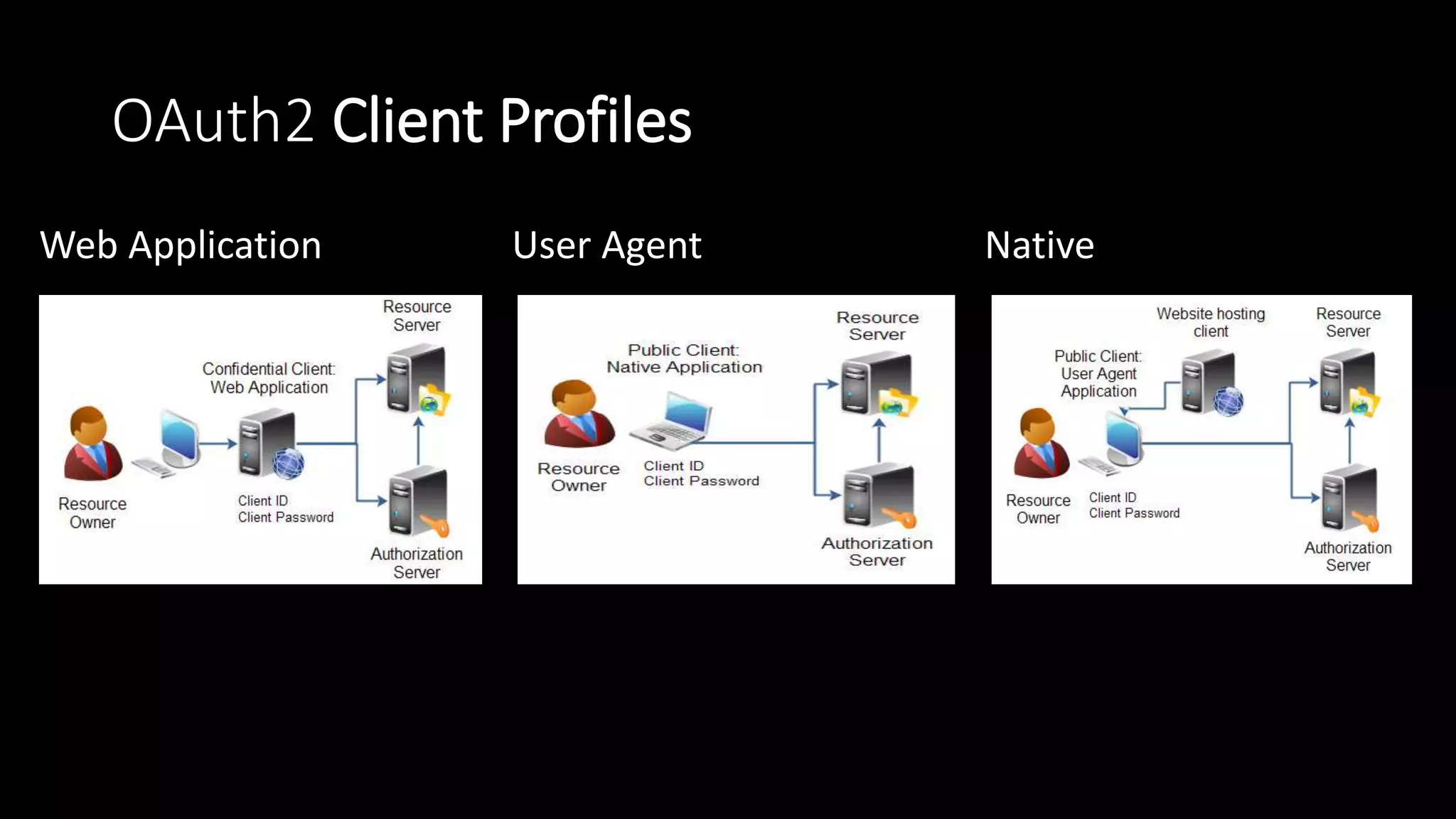
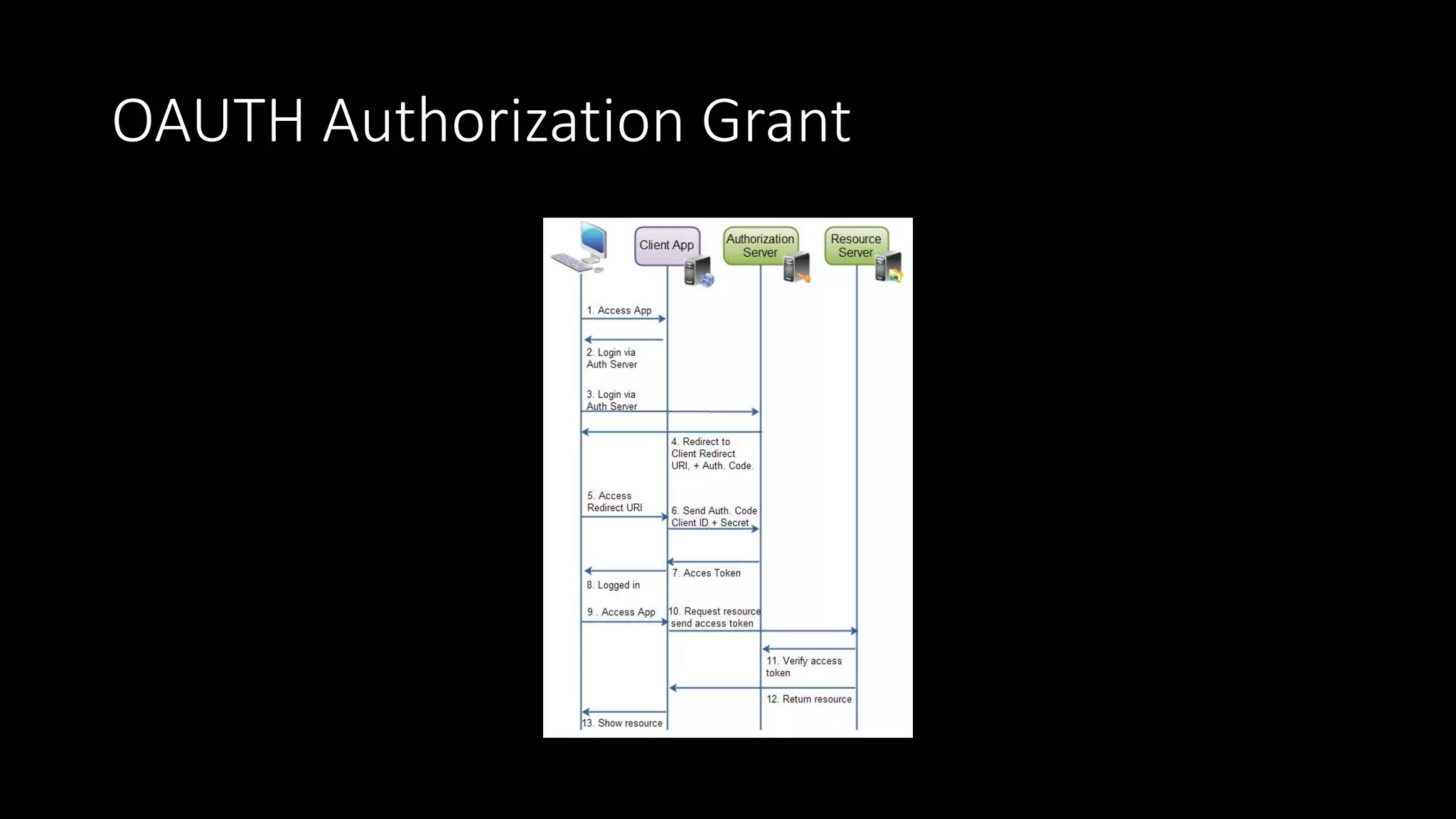
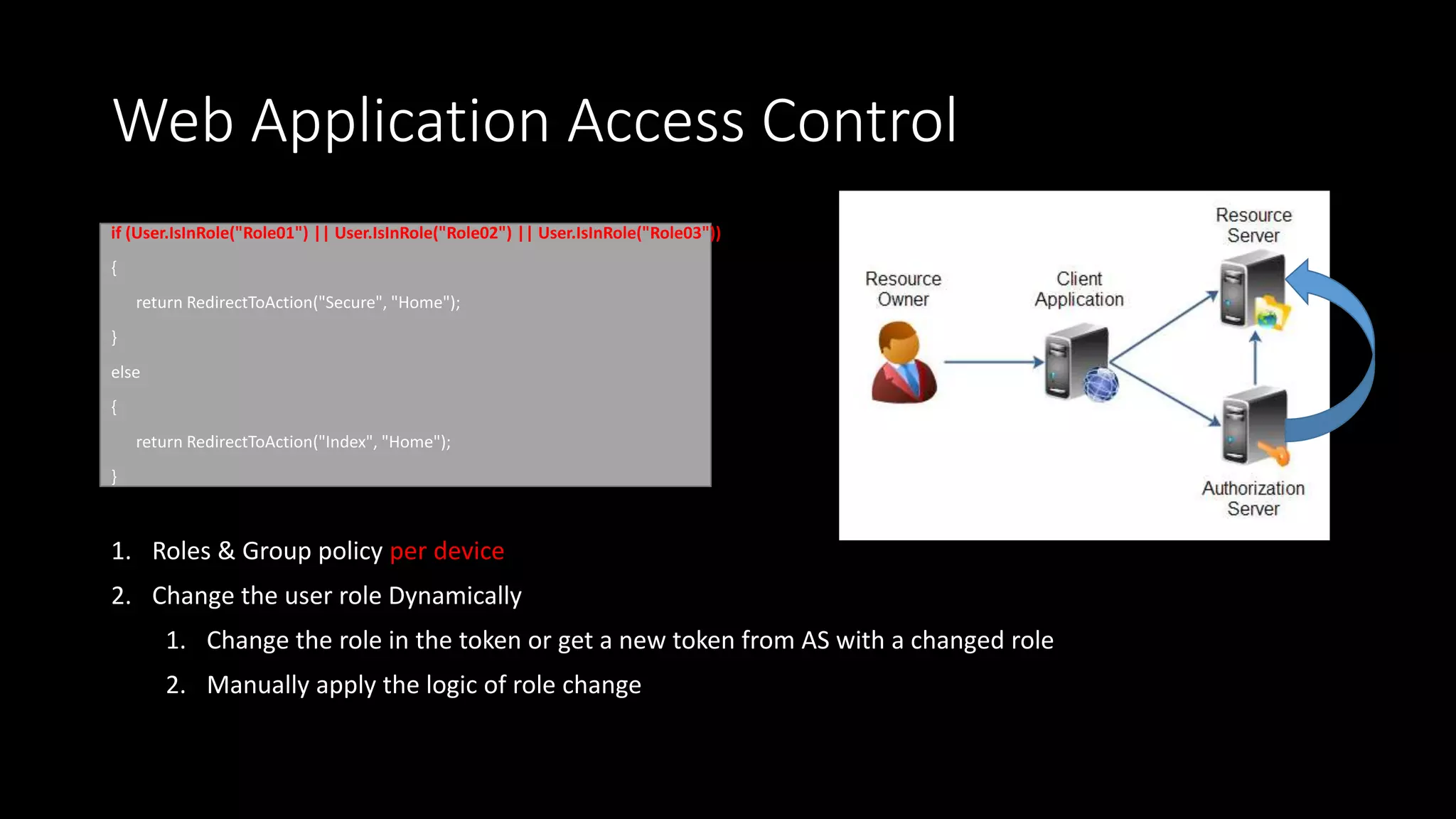
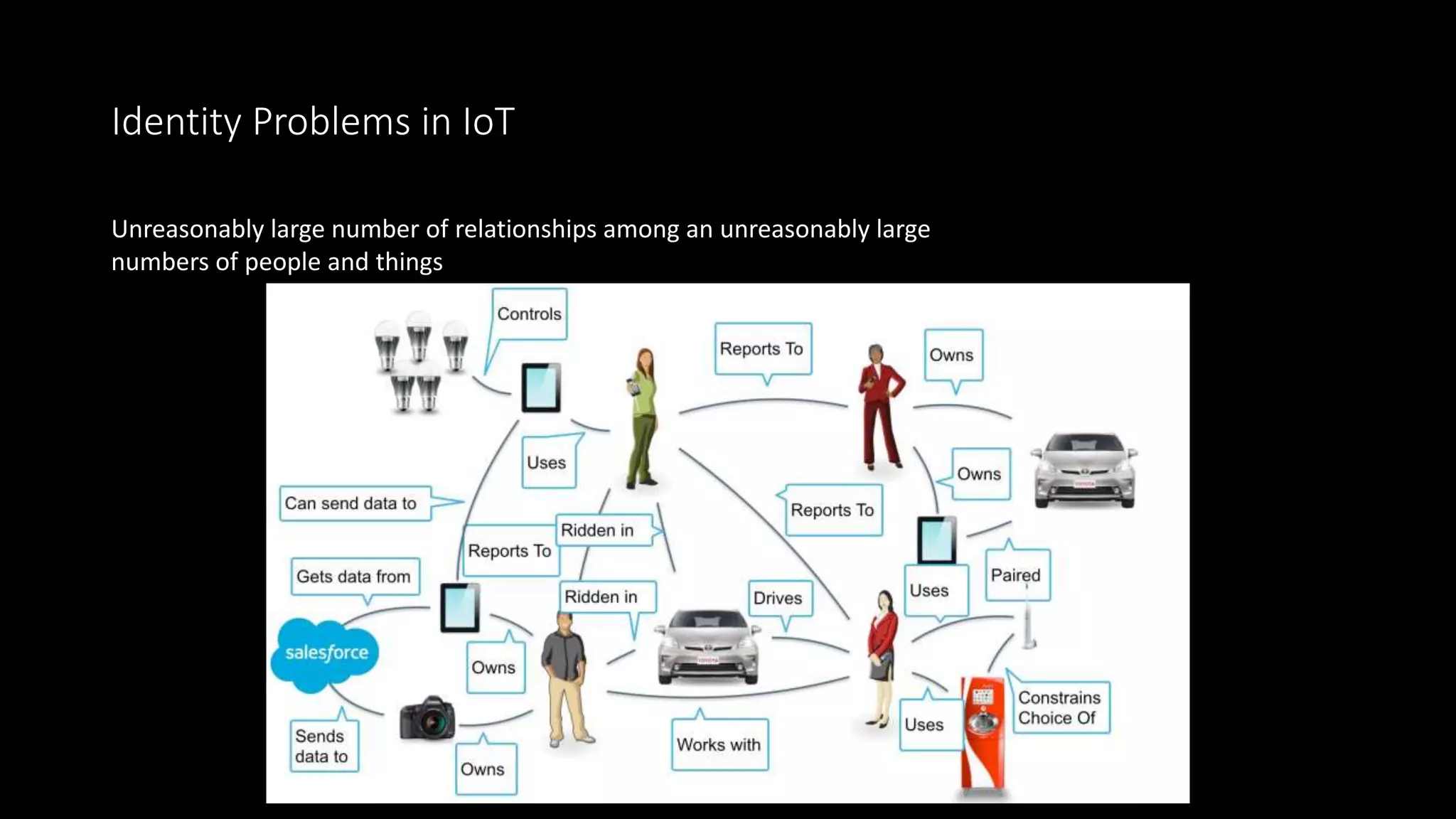
The document outlines the architecture and issues related to identity, authentication, and authorization within IoT systems, focusing on communication strategies and usability challenges. It highlights problems with existing models, such as multiple identity providers and the necessity for effective identity relationship management. A proposed solution involves leveraging control systems as identity providers and improving synchronization methods between cloud and local identities.



![Identity
• Identity = set of attributes related to an entity [iso 29115]
Entity Identity
6’ 5” Tall
Grey Hair Man
Work
Husband
Father
Women
Mother
Daughter
Wife
Girl FriendFriend
Boss
Collegue
Identity is Context Driven
For each context, the attribute differs
Identity1
Identity2
Identity3](https://image.slidesharecdn.com/iotmobileapp-device-cloudidentityandsecurityarchitecture-170930072357/75/IoT-mobile-app-device-cloud-identity-and-security-architecture-5-2048.jpg)












![Is button Pressed?
GET /en-US/user/isbuttonpressed HTTP/1.1
