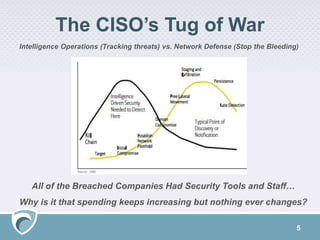
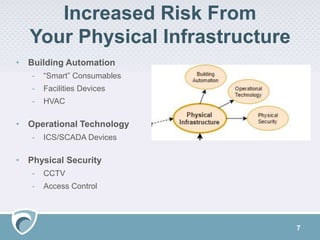
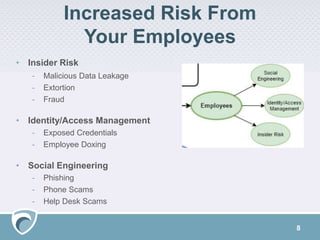
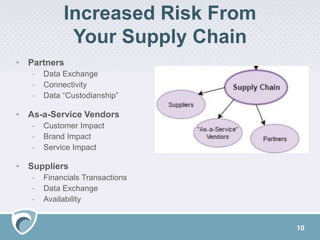
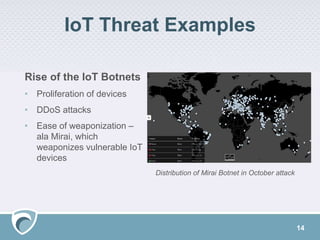
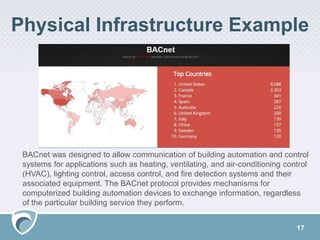
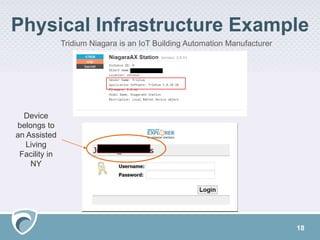
The document discusses the rising challenges of digital risks and cyber threats faced by businesses, emphasizing the necessity of threat intelligence for risk management. It highlights various sources of increased risk including supply chains, insider threats, technology infrastructure, and the growing digital footprint due to IoT devices. The speaker, Adam Meyer, advocates for a strategic approach to using threat intelligence to enhance defenses, manage risks proactively, and better allocate resources.