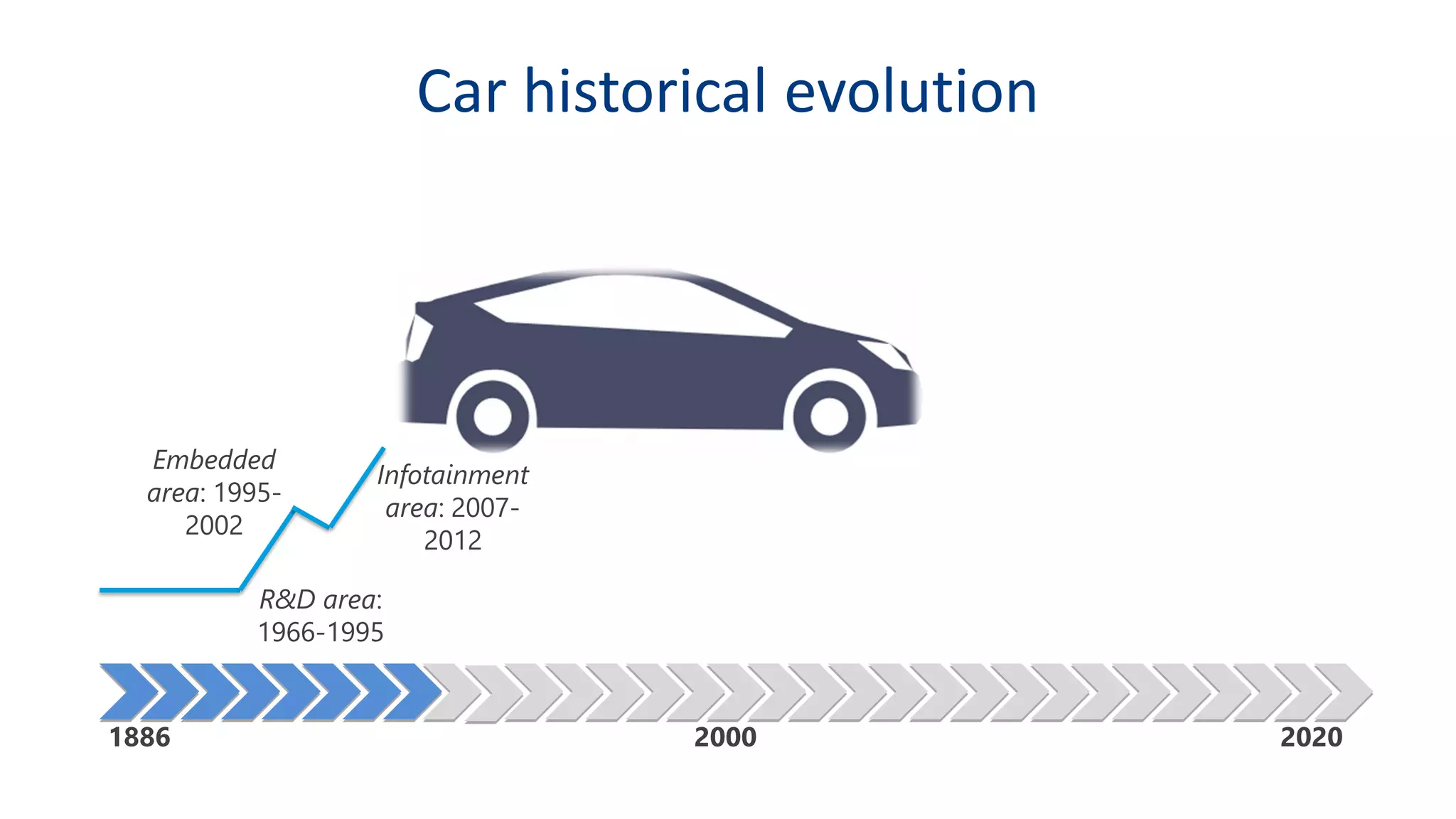
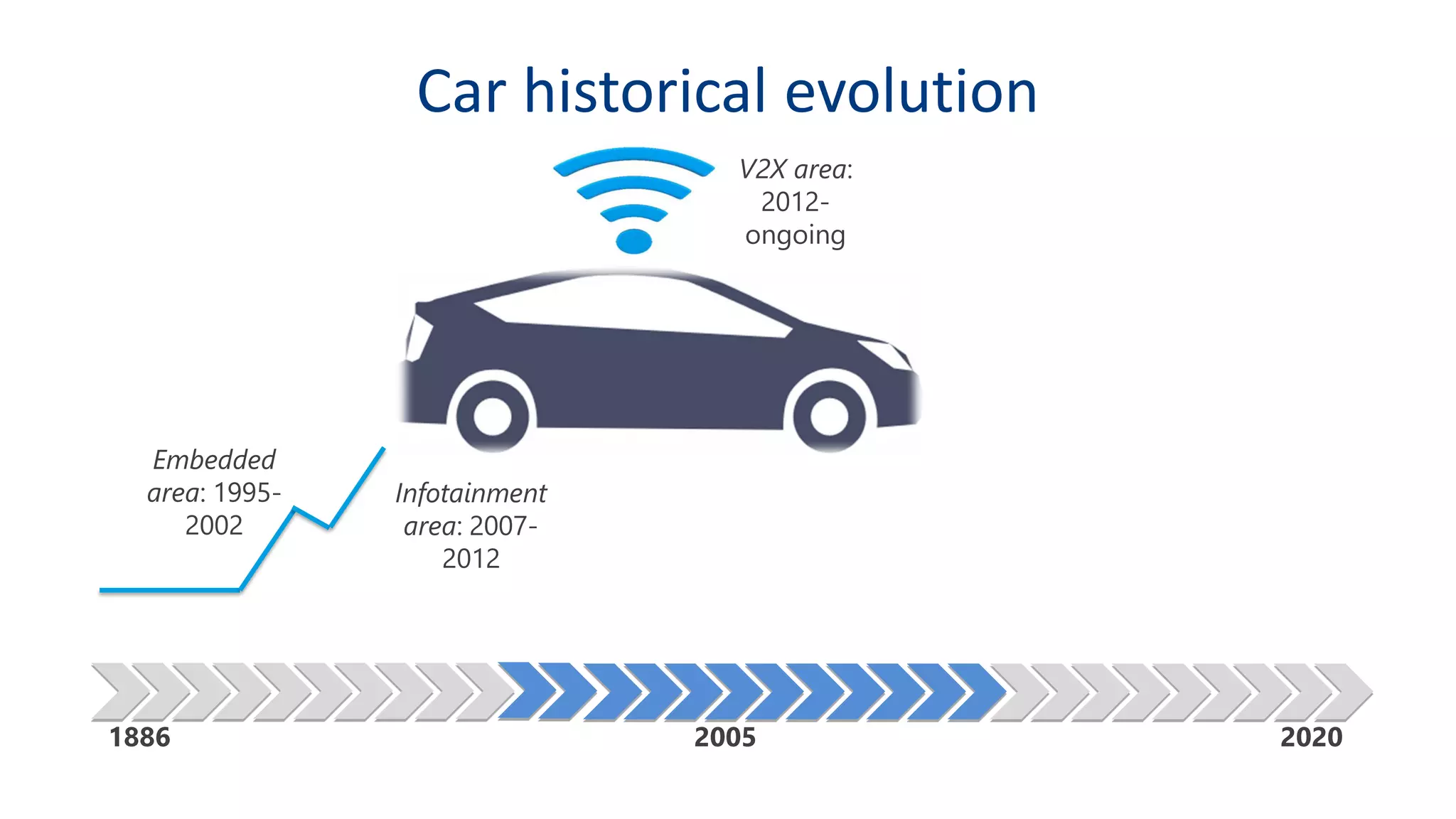
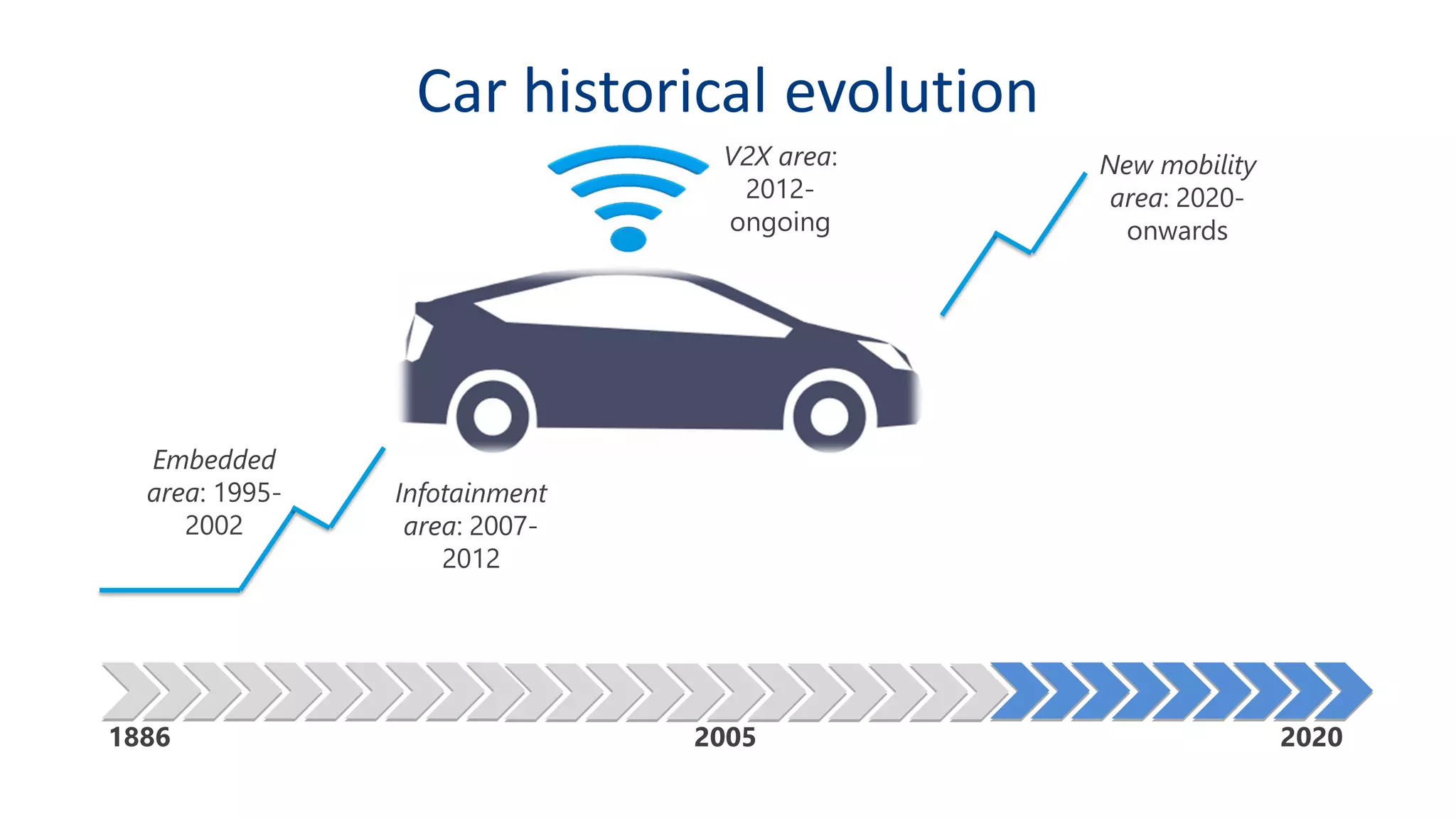
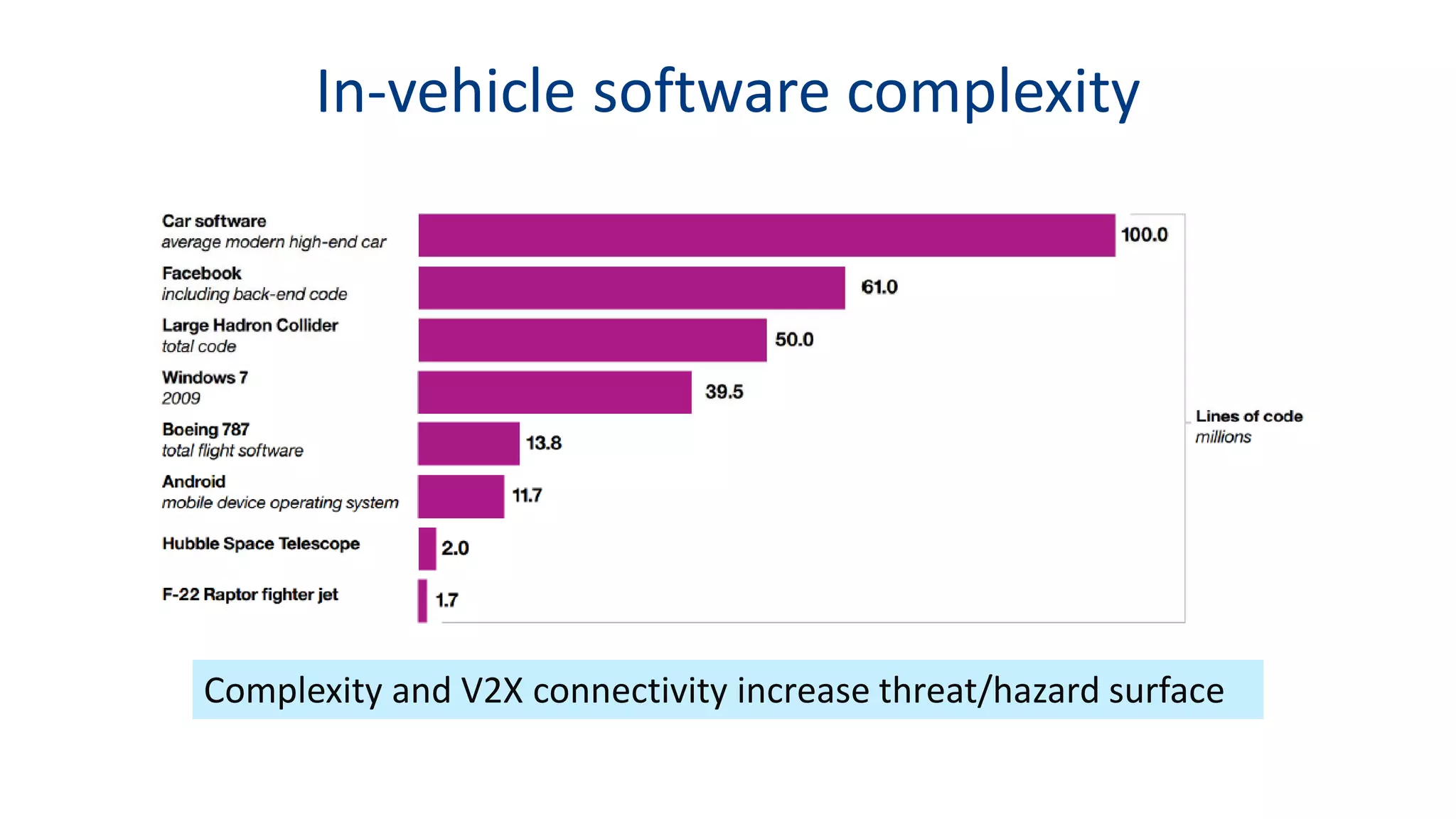
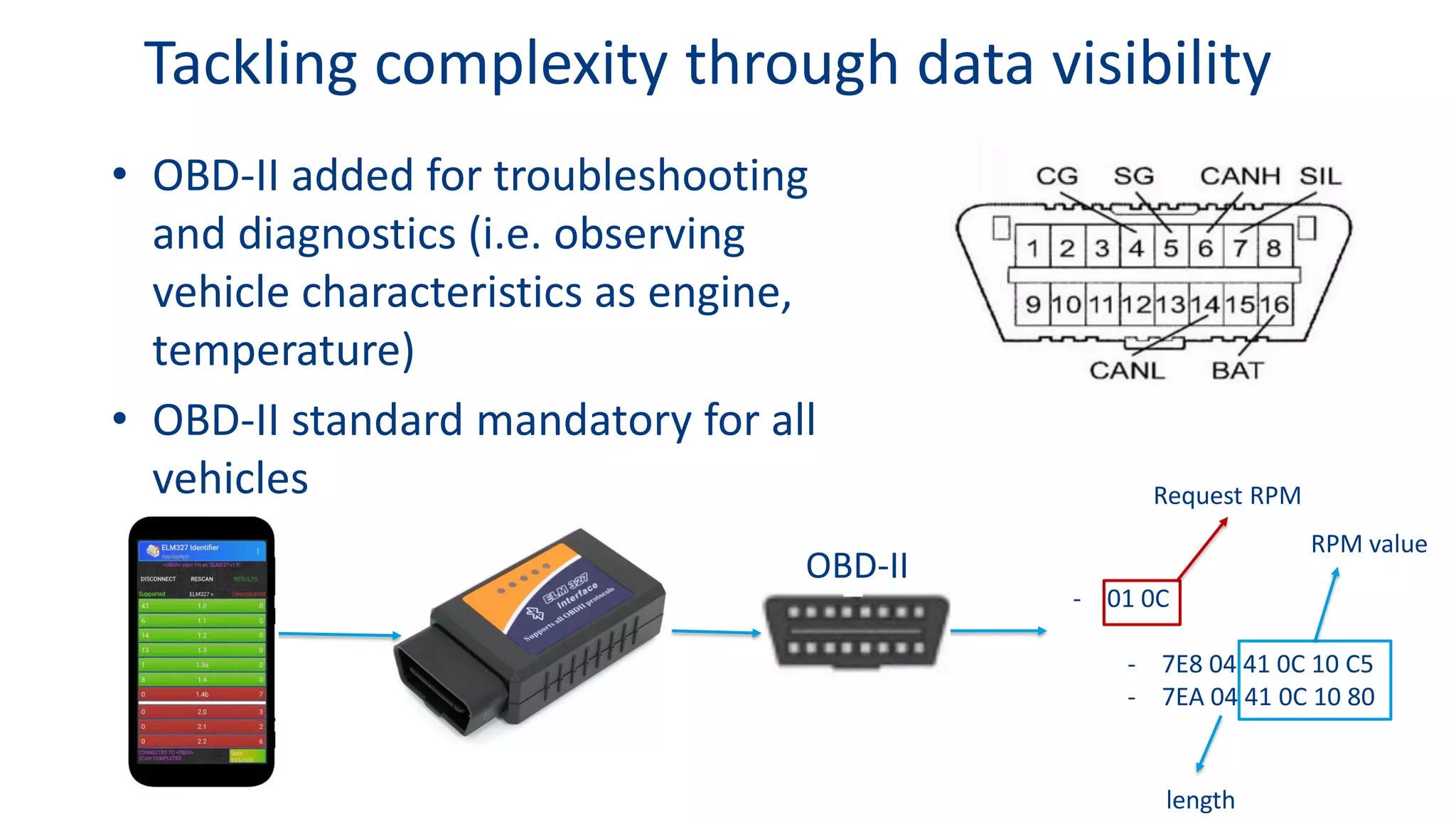