Host: www.meethue.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_8_3) AppleWebKit/536.28.10
(KHTML, like Gecko) Version/6.0.3 Safari/536.28.10
Accept: */*
DNT: 1
X-Requested-With: XMLHttpRequest
Referer: https://www.meethue.com/en-US/user/linkbridge
Accept-Language: en-us
Accept-Encoding: gzip, deflate
Cookie:[DELETED]
Connection: keep-alive
Proxy-Connection: keep-alive
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8
Cache-Control: no-cache
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Set-Cookie: PLAY_FLASH=;Path=/;Expires=Thu, 01 Jan 1970 00:00:00 GMT
Set-Cookie: PLAY_ERRORS=;Path=/;Expires=Thu, 01 Jan 1970 00:00:00 GMT
Set-Cookie: [DELETED]
Vary: Accept-Encoding
Date: Mon, 29 Apr 2013 23:30:06 GMT
Server: Google Frontend
Content-Length: 4
true
Request Response](https://image.slidesharecdn.com/iotmobileapp-device-cloudidentityandsecurityarchitecture-170930072357/75/IoT-mobile-app-device-cloud-identity-and-security-architecture-36-2048.jpg)
![Complete setup
GET /en-US/user/setupcomplete HTTP/1.1
Host: www.meethue.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_8_3)
AppleWebKit/536.28.10
(KHTML, like Gecko) Version/6.0.3 Safari/536.28.10
Accept: text/html,application/xhtml+xml,application/xml;
DNT: 1
