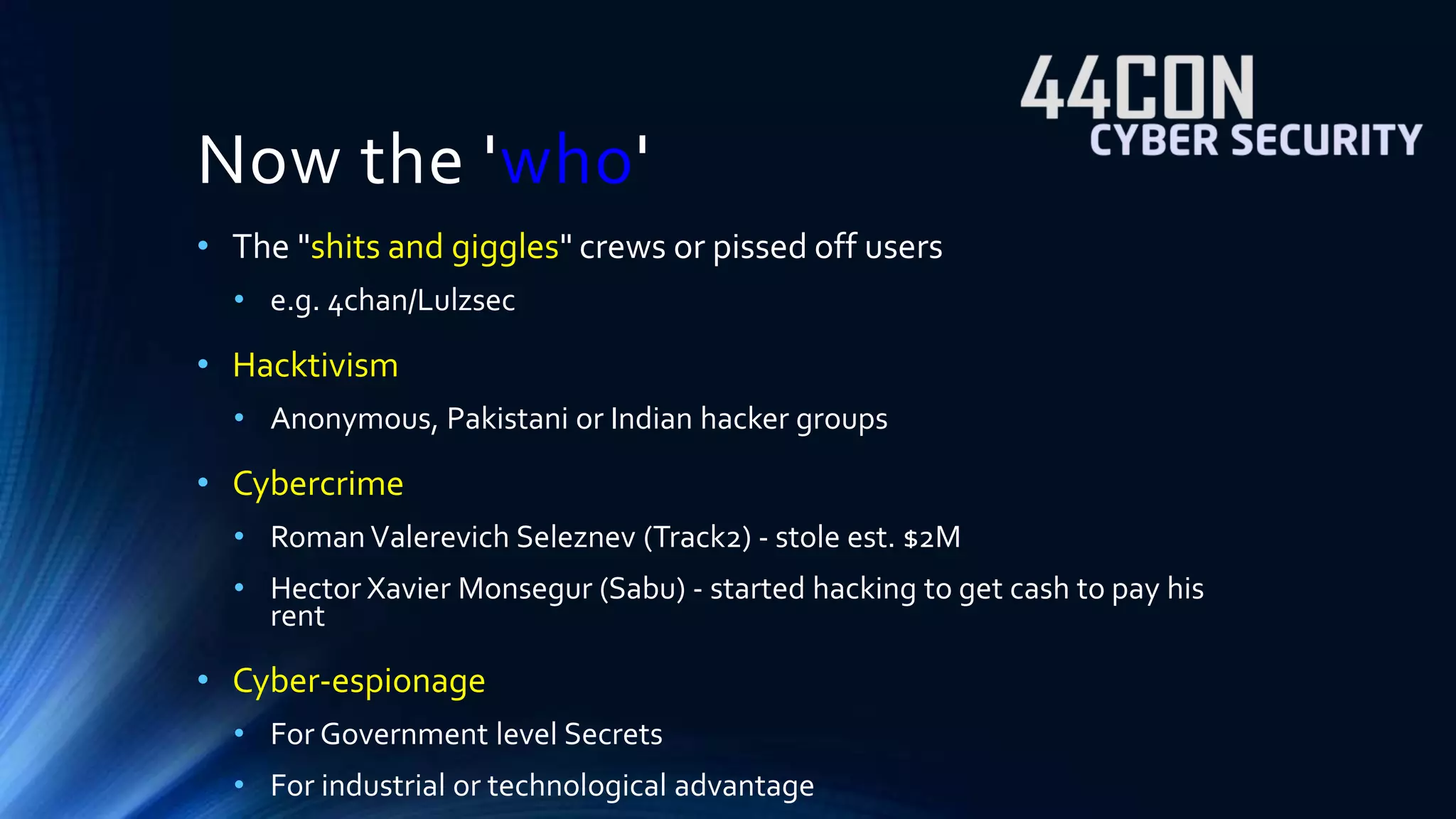
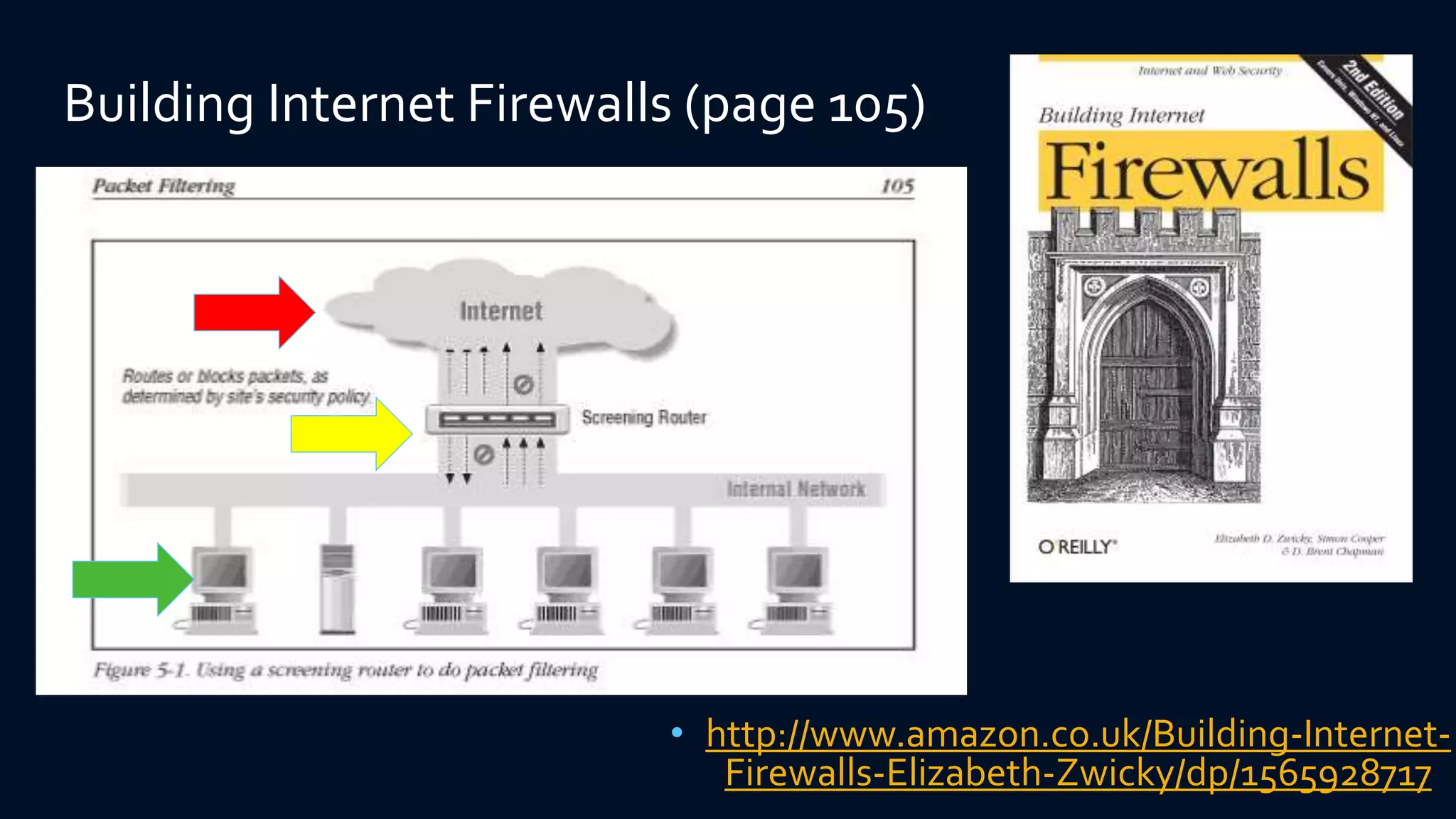
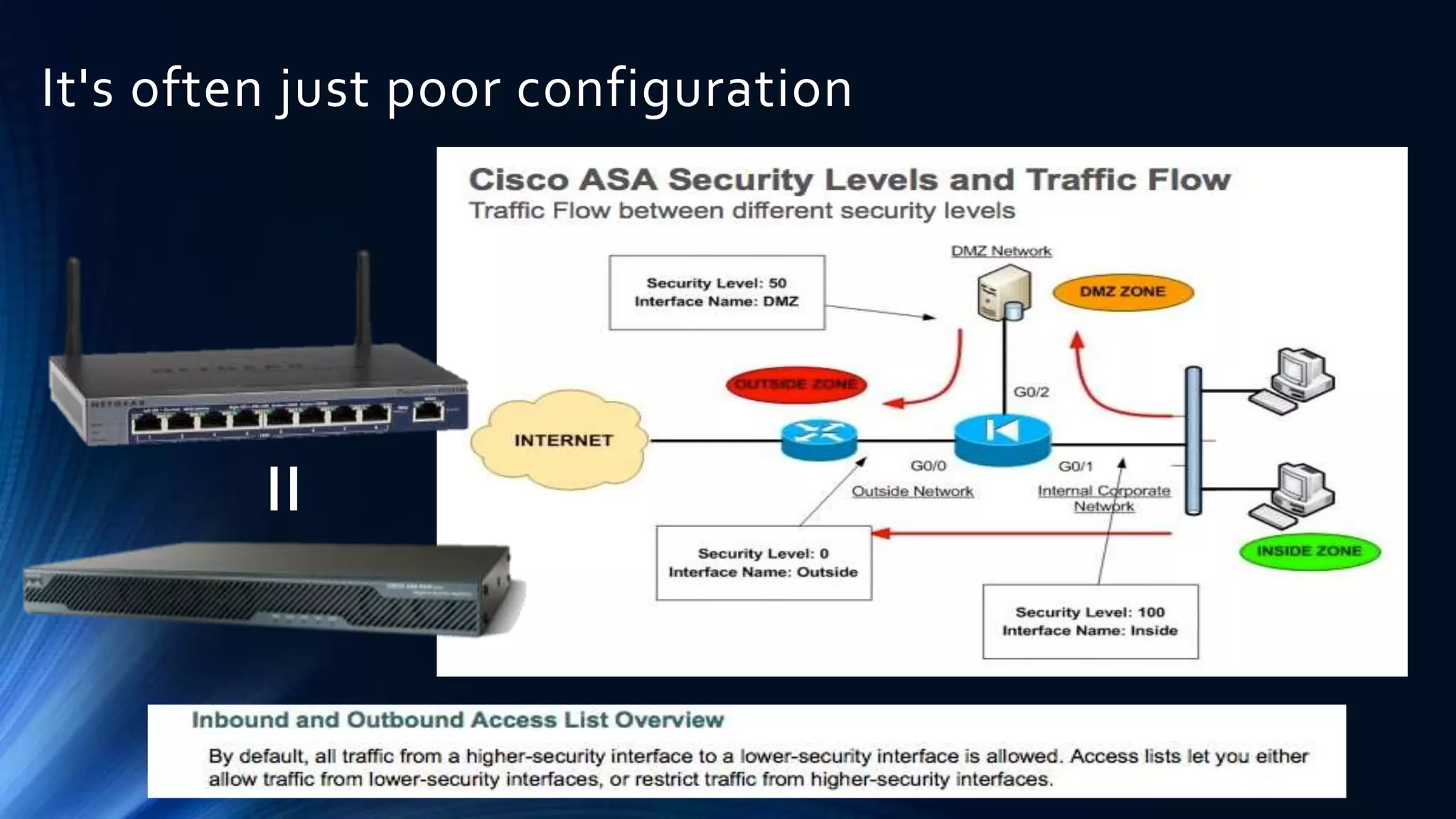
