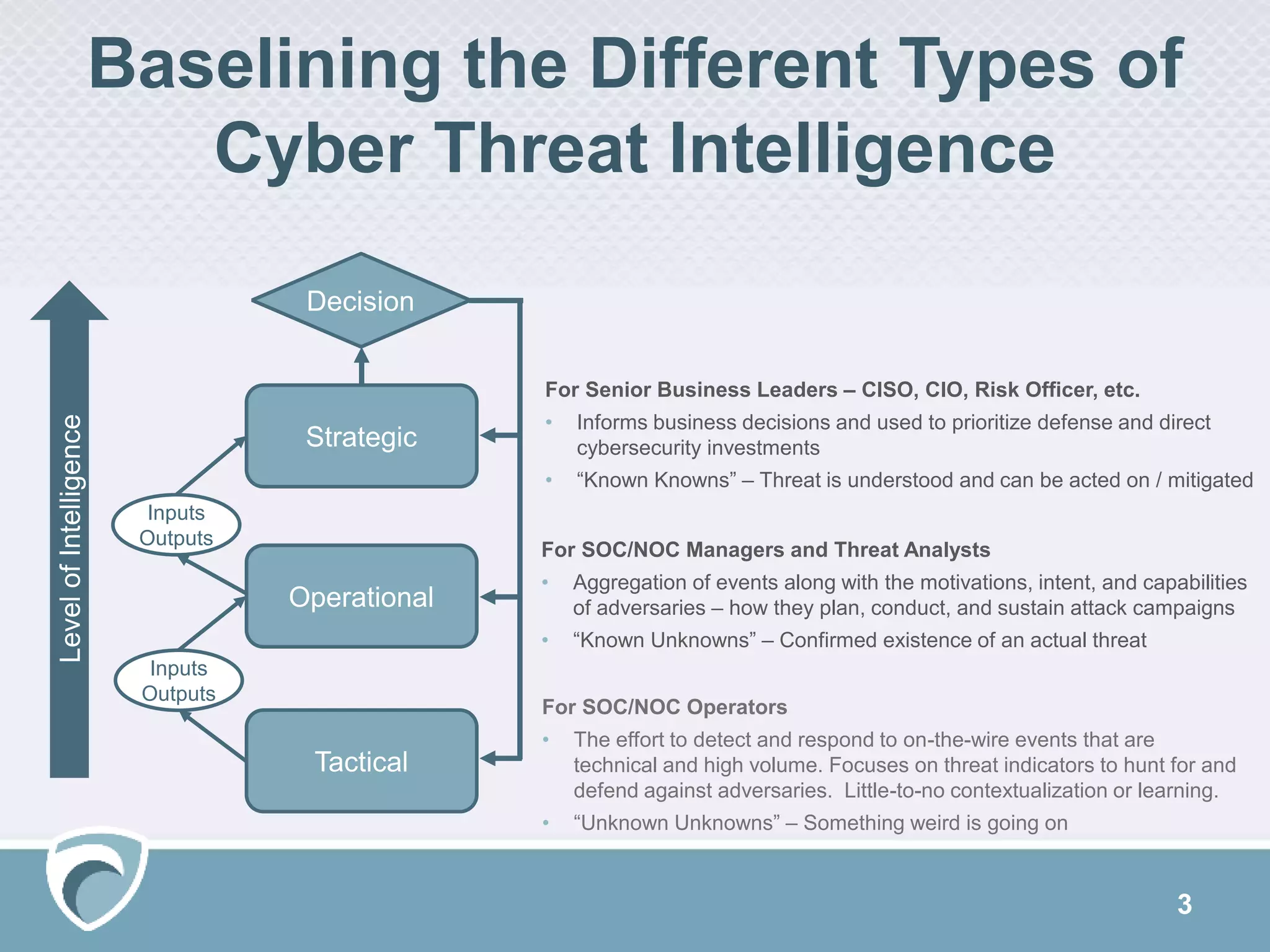
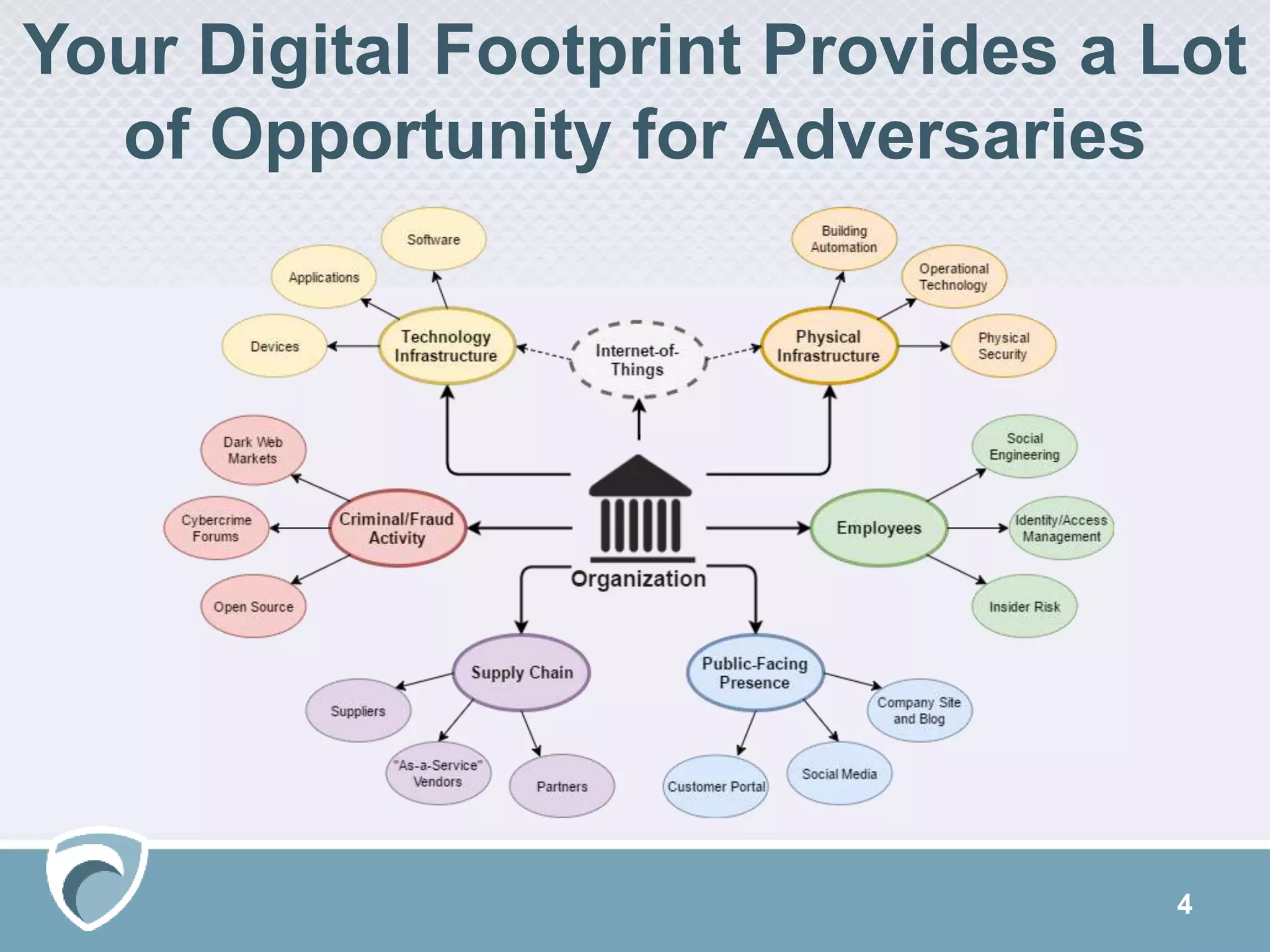
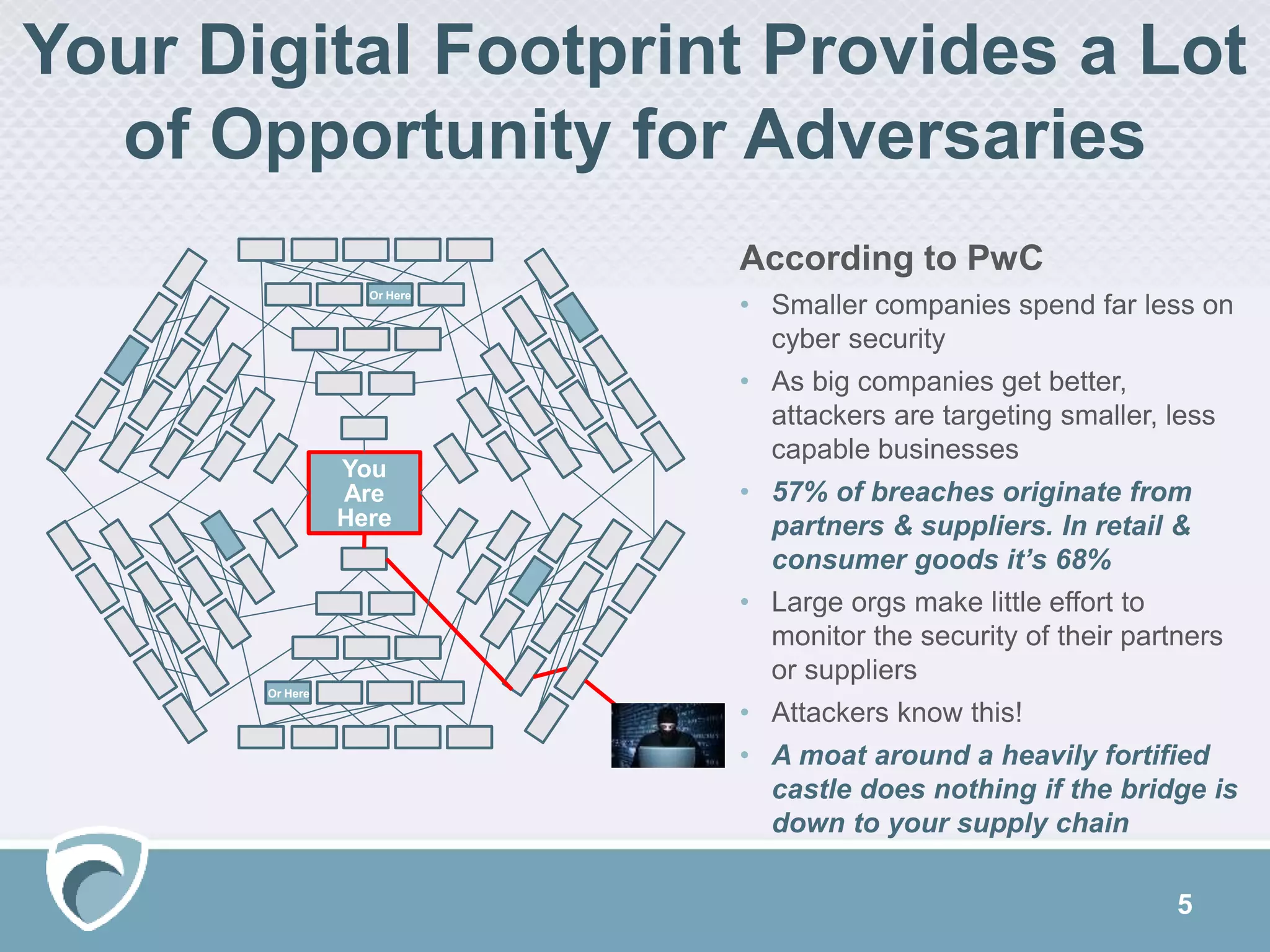
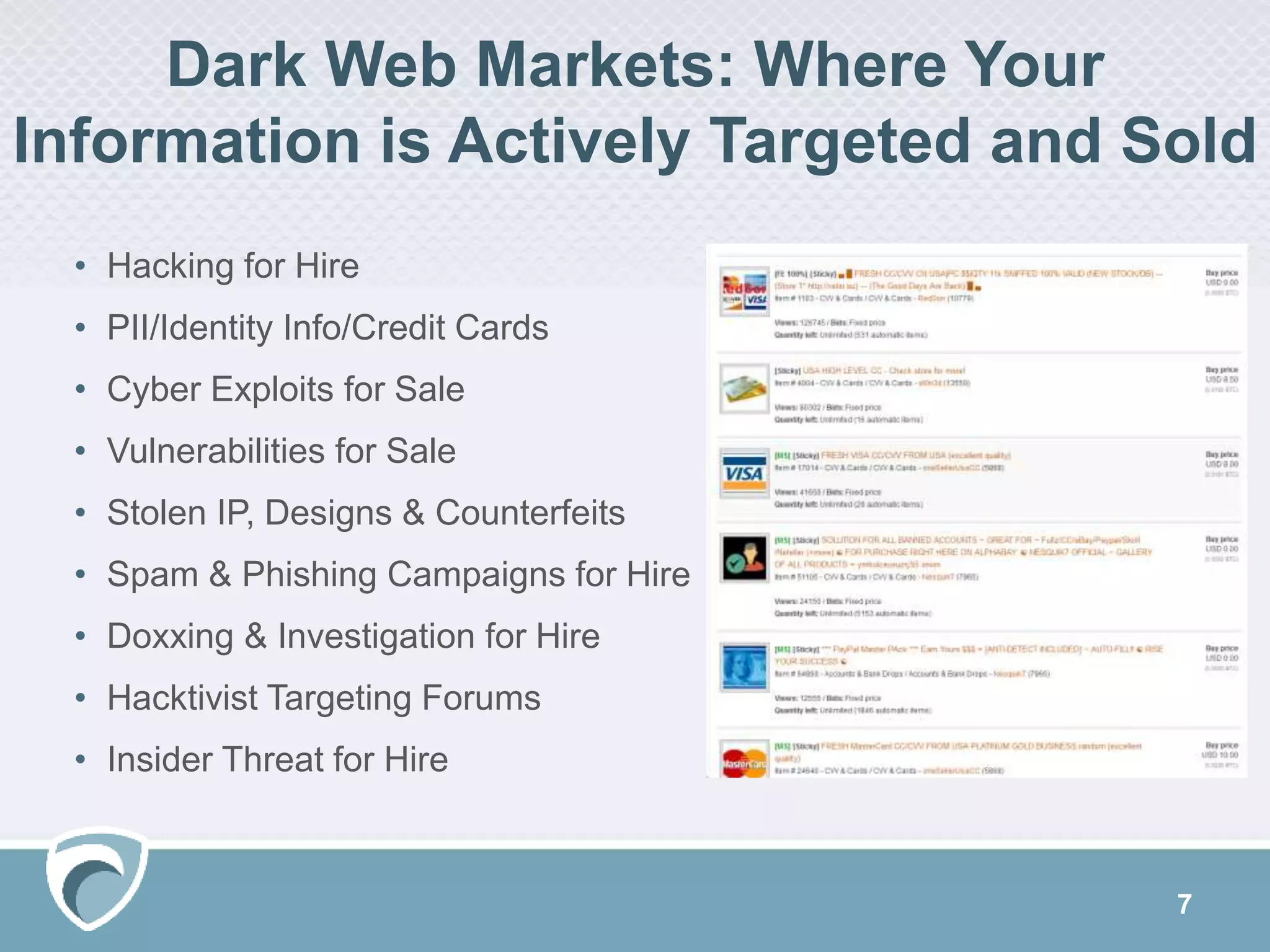
