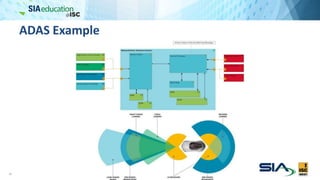
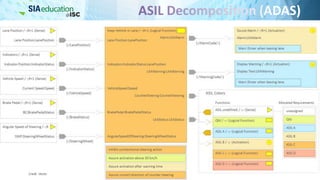
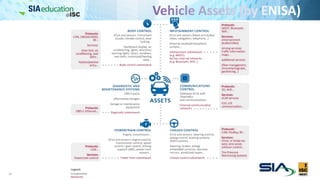
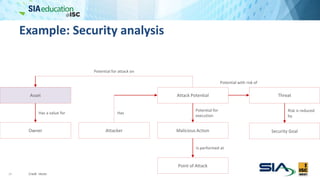
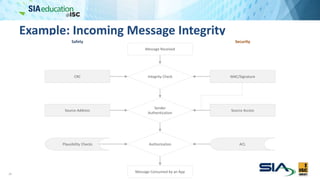
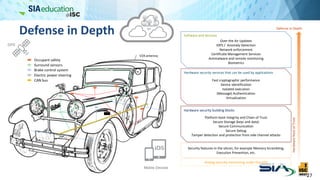
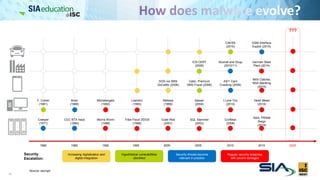
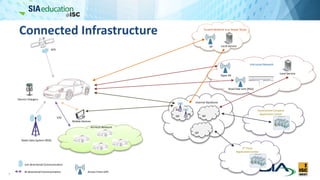
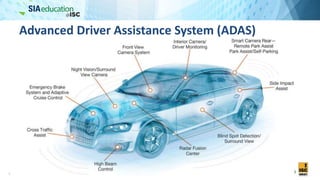
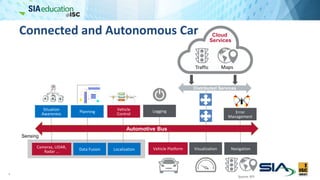
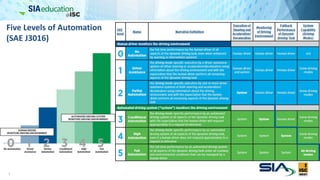
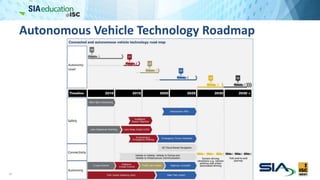
The document discusses the complexities of securing connected vehicles, highlighting their extensive software and hardware components that contribute to potential vulnerabilities. It covers functional safety standards, such as ISO 26262, and outlines security practices necessary to protect against unauthorized access and failures. The presentation emphasizes that security must be integrated into the vehicle's architecture to effectively manage risks and ensure safety and functionality.





![Toyota Unintended Acceleration
12
• Toyota Lexus ES 350 sedan Reached 100
mph+
• 911 Emergency Phone Call from passenger
during event.
• All 4 occupants killed in crash.
• Toyota data on infotainment software
shows an expected one “major bug” for
every 30 coding rule violations. [Kawana
2004]
Source: Prof. Phil Koopman. A Case Study of Toyota Unintended
Acceleration and Software Safety](https://image.slidesharecdn.com/willfuturevehiclesbesecure-170406205450/85/Will-future-vehicles-be-secure-12-320.jpg)