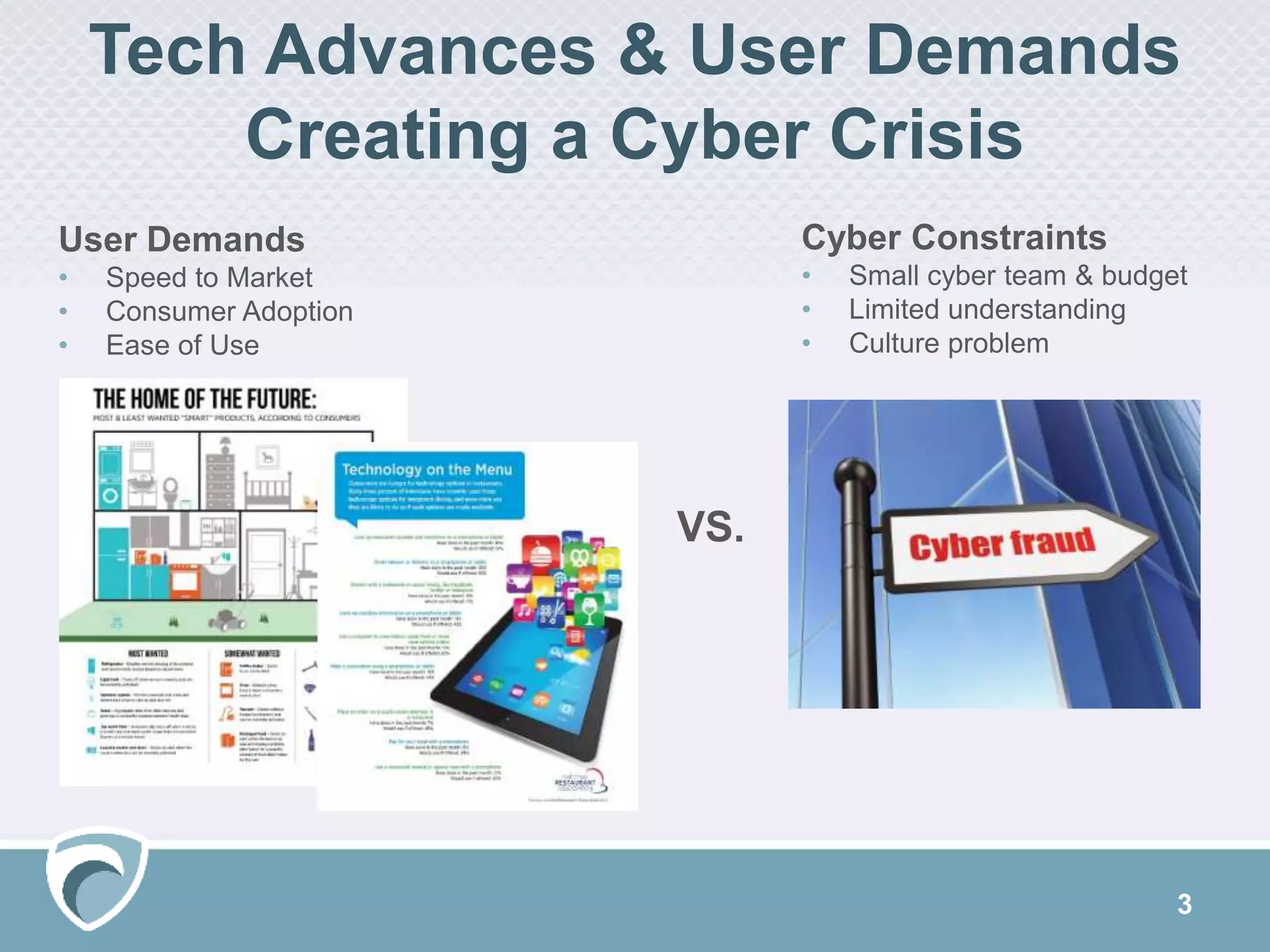
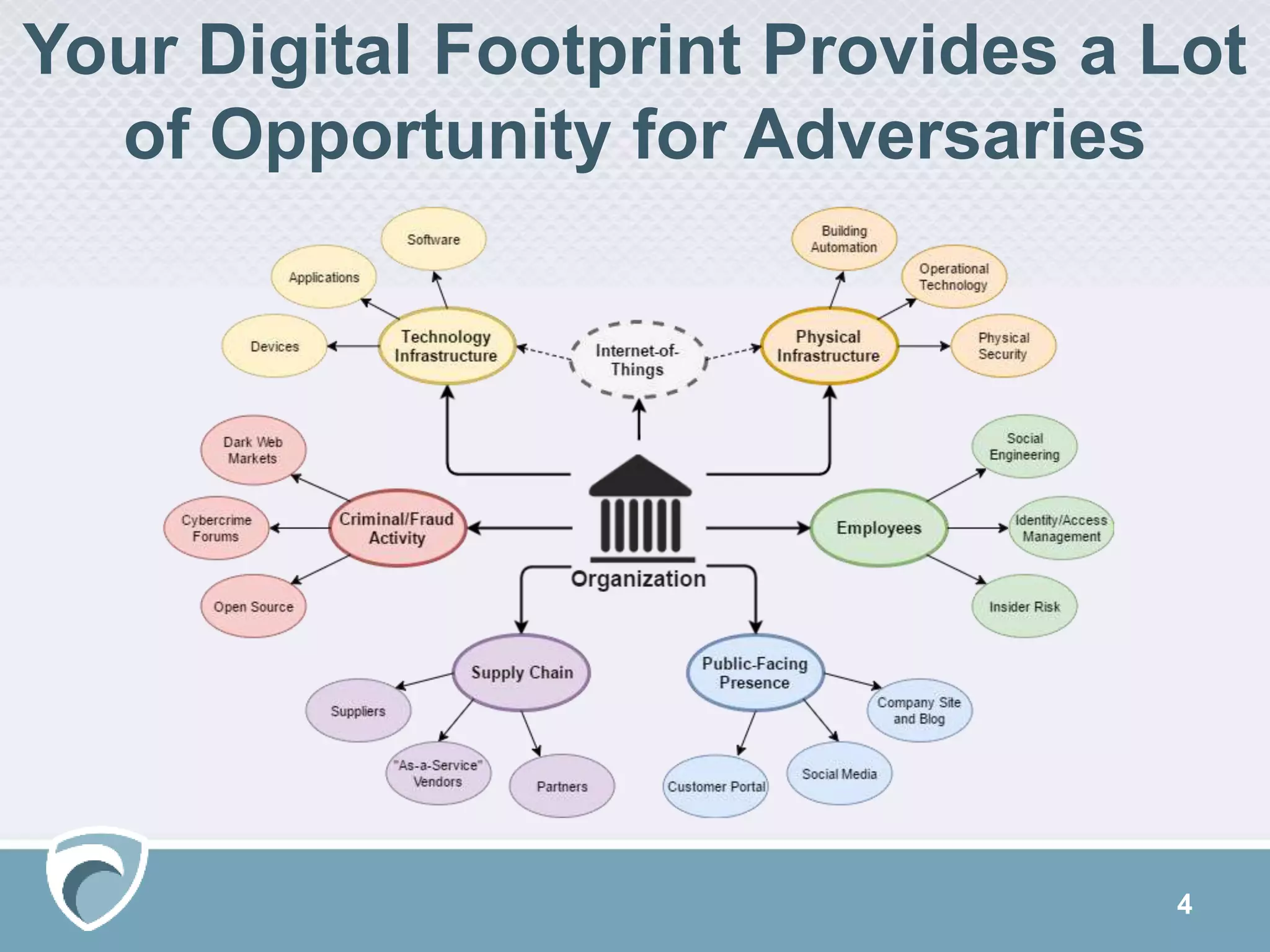