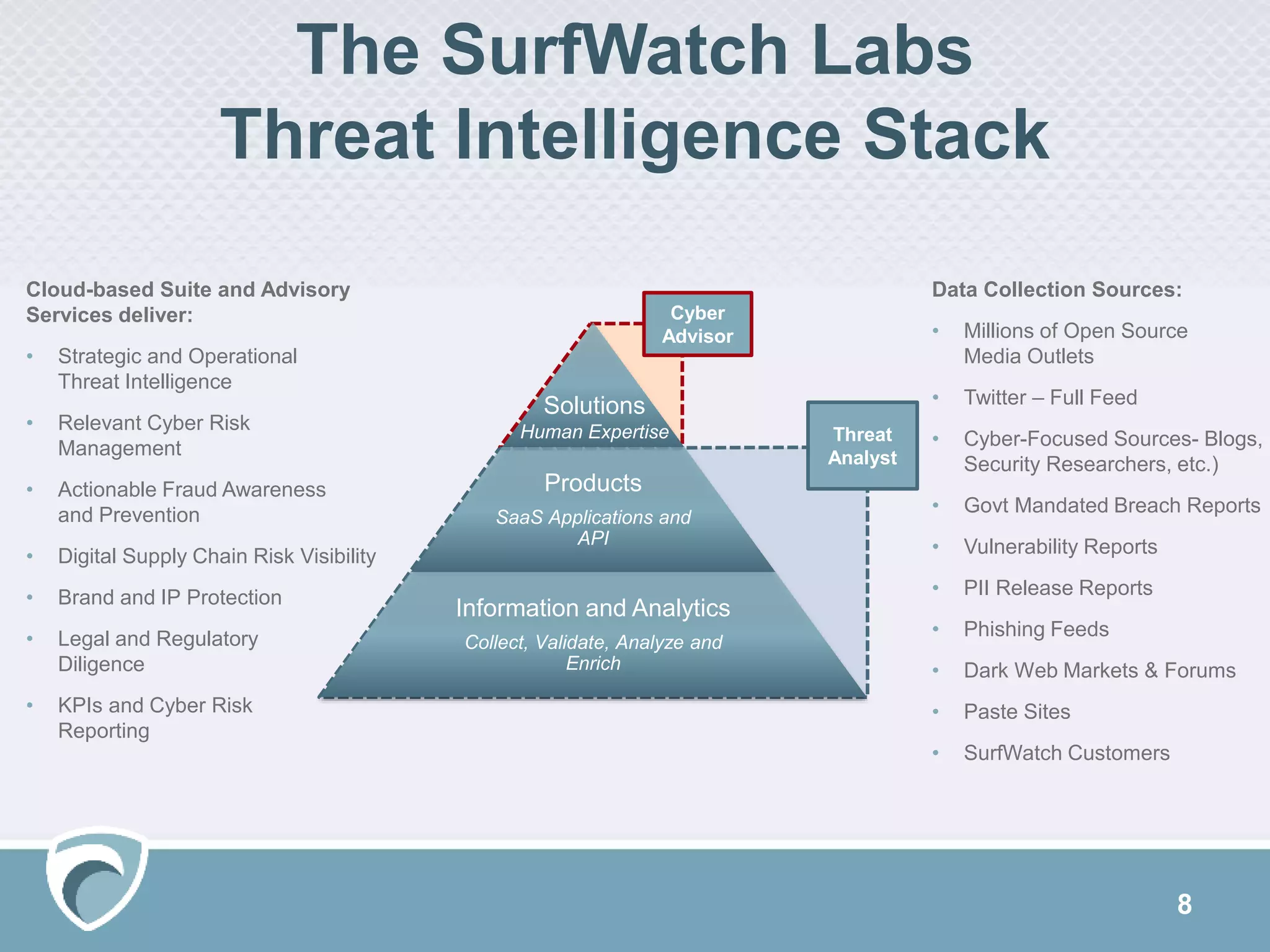
The document discusses using Surfwatch Labs' threat intelligence to manage third-party cyber risks, emphasizing the different types of threat intelligence: 'known knowns', 'known unknowns', and 'unknown unknowns'. It outlines the importance of understanding digital footprints and highlights that a significant percentage of breaches come from partners and suppliers, particularly affecting smaller businesses. Practical risk mitigation strategies include ensuring vendor compliance, gaining visibility of connected parties, and leveraging both internal and external threat intelligence.