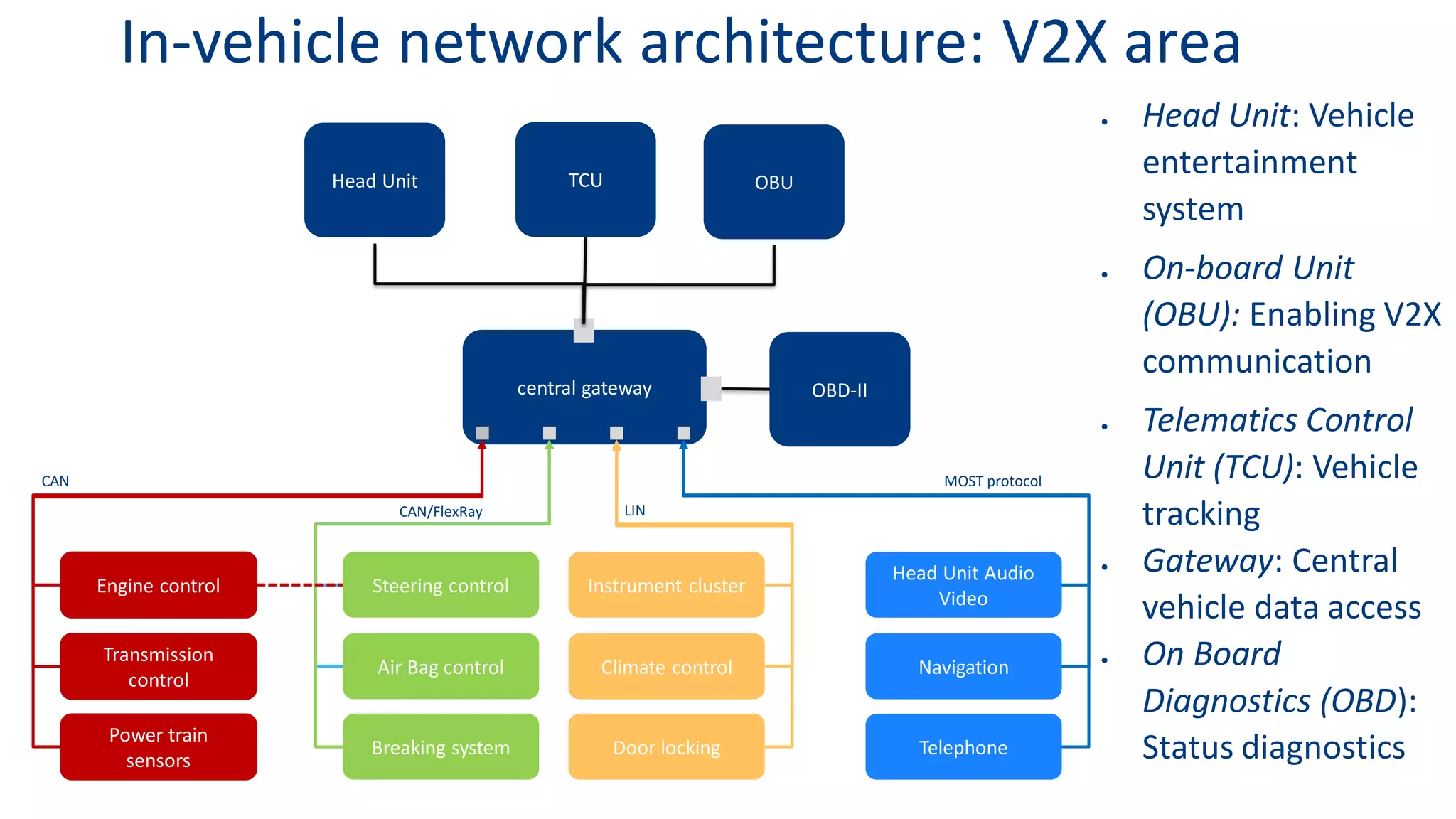
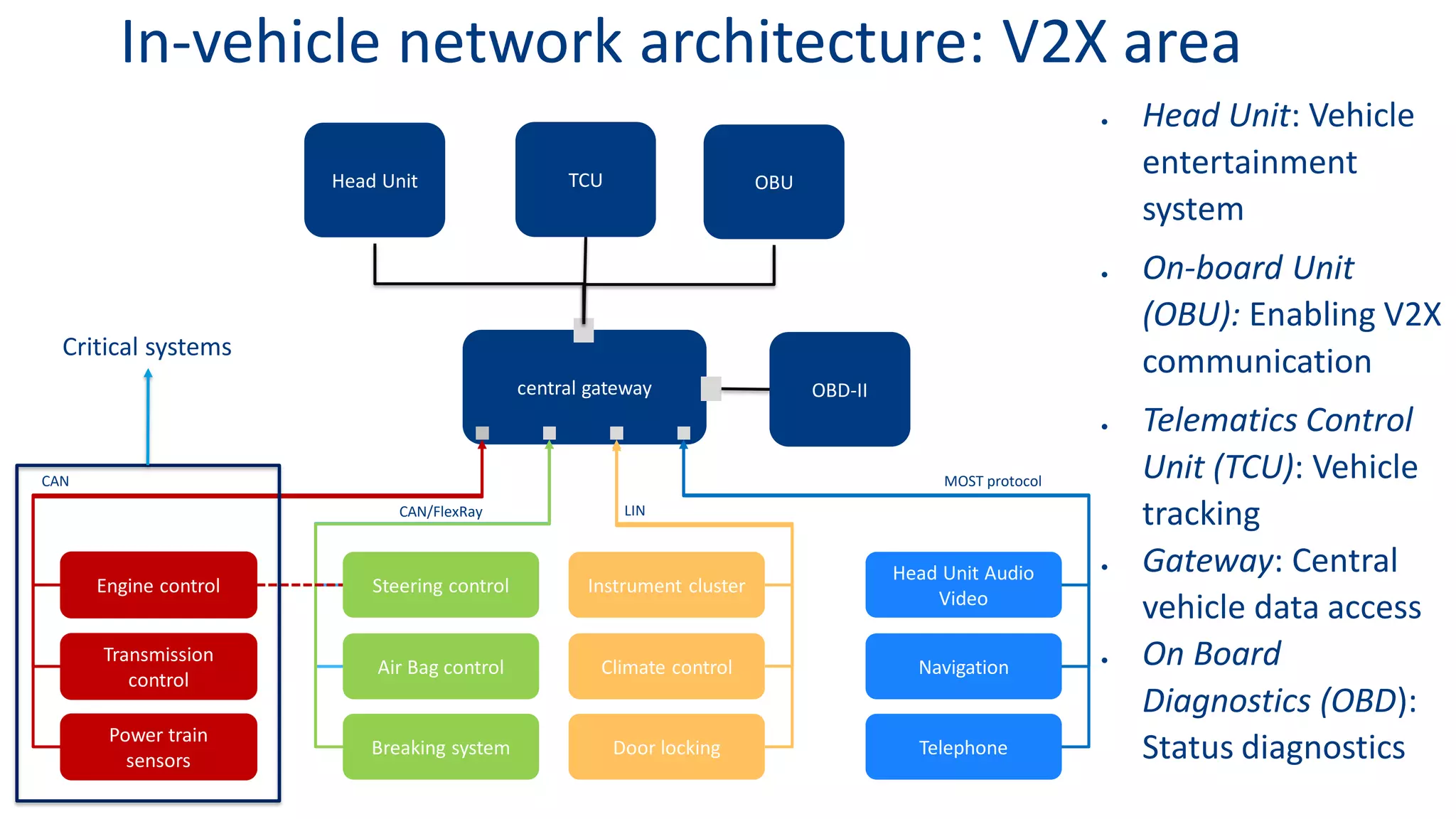
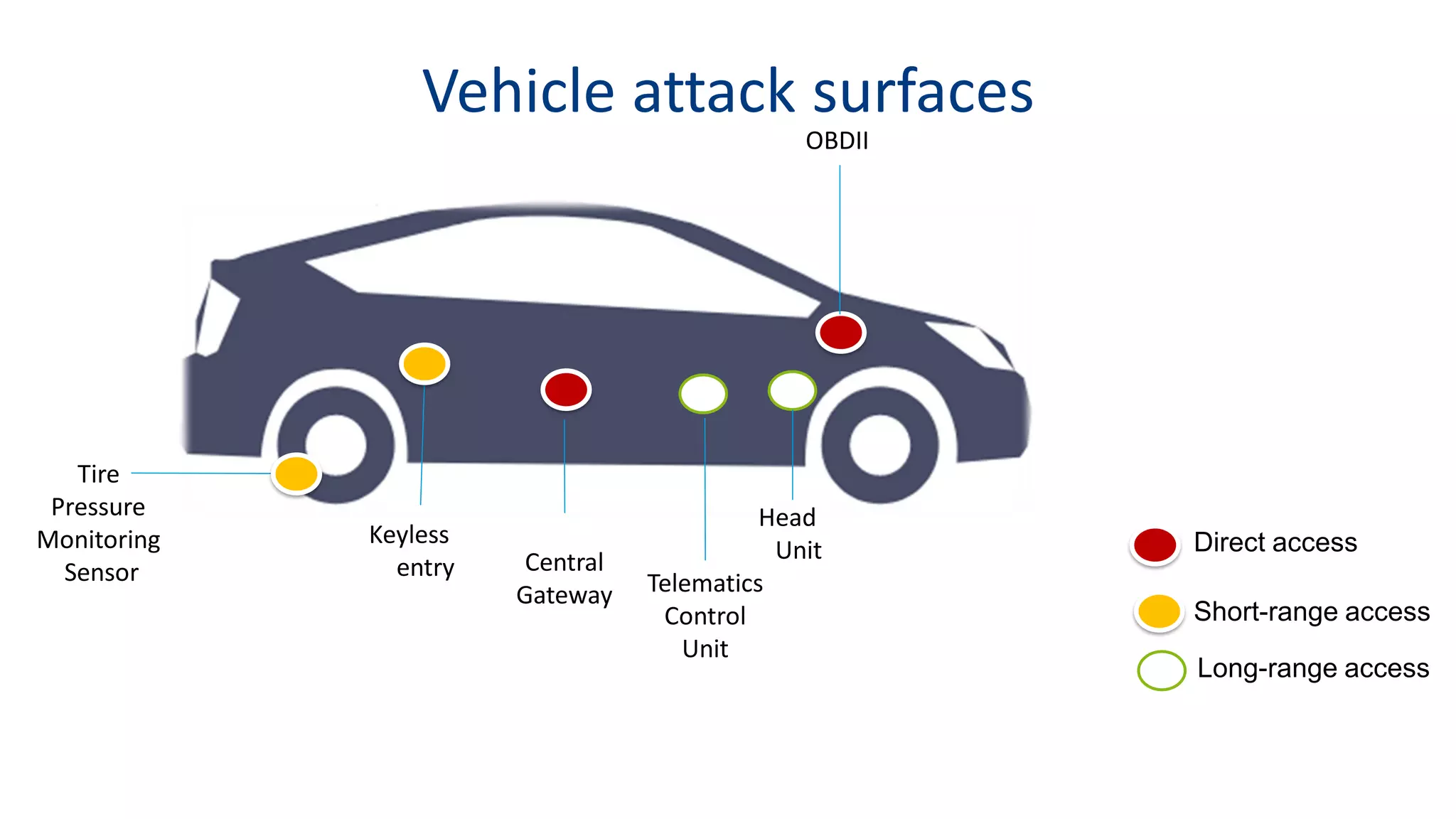
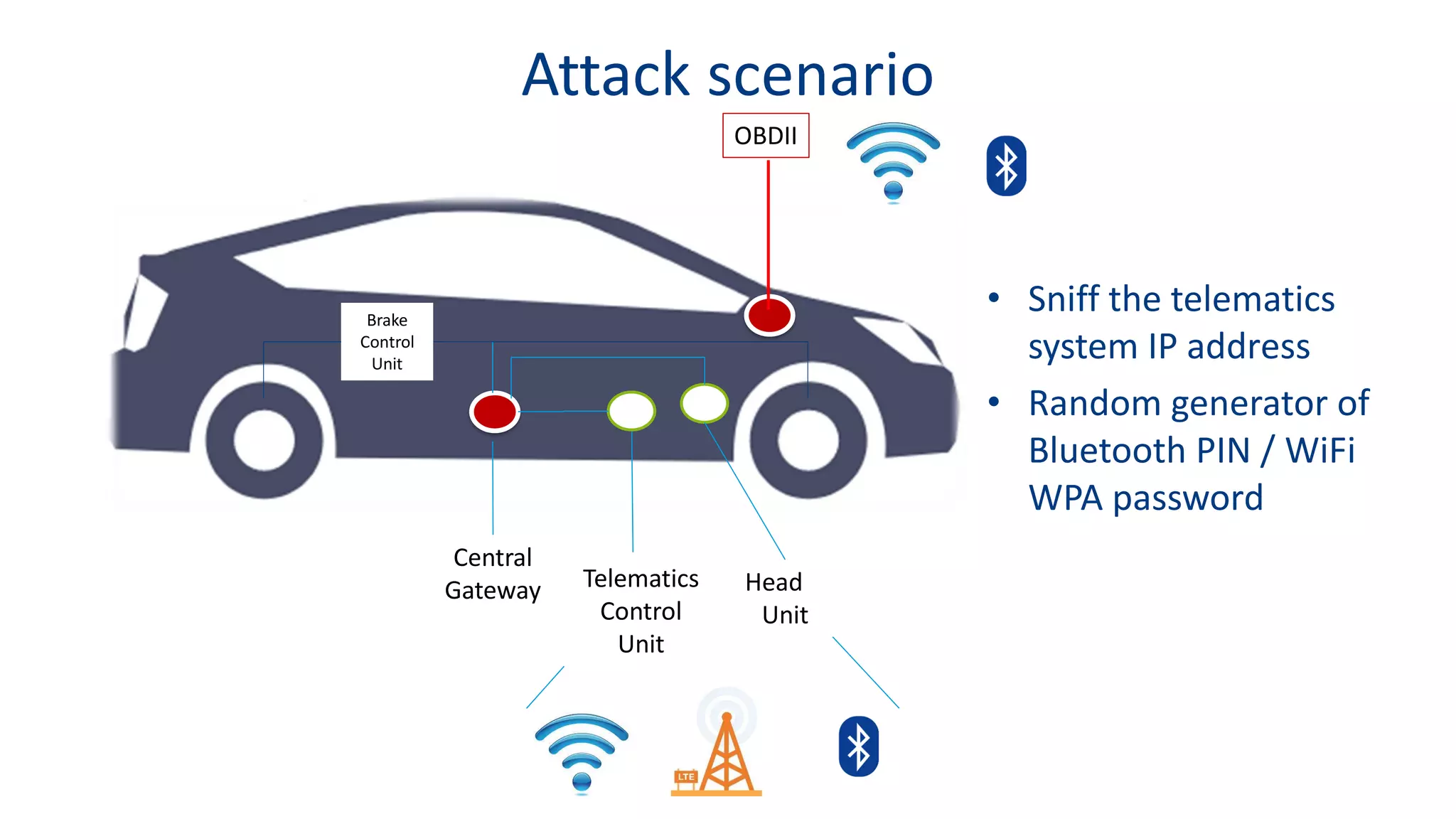
