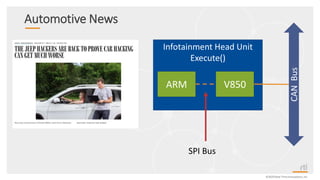
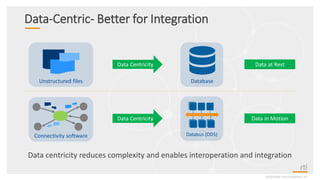
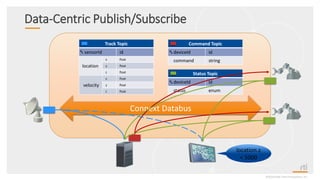
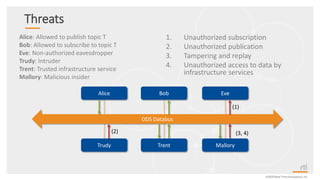
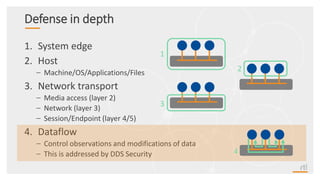
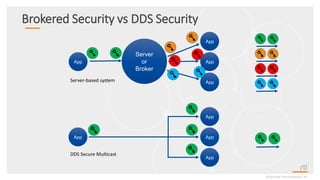
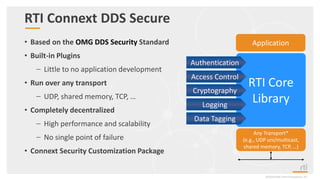
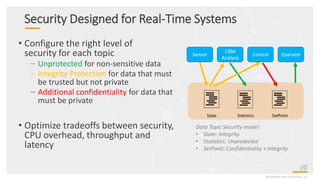
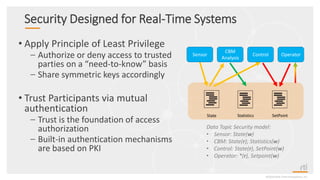
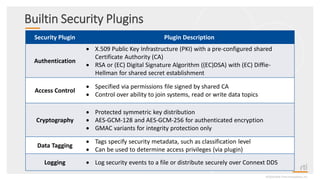
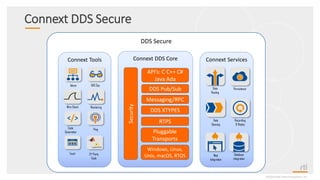
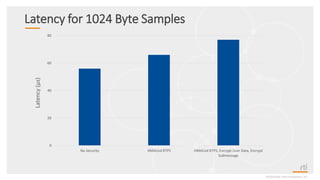
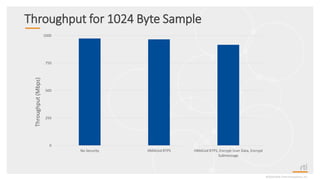
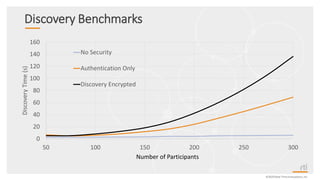
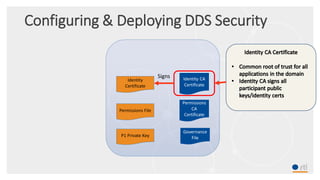
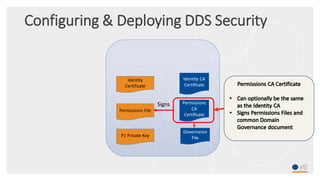
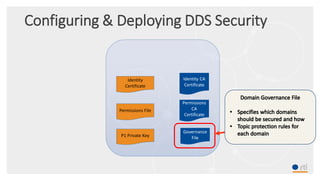
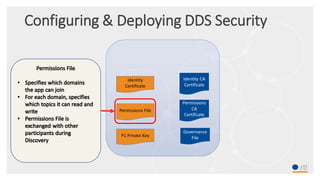
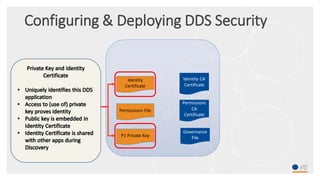
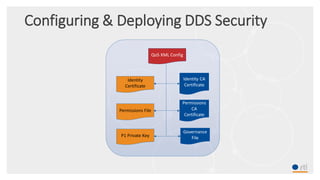
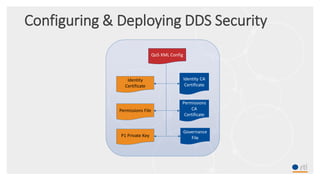
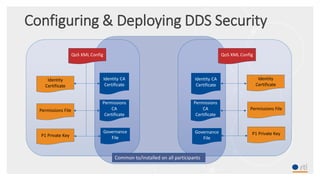
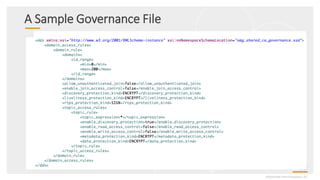
