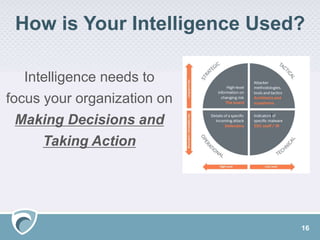
This document discusses how organizations can build an effective cyber risk intelligence program. It emphasizes that cyber risk should be viewed holistically and aligned with business priorities, not just as an IT issue. An effective program measures an organization's proficiency against benchmarks and assesses how well positioned it is for cyber risks compared to competitors. The document provides best practices such as aligning intelligence resources across strategic and tactical levels, mapping cyber risks to key business areas, and using intelligence to drive security decisions and focus resource allocation. It stresses that intelligence programs should have measurable outcomes, not just tool outputs, and risks should be made learnable and tied to the organization's unique attributes.