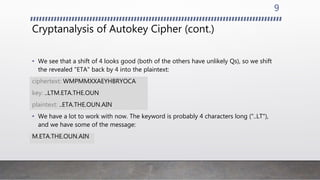
Cryptanalysis of the Autokey Cipher involves trying common words, letters, and letter combinations in the plaintext and using the relationship between the plaintext and key to reveal more of both. By guessing fragments of the plaintext shifted in the key, if the guesses are correct they will also appear in the plaintext shifted the other way. This feedback allows the cryptanalyst to quickly fill in more of the plaintext and key to decrypt the message.