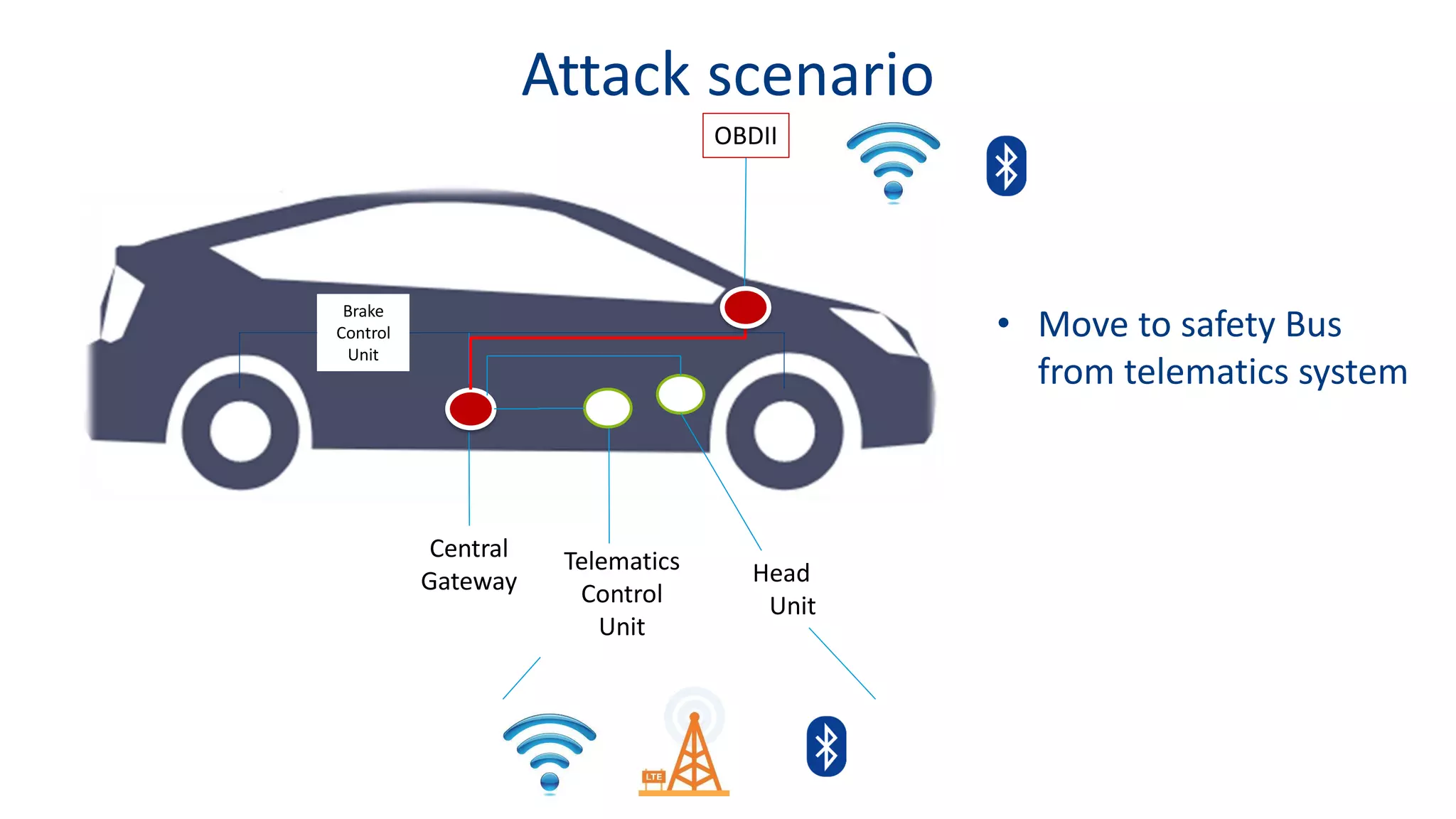
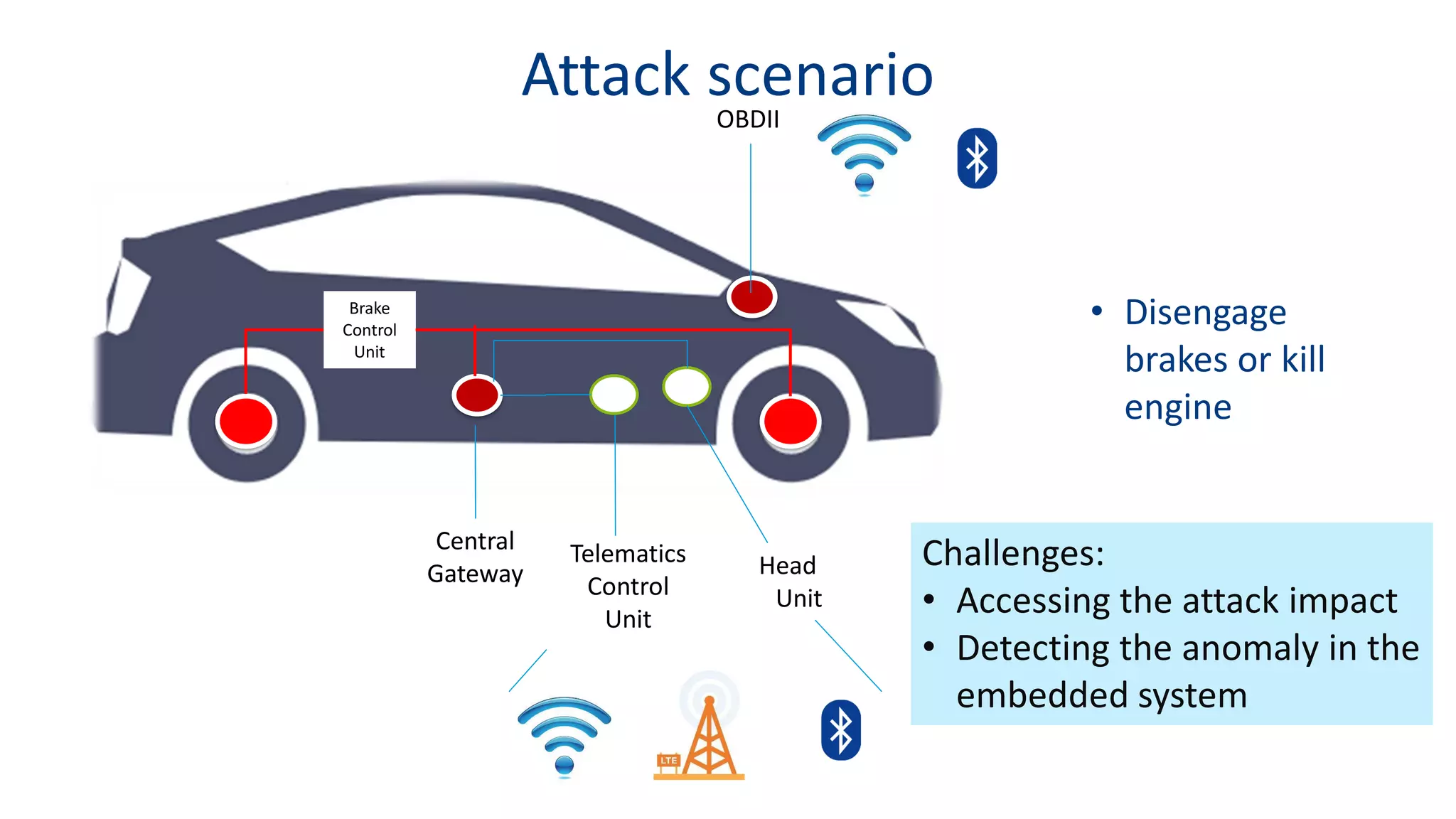
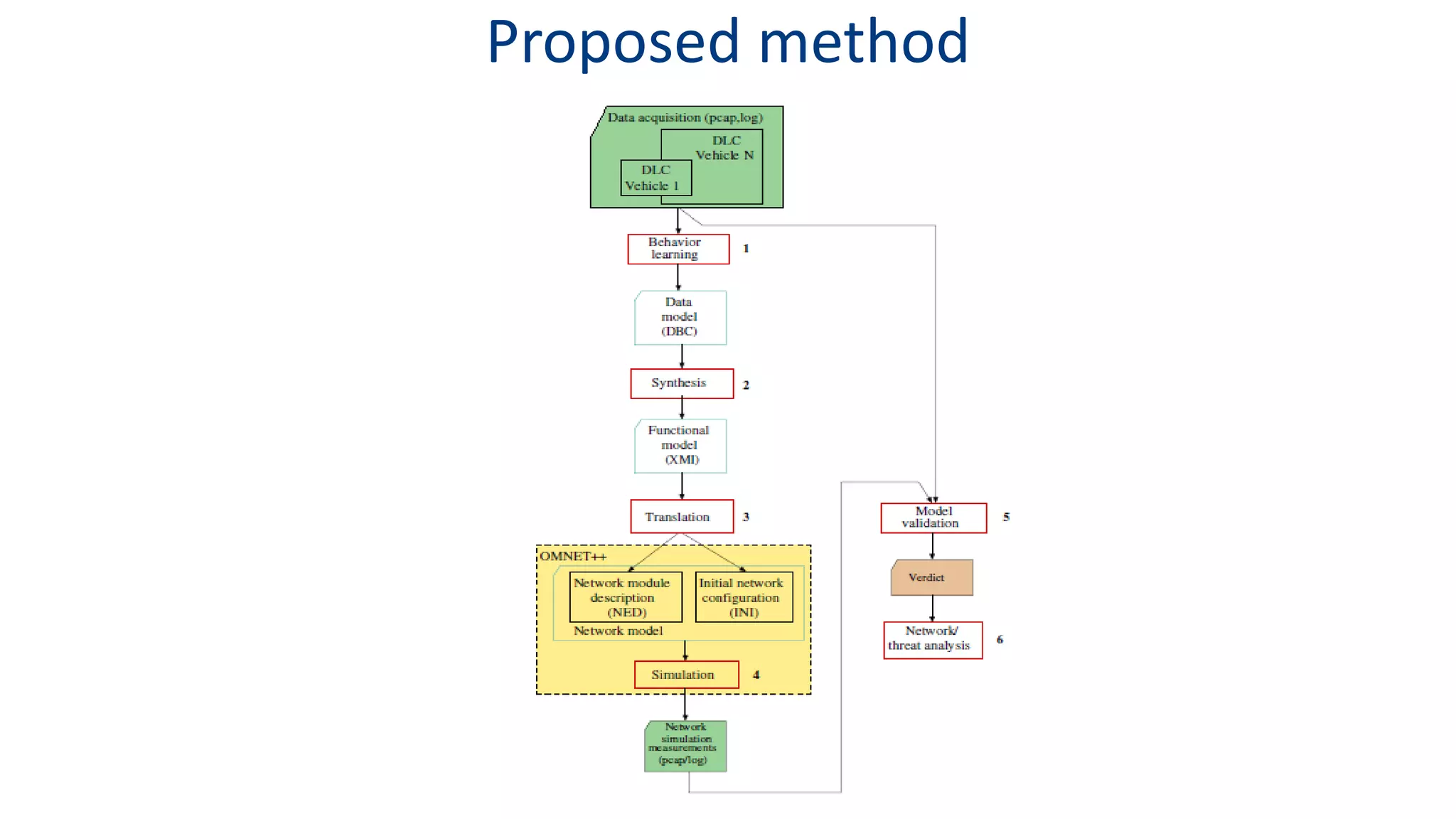
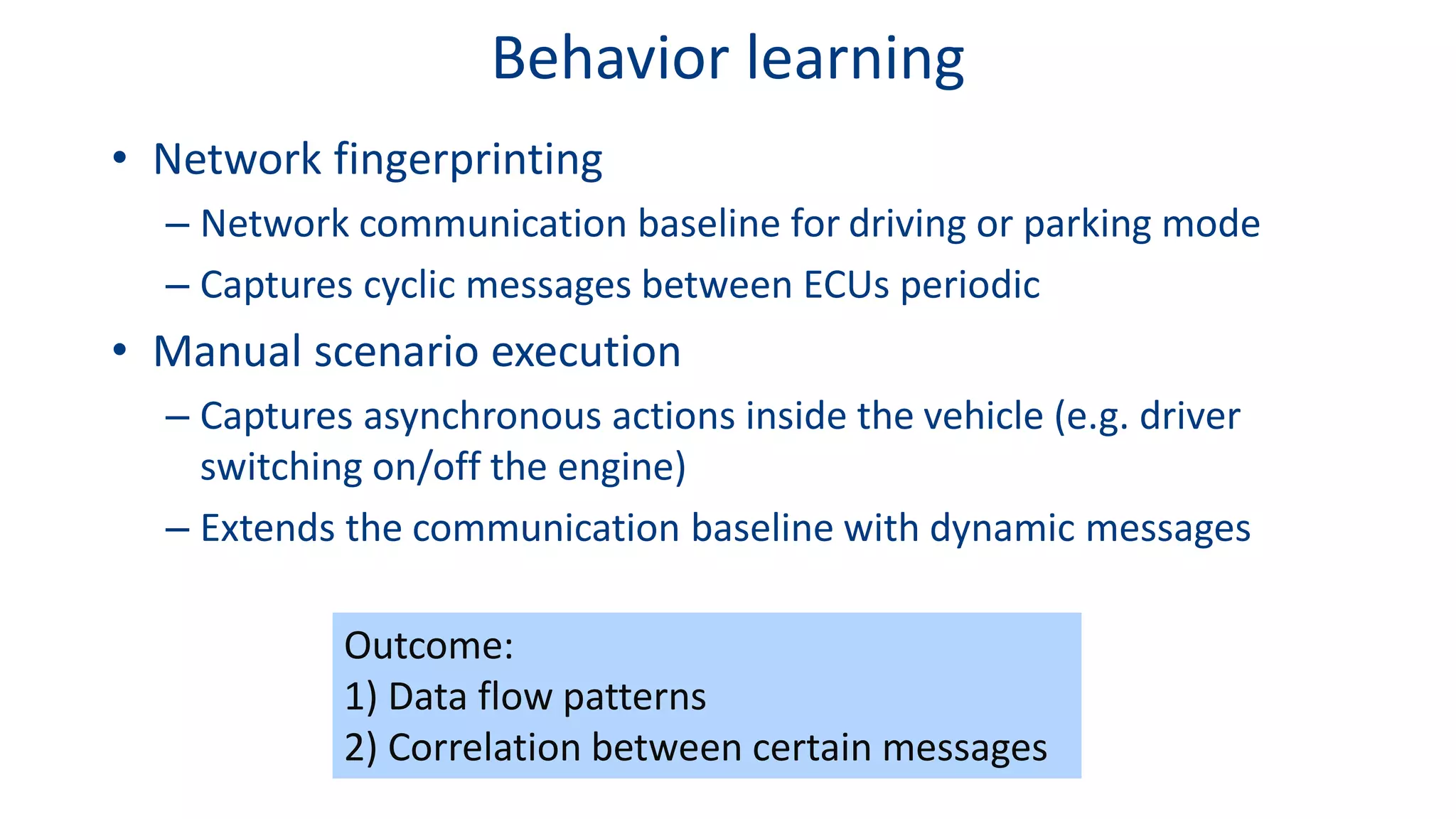
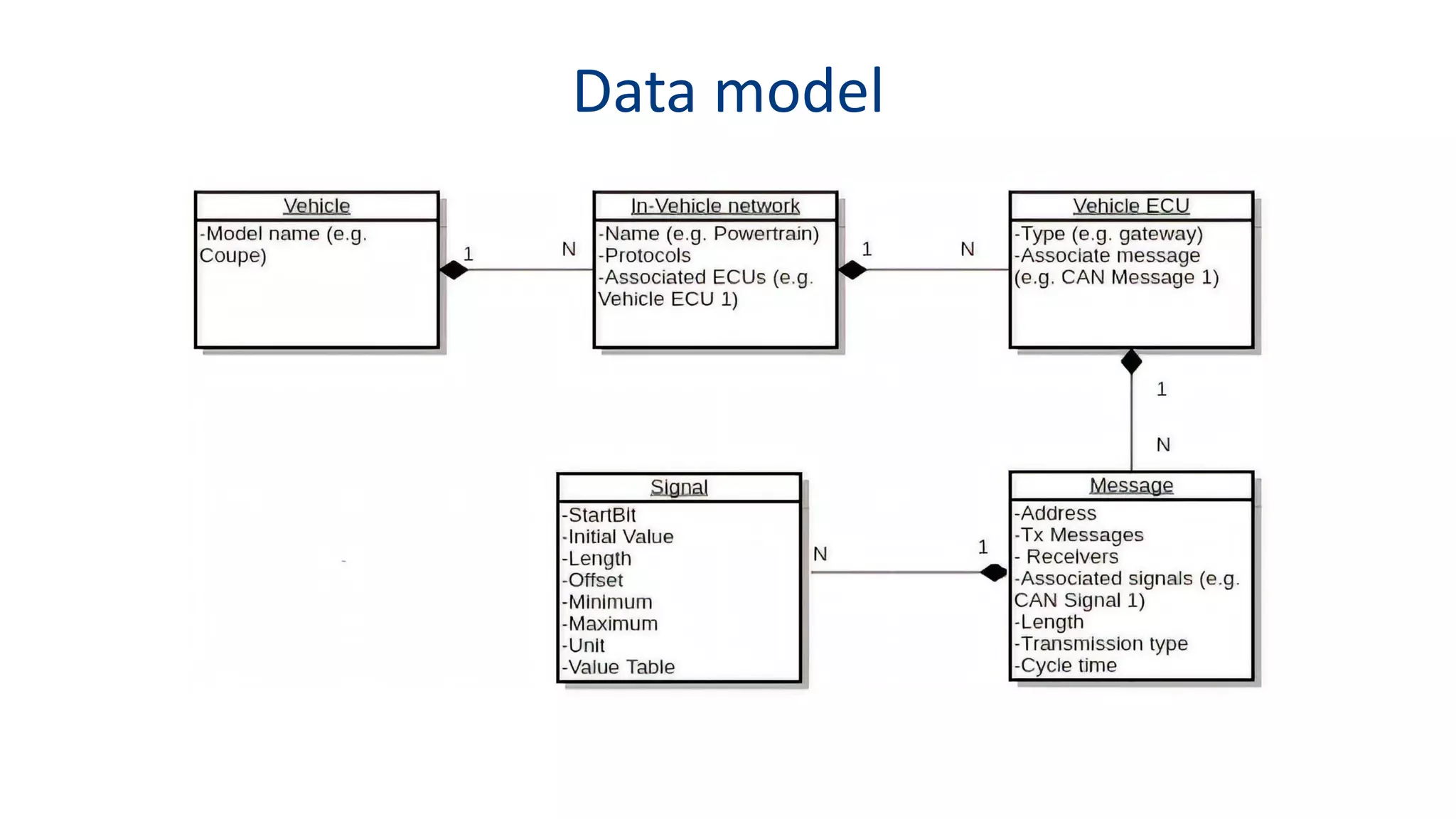
