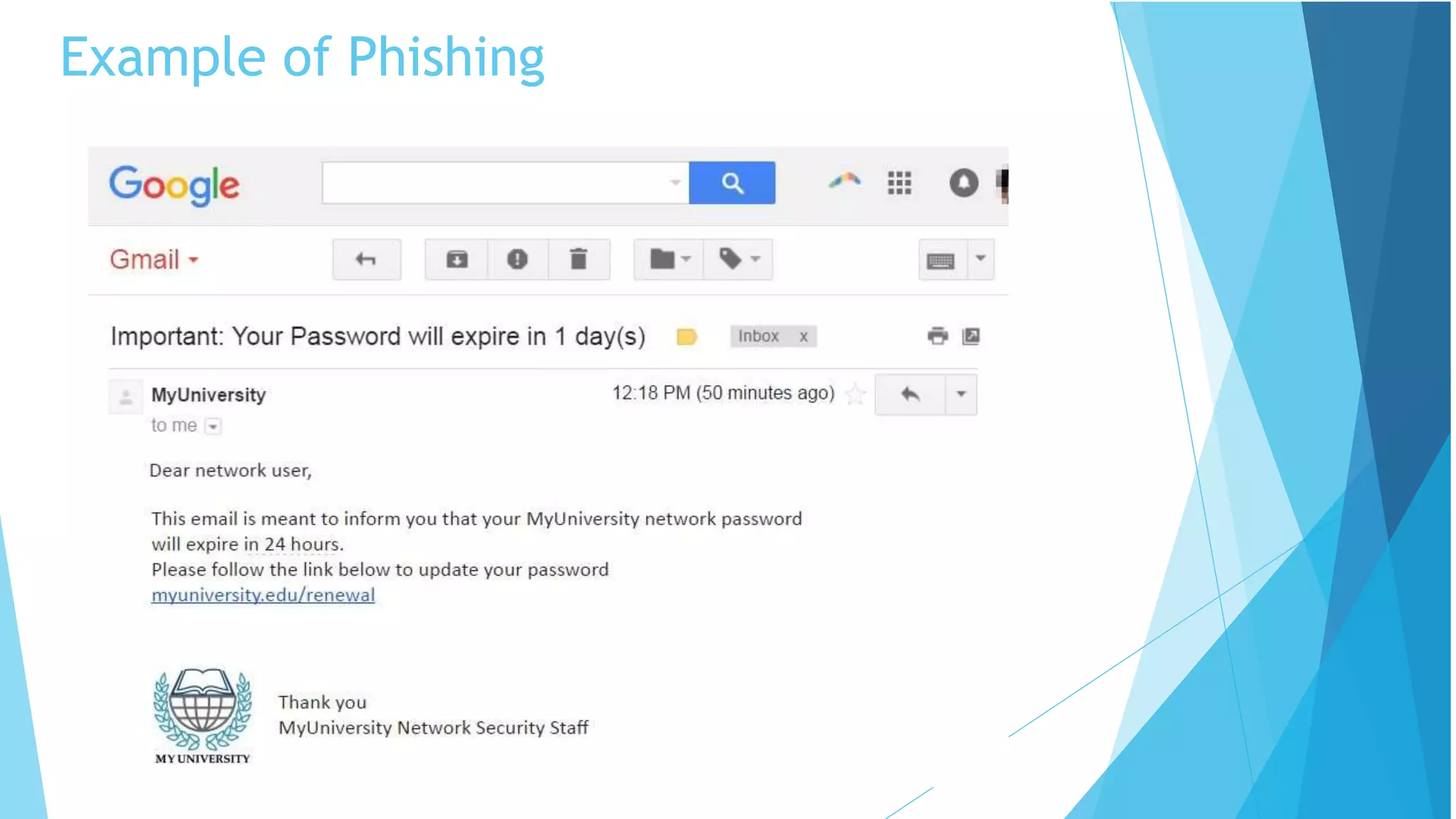
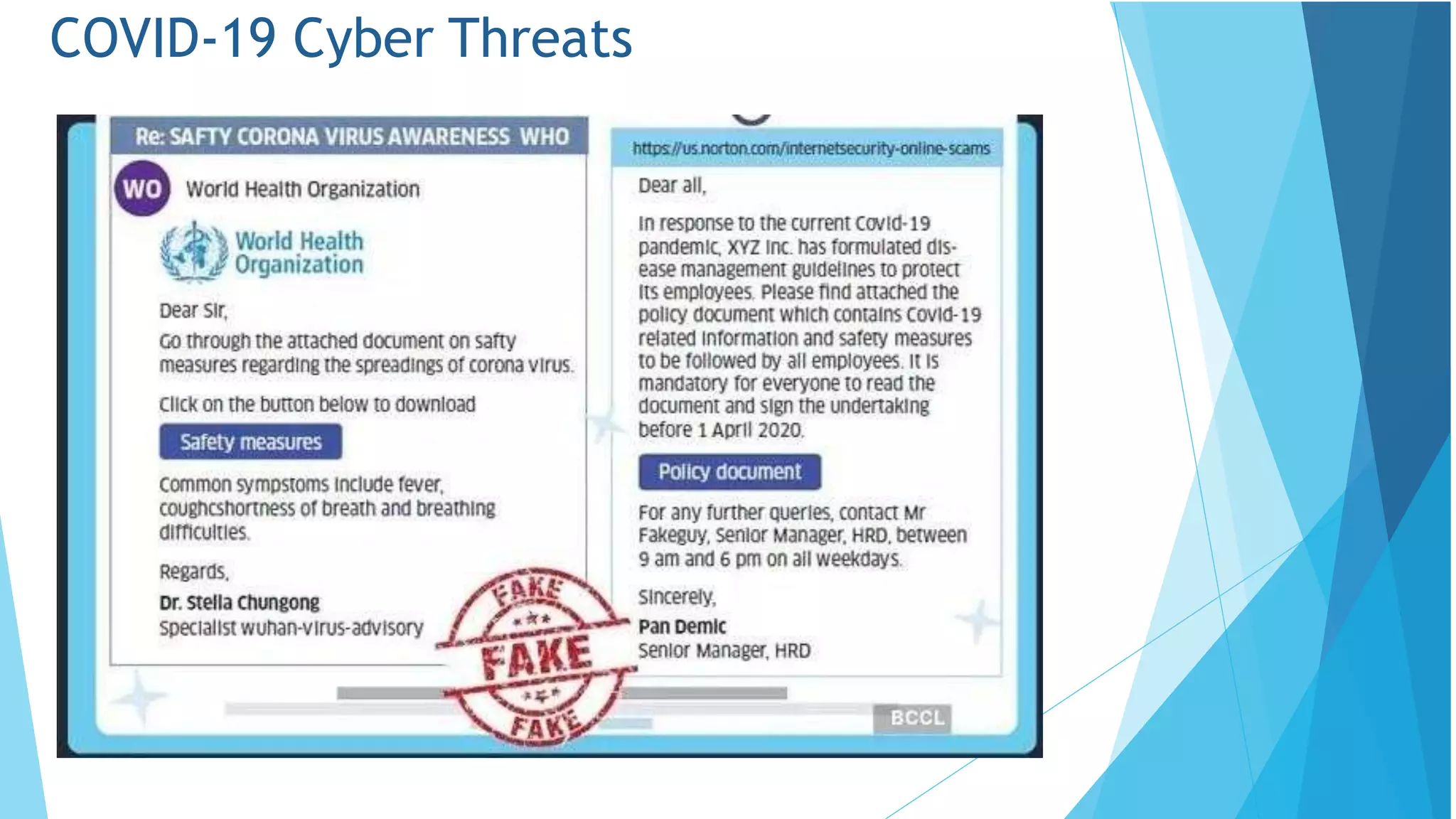
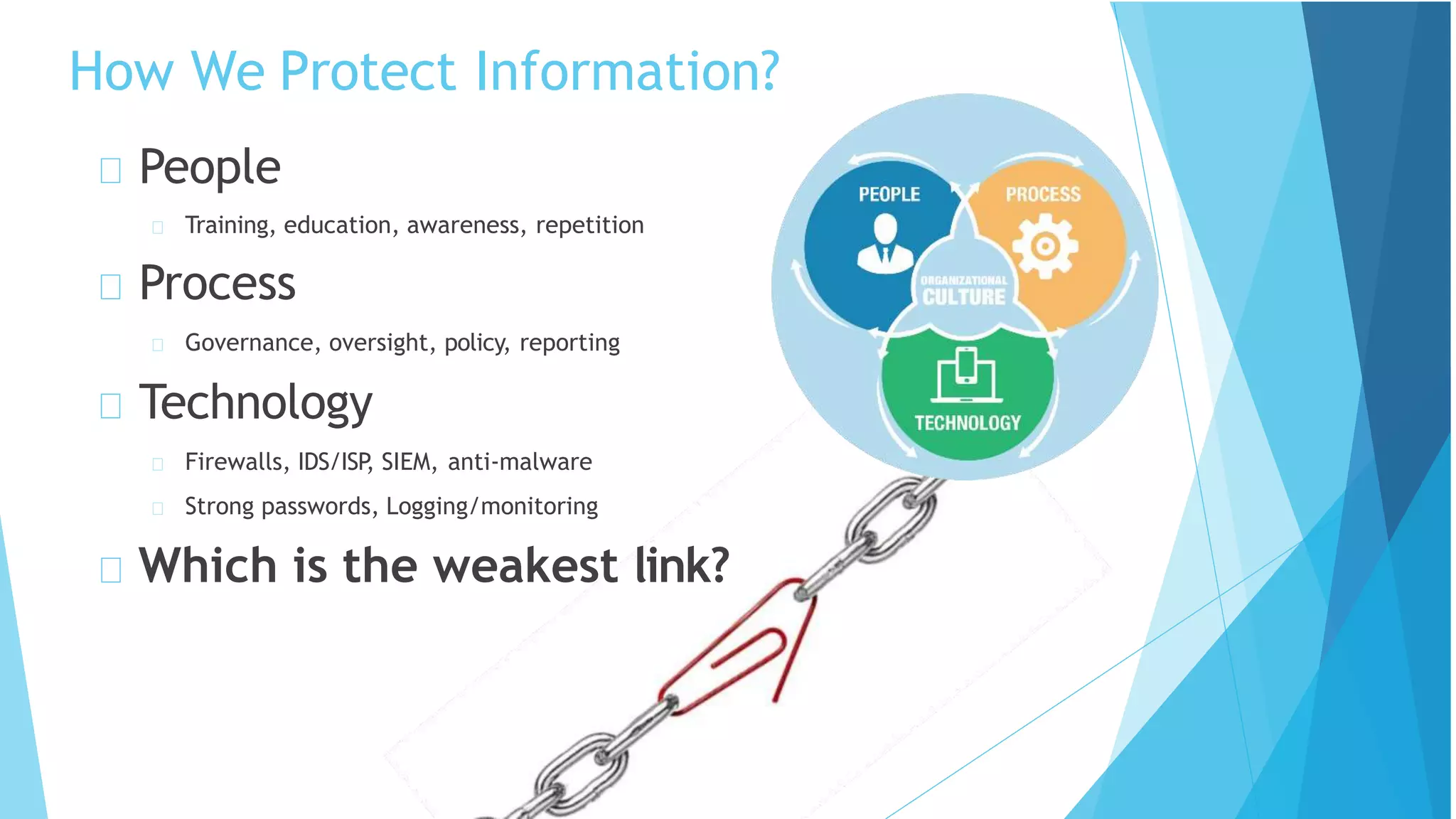
This document discusses cyber security and online scams. It defines cyber security as protecting computers, networks, and data from malicious attacks. Some key risks from poor security are identity theft, monetary theft, and information theft. The document then discusses concepts like the CIA triad of confidentiality, integrity and availability and how these relate to protecting information. It also covers common cyber threats such as phishing, malware, and business email compromise scams. Throughout, it provides examples and best practices for improving cyber security and avoiding online scams.