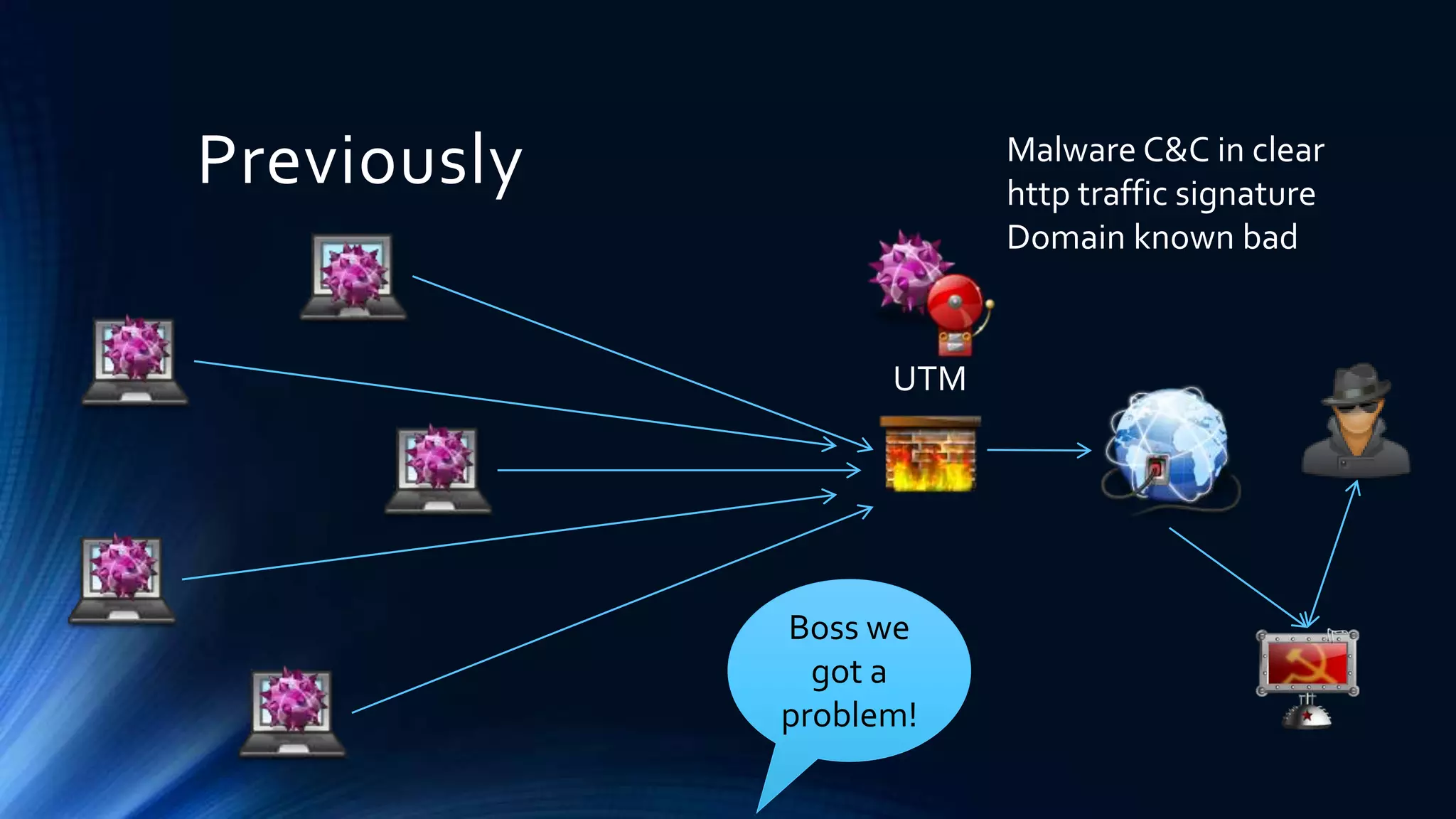
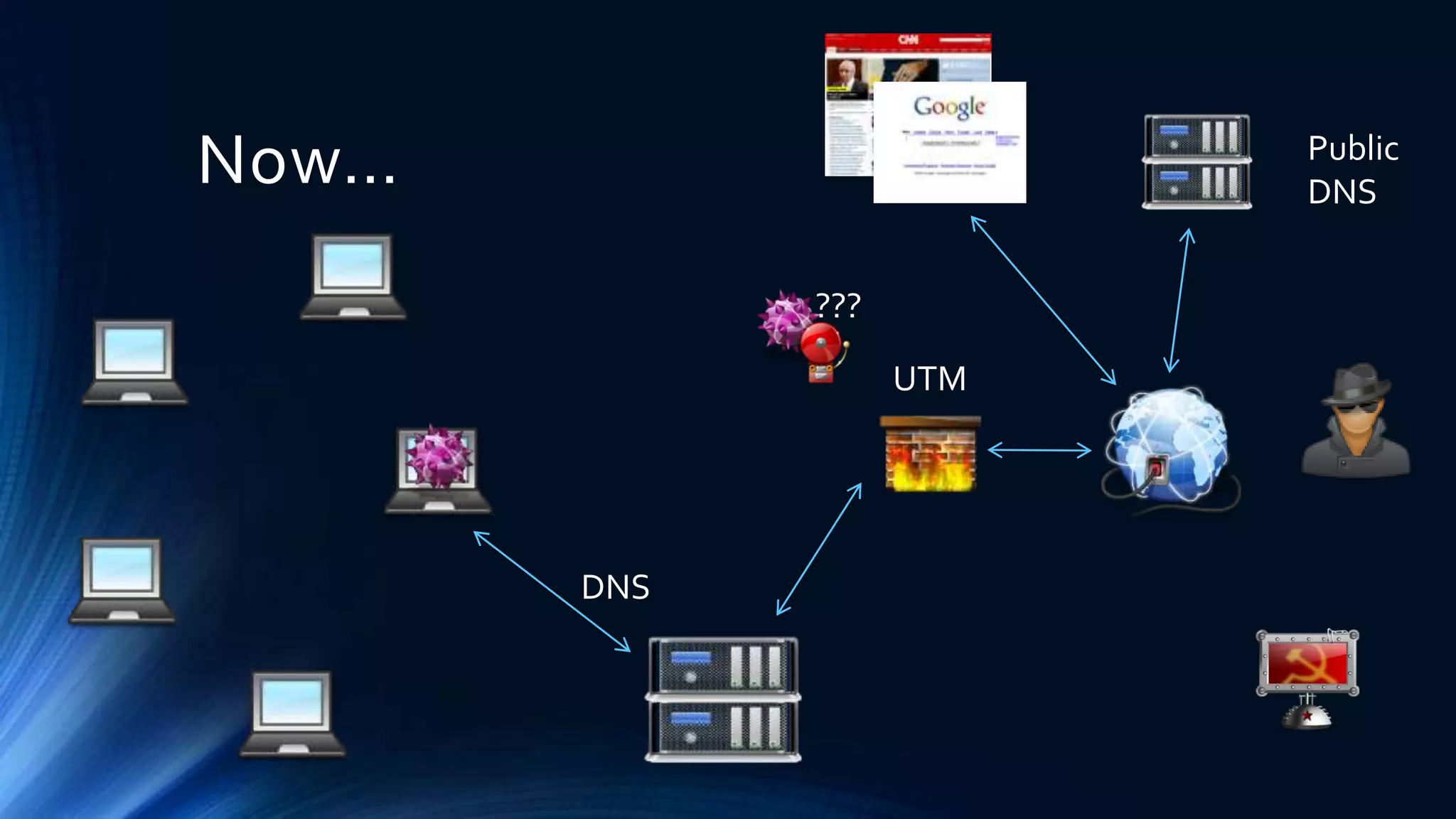
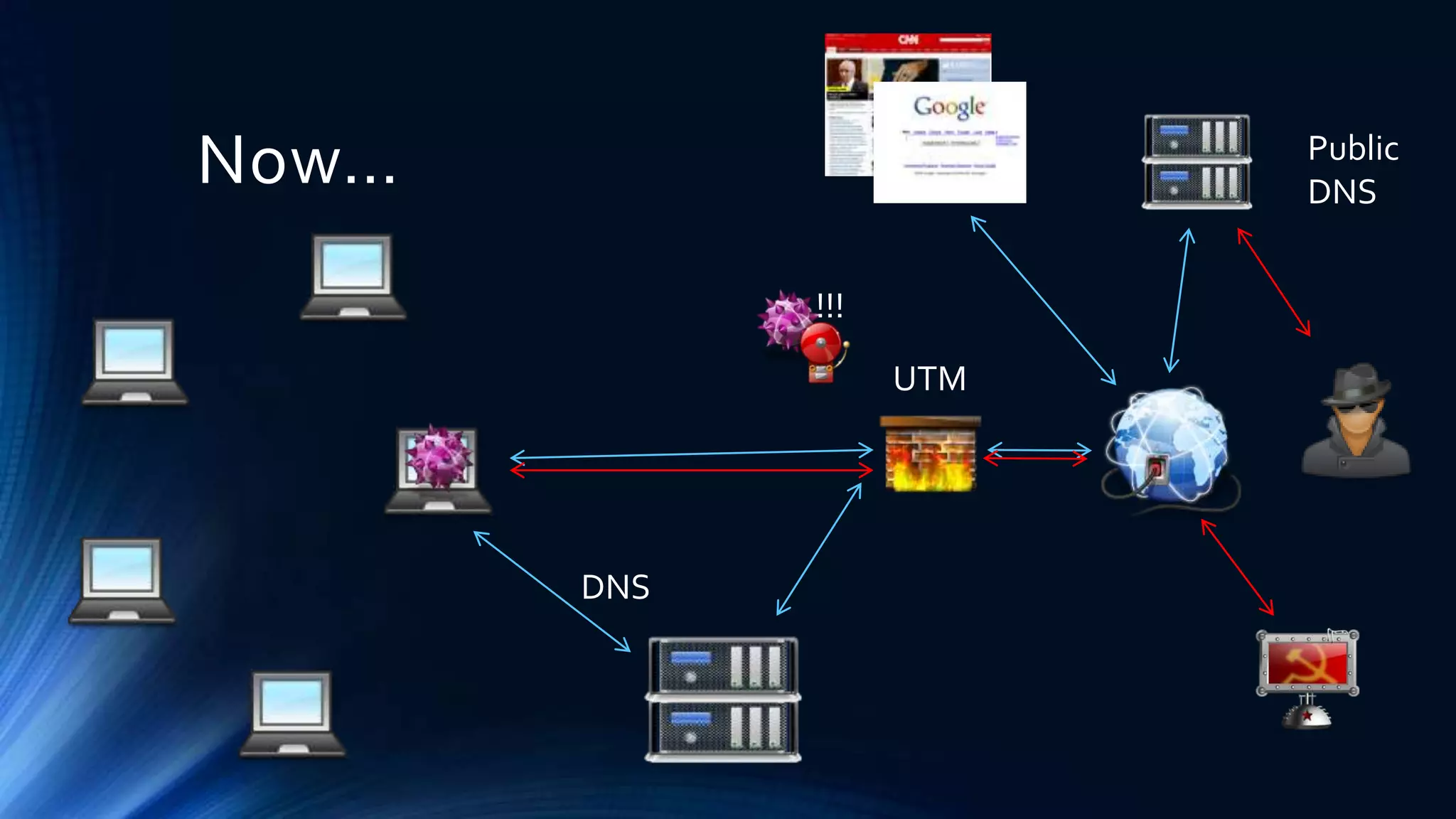
