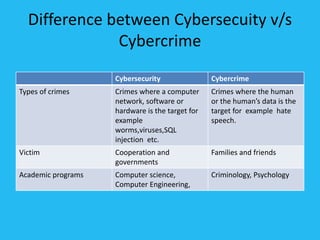
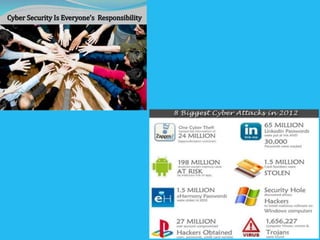
Cybersecurity involves protecting computers, networks, programs, and data from digital attacks. It includes topics like hacking, denial of service attacks, cyber terrorism, and software piracy. Some key aspects of cybersecurity are using antivirus software, anti-spyware, firewalls, secure passwords, and maintaining regular backups to protect private information and systems from viruses, malware, and unauthorized access. Understanding different types of hackers like white hat, grey hat, and black hat is also important for cybersecurity.