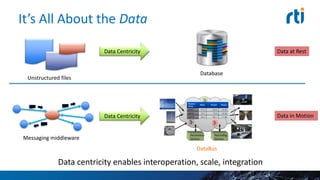
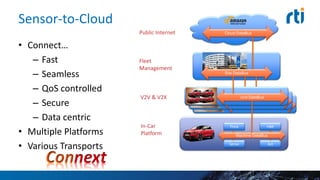
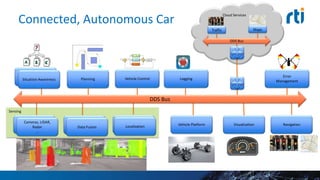
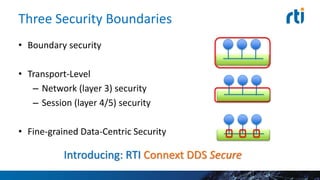
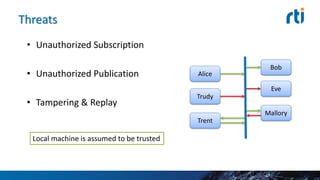
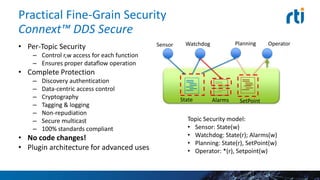
This document discusses cyber security challenges for connected cars. It notes connected cars have multiple attack surfaces through the internet, cloud, communication with other cars, and in-car systems. The document advocates for a layered security approach, including boundary security, transport-level security, and fine-grained data-centric security. It describes using Real-Time Innovation's Connext DDS Secure product to implement fine-grained security at the individual data topic level to control access and ensure proper system operation in a secure manner.