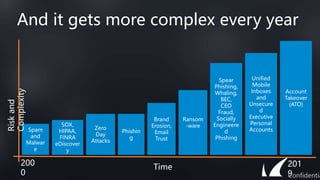
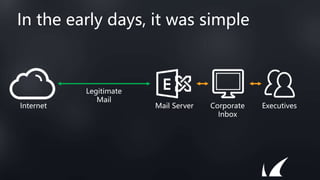
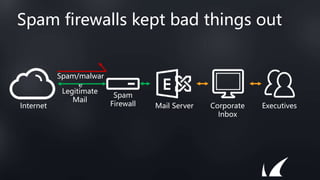
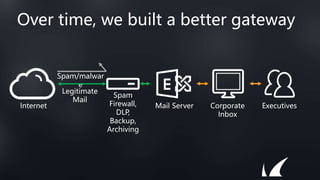
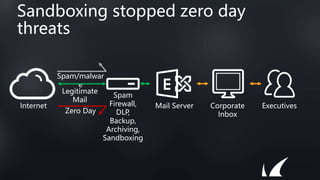
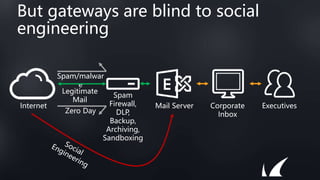
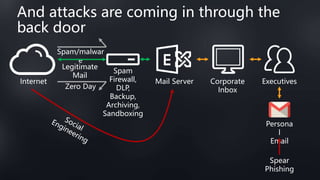
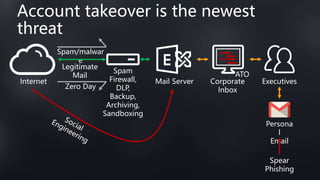
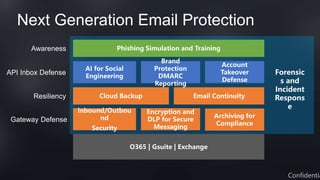
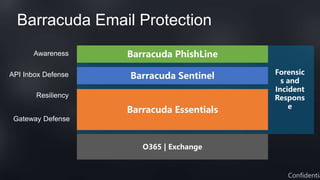
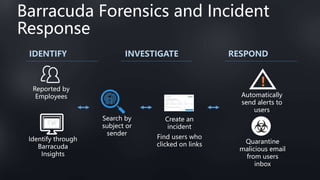
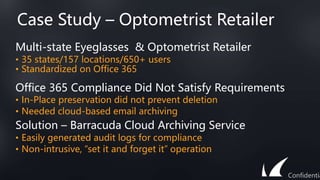
This document discusses Barracuda's email protection solutions. It begins by outlining the increasing threats to email over time, from spam and malware to more advanced targeted attacks. It then describes Barracuda's portfolio of products that provide gateway defense, fraud protection, awareness training, and forensics to secure email against these evolving threats. Case studies demonstrate how Barracuda has helped organizations eliminate spam, prevent account compromise, satisfy compliance needs, and more. The document encourages next steps like learning more on their website or requesting a demo.