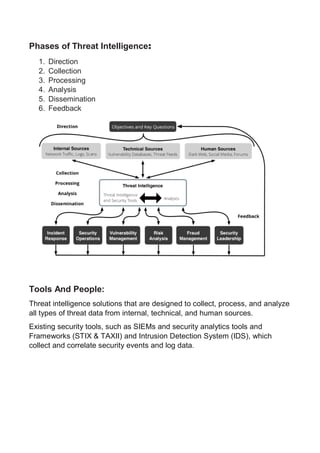
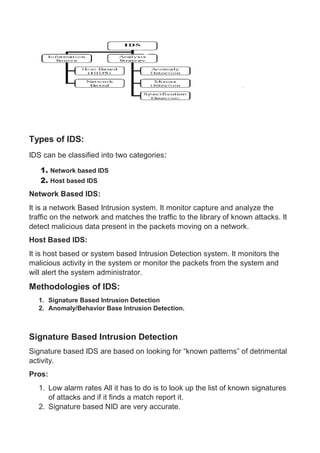
Cyber threat intelligence involves collecting, analyzing, and sharing information about threats to help organizations assess risks and defend themselves. It follows principles like being centralized, objective, and continuous. The Structured Threat Information Expression (STIX) framework allows sharing threat data consistently between organizations using common language. Intrusion detection systems monitor networks and systems for malicious activity, using either signature-based methods to detect known threats or anomaly-based methods to find unknown behaviors.