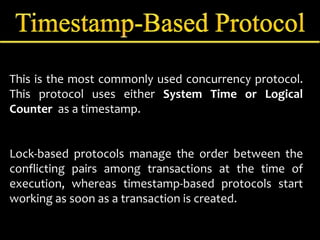
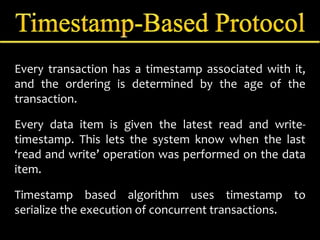
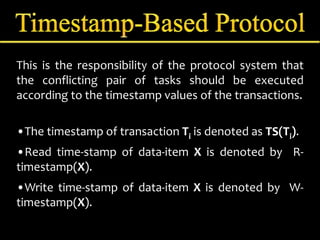
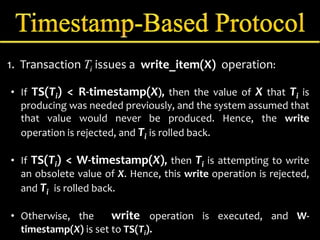
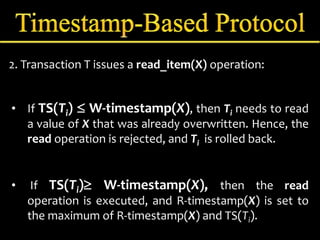
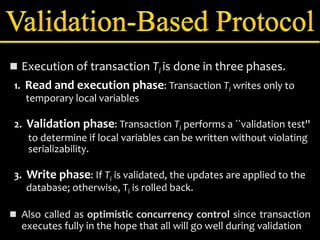
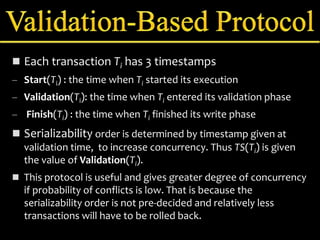
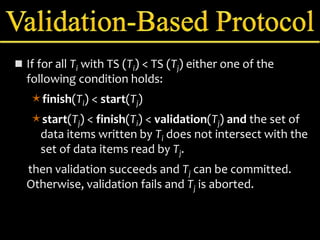
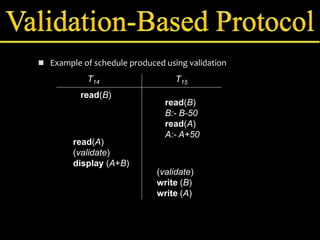
Concurrency control manages simultaneous database operations to prevent interference. It enforces isolation through techniques like locking to resolve conflicts. The main goals are preserving consistency, resolving read-write and write-write conflicts, and maintaining integrity despite lost updates or inconsistent data. Approaches include lock-based protocols, timestamp-based protocols, and validation-based protocols.