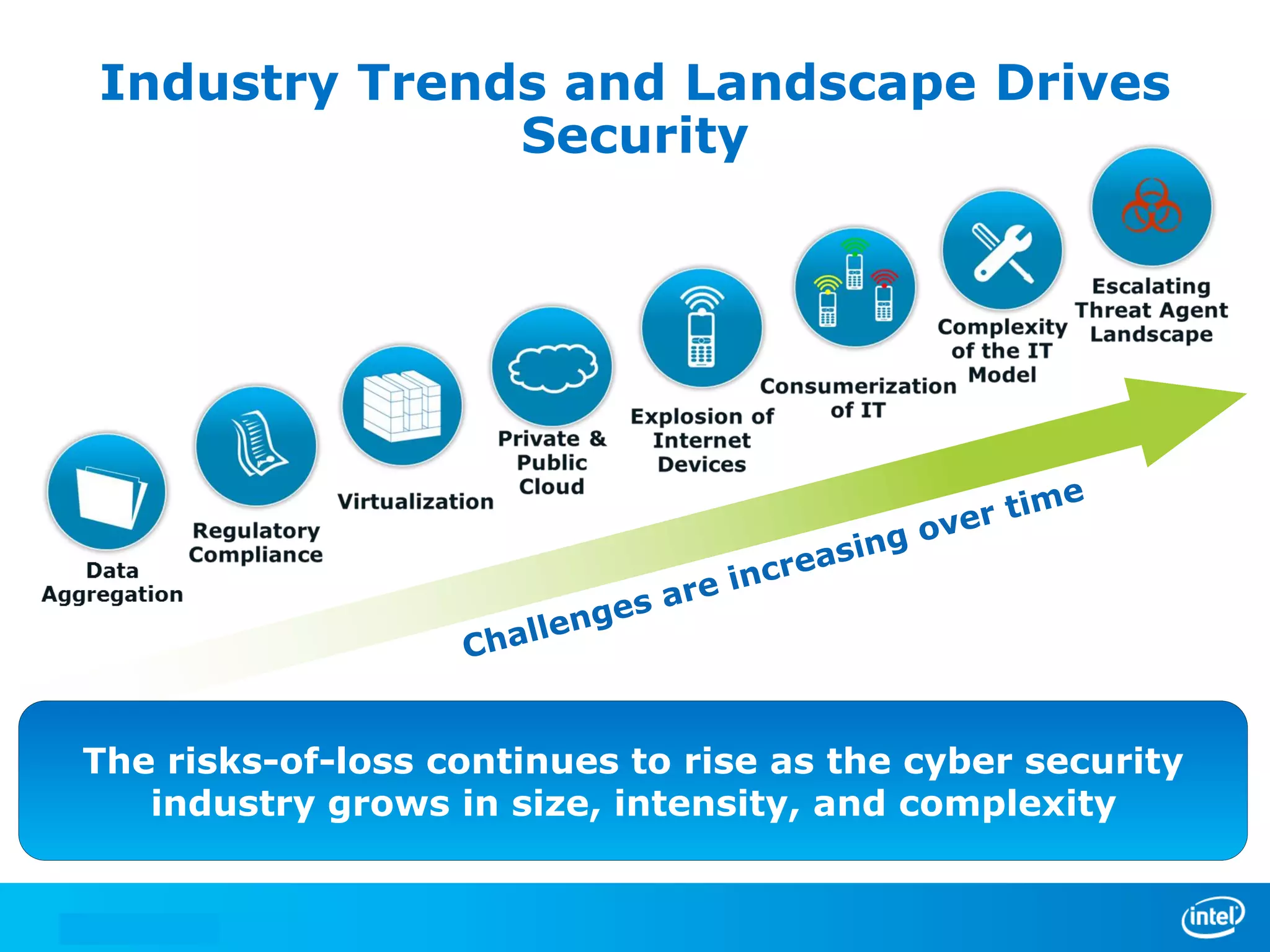
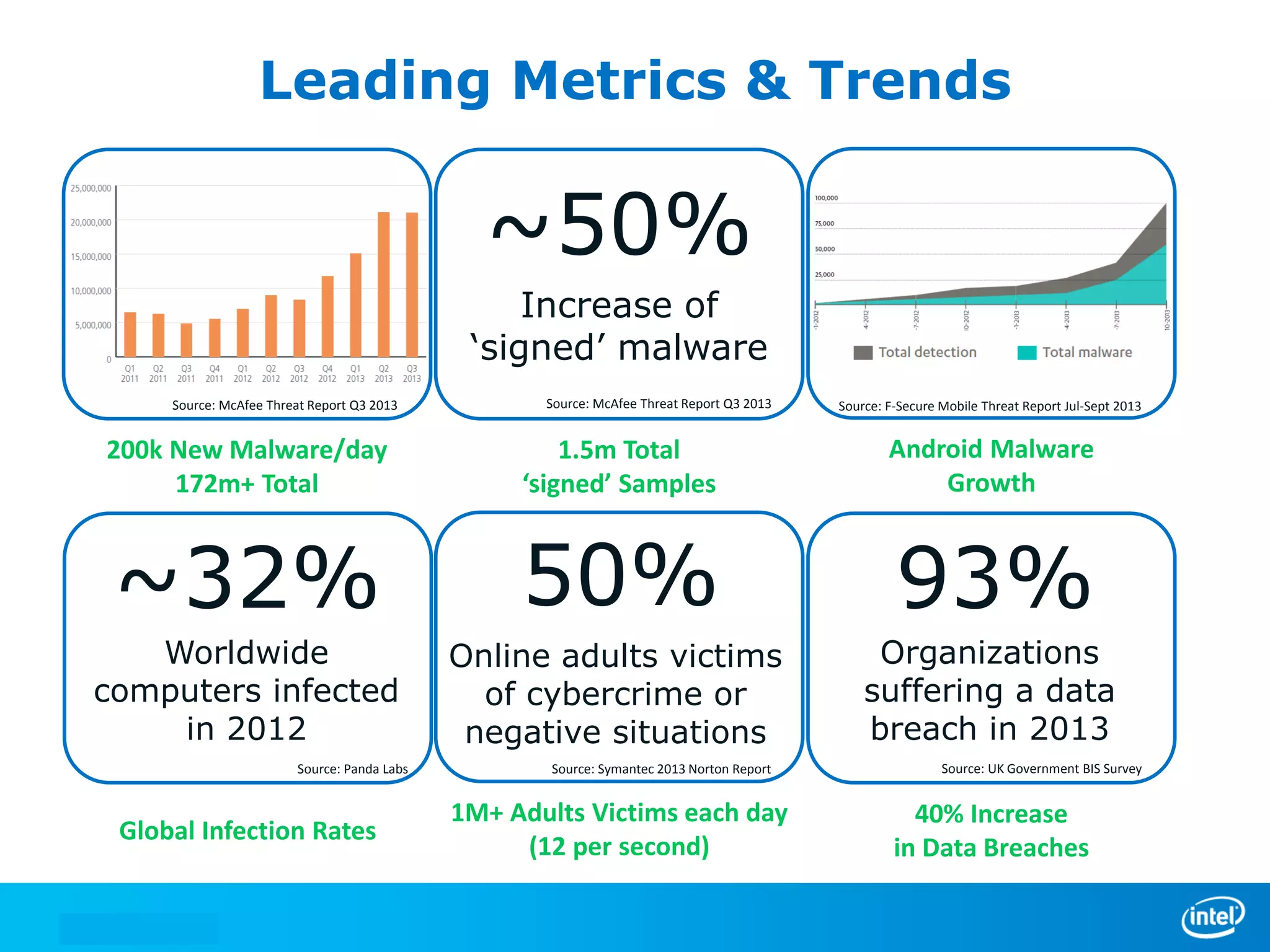
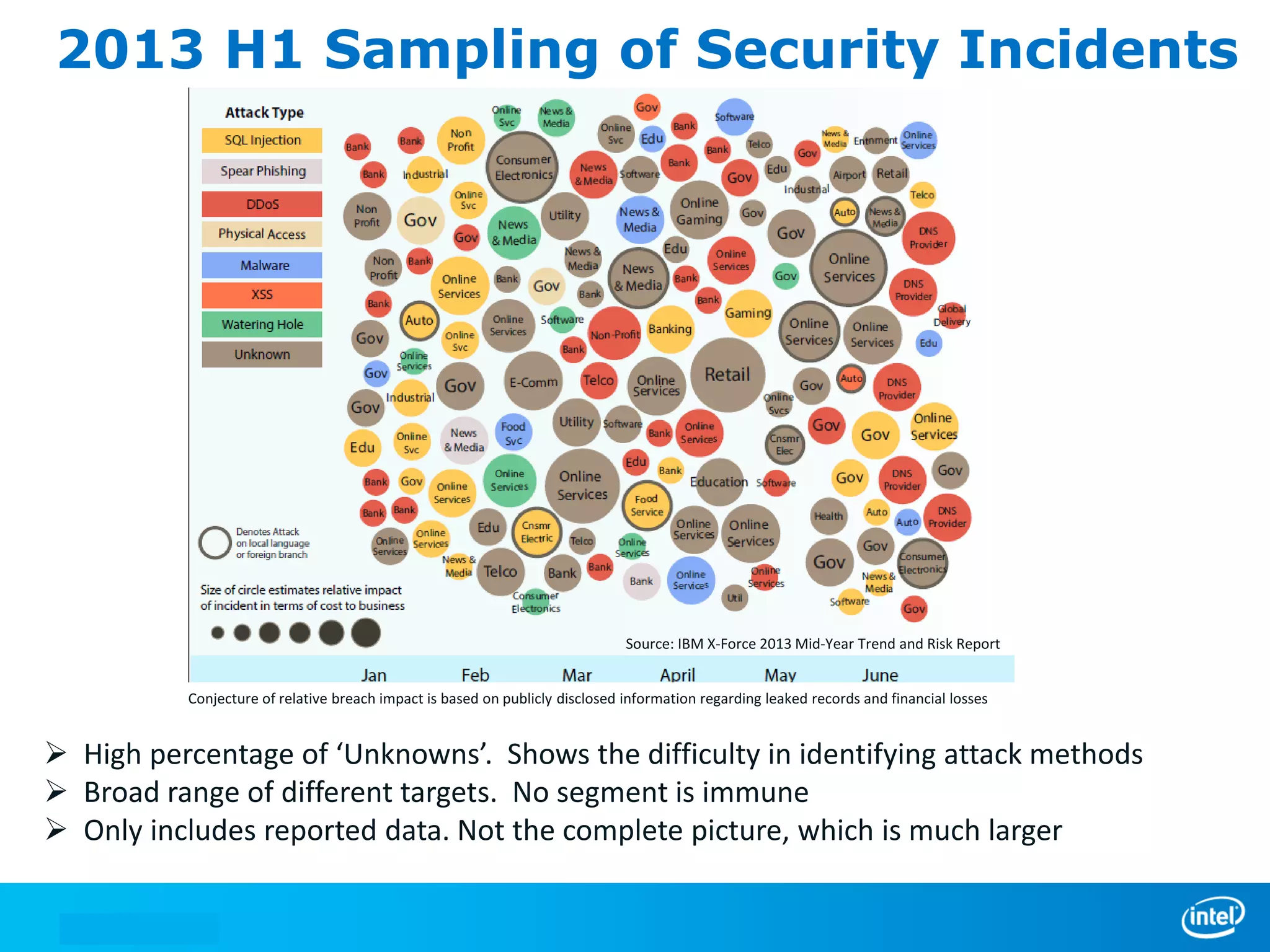