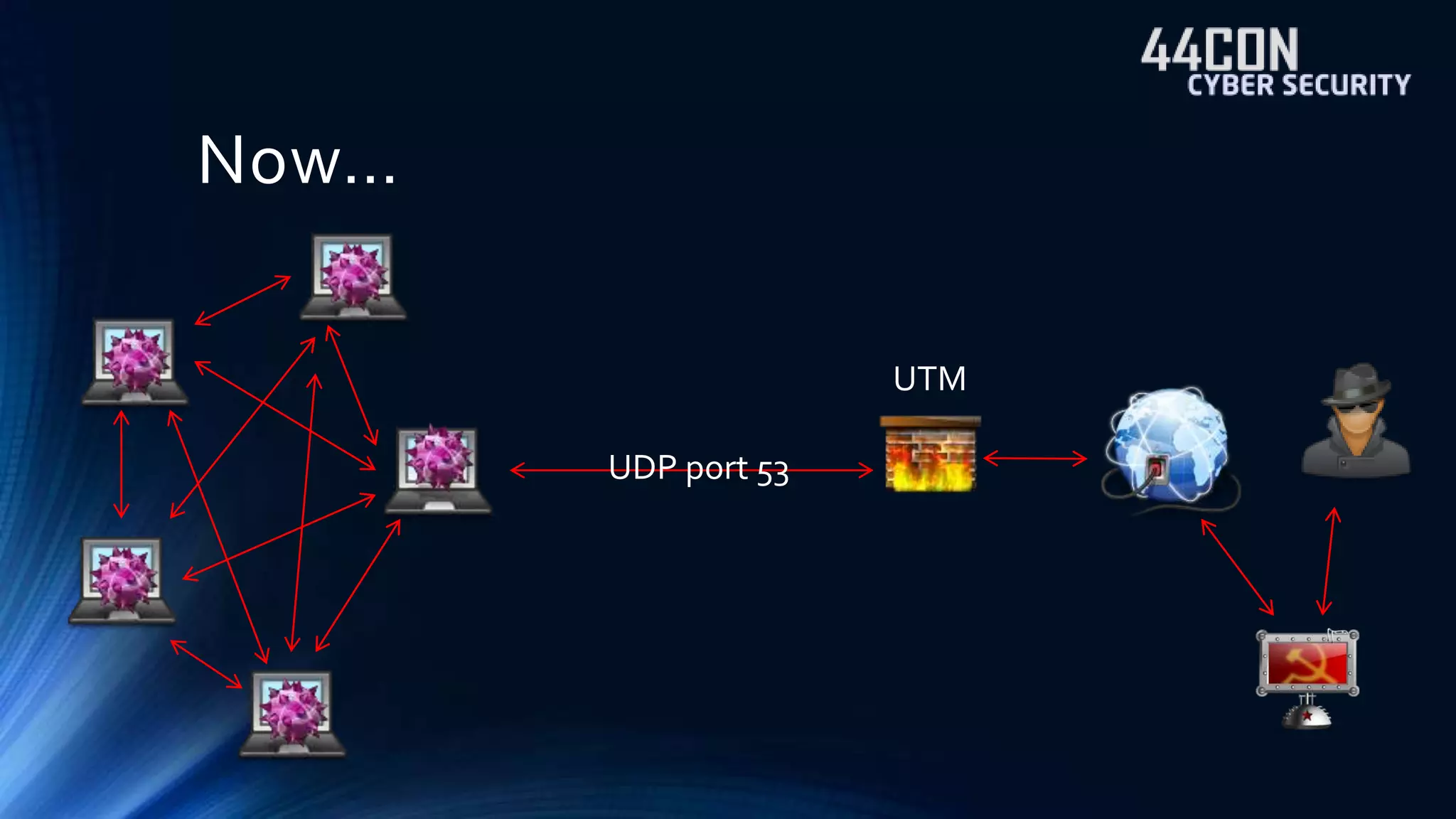
The document discusses strategies for defending against advanced persistent threats (APTs). It notes that many organizations are still relying on network configurations and security tools conceived decades ago. Modern APTs have evolved tactics to avoid detection, like using internal peer-to-peer communications and fast-flux domain naming that evade perimeter-based security tools. The document advocates deploying detection capabilities throughout the network rather than just at the boundary, and maintaining coordinated incident response plans and skills to understand adversaries' techniques.