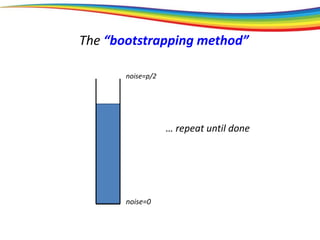
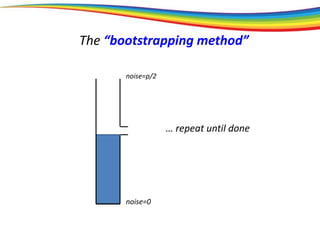
The “bootstrapping method”
Principle: If you can go a (large) part of the way,
then you can go all the way.
RSA&friends
MANY mult
ZERO add](https://image.slidesharecdn.com/razvanbocudefcamp2018-190531064514/85/Secure-and-privacy-preserving-data-transmission-and-processing-using-homomorphic-encryption-57-320.jpg)