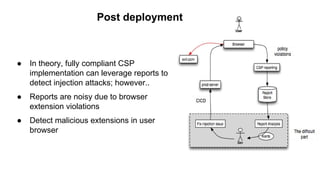
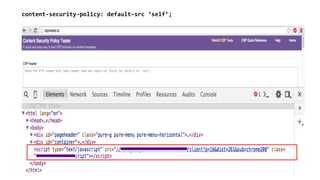
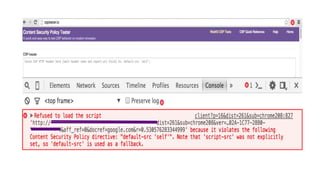
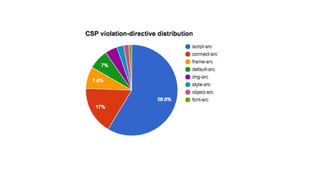
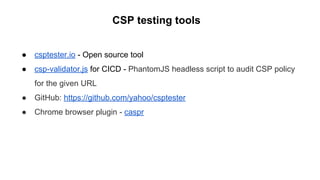
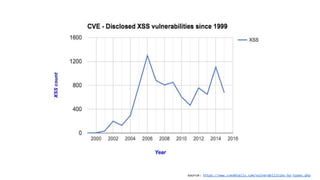
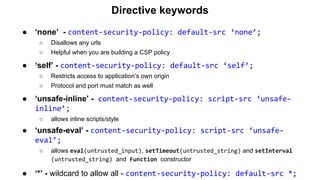
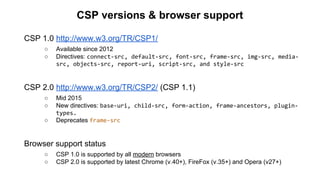
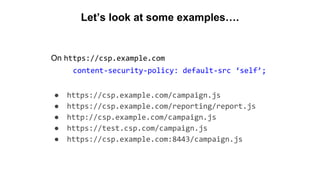
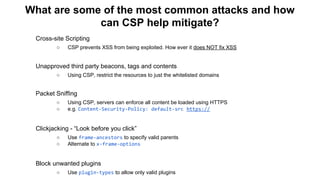
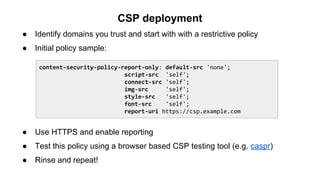
The document discusses the importance of implementing Content Security Policy (CSP) as a defense against cross-site scripting (XSS) and other web attacks by allowing the specification of trusted resource locations. It outlines CSP directives, best practices for deployment, and highlights the need to balance security with usability, mentioning potential challenges from browser extensions. Additionally, it offers tools and methods for testing and validating CSP compliance to enhance web application security.





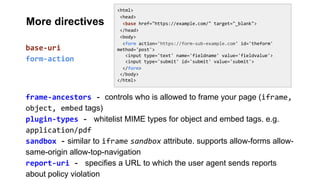
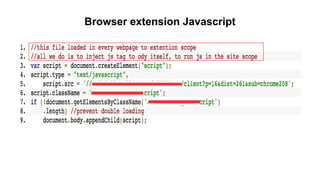
![Why inline Javascript is bad?
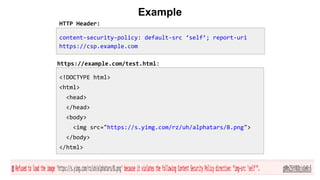
Content-Type: text/html; charset=utf-8
<script>console.log("Legitimate javascript code as part of the page");</script>
<div> Welcome, <script>alert("Attack!");</script></div>
https://trusted.example.com/welcome.php?username=<script>alert("Attack!");</script>
<?php
echo '<script>console.log("This is a legitimate javascript code as part of the
page");</script>'
echo '<div class="header"> Welcome, ' . $_GET['username']; . '</div>';
?>
It is hard for the browser to distinguish trusted javascript with a malicious script](https://image.slidesharecdn.com/copyofconference-contentsecuritypolicy-151123223022-lva1-app6892/85/Content-Security-Policy-Lessons-learned-at-Yahoo-15-320.jpg)


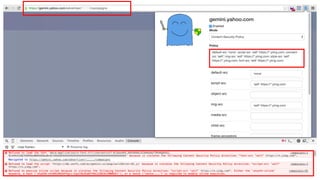
![Automation with csp-validator.js
% bin/phantomjs csp-validator.js
Usage: csp-validator.js [--quiet] <URL>
Returns:
0 => SUCCESS - No violations
1 => FAIL - System/parse/input error
2 => CSP-VIOLATION - Violation detected](https://image.slidesharecdn.com/copyofconference-contentsecuritypolicy-151123223022-lva1-app6892/85/Content-Security-Policy-Lessons-learned-at-Yahoo-21-320.jpg)