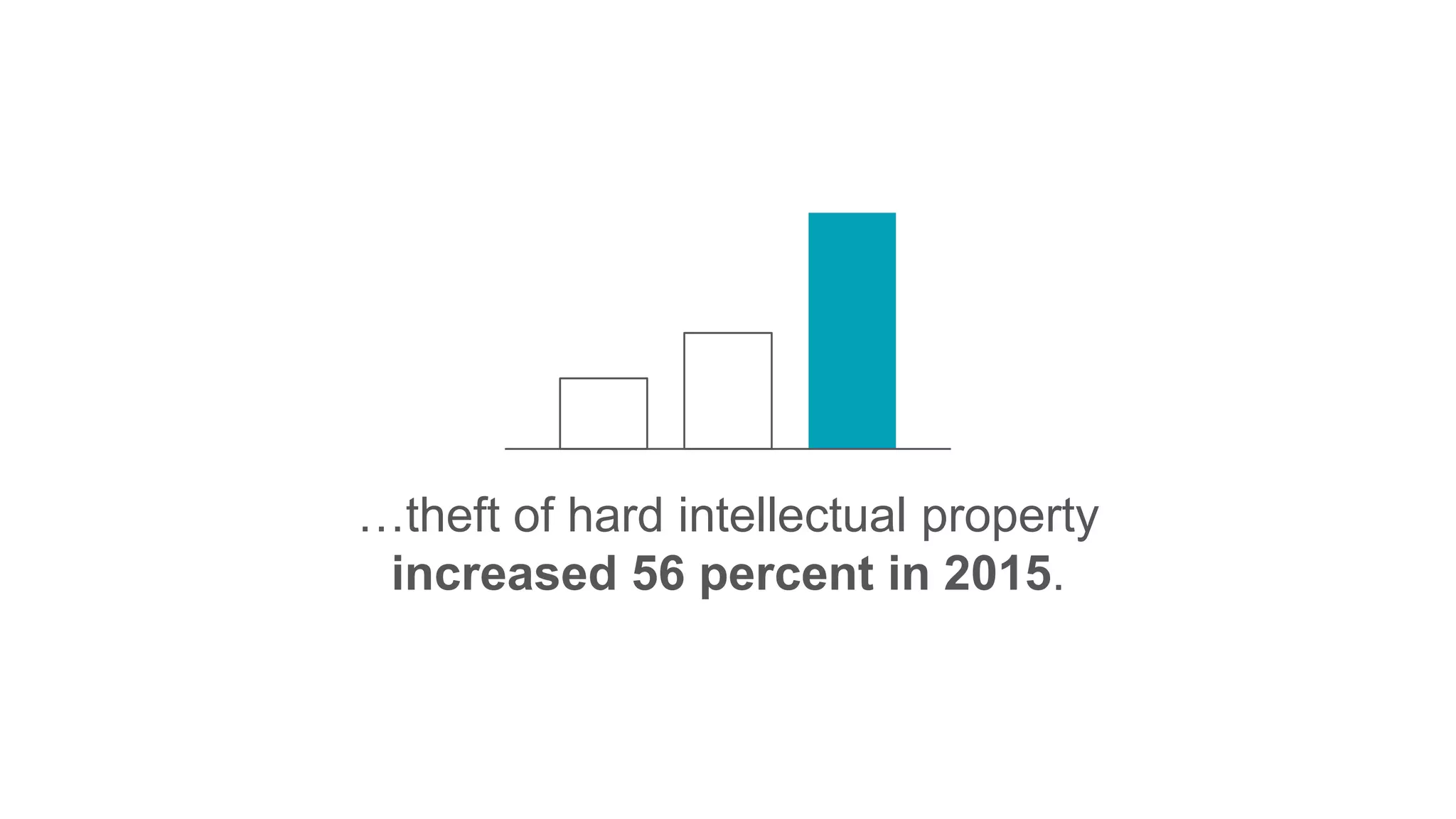
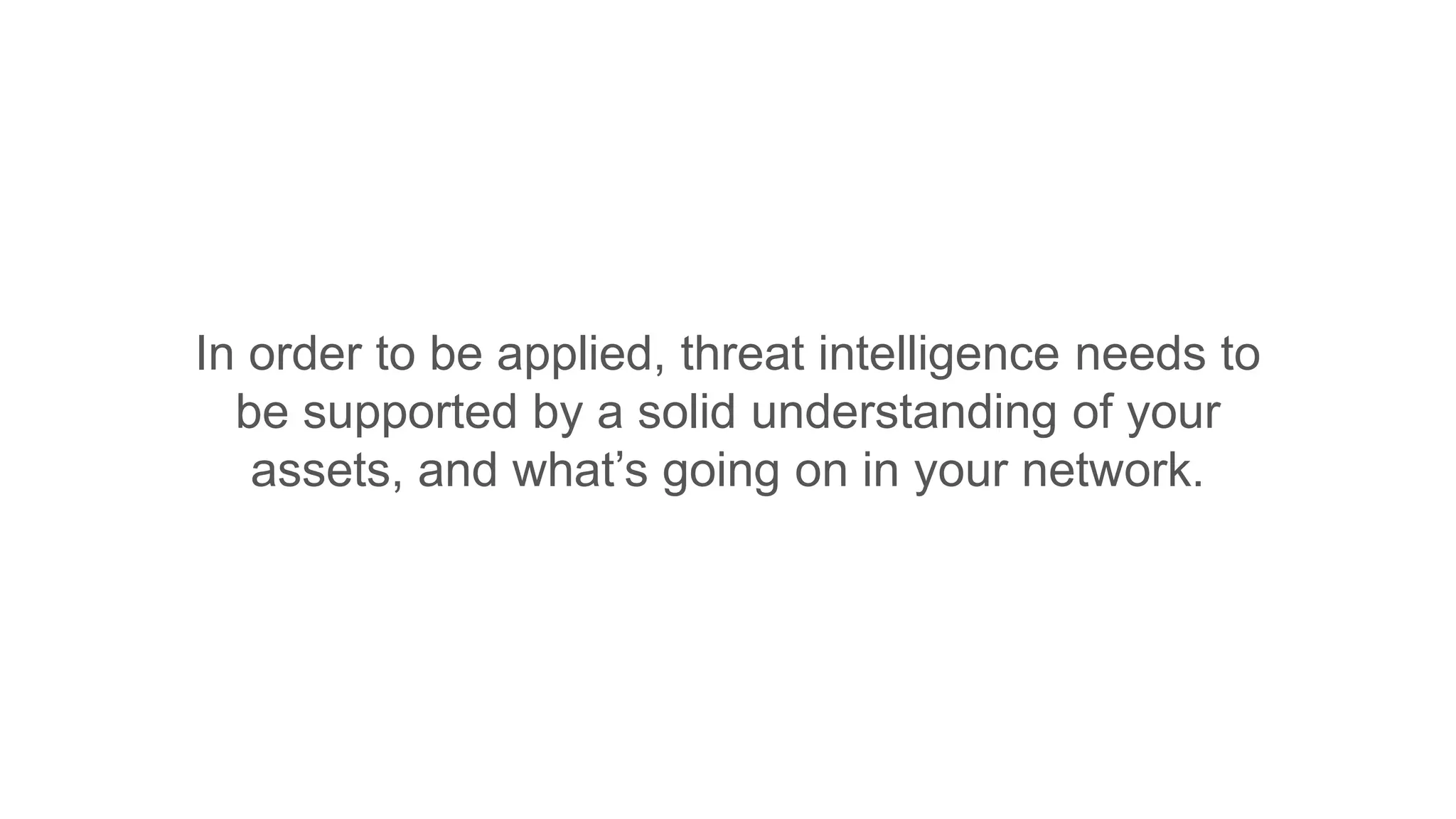
Forsythe is a leading IT company that provides security and advisory solutions for Fortune 1000 organizations to enhance their agility and security. The document emphasizes the importance of commercial threat intelligence in defending against cyber threats, suggesting that a strategic understanding of an organization's assets and capabilities is essential. It also highlights the need for effective operationalization of threat intelligence to improve security measures and respond efficiently to threats.