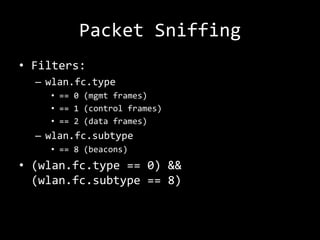
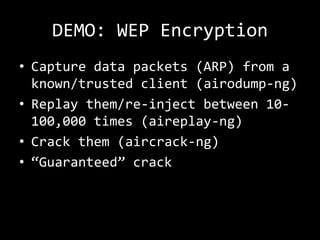
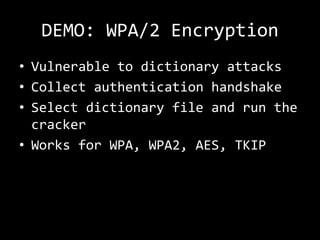
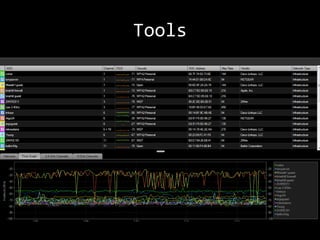
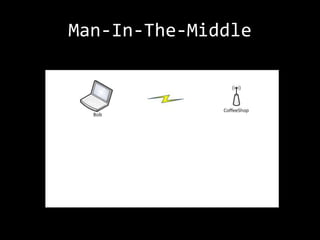
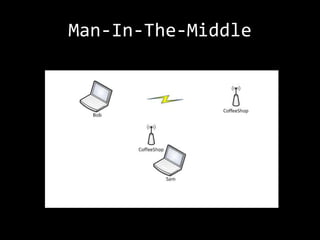
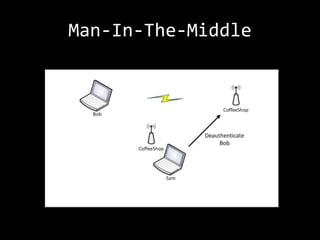
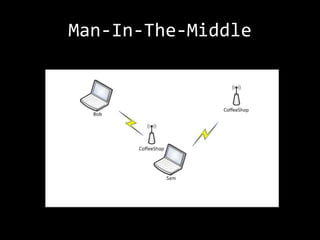
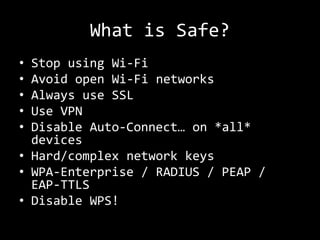
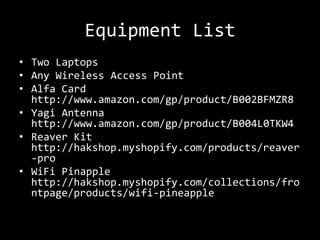
This document summarizes a presentation on wireless security testing and attacks. It describes tools like airodump-ng for packet sniffing, aireplay-ng for packet injection, and aircrack-ng for cracking wireless encryption keys. It demonstrates attacks like cracking WEP encryption, exploiting vulnerabilities in WPS, and performing man-in-the-middle attacks. The presentation emphasizes that these attacks would be illegal to perform without permission and stresses the importance of responsible disclosure.