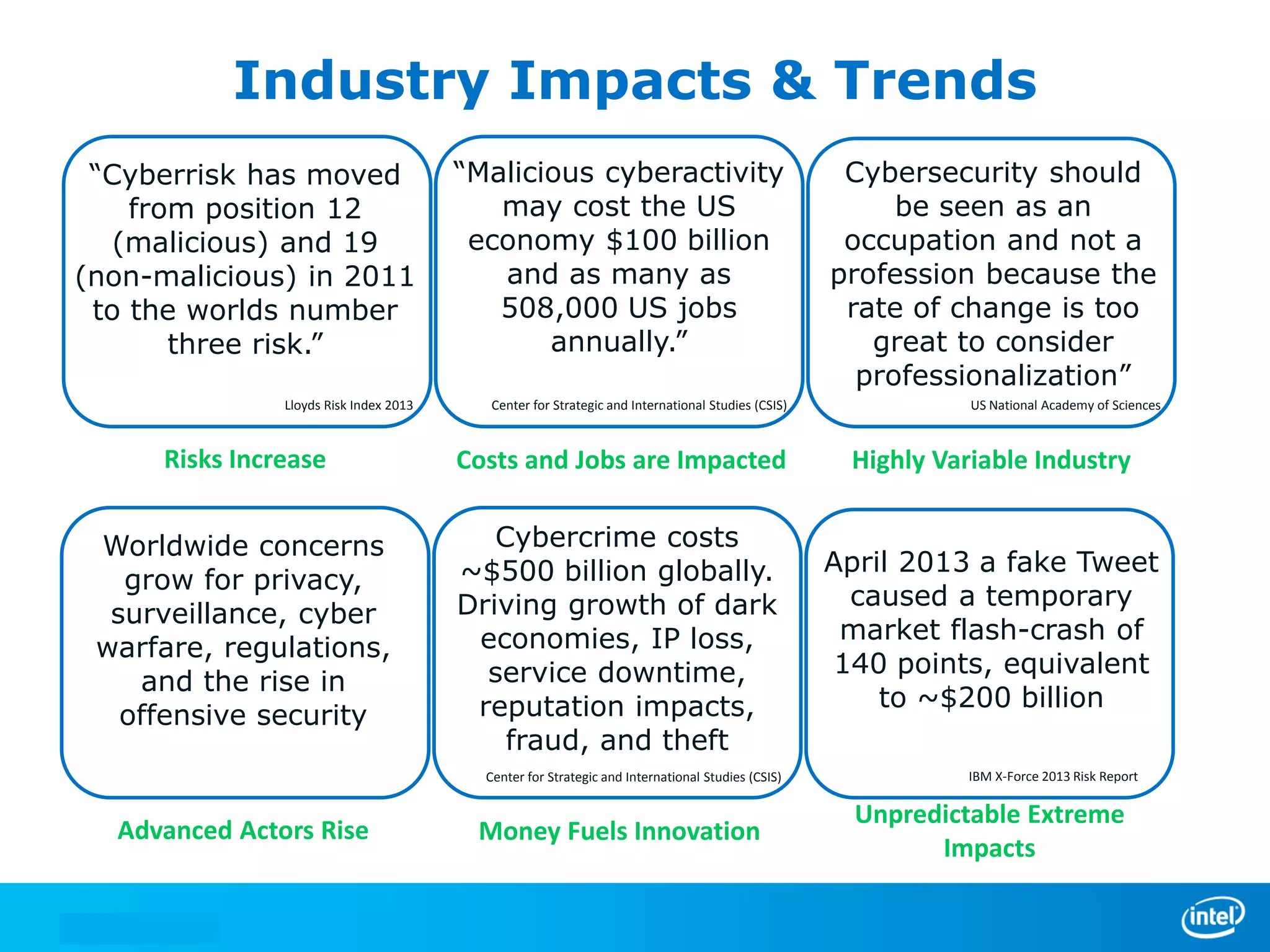
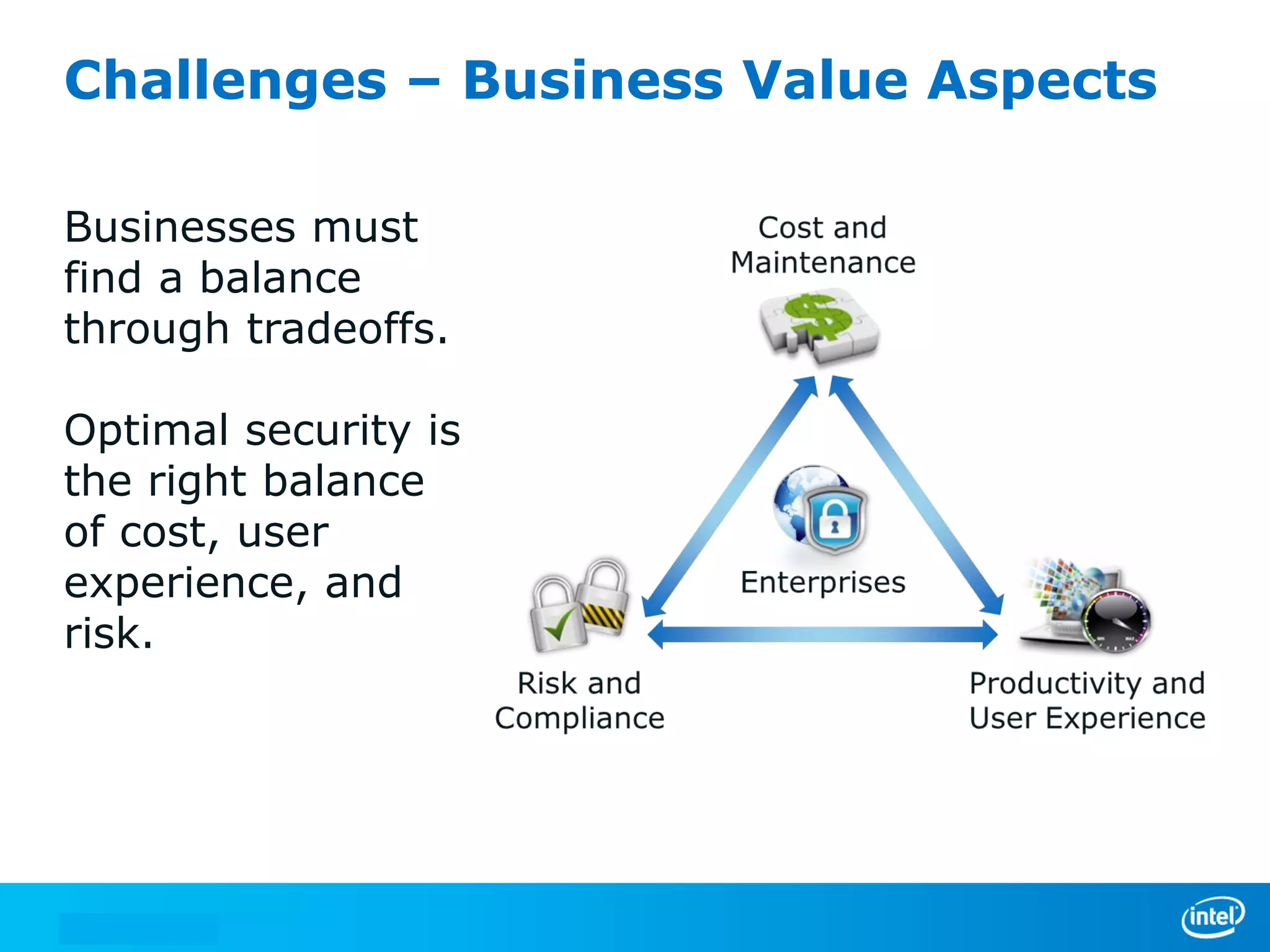
