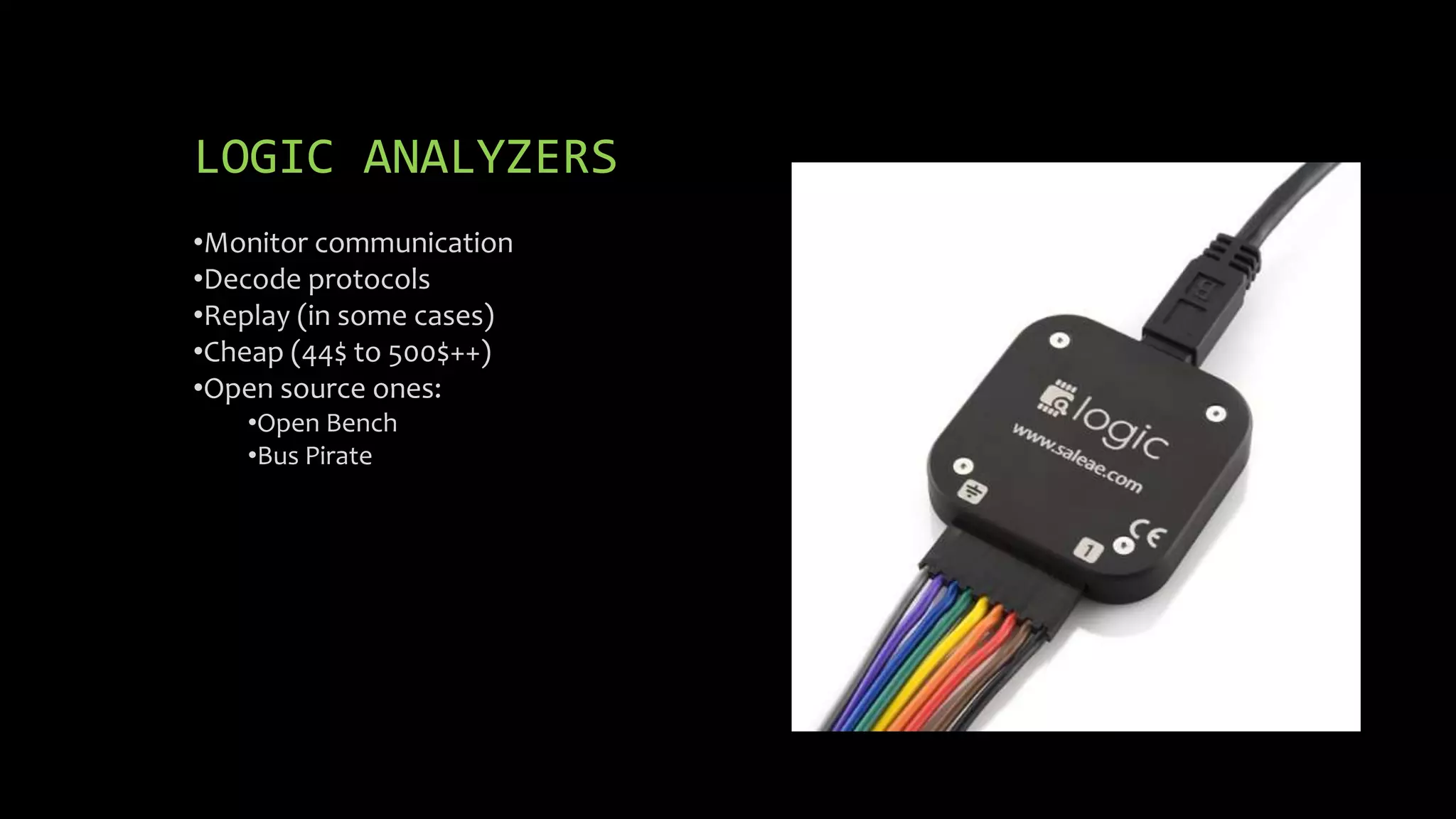
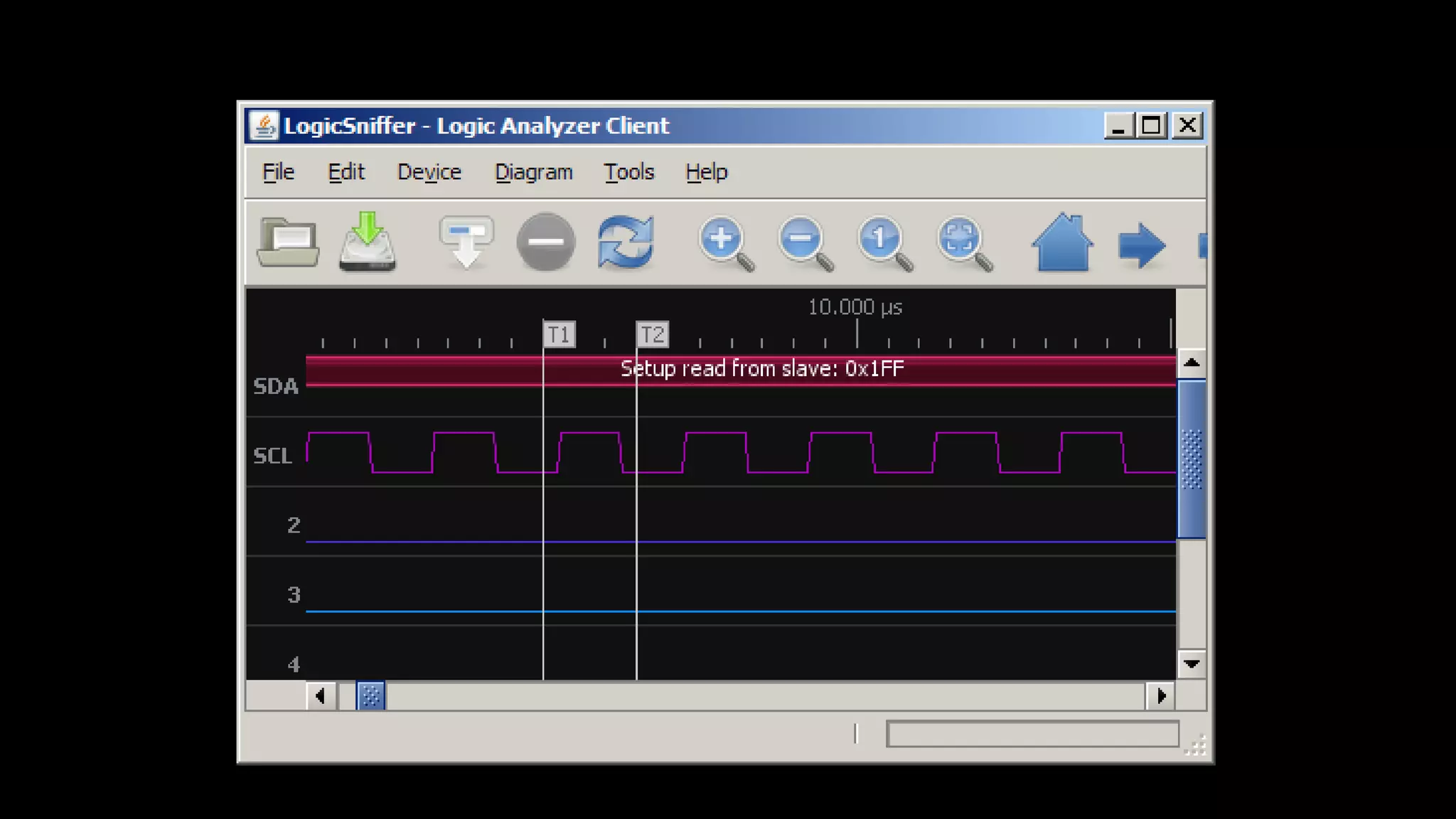
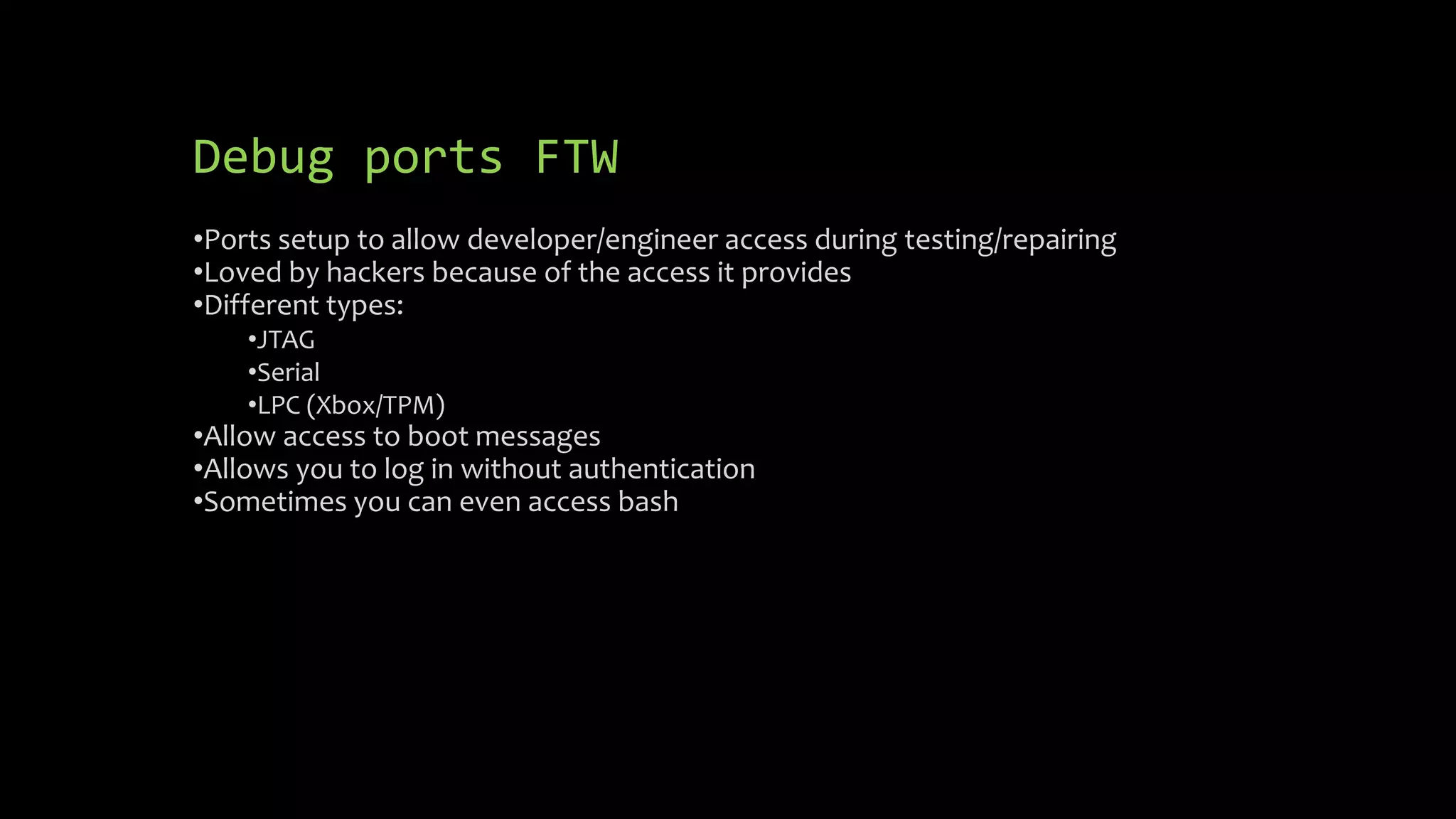