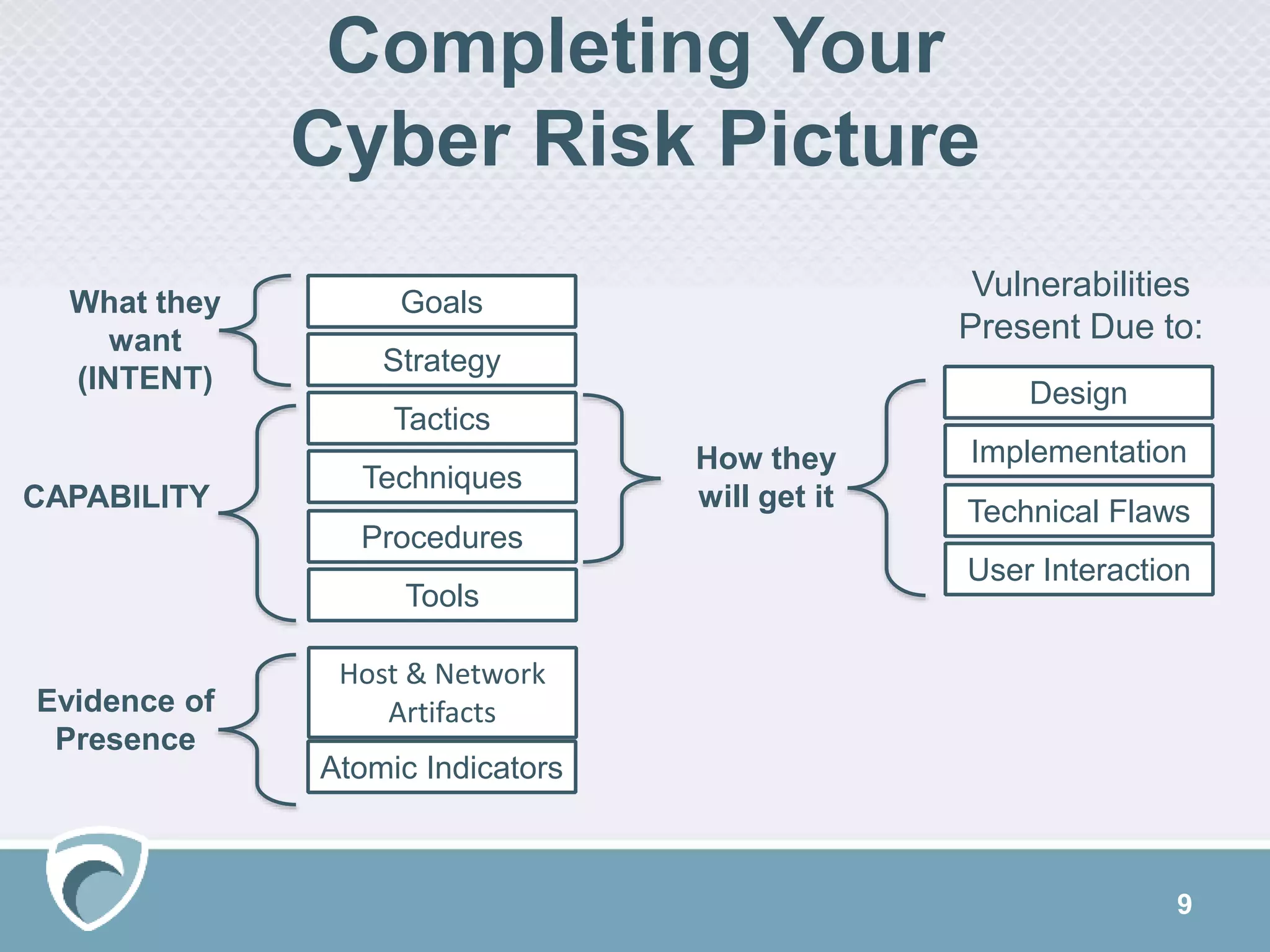
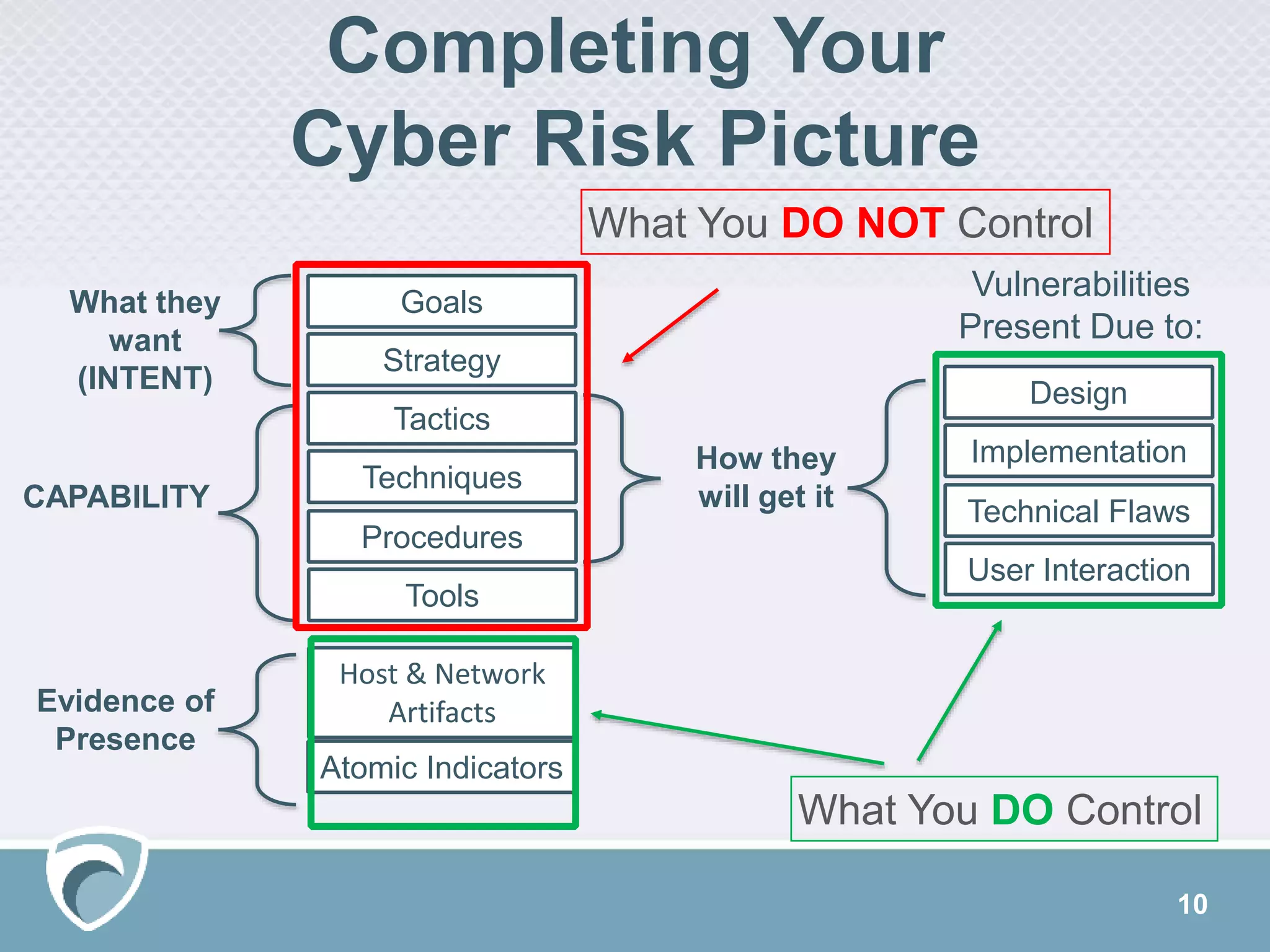
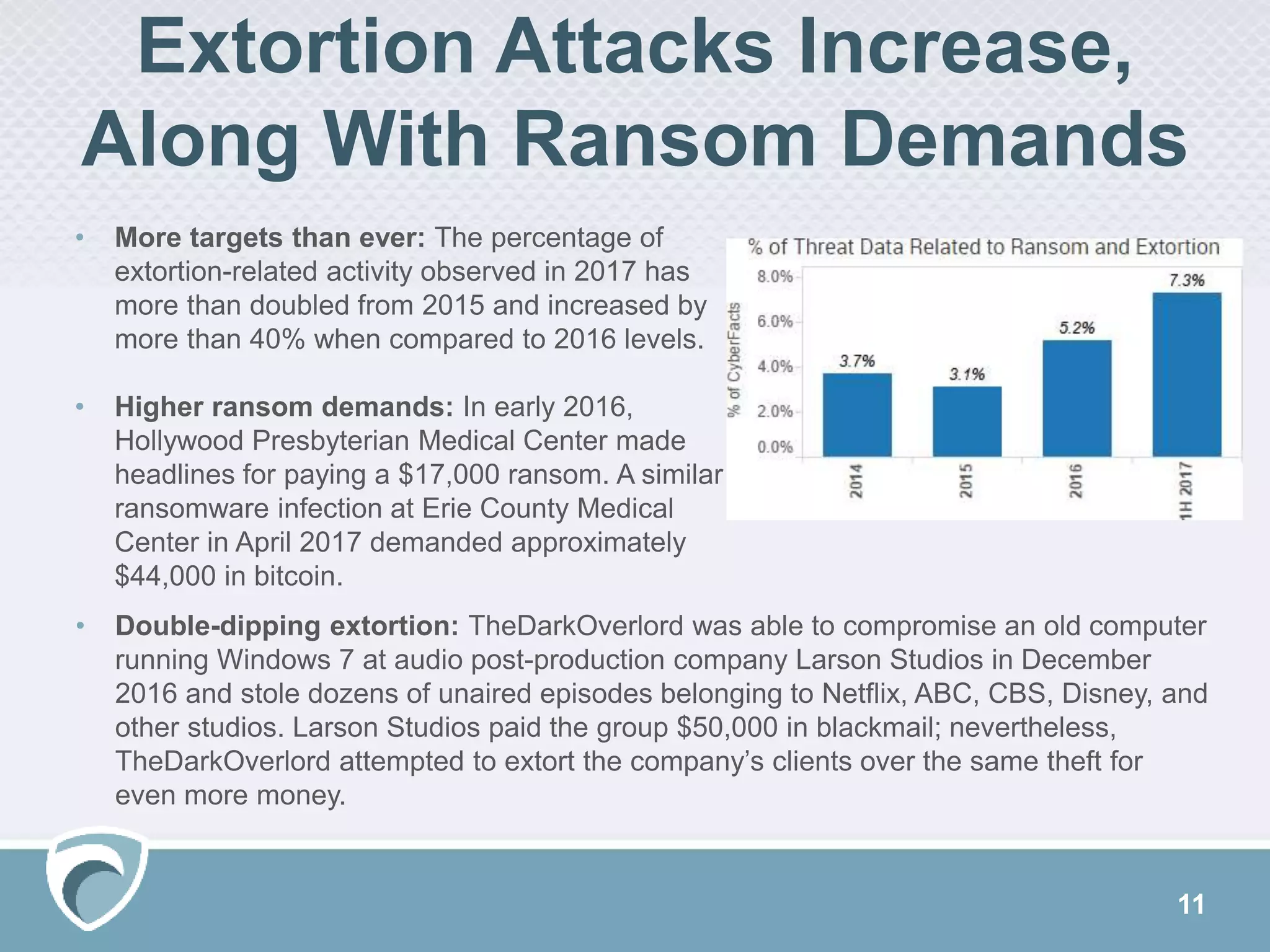