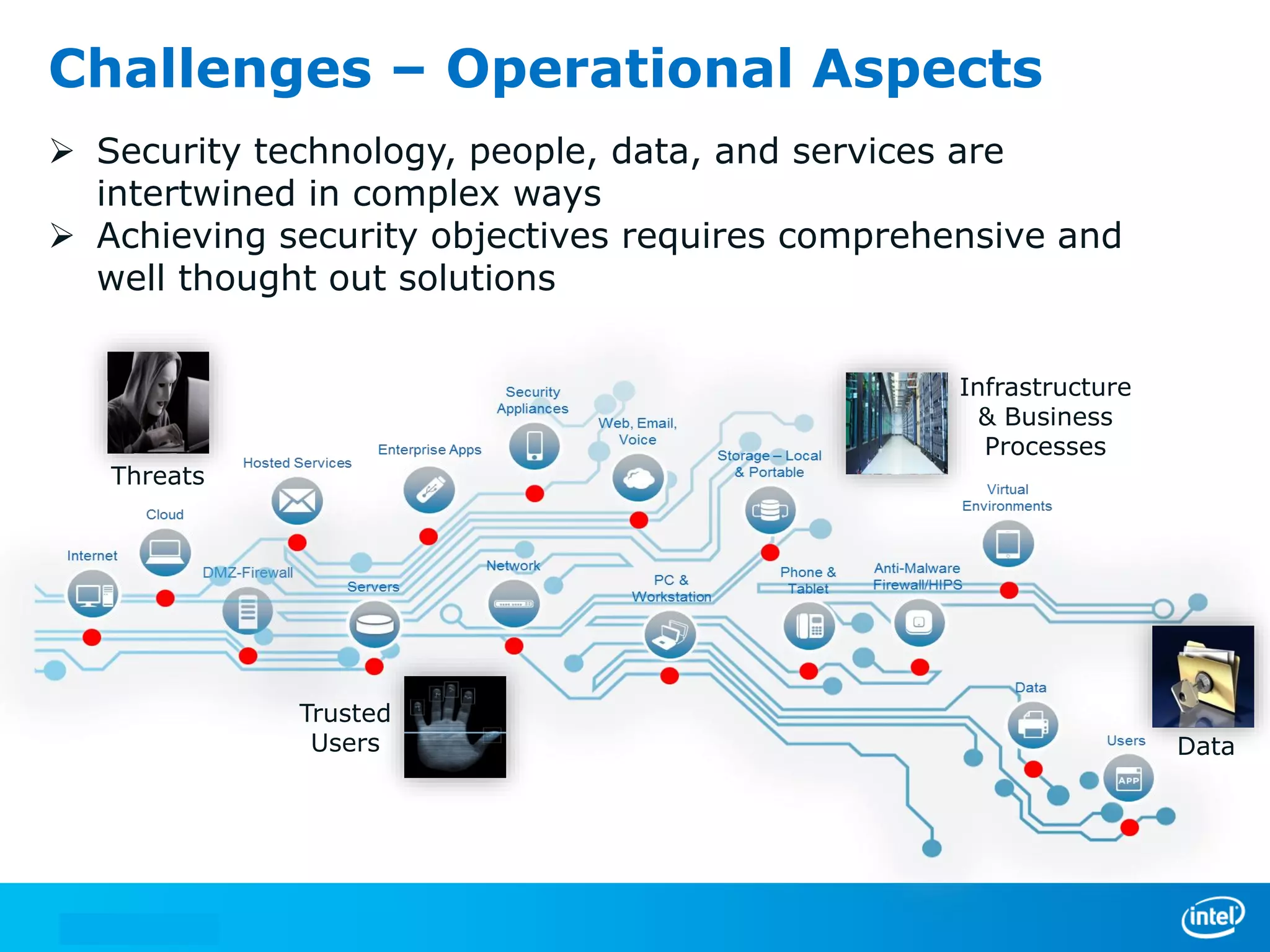
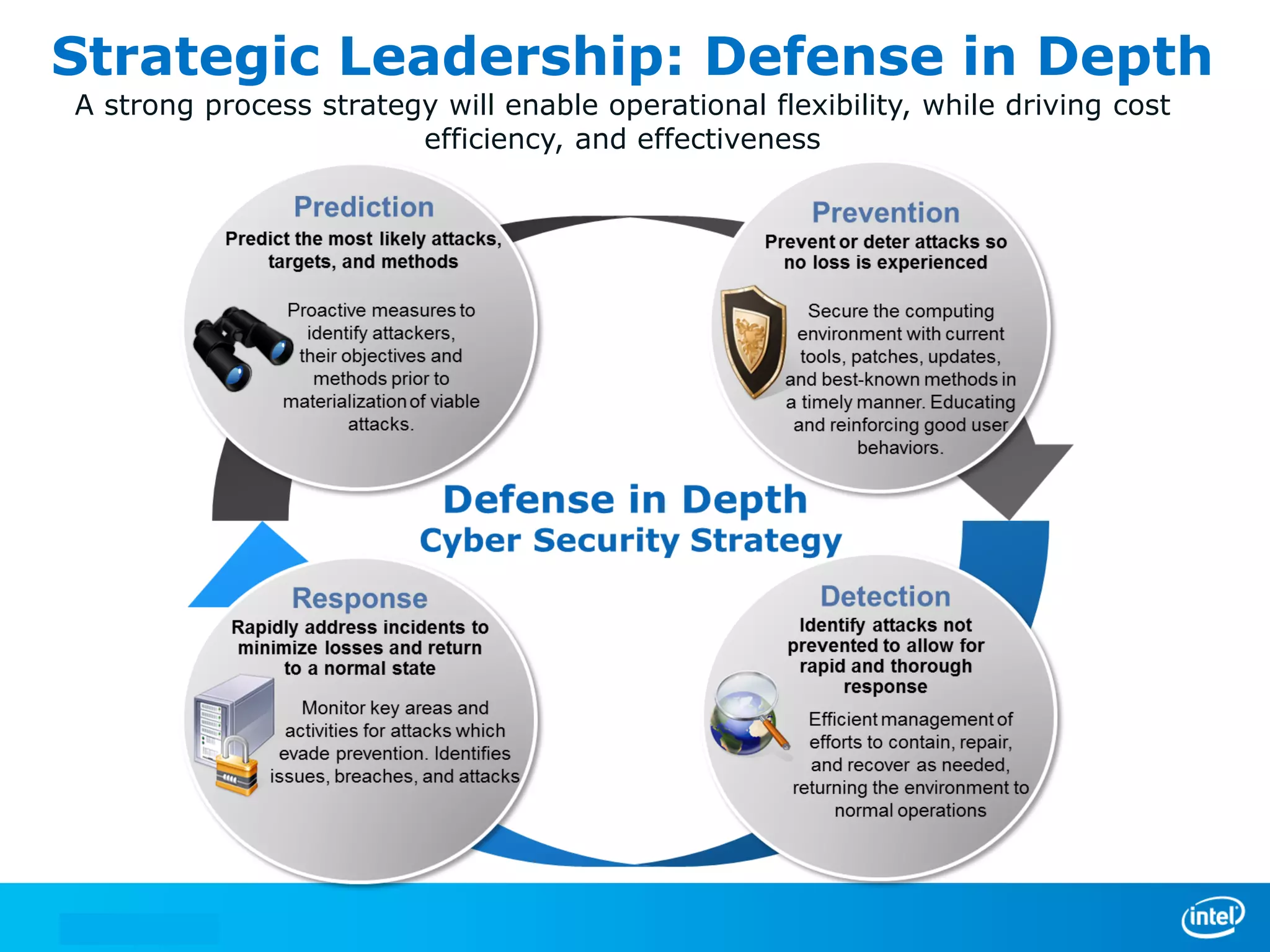
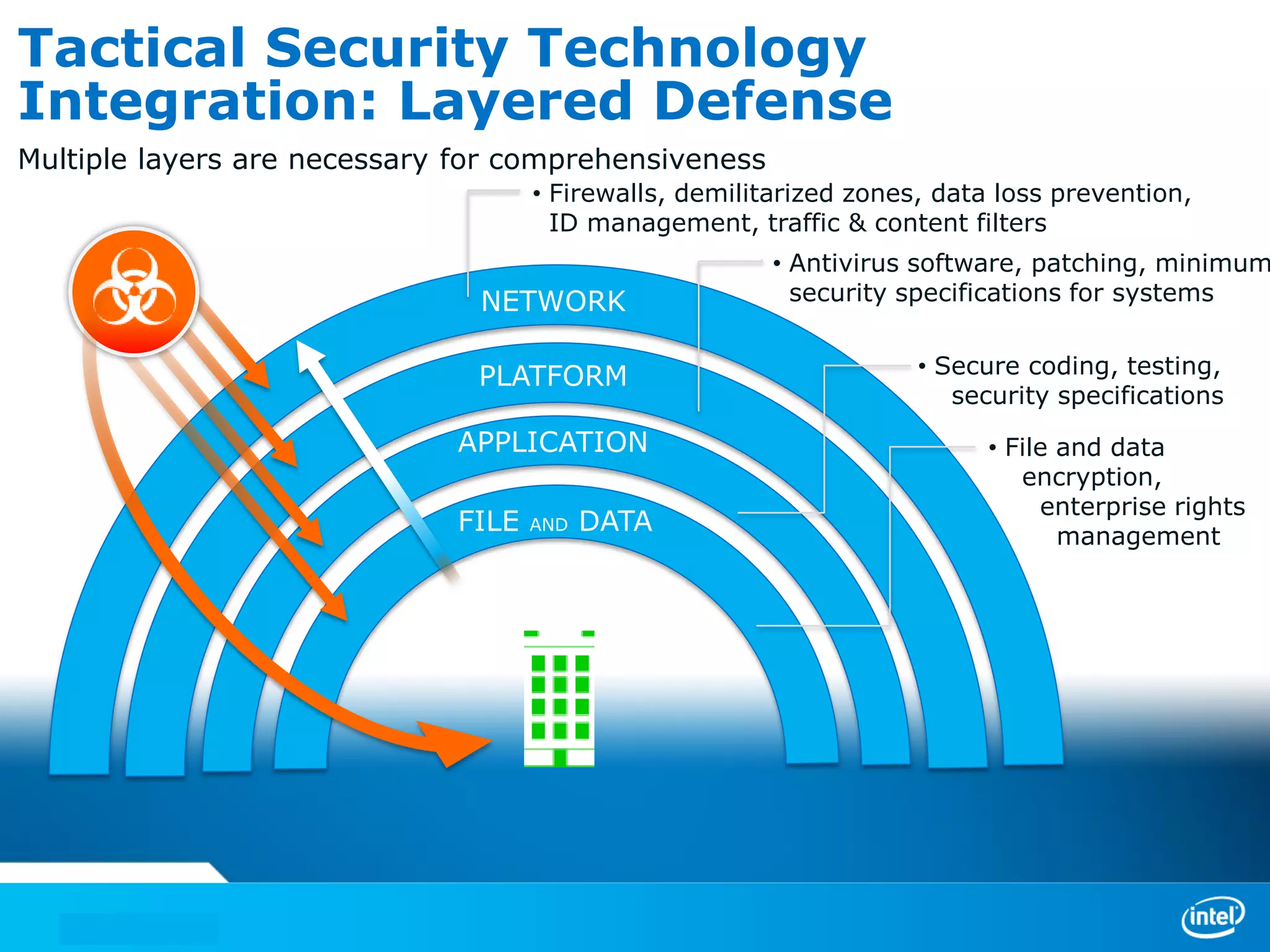
