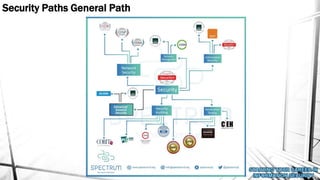
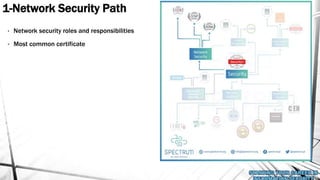
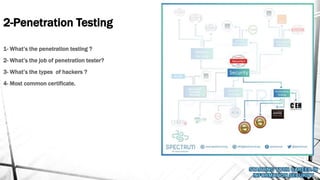
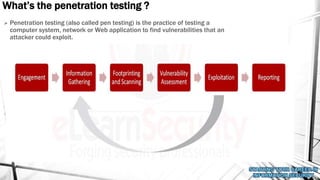
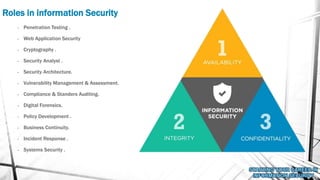
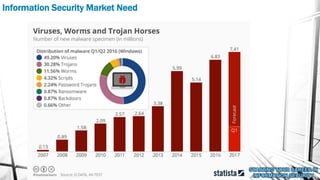
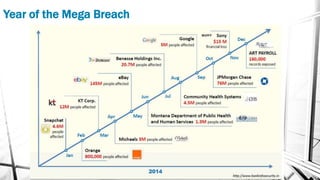
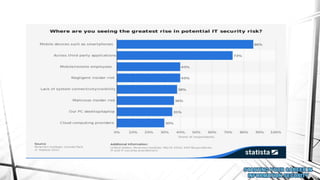
This document outlines a presentation on information security. It discusses what information security is, general paths in security like network security and penetration testing, roles in information security, opportunities in the Middle East market, how to start in information security with CompTIA Security+ as the main certification, and concludes with a question and answer section. The presenter has over 14 years of experience in IT and information security and holds multiple technical certifications.