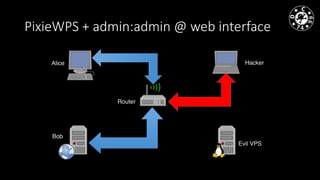
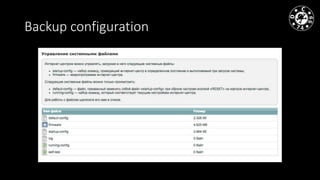
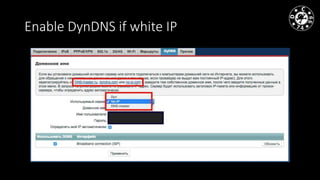
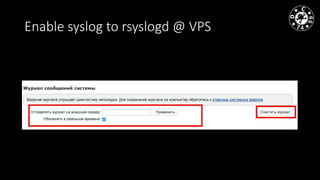
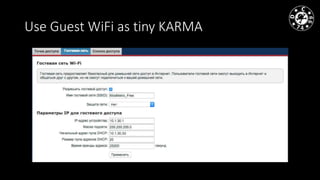
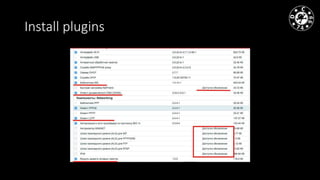
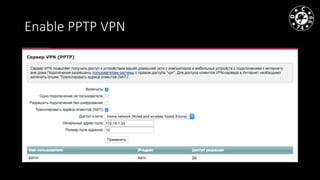
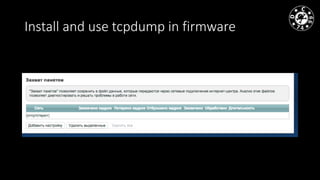
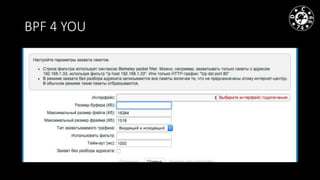
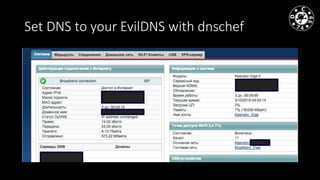
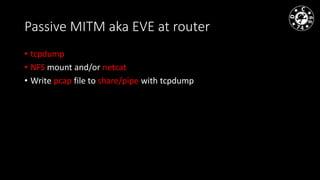
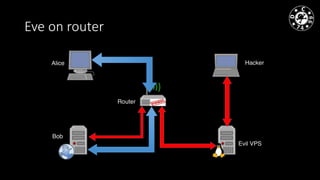
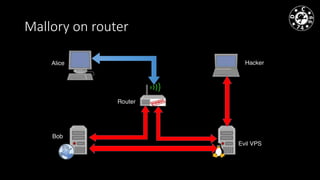
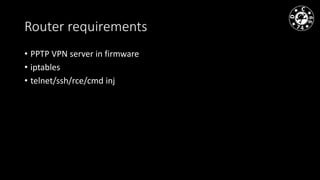
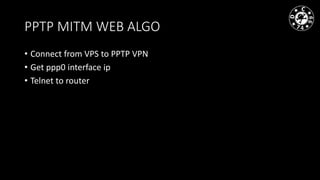
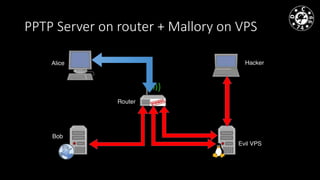
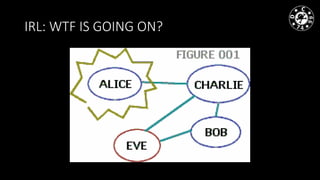
- The document discusses techniques for man-in-the-middle (MiTM) attacks in various conditions and networks.
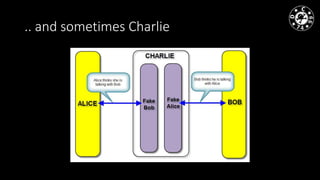
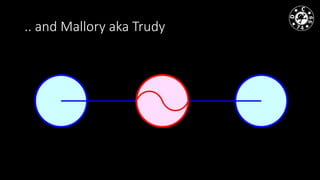
- MiTM attacks are fundamental to communications and can be implemented in different data channels like Ethernet, WiFi, and mobile networks.
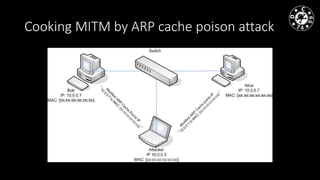
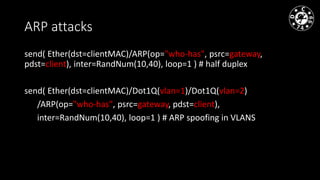
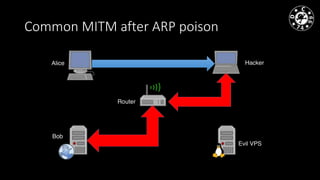
- The author has experience with historical MiTM techniques from the 1990s as well as more modern approaches like ARP cache poisoning to intercept traffic on local networks.