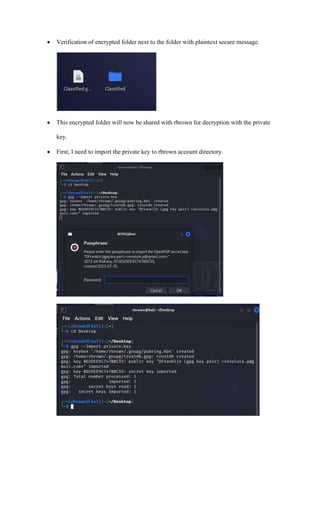
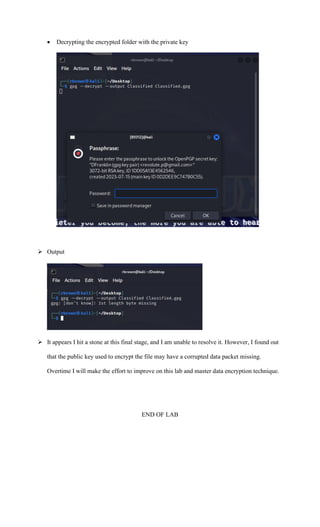
The document discusses the fundamentals of classical cryptography, including definitions of key terms such as plaintext, ciphertext, and cipher. It outlines symmetric and asymmetric encryption processes, their advantages and limitations, as well as practical exercises on encrypting names using substitution and transposition ciphers. Additionally, it describes the creation and use of key pairs for public key encryption, highlighting challenges faced during the implementation.

![Part 1 – Questions (30 marks)
1. What is the purpose of encryption? [4 Marks]
Ans: Encryption is a process of converting plaintext data into unreadable cyphertext
using a mathematical algorithm known as a cipher which when received by the intended
recipient can only be converted back to plain text with the right cryptographic key.
2. Describe the following terms: (a) plaintext, (b) ciphertext, (c) cipher, (d) encrypt, (e)
decrypt, (f) key [6 Marks]
Ans: Plaintext is the text that is readable prior to encryption, whereas ciphertext is the
conversion of plaintext into unreadable codes using an algorithm known as a cipher. A
cipher is a method or algorithm used to encrypt the plaintext and decrypt the ciphertext.
The effectiveness of the encryption is dependent on the cipher used, which can be AES,
RSA, Triple DES, or Blowfish. To encrypt and decrypt refers to the methods of coding
and decoding data using a pair of public and private keys. In cryptography, a key refers to
a public key that is shared and a private key that is kept confidential. In the encryption
and decryption processes, both keys are utilized. These keys can function as either a
symmetric or an asymmetric pair when combined.
3. Describe the steps of symmetric-key encryption [4 Marks]
• Step 1: the sender encrypts the plaintext message with a secret key.
• Step 2: the encrypted message is converted to unintelligible ciphertext which
cannot be read by anyone during transit.
• Ste 3: the recipient decrypts the ciphertext back to its original plaintext with the
same key used for encryption.
• Step 4: With symmetric key encryption, only the sender and receiver have access
to the data, as both parties share the same private key used for encryption and
decryption.](https://image.slidesharecdn.com/formativeassessment2-240210175840-cfc6b68a/85/Classical-Cryptography-and-Digital-Encryption-2-320.jpg)
![4. What is the difference between a substitution and a transposition cipher? [2 Marks]
Ans: Substitution and transposition ciphers are both forms of symmetric ciphers;
however, a substitution cipher is one in which the letters of a plaintext retain their
position but changes their identity by being replaced with other letters using a shift
number. On the other hand, transposition ciphers do the opposite whereby the letters of a
plaintext retain their identity by changing their position. For example, substitution cipher
(A, B, C) shift key = 2, will be (C, D, E), also transposition cipher of the word (SECRET)
would be (SCEERT).
5. List 3 different classical substitution ciphers [1 Mark]
Ans: Caesar Cipher, Porta Cipher, and Four-Square Cipher
6. List 3 different classical transposition ciphers [1 Mark]
Ans: Rail-Fence, Scytale Cipher, and Route Cipher.
7. Discuss the limitations of symmetric encryption [5 Marks]
Ans:
• symmetric encryption does not guarantee data confidentiality, integrity, and
authentication since the same key used for both encryption and decryption must
be shared.
• Symmetric encryption does not guarantee nonrepudiation since anyone with the
key can easily decrypt the message which may cause an argument between the
sender and receiver.
• A new secret key must be generated and shared each time communication takes
place. This creates an issue with the security and privacy of the keys.
8. Describe the asymmetric encryption process using digital signatures [5 marks]
Ans:
• Step 1: a plaintext message is generated.
• Step 2: The plaintext message is then run through a hashing algorithm (SHA-1,
SHA-256, MD5) which results in a particular digest.
• Step 3: the message digest is then encrypted with the sender’s private key.
• Step 4: the result of the encrypted digest is the signature of the message.
• Step 5: both the signature and message are then transmitted to the intended
recipient.](https://image.slidesharecdn.com/formativeassessment2-240210175840-cfc6b68a/85/Classical-Cryptography-and-Digital-Encryption-3-320.jpg)
![• Step 6: On the receiving end the recipient uses the sender’s public key to decrypt
the digital signature for verification which will result in the sender’s original
digest.
• Finally, the recipient then calculates a hash of the message and if the sender’s
digest matches the recipient’s digest, then it proves that the message was digitally
signed by the intended sender and the content of the message was unchanged.
9. What is a Hash Function and why is it useful? [2 Marks]
Ans: A hash function is an algorithm used to convert plaintext data of any size to a hash
value of a particular length. A hash function is useful because it protects data from
unauthorized changes, thereby preserving its integrity.
Part 2 - Practical Exercises (70 marks)
For these practical exercises, you will have to encrypt some text using classical cryptography
algorithms and then you will be tasked with creating and sharing a secret digital message by key
pair generation.
Exercise 1
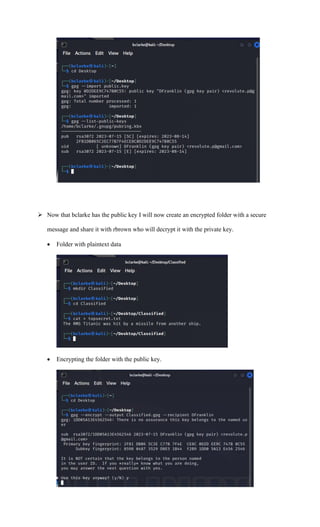
1. Encrypt your first name using any classical substitution cipher.
• Plaintext: Damaine
• Alphabet: English
• Shift Key: #3
• Cipher: Caesar Cipher
• Ciphertext: Damaine (GDPDLQH)
A B C D E F G H I J K L M
D G H L P
N O P Q R S T U V W X Y Z
Q
Note: See steps on the next page](https://image.slidesharecdn.com/formativeassessment2-240210175840-cfc6b68a/85/Classical-Cryptography-and-Digital-Encryption-4-320.jpg)