Referer: https://www.meethue.com/en-US/user/linkbridge
Accept-Language: en-us
Accept-Encoding: gzip, deflate
Cookie: [DELETED]
Connection: keep-alive
Proxy-Connection: keep-alive
HTTP/1.1 200 OK
Content-Type: text/html; charset=utf-8; charset=utf-8
Cache-Control: no-cache
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Set-Cookie: PLAY_FLASH=;Path=/;Expires=Thu, 01 Jan 1970 00:00:00 GMT
Set-Cookie: PLAY_ERRORS=;Path=/;Expires=Thu, 01 Jan 1970 00:00:00 GMT
Set-Cookie: PLAY_SESSION="[DELETED]-%00ip_address%3A[DELETED]__[DELETED]
;Path=/
Vary: Accept-Encoding
Date: Mon, 29 Apr 2013 23:30:08 GMT
Server: Google Frontend
Content-Length: 47369
[DELETED]
app.data.bridge = {"clientMessageState":[DELETED],"config":{"lights":{"15":
{"name":"Bathroom 2","state":{"bri":254,"effect":"none","sat":144,"reachabl
e":true,"alert":"none","hue":14922,"colormode":"ct","on":false,"ct":369,"xy
":[0.4595,0.4105]},"modelid":"LCT001","swversion":"65003148"
Request Response](https://image.slidesharecdn.com/iotmobileapp-device-cloudidentityandsecurityarchitecture-170930072357/75/IoT-mobile-app-device-cloud-identity-and-security-architecture-37-2048.jpg)
![Controlling Lights Using the iOS App
GET /api/[username MD5 Hash of MacID] HTTP/1.1
Host: 10.0.1.2