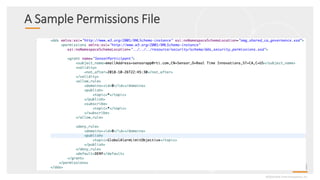
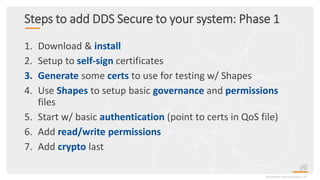
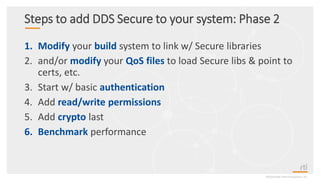
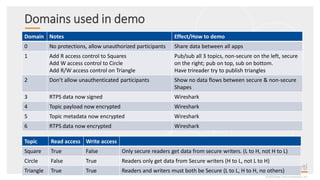
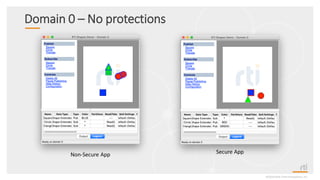
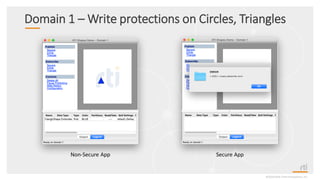
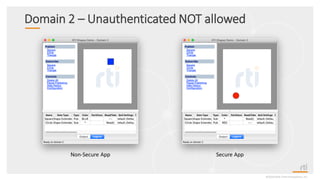
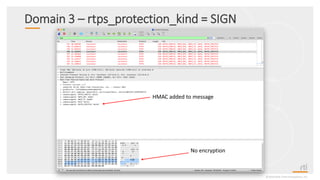
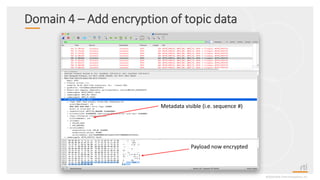
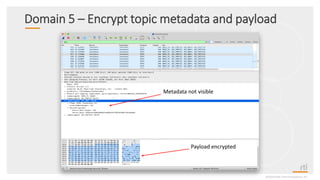
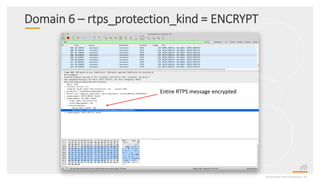
This document provides an overview and agenda for a presentation on securing critical real-time data using RTI Connext DDS Secure. The presentation covers RTI company overview, security requirements for modern distributed systems, implementing a secure connectivity model, upgrading to Connext DDS Secure, leveraging RTI tools, and a demo. The demo shows how to configure different security domains to add authentication, access control, integrity protection and encryption between Shape applications.