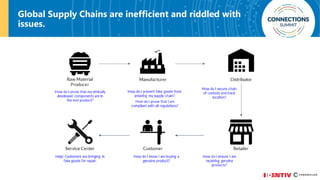
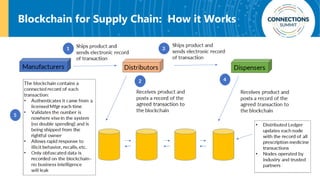
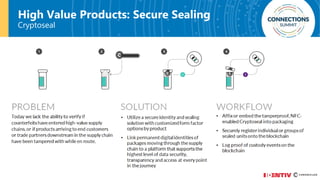
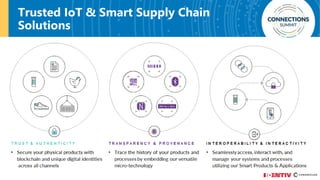
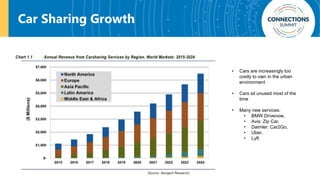
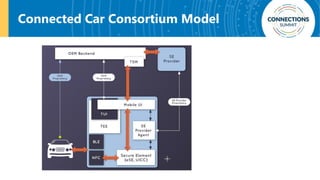
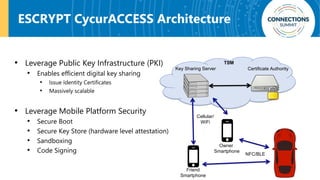
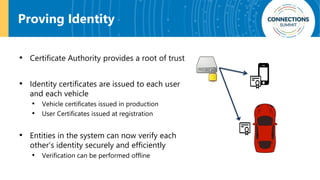
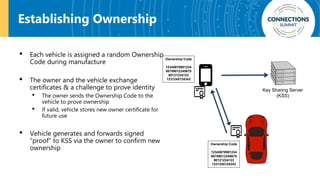
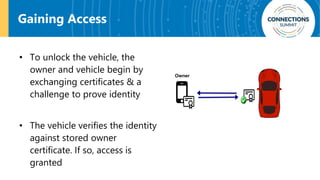
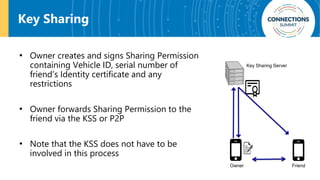
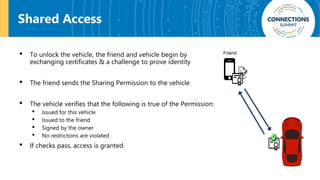
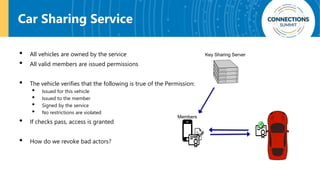
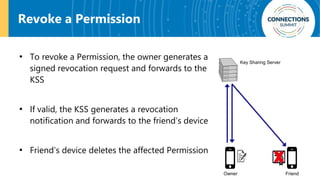
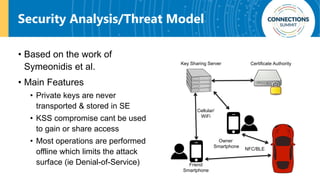
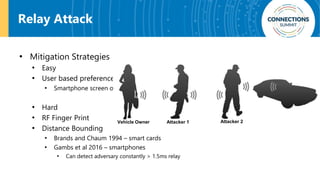
The document discusses the integration of blockchain and NFC technology in supply chains to combat issues like counterfeiting, detailing products like temperature-sensitive data logging labels. It also covers a framework for secure digital key sharing for vehicle access, highlighting smartphone integration and a public key infrastructure (PKI) for secure identity verification. The presentation concludes with insights on security analysis and future work regarding digital key sharing and vehicle access technology.