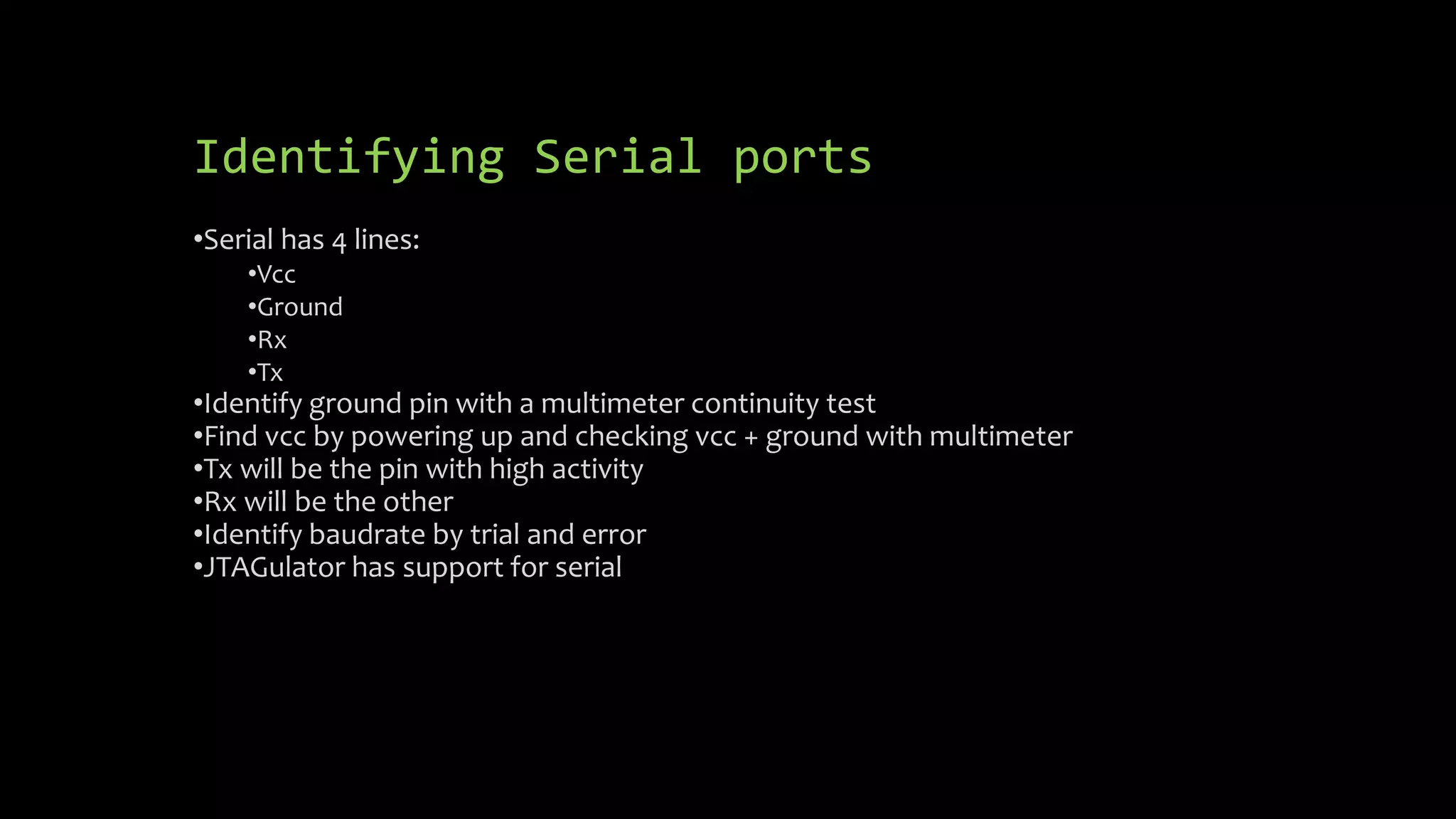
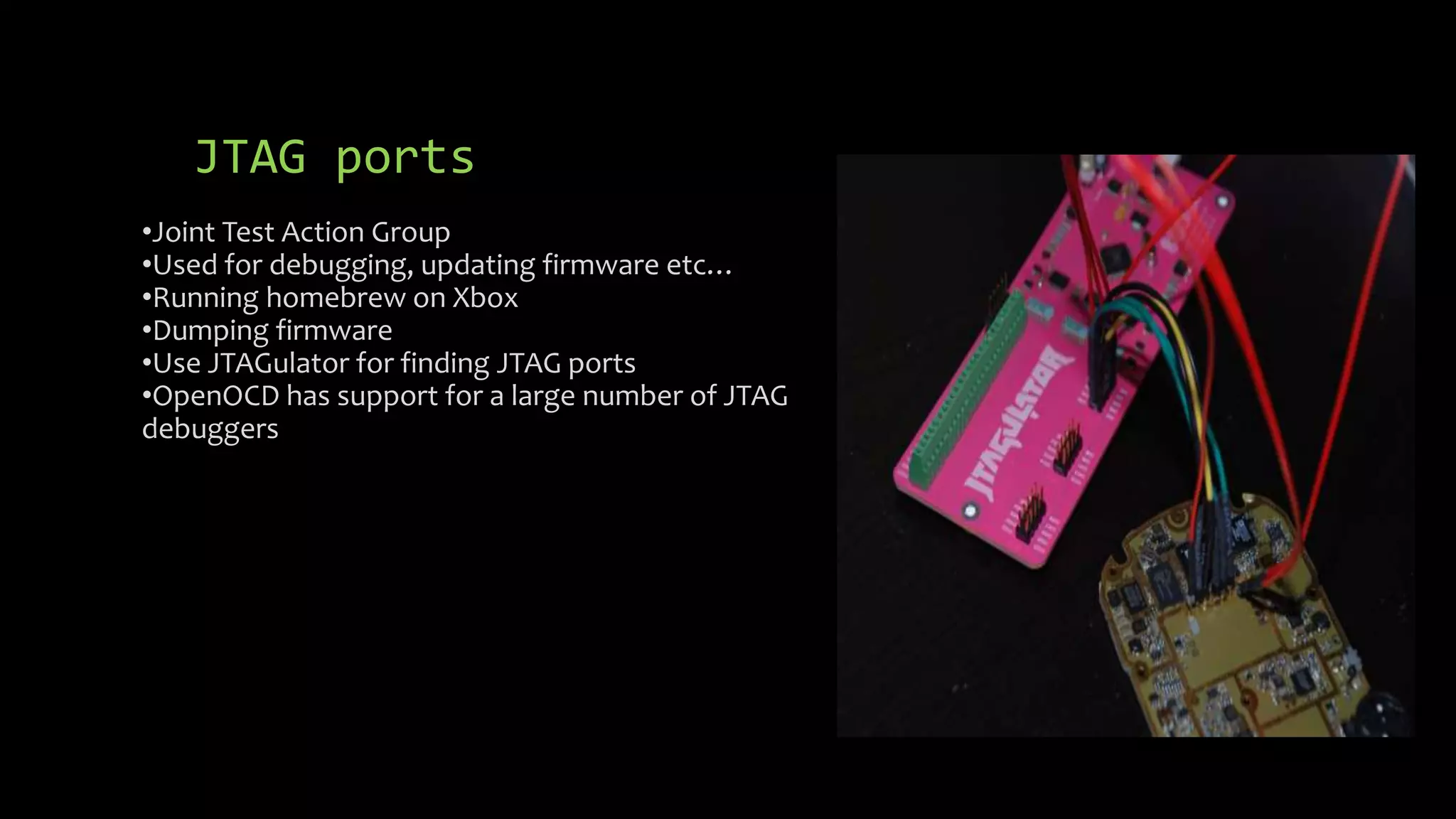
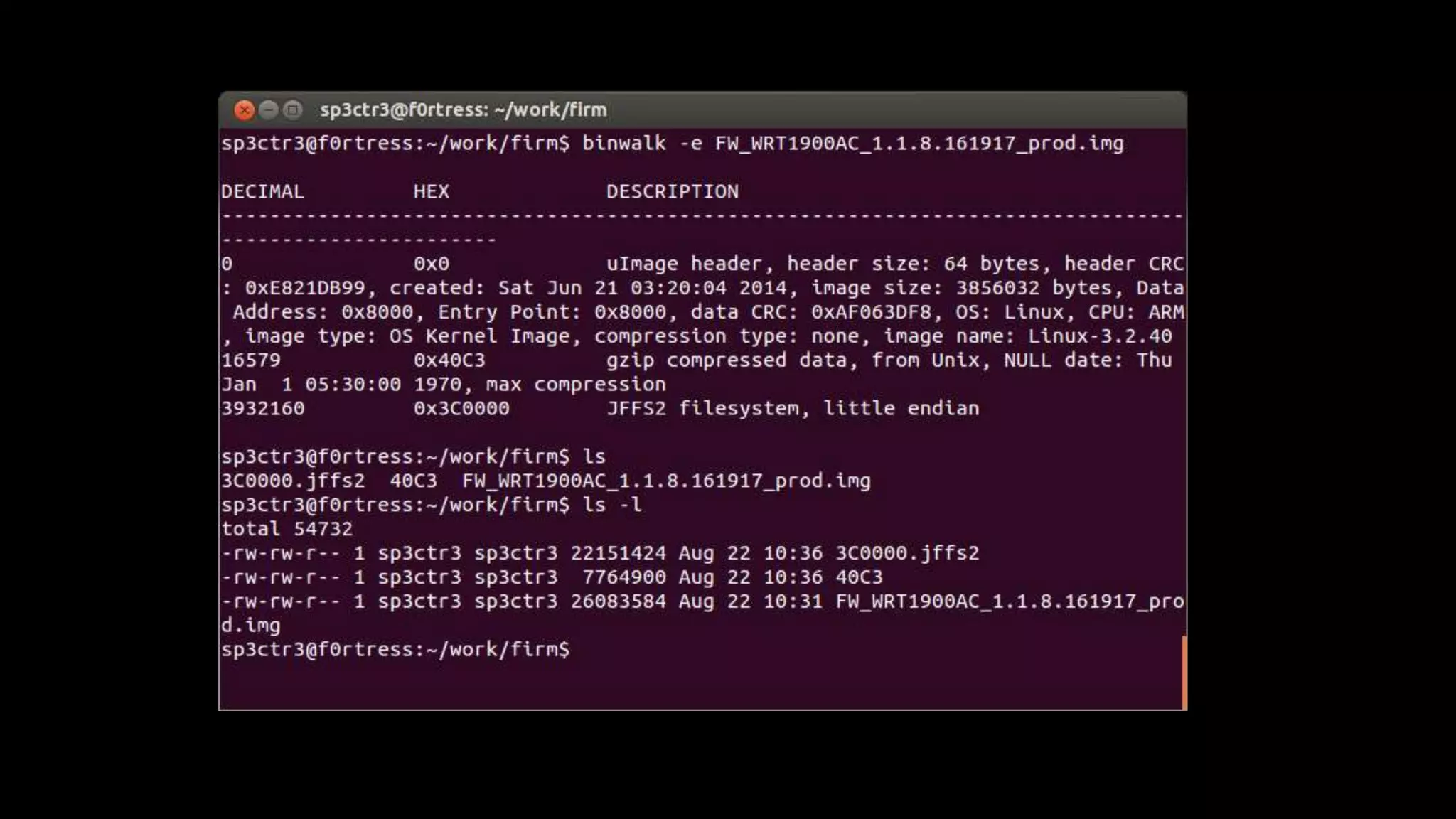
This document discusses security issues in embedded devices and techniques for analyzing and attacking them. It covers identifying debug ports, sniffing communication protocols like SPI and I2C, analyzing radio signals with software-defined radios, extracting firmware from flash memory, analyzing code for vulnerabilities, and defending against such attacks. A variety of open-source tools are recommended for reverse engineering tasks like bus pirate, hackRF, binwalk, and JTAGulator.