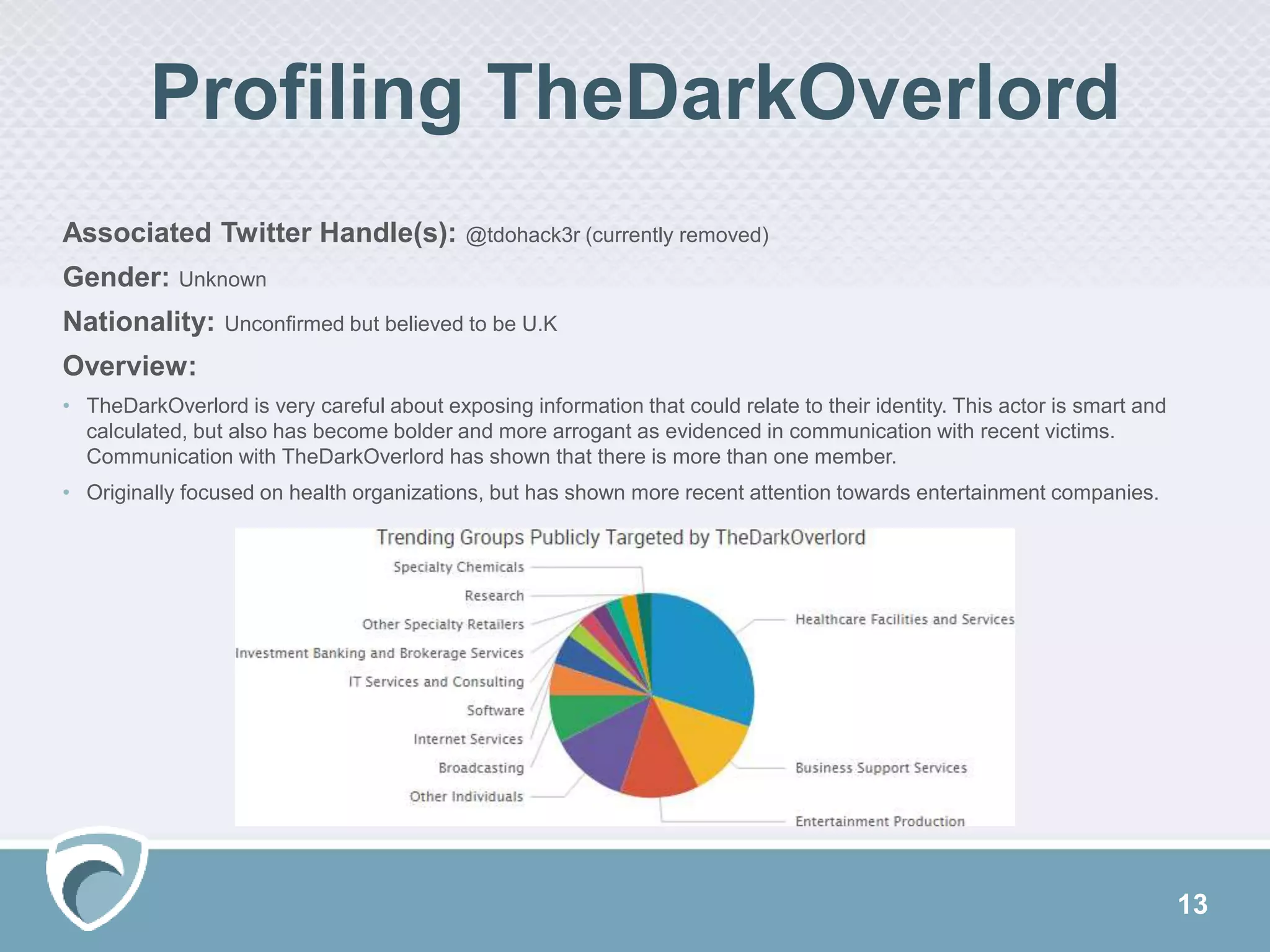
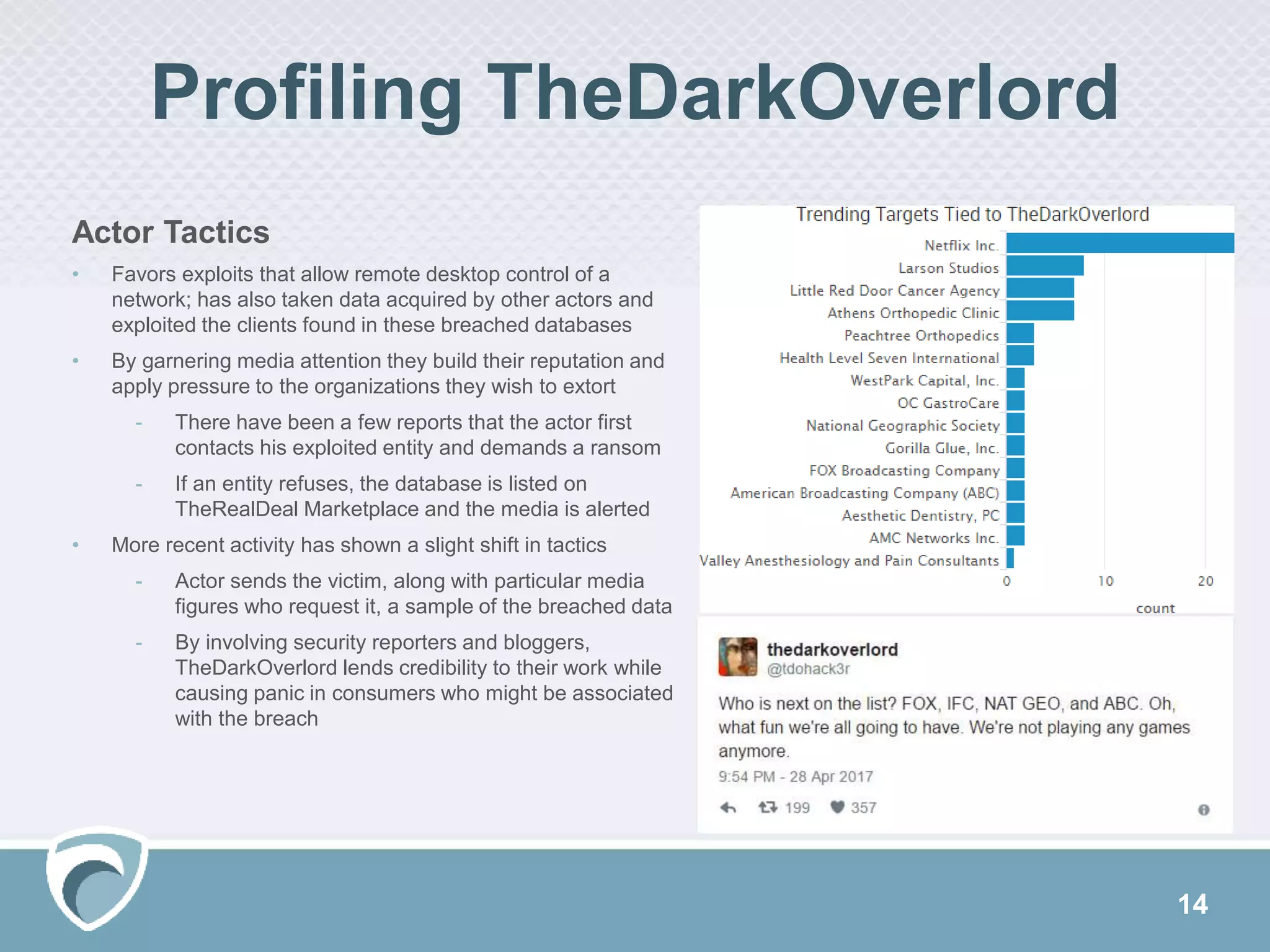