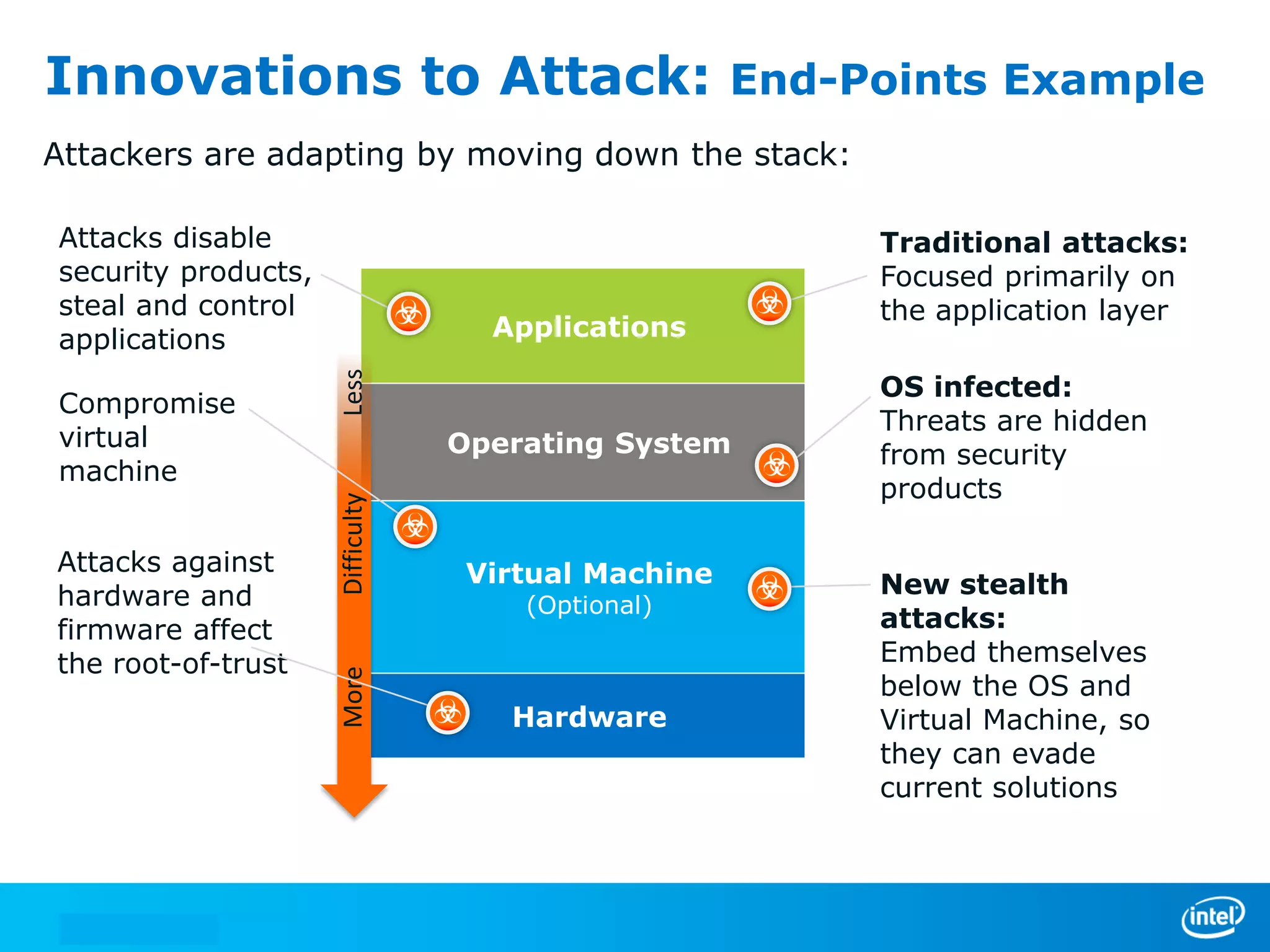
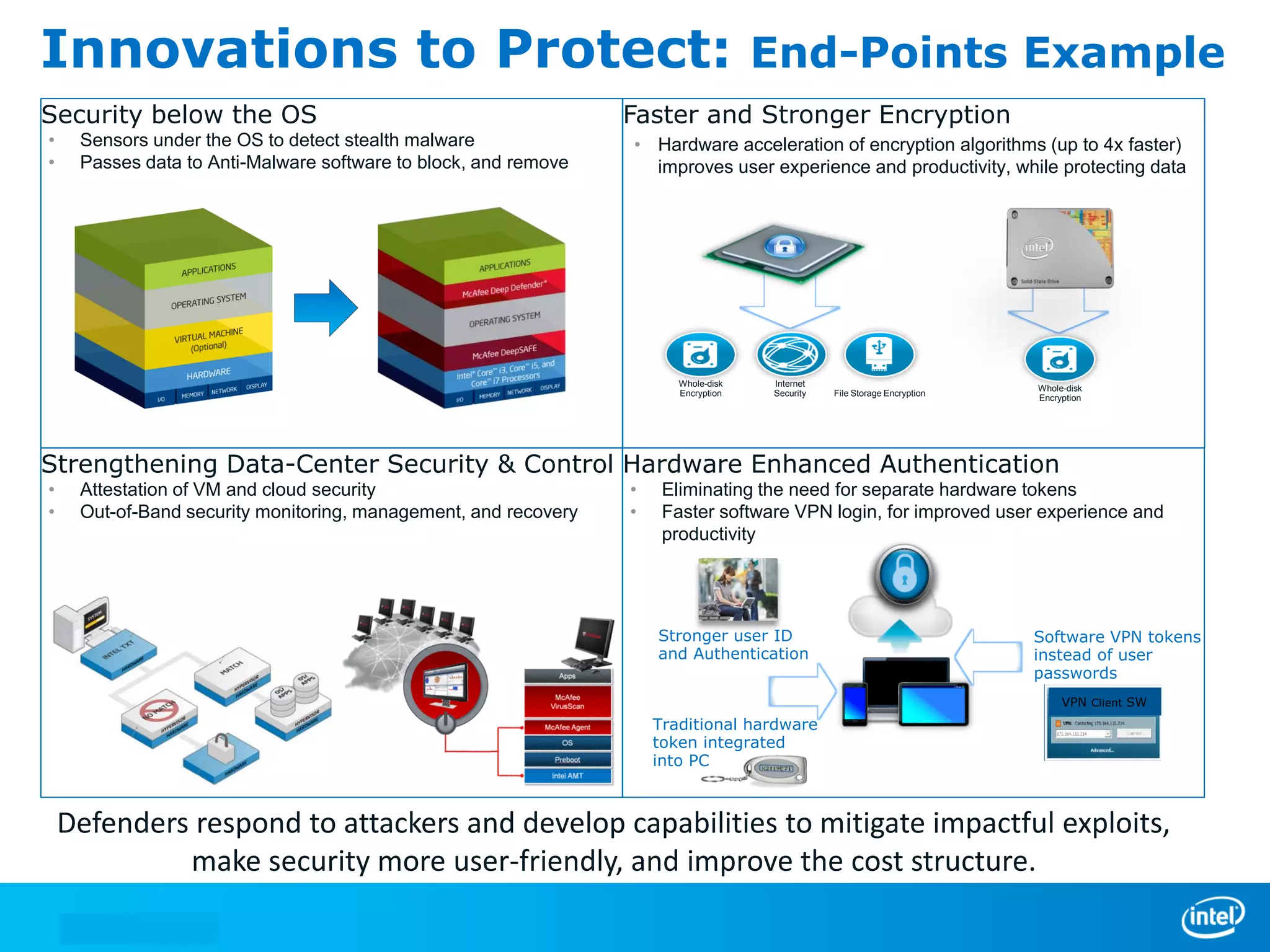
We manage security through either leadership or crisis. In the absence of leadership, we are left with crisis. The document discusses trends in cyber security threats, challenges faced by organizations, and the need for strategic leadership in cyber security. It outlines a defense in depth approach using layered security technologies and controls. Key risks like increasing attacks and data aggregation are addressed. Innovation on both sides of attacks and protections is also covered.