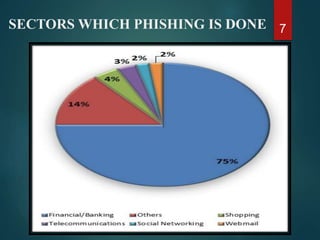
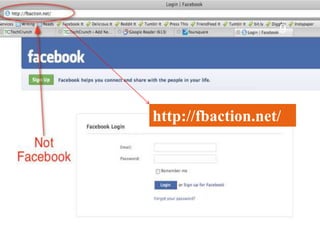
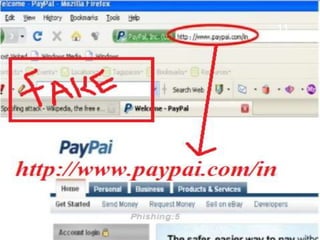
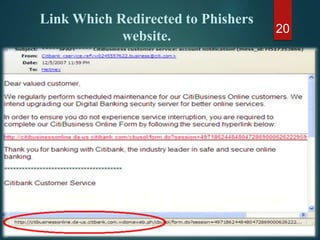
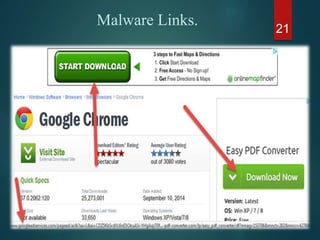
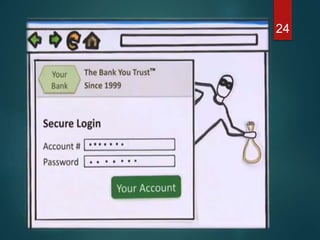
The document discusses phishing, a deceptive technique aimed at stealing personal information, including credit card numbers and passwords. It outlines various methods of phishing, such as spear phishing and session hijacking, as well as preventive measures that users can take to protect themselves, like using secure connections and being cautious with unsolicited emails. Overall, it emphasizes the importance of awareness and education in preventing phishing attacks.