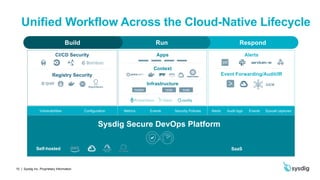
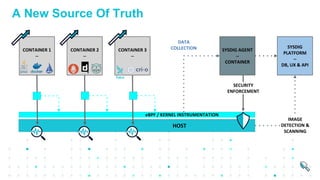
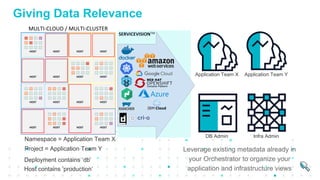
The document describes Sysdig Secure DevOps Platform, which provides unified visibility and security for production deployments of cloud-native applications. It converges security and monitoring to embed security, maximize availability, and validate compliance across the cloud-native lifecycle. The platform provides a single source of truth with context about containers, hosts, services and infrastructure. It leverages metadata to organize application and infrastructure views. The platform includes Sysdig Monitor for observability and reliability and Sysdig Secure for protection and assurance. It addresses security and operations needs for DevOps workflows across build, run and respond phases in a cloud-native environment.