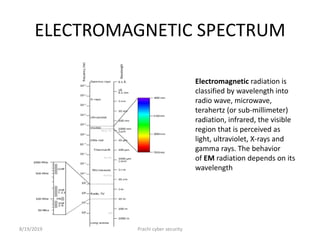
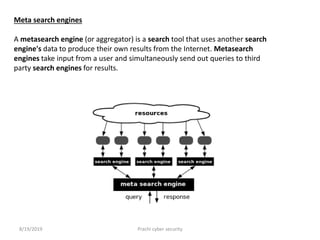
Virtual reality uses electronic equipment to simulate a 3D environment that can be interacted with, while cyberspace refers to the notional environment where communication over computer networks occurs. Cyberspace can be thought of as a virtual reality where one can navigate computer networks. Cyberspace provides opportunities to reshape society and culture through hidden identities and borderless communication, though some argue its use of spatial metaphors is misleading.

![CYBERSPACE AS A METAPHOR FOR
INTERNET
Metaphor is a thing regarded as representative or symbolic of something else.
According to this interpretation, events taking place on the Internet are not
happening in the locations where participants or servers are physically located, but
"in cyberspace". So that a website, for example, might be metaphorically said to
"exist in cyberspace.
Cyberspace provides new opportunities to reshape society and culture through
"hidden" identities, or it can be seen as borderless communication and culture.
Cyberspace is the "place" where a telephone conversation appears to occur. Not
inside your actual phone, the plastic device on your desk. Not inside the other
person's phone, in some other city. The place between the phones. [...]
8/19/2019 Prachi cyber security](https://image.slidesharecdn.com/cyberspace-190819091638/85/Cyberspace-2-320.jpg)