Proxy-Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en-us
Connection: keep-alive
Pragma: no-cache
User-Agent: hue/1.1.1 CFNetwork/609.1.4 Darwin/13.0.0
HTTP/1.1 200 OK
Cache-Control: no-store, no-cache, must-revalidate, post-
check=0, pre-check=0
Pragma: no-cache
Expires: Mon, 1 Aug 2011 09:00:00 GMT
Connection: close
Access-Control-Max-Age: 0
Access-Control-Allow-Origin: *
Access-Control-Allow-Credentials: true
Access-Control-Allow-Methods: POST, GET, OPTIONS, PUT,
DELETE
Access-Control-Allow-Headers: Content-Type
Content-type: application/json
[{"error":{"type":1,"address":"/","description":"unauthorized
user"}}]
Request Response](https://image.slidesharecdn.com/iotmobileapp-device-cloudidentityandsecurityarchitecture-170930072357/75/IoT-mobile-app-device-cloud-identity-and-security-architecture-40-2048.jpg)
![Identity / Authentication
POST /api HTTP/1.1
Host: 10.0.1.2
Proxy-Connection: keep-alive
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-
form-urlencoded
Accept-Language: en-us
Accept: */*
Pragma: no-cache
Connection: keep-alive
User-Agent: hue/1.1.1
CFNetwork/609.1.4 Darwin/13.0.0
Content-Length: 71
{"username":"[username
DELETED]","devicetype":"iPhone
5"}
HTTP/1.1 200 OK
Cache-Control: no-store, no-cache,