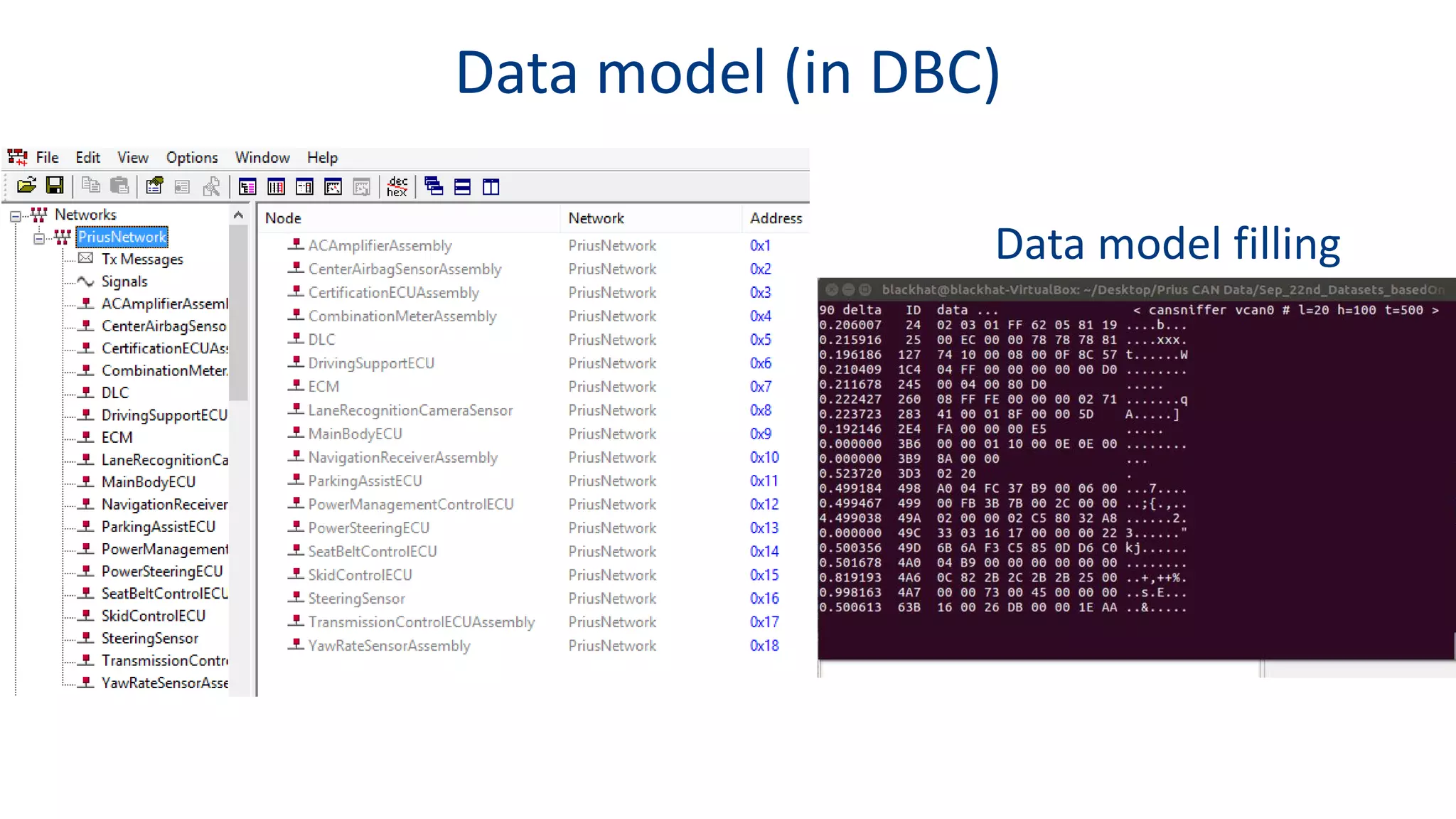
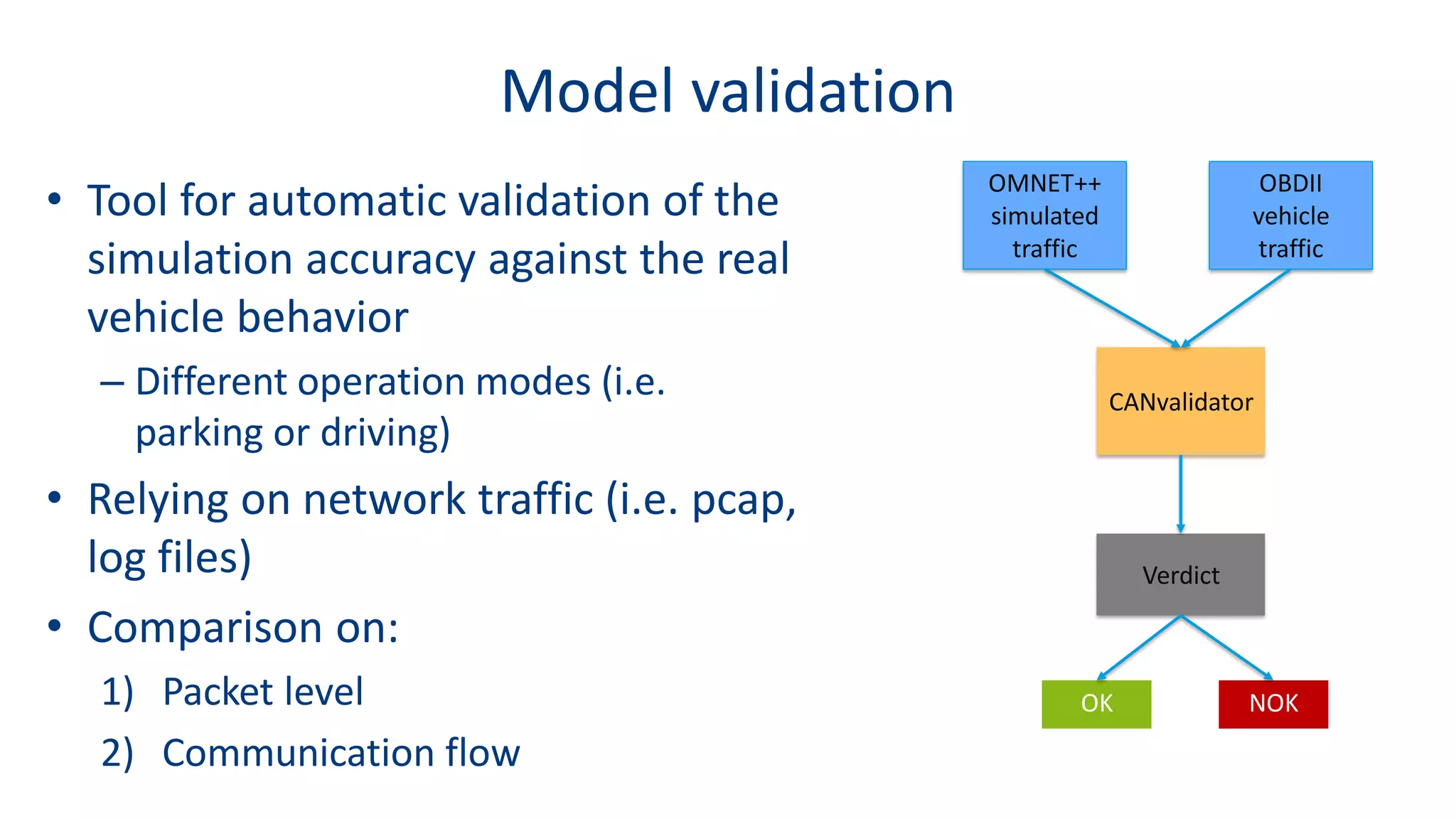
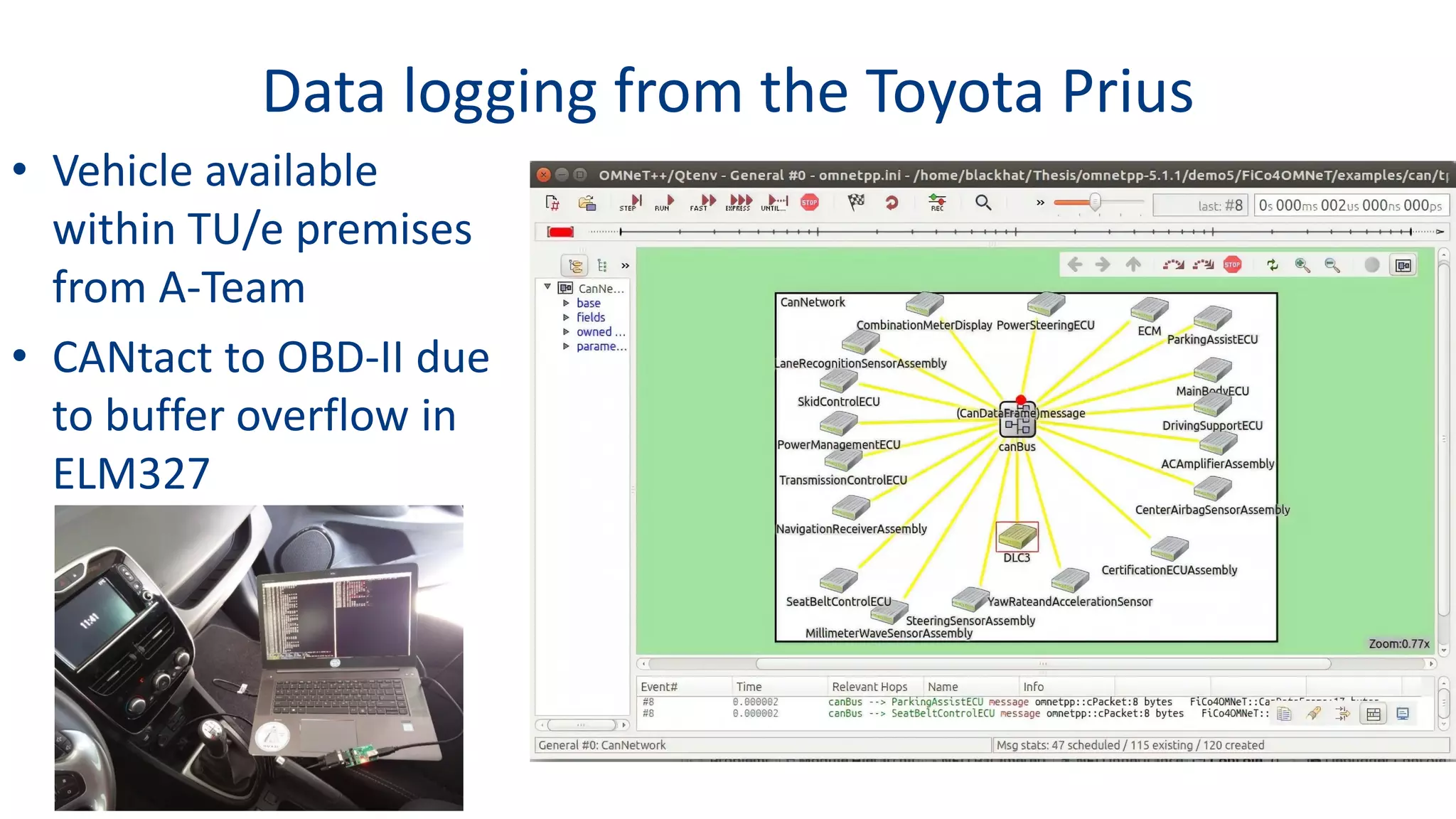
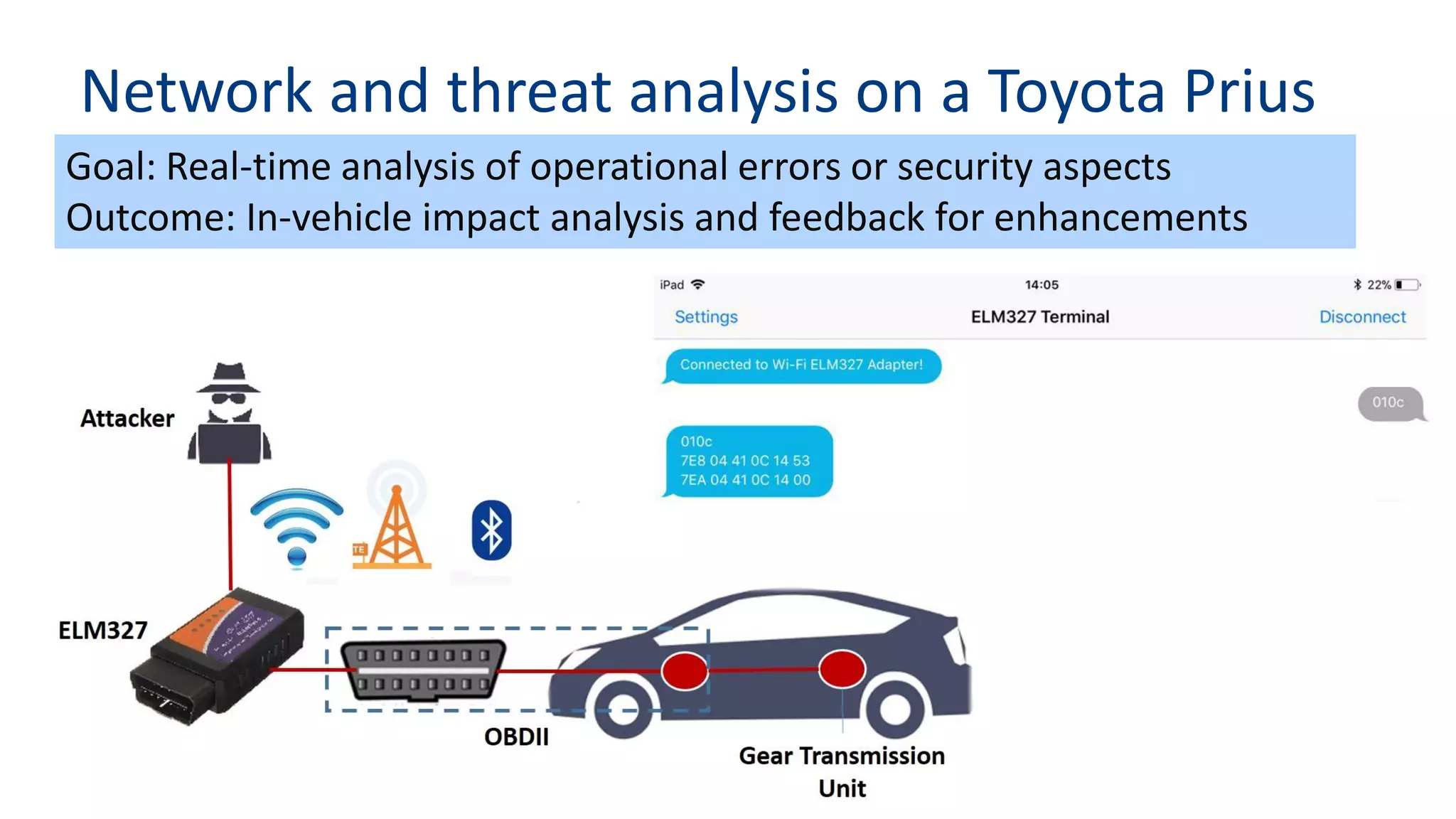
