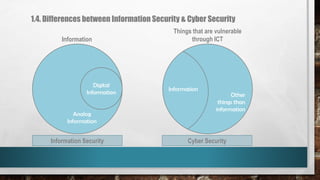
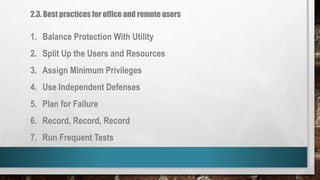
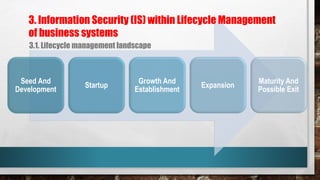
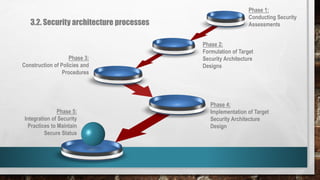
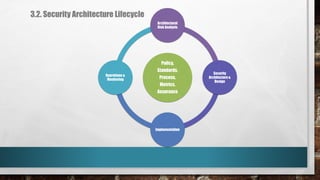
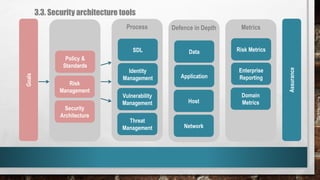
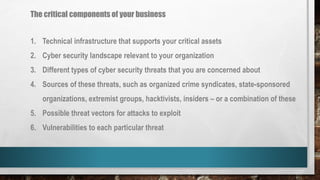
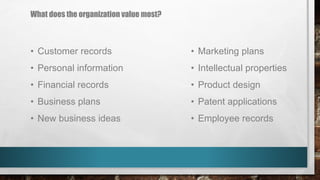
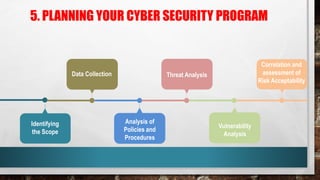
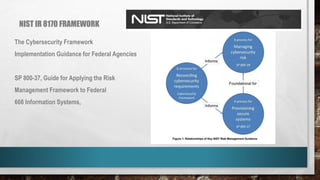
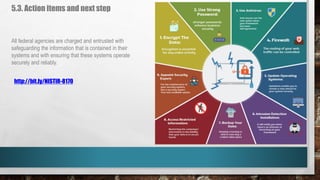
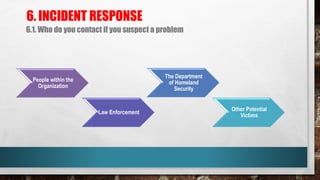
This document outlines cyber security principles, roles, and risks for non-technical executives, focusing on understanding and managing cyber security threats. It emphasizes the importance of confidentiality, integrity, and availability while providing a roadmap for planning and responding to cyber incidents. Additionally, it discusses the NIST framework for managing cybersecurity-related risks, covering implementation phases, risk evaluation, and incident response strategies.