must-revalidate, post-check=0, pre-
check=0
Pragma: no-cache
Expires: Mon, 1 Aug 2011 09:00:00
GMT
Connection: close
Access-Control-Max-Age: 0
Access-Control-Allow-Origin: *
Access-Control-Allow-Credentials: true
Access-Control-Allow-Methods: POST,
GET, OPTIONS, PUT, DELETE
Access-Control-Allow-Headers:
Content-Type
Content-type: application/json
[{"success":{"username":"[username
DELETED]"}}]
Request Response](https://image.slidesharecdn.com/iotmobileapp-device-cloudidentityandsecurityarchitecture-170930072357/75/IoT-mobile-app-device-cloud-identity-and-security-architecture-41-2048.jpg)
![Away from home setup complete
GET /en-US/api/getaccesstokenpost HTTP/1.1
Host: www.meethue.com
Referer: https://www.meethue.com/en-US/api/getaccesstokengivepermission
Proxy-Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Cookie: [DELETED]
Accept-Language: en-us
Connection: keep-alive
User-Agent: Mozilla/5.0 (iPhone; CPU iPhone OS 6_1_4 like Mac OS X)
AppleWebKit/536.26 (KHTML, like Gecko) Version/6.0 Mobile/10B350
Safari/8536.25
Request](https://image.slidesharecdn.com/iotmobileapp-device-cloudidentityandsecurityarchitecture-170930072357/75/IoT-mobile-app-device-cloud-identity-and-security-architecture-43-2048.jpg)