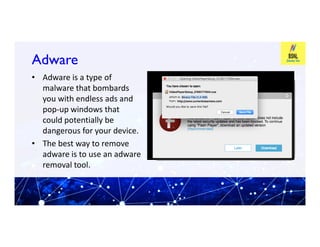
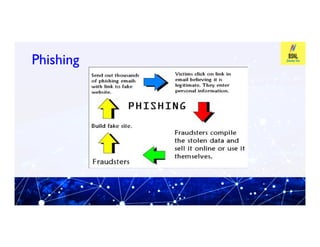
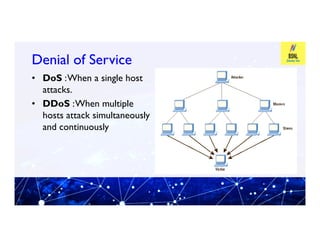
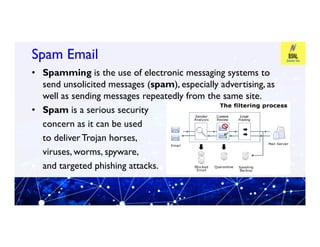
This document provides an overview of information and cyber security. It defines cyber security as technologies and processes designed to protect computers, networks, and data from attacks, vulnerabilities, damages, and unauthorized access. It discusses why cyber security is important by explaining the principles of confidentiality, integrity, and availability. It also covers common cyber security threats like viruses, malware, hacking, phishing, and denial of service attacks. The document provides tips on cyber security best practices for passwords, mobile devices, banking, and more. It introduces tools used in cyber security like Profession Look at Net and F-RAT.