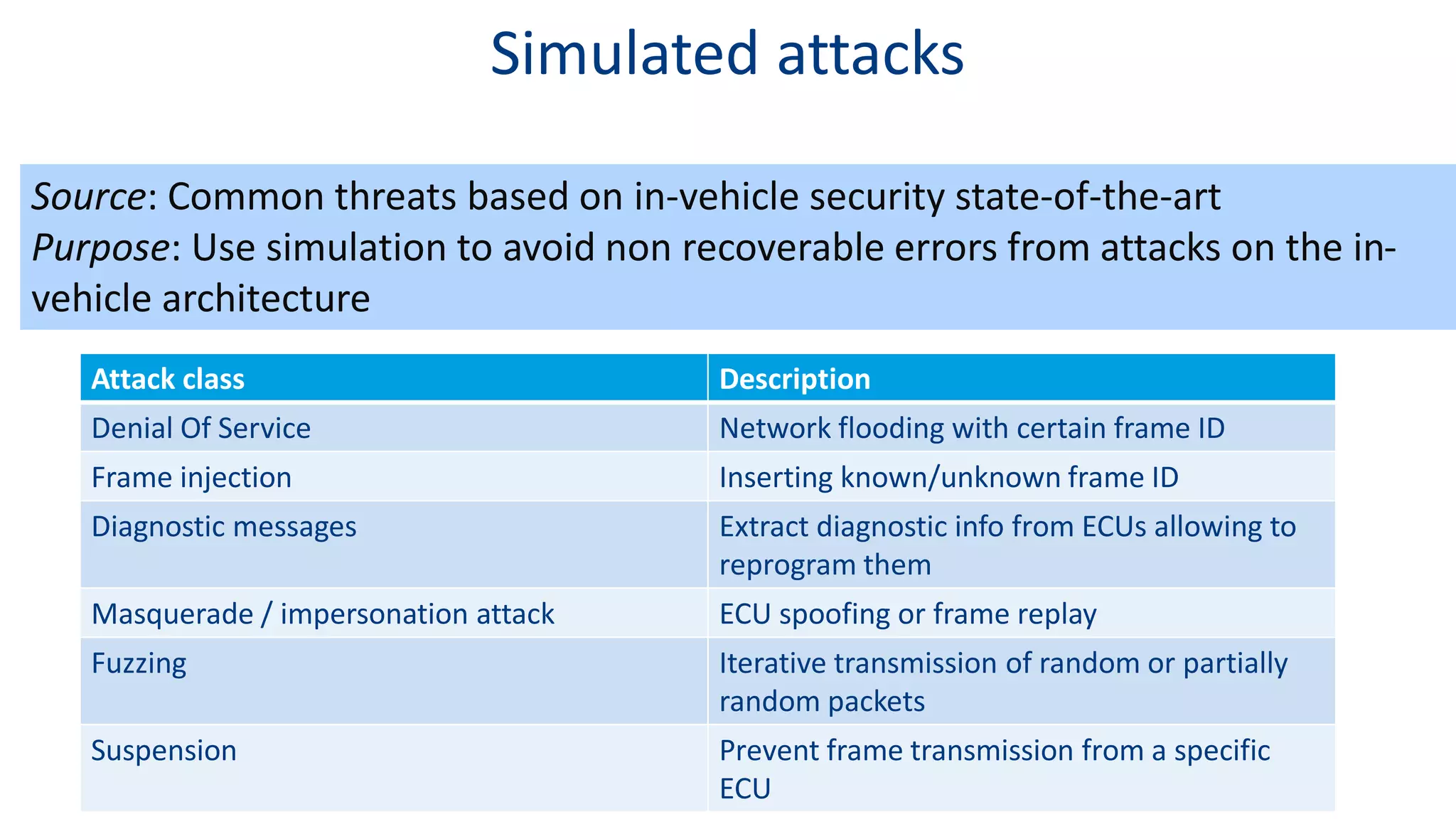
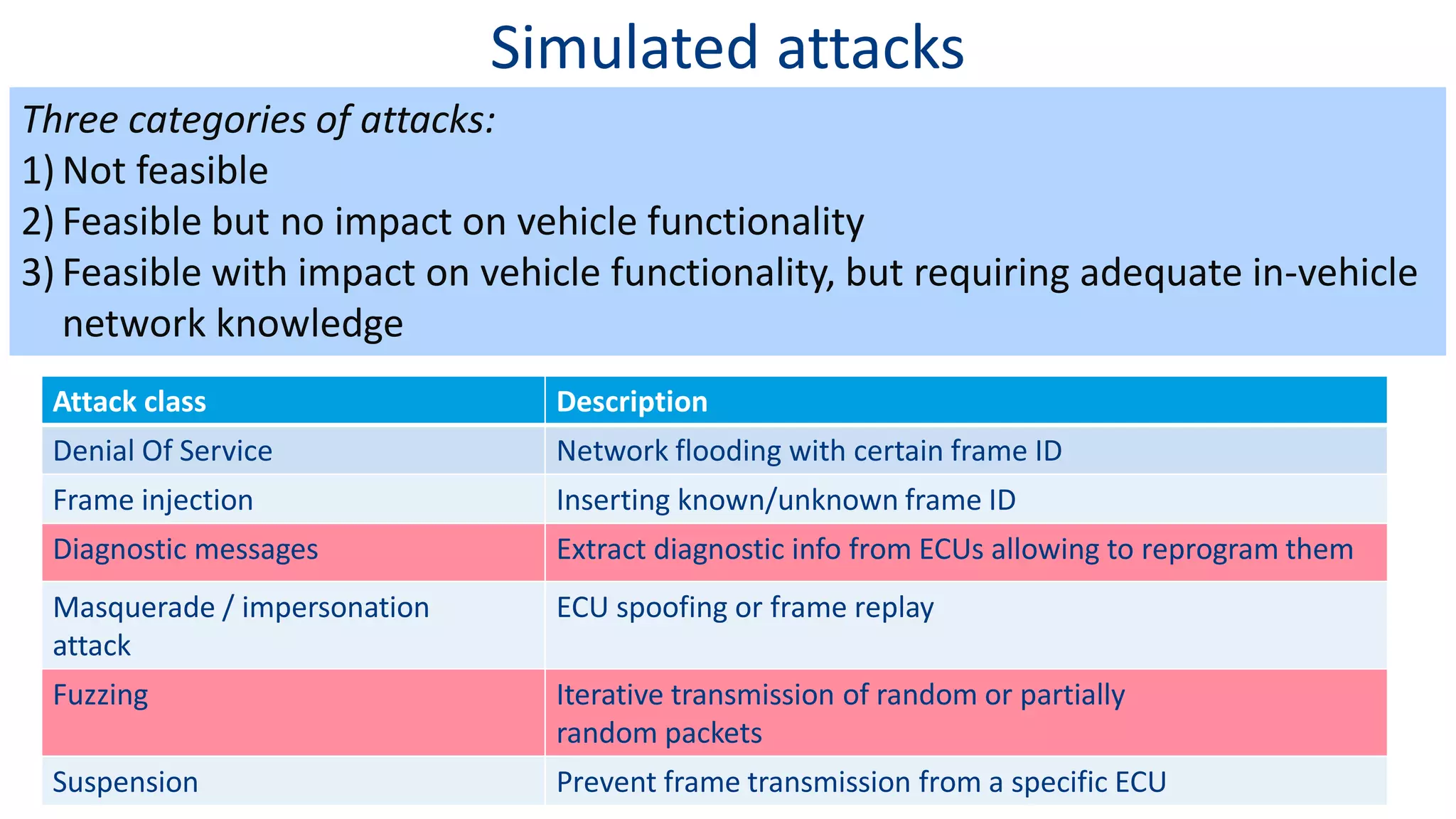
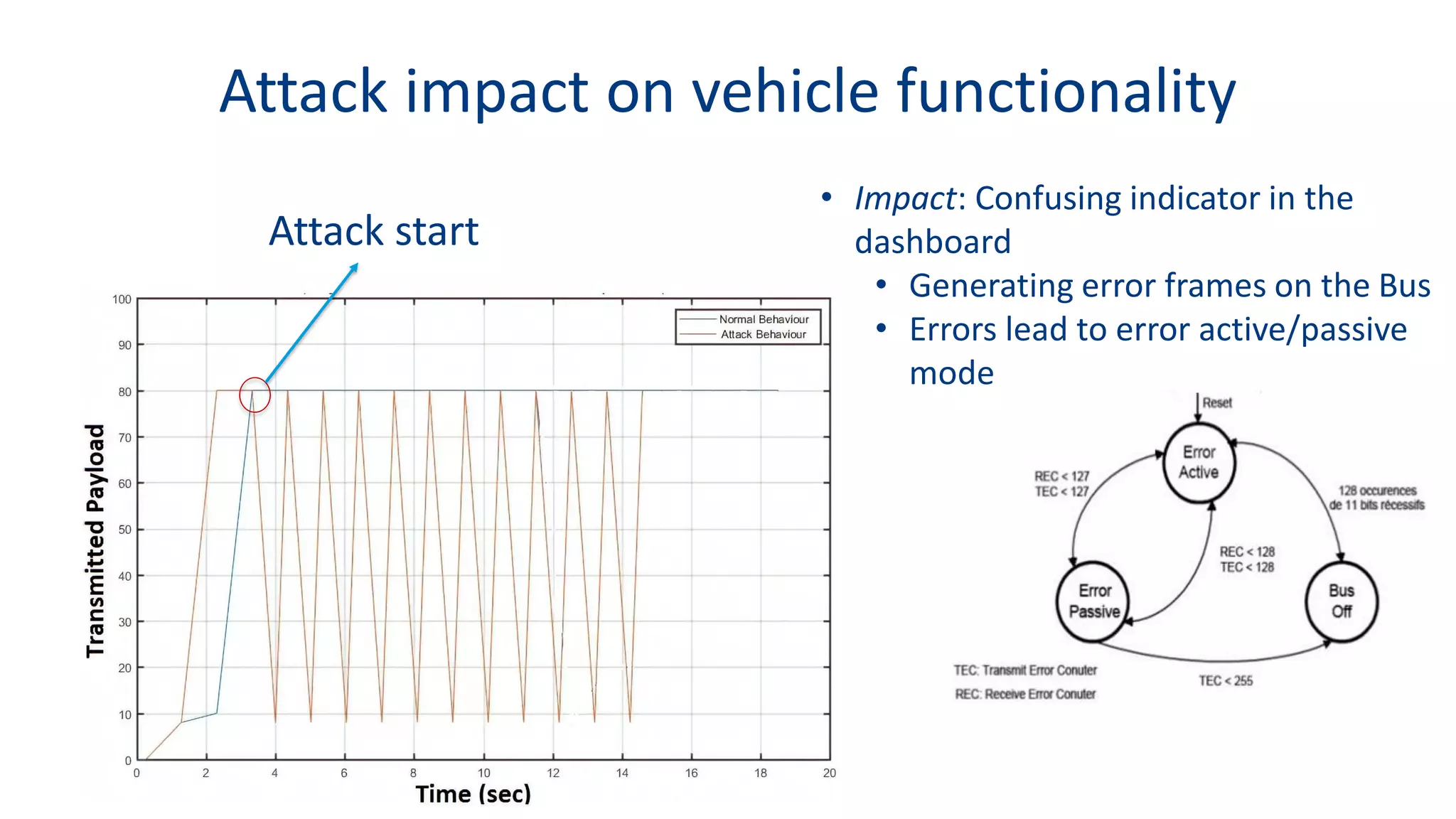
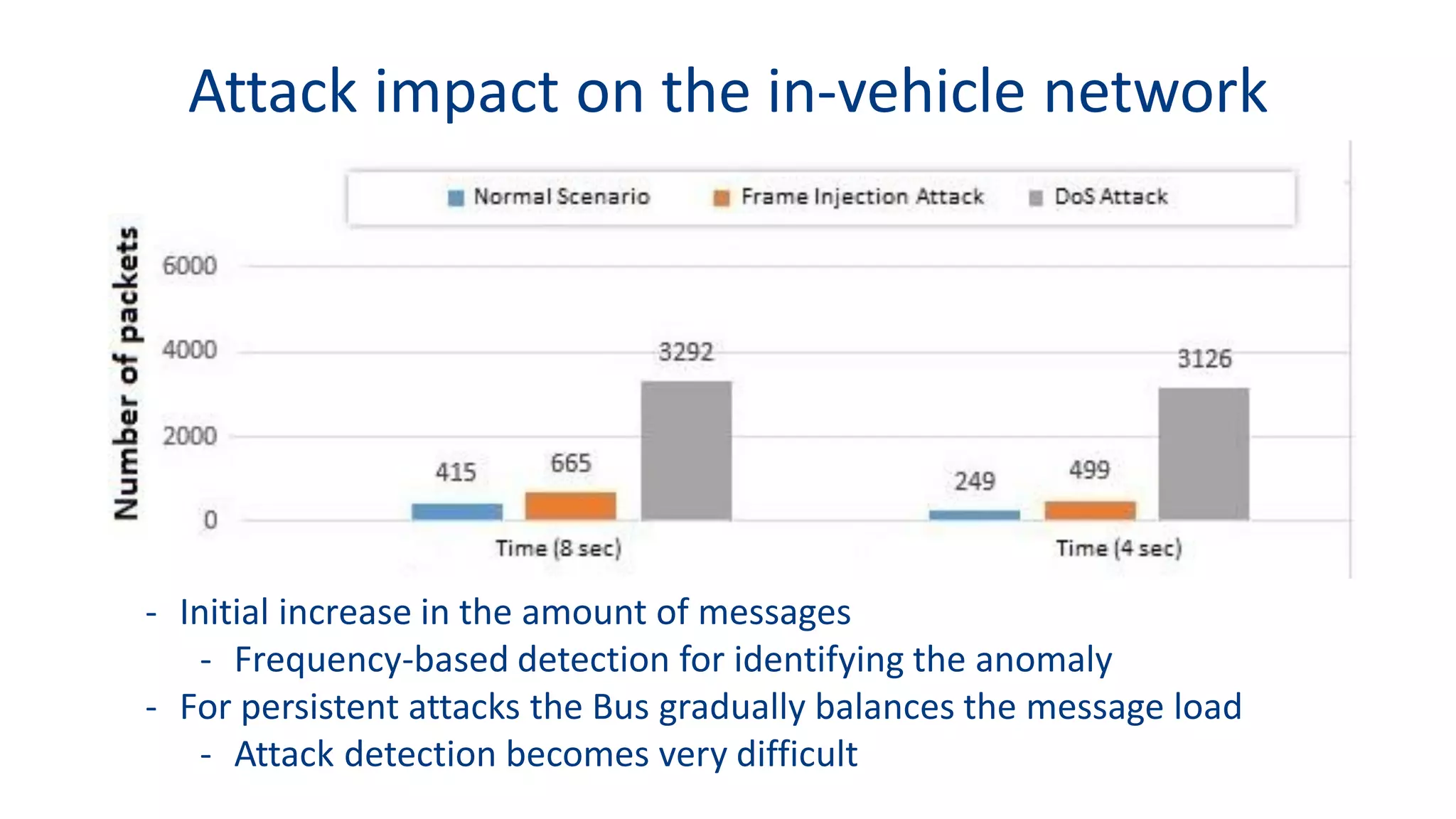
This document discusses model-based simulation and threat analysis of in-vehicle networks. It outlines the evolution of connected cars and the associated security risks. It then introduces the CARSEC environment for simulating in-vehicle networks and assessing risks. A case study applies CARSEC to evaluate security on a Toyota Prius architecture. Attacks are simulated and their impacts analyzed. The document concludes that CARSEC allows early detection of errors and threats to help enhance vehicle security. Future work includes automating the data collection process and directly using OBD-II port access.