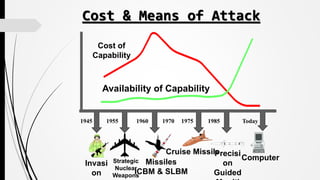
The document discusses the emerging threat of cyber terrorism and how terrorists can use internet-based attacks to cause widespread disruption and damage. It notes that cyber terrorism allows attackers to remain anonymous, has no boundaries, and costs little to perpetrate. Common cyber attack methods include hacking, introducing viruses, website defacing, and denial-of-service attacks. Examples of past cyber terrorist incidents like the 9/11 attacks, 2008 Ahmedabad bombings, and 2008 Mumbai attacks are described. The document emphasizes the importance of prevention through maintaining security software and being cautious online to avoid becoming victims of cyber terrorism.