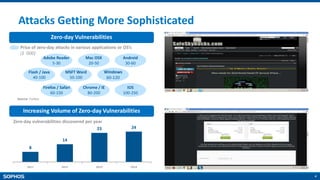
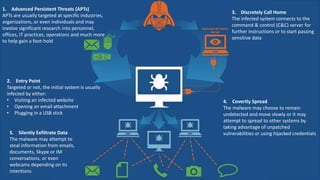
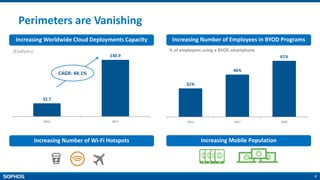
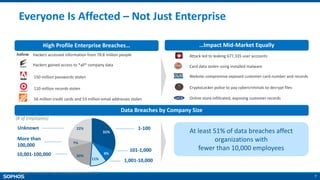
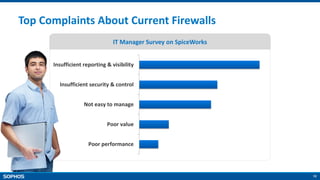
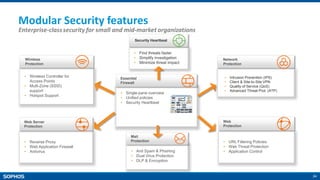
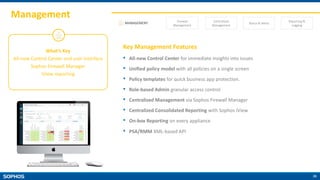
The document provides an overview of the Sophos XG Firewall. It discusses how the IT landscape is changing with increasing attacks and the blurring of network perimeters. It then introduces the Sophos XG Firewall as having the following key attributes:
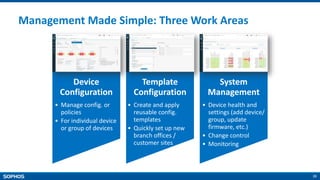
- Simple and easy to use interface
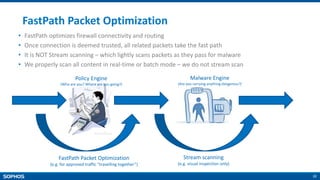
- Lightning fast performance with FastPath packet optimization
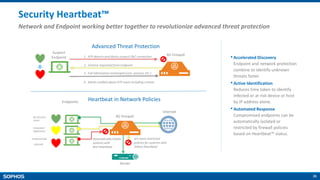
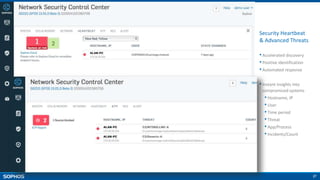
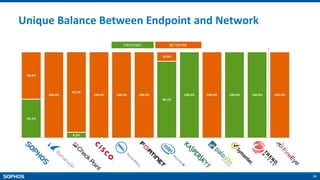
- Unparalleled protection with features like Security Heartbeat that links endpoints and firewalls
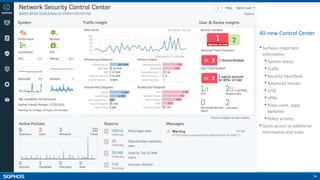
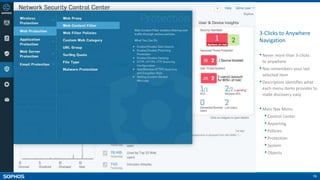
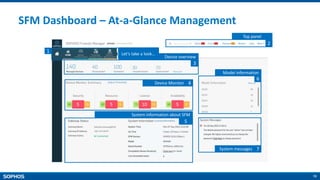
- On-box reporting and visibility tools
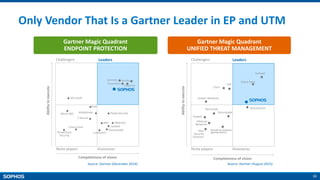
- Backed by Sophos as a trusted industry leader in cybersecurity




















![44
Competitive Chart Sophos
XG Firewall
Fortinet
FG 20-90
Dell SonicWALL
TZ Series
WatchGuard
XTM Series
Network Firewall/Protection
Advanced threat protection
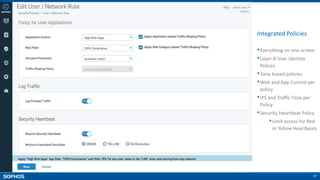
Network and Endpoint Integration [Heartbeat]
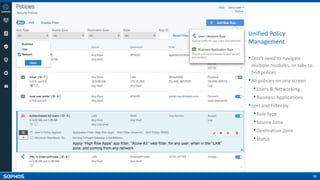
Unified Policies
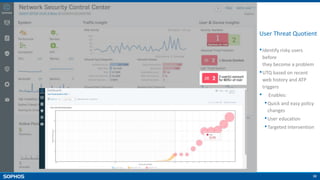
User Risk Visibility [User Threat Quotient]
FastPath Packet Optimization
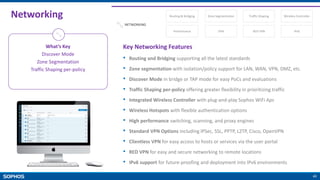
Site to site and remote user VPN
Secure web gateway
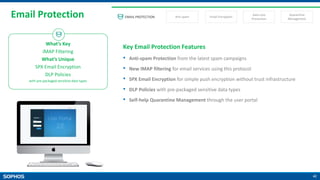
Complete Email Protection [AV, AS, Enc., DLP]
Dual antivirus
Wi-Fi
Reverse proxy
Web application firewall
User portal
Full Reporting
Best TMG feature parity
Discover (TAP) Mode Deployment
$ $
$ $ $
$ $ $
$ = Another product required
New Differentiators
•New competitive differentiators
•Heartbeat
•Unified policy
•User Threat Quotient
•New comparative differentiators
•FastPath
•Discover Mode
•User-based Firewall Policies](https://image.slidesharecdn.com/xg-firewall-webcast-161020171726/85/XG-Firewall-44-320.jpg)