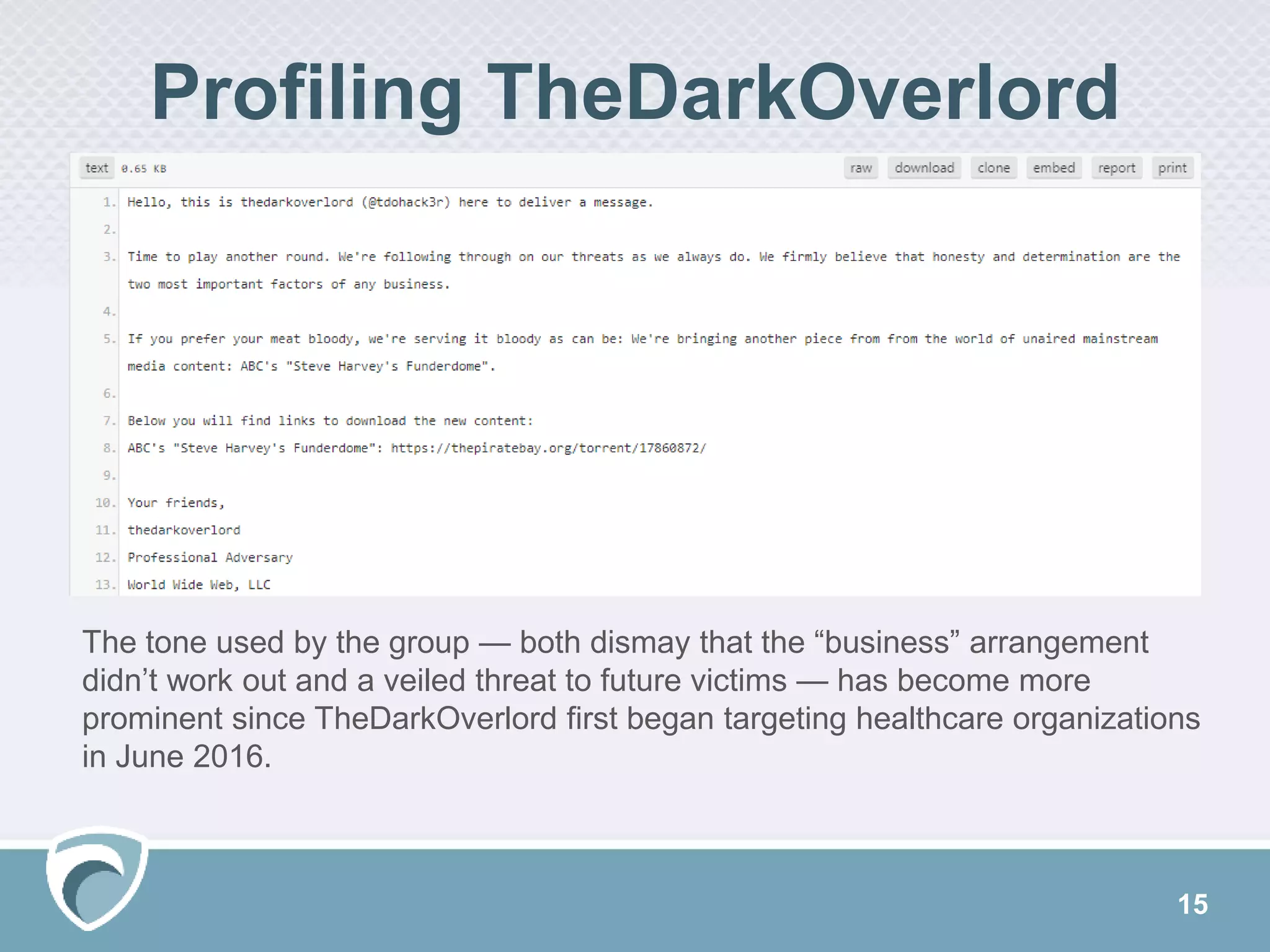
This document discusses evolving cyber threats and how adversaries target organizations. It notes that criminals shift tactics to hit attractive soft targets, exploiting technical flaws and user interactions. One group discussed, called TheDarkOverlord, uses extortion by threatening to publish stolen data if ransom is not paid. The document stresses the importance of understanding adversaries' goals and capabilities in order to minimize risks and reduce vulnerabilities.