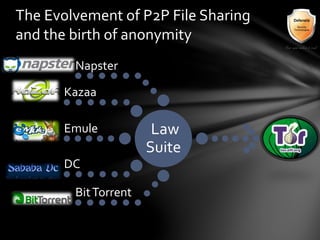
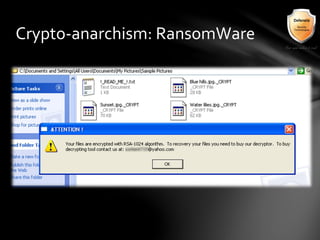
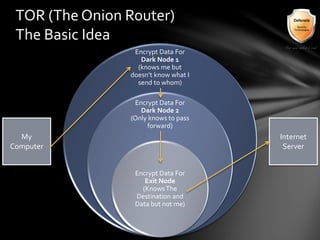
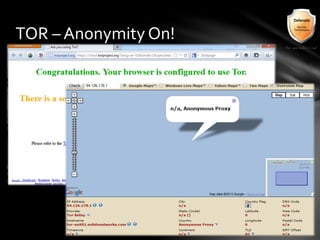
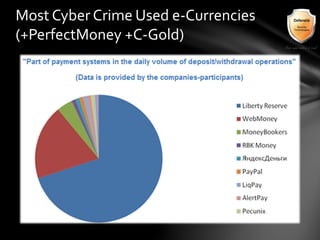
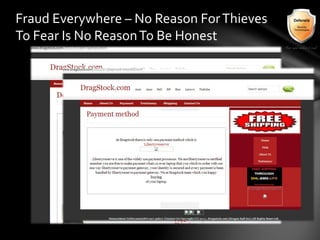
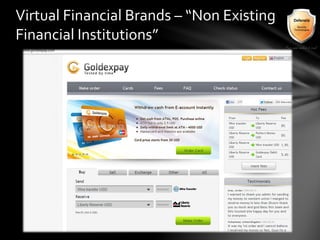
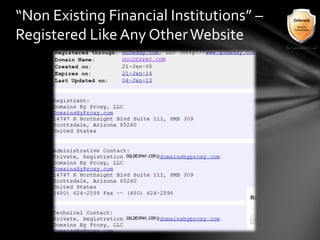
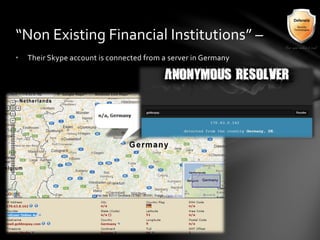
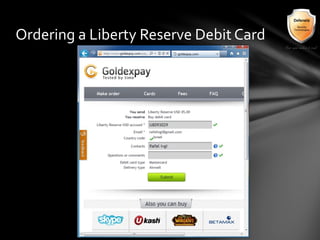
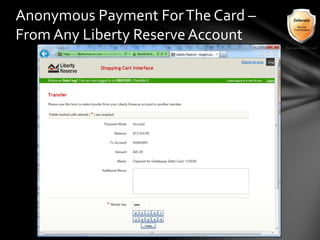
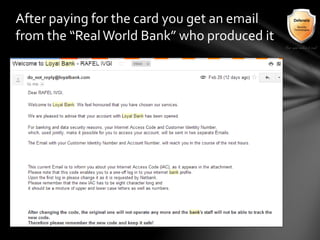
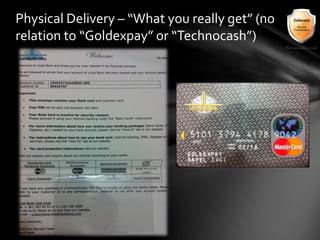
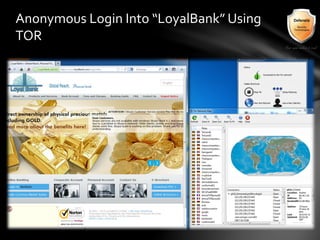
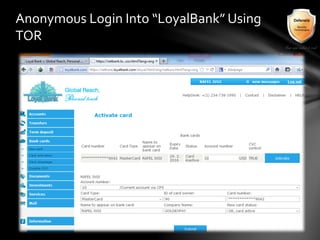
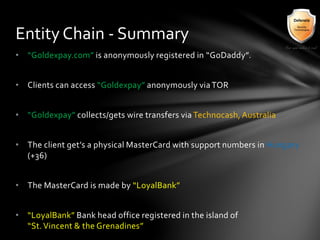
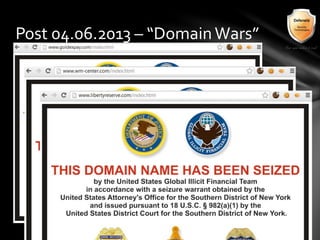
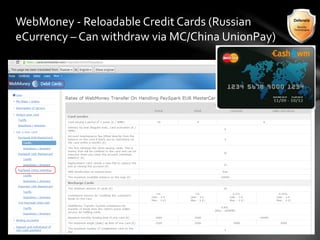
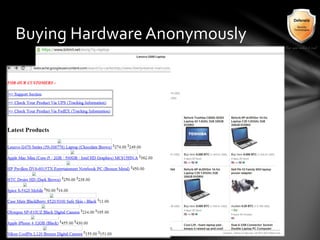
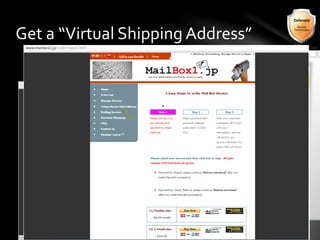
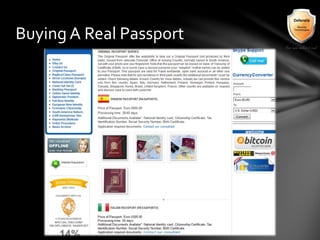
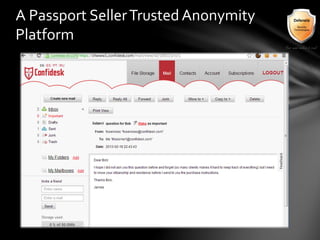
This document outlines the agenda and topics covered in a presentation on cyber crime. The presentation discusses the definition of cyber crime, the major players involved, common money laundering and anonymous purchasing techniques, and gives a live demonstration of how to anonymously conduct illegal activities online. Key points covered include the international nature of cyber crimes, challenges with legal accountability across borders, common cyber crime products and services, and the use of technologies like TOR and cryptocurrencies